This is the second part of Elcomsoft Phone Password Breaker Enhances iCloud Forensics and Speeds Up Investigations article.
Extracting the content of an iPhone is only half the job. Recovering meaningful information from raw data is yet another matter. The good news is there are plenty of powerful tools providing iOS analytics. The bad news? You’re about to spend a lot of time analyzing the files and documenting the findings. Depending on the purpose of your investigation, your budget and your level of expertise using forensic tools, you may want using one tool or the other. Let’s see what’s available.
Mobile Forensic Tools
There are few tools in this category. These tools offer powerful analytics, and can extract pretty much everything you can imagine.
Oxygen Forensic Suite is by far the most powerful mobile analytics toolkit on the market. Designed for investigators and forensic specialists, the toolkit can analyze information from a huge number of mobile devices including all models of iPhone, iPad and iPod Touch. You can feed it with iPhone backups acquired with Elcomsoft iOS Forensic Toolkit or downloaded with Elcomsoft Phone Password Breaker.
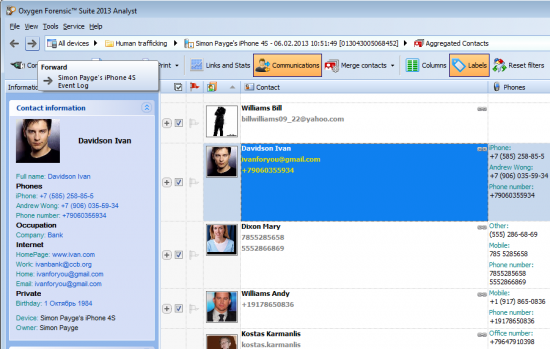
Oxygen Forensic Suite offers a quite unique feature that can aggregate information about subject’s activities collected from a variety of sources across the device, including Apple and third-party applications. Investigators can view all conversations, chats and communications made with a huge number of apps in a single aggregated timeline. Historical geolocation analysis helps discover the subject’s whereabouts at any point in time. Global search across multiple acquired devices can quickly reveal connections between owners of different devices such as common contacts, exchanged calls, texts or emails.
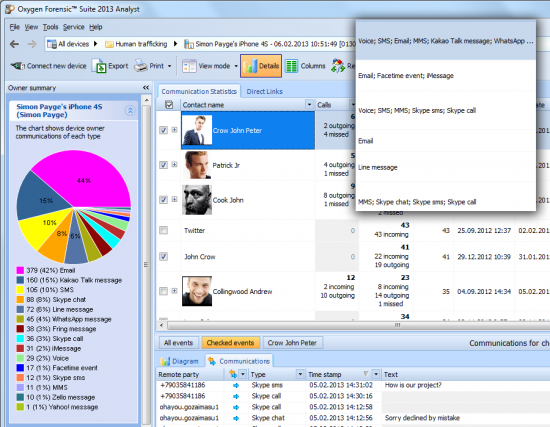
The tool can recover deleted records from SQLite databases, enabling access to destroyed evidence and often recovering enough information from cleared histories. With functionality like this, it’s worth every penny of its price tag.
Oxygen Forensic Suite runs on Windows PCs.
iBackupBot is not a forensic tool, strictly speaking, but it offers enough features at a n extremely affordable price to make it to the list. If you are on a tight budget, iBackupBot offers the ability to view and analyze iOS backup files. Note that this tool will not accept “unpacked” backups with file name conversion. You’ll have to supply it with a full backup image. No big deal, just select this option when acquiring an iPhone with Elcomsoft iOS Forensic Toolkit or downloading data from the cloud with Elcomsoft Phone Password Breaker.
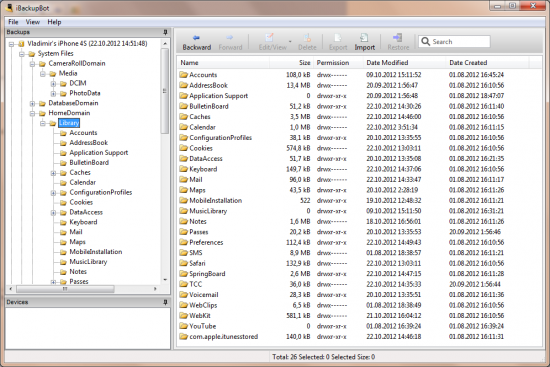
iBackupBot helps investigators view and analyze backup files in iTunes format, locating and viewing relevant files of interest. The tool allows viewing PLIST files and SQLite databases, extracting essential information such as images, SMS messages, notes, address book, call history, and more.
As you can see, compared to Oxygen Forensic Suite, iBackupBot is rather basic, offering none of the great analytic features of Oxygen’s toolkit. Its extremely modest price tag (just under $35 at the time of the writing) makes it a worthy proposition if you are on a tight budget.
iBackupBot can run on Windows or MacOS X computers.
iPhoneAnalyzer is a free tool helping experts to examine information stored in iOS devices. Just like iBackupBot, iPhoneAnalyzer expects a full backup file in iTunes format, and offers a convenient presentation of information stored in the phone.
