With all the trouble of jailbreaking iOS 8 devices and the lack of support for 64-bit hardware, does iOS physical acquisition still present meaningful benefits to the investigator? Is it still worth your time and effort attempting to acquire that iPhone via a Lightning cord?
Granted, jailbroken iOS devices are rare as hen’s teeth. You are very unlikely to see one in the wild. However, we strongly believe that physical acquisition still plays an important role in the lab, and here are the reasons why.
- Apple’s current privacy policy explicitly denies government information requests if the device in question is running iOS 8. This means that handing over the device to Apple will no longer result in receiving its full image if the device is running iOS 8.x (source: https://www.apple.com/privacy/government-information-requests/)
- In many countries (Mexico, Brazil, Russia, East Europe etc.) Apple sells more 32-bit phones than 64-bit ones. Old iPhones traded in the US are refurbished and sold to consumers in other countries (BrightStar coordinates these operations for Apple in the US). As an example, new and refurbished iPhone 4S and 5 units accounted for some 46% of all iPhones sold through retail channels in Russia in Q1 2015.
- Physical extraction returns significantly more information compared to any other acquisition method including logical or over-the-air acquisition. In particular, we’re talking about downloaded mail and full application data including logs and cache files (especially those related to Internet activities). A lot of this information never makes it into backups.
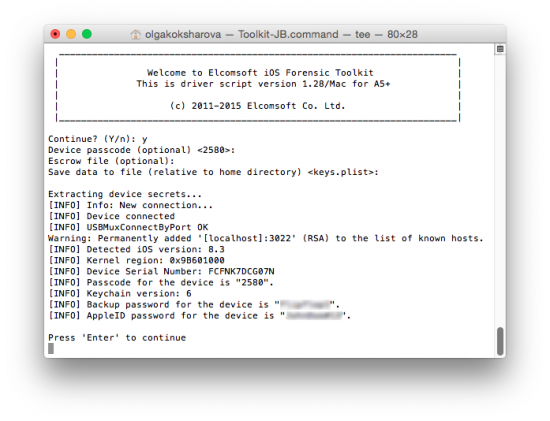
- Full keychain extraction is only available with physical acquisition. Physical is the only way to fully decrypting the keychain including those records encrypted with device-specific keys. Those keychain items can be extracted from a backup file, but cannot be decrypted without a device-specific key. In addition, the keychain often contains the user’s Apple ID password.
- With physical acquisition, you can extract the ‘securityd’ (0x835) from the device. This key can be used to completely decrypt all keychain items from iCloud backups.
- Physical acquisition produces a standard DMG disk image with HFS+ file system. You can mount the image into the system and use a wider range of mobile forensic tools to analyze compared to iTunes or iCloud backup files.
At this time, Elcomsoft iOS Forensic Toolkit remains the only third-party forensic tool to perform physical acquisition of iPhone 4S, 5 and 5C.
Limitations of Physical Acquisition
Apple makes their platform increasingly secure with each generation of hardware and every version of iOS. Apple devices equipped with 64-bit hardware are not susceptible to physical acquisition. Since the overwhelming majority of iOS devices sold in the US through retail channels are already equipped with 64-bit hardware, the number of handsets equipped with 32-bit chips is rapidly declining. The opposite is true for many developing markets where old-generation devices oversell latest hardware.
When it comes to iOS 8, physical acquisition is only available to jailbroken devices. At this time, jailbreak is available for all current versions of iOS 8 up to and including iOS 8.3.
As a result, physical acquisition has the following limitations:
- Only 32-bit hardware is supported *
- iOS 8 devices must be jailbroken in order to perform physical acquisition.
- Jailbreaking is not as reliable and straightforward as we’d like it to be.
- You can’t jailbreak a locked device if you don’t know the passcode.
- Find My Phone must be disabled before installing jailbreak. If Find My Phone is on, you must enter the user’s Apple ID password to turn it off.
- In order to perform physical acquisition of a jailbroken device, you’ll need to manually install OpenSSH from Cydia.
- At this time, only TaiG jailbreak is supported for the purpose of physical acquisition (http://www.taig.com/en/)
* 64-bit devices are still not supported regardless of iOS version or jailbreak status. For the purpose of physical acquisition, the following compatibility matrix applies.
Supported:
- iPhone 4S, 5, 5C
- iPod Touch (5th gen)
- iPad 2 through 4
- iPad mini (original)
NOT supported:
- iPhone 5S, 6, 6 Plus
- iPad Air
- iPad mini Retina, iPad mini 3
Conclusion
Even with all limitations of physical acquisition, the method still remains viable in many situations. Some countries still see more 32-bit Apple devices than 64-bit ones, with Apple refurbished devices (trade-ins from the US) pushed by the company as a cheap entry into the ecosystem. Since Apple no longer serves government information requests for devices running iOS 8, physical acquisition remains the only method to extract the full file system from the device, returning more information than any other acquisition method.



