July 17th, 2023 by Vladimir Katalov
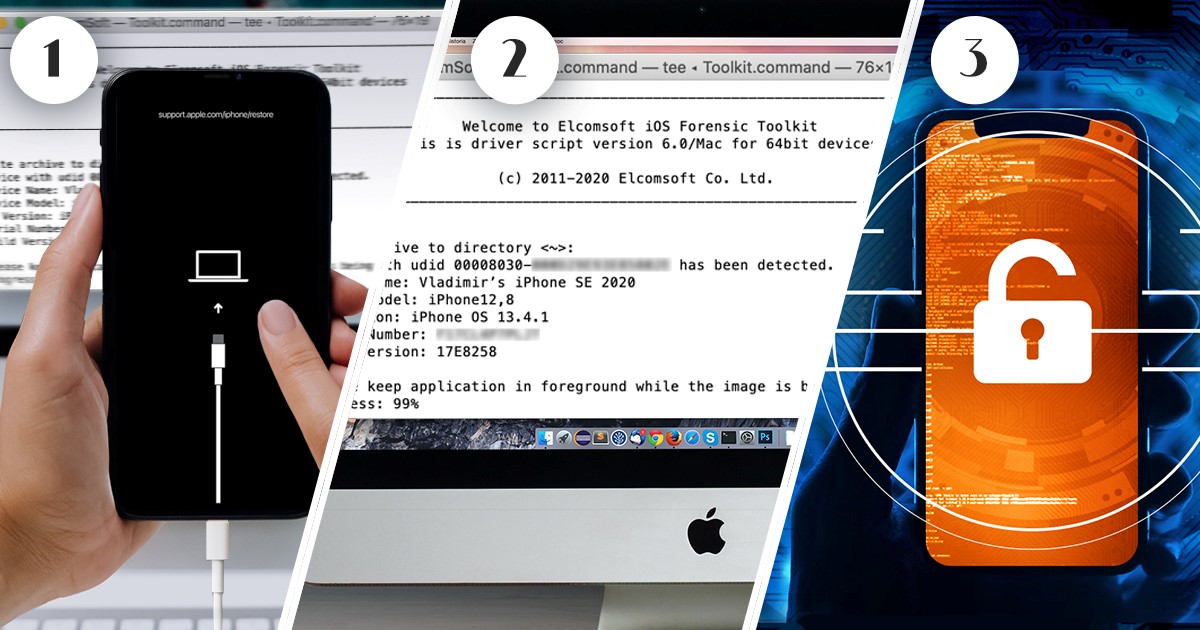
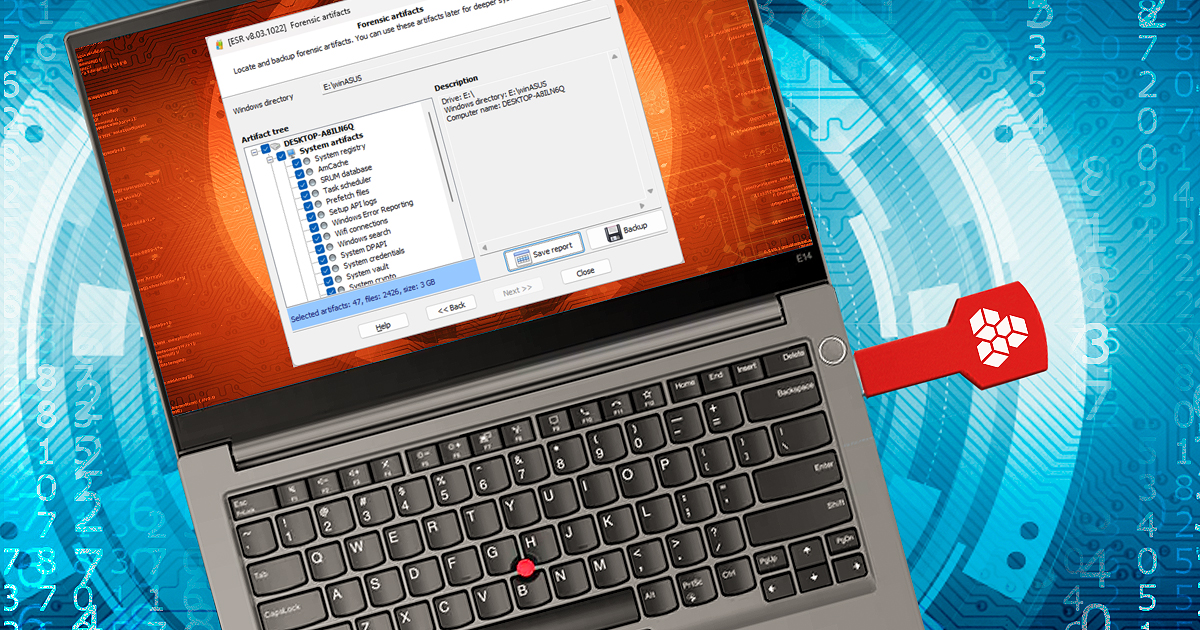
For forensic experts dealing with mobile devices, having a reliable and efficient forensic solution is crucial. Elcomsoft iOS Forensic Toolkit is an all-in-one software that aids in extracting data from iOS devices, yet it is still far away from being a one-button solution that many experts keep dreaming of. In this article, we will walk you through the preparation and installation steps, list additional hardware environments, and provide instructions on how to use the toolkit safely and effectively.
Read the rest of this entry »