Unfortunately, the product has been discontinued by its manufacturer. It’s available as an open-source project.
Distributed as a .jar package, this tool should work on any Java-enabled computer.
iPBA2: iOS Backup Analyzer is another free, open-source tool helping to analyze the content of iPhone backups. Written in Python, it can be used on any computer with Python libraries.
SQLite Analysis Tools
If you only need to extract certain types of information, you can try using a smaller, lighter tool just to view records from SQLite databases (*.sqlite, *.sqlitedb, and *.db files extracted from the backup). If this is the case, you will need to configure Elcomsoft iOS Forensic Toolkit or Elcomsoft Phone Password Breaker to recover original file names instead of saving the complete backup file in iTunes format. You will then be able to analyze individual databases with any of the following tools.
Belkasoft Evidence Center is a highly advanced forensic tool offering native SQLite database parsing and freelist processing. These two features allow investigators recover deleted records and gain access to cleared histories. Native SQLite handling allows recovering badly damaged, fragmented and incomplete databases.
Freelist access is a great feature allowing to recover deleted SQLite records. Information deleted from SQLite databases is not wiped immediately. Instead, it is transferred into a so-called freelist. Note that freelists are not accessible with standard SQLite parsing tools, so if you need recovering destroyed evidence, your choice of tools becomes very limited.
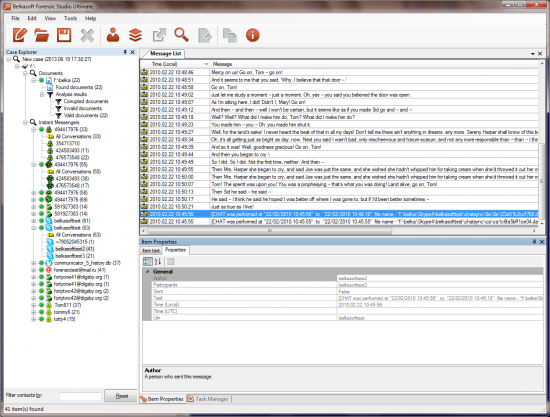
Other than SQLite parsing, Evidence Center makes it easy for an investigator to analyze evidence found in iOS backups. The toolkit will help quickly locate and analyze information found in instant messenger logs, internet browser histories, mailboxes of popular email clients, social network remnants, peer-to-peer data, multi-player game chats, office documents, pictures, videos, etc.
Belkasoft Evidence Center runs in Windows.
Epilog is another forensic toolkit that can deal with deleted SQLite records and freelists. Epilog allows investigators recover deleted data from SQLite databases. The tool does nothing more than that, and its price tag is just a few dollars short of the price of Oxygen Forensic Suite (which is miles ahead in the analytic department), so make sure to check out Oxygen’s Web site before you make a decision.
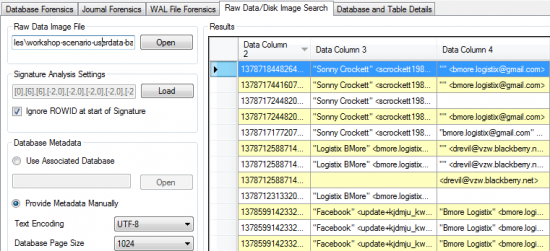
Epilog processes individual SQLite files, so you have to configure Elcomsoft iOS Forensic Toolkit or Elcomsoft Phone Password Breaker to recover original file names.
EPilog runs in Windows.
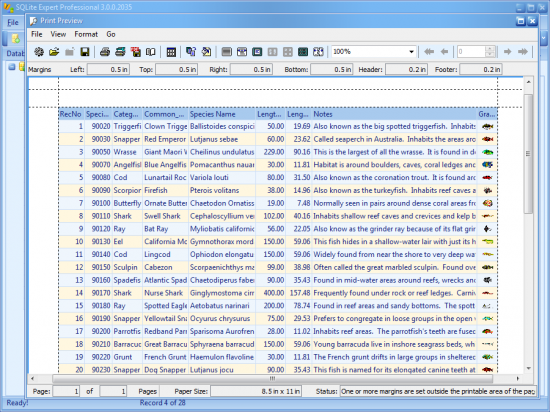
SQLite Expert is a de-facto standard tool for viewing SQLite databases. Unfortunately, it offers no access to deleted records or the freelist, so its use as a forensic tool is limited.
Viewing .plist Files
The property list (.plist) format are often used to store user configurable settings, and may contain information about bundles and applications. Plist files can contain XML and binary files. You can analyze XML files with any XML viewer (there are plenty of them out there). Binary files can be analyzed in Oxygen Forensic Suite with a built-in Plist Viewer.
Alternatively, you can use a standard MacOS X utility called plutil.
Finally, you can use PIP XML and PLIST Parsing Tool or plist Editor to view plist data stored in both XML and binary formats.








