Every time when you open a document in Advanced Office Password Recovery it performs the preliminary attack in case when the "file open" password is set. This attack tries all passwords that you recovered in past (which are stored in password cache), dictionary attack and finally the brute-force attack is running.
The brute-force attack consists of two parts:
1. Trying digits and latin letters
2. Trying national characters depending on code page set in Windows.
Before this time these parts were hardcoded in the program. The new version of Advanced Office Password Recovery has an option to customize the preliminary brute-force attack.
Look to the directory where AOPR is installed. There is "attacks.xml" file inside. The first section of this file is the language map:
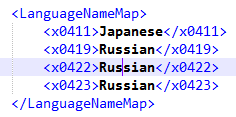
The codes are Windows language identifiers. You can link any LID to your custom name.
The next section contains predefined charsets:
.gif)
All charsets are in unicode so you can define any national characters here.
And the final section is "documents". All parts of this section has comments about document types. You can define the "common" charsets and charsets that are related to system language. Each "attack" record defines password length and charset.
In this XML file you can simply change the standard preliminary attack and define the custom charsets for your language. I hope this will help to recover your Office passwords faster.

.gif)


