February 16th, 2026 by Vladimir Katalov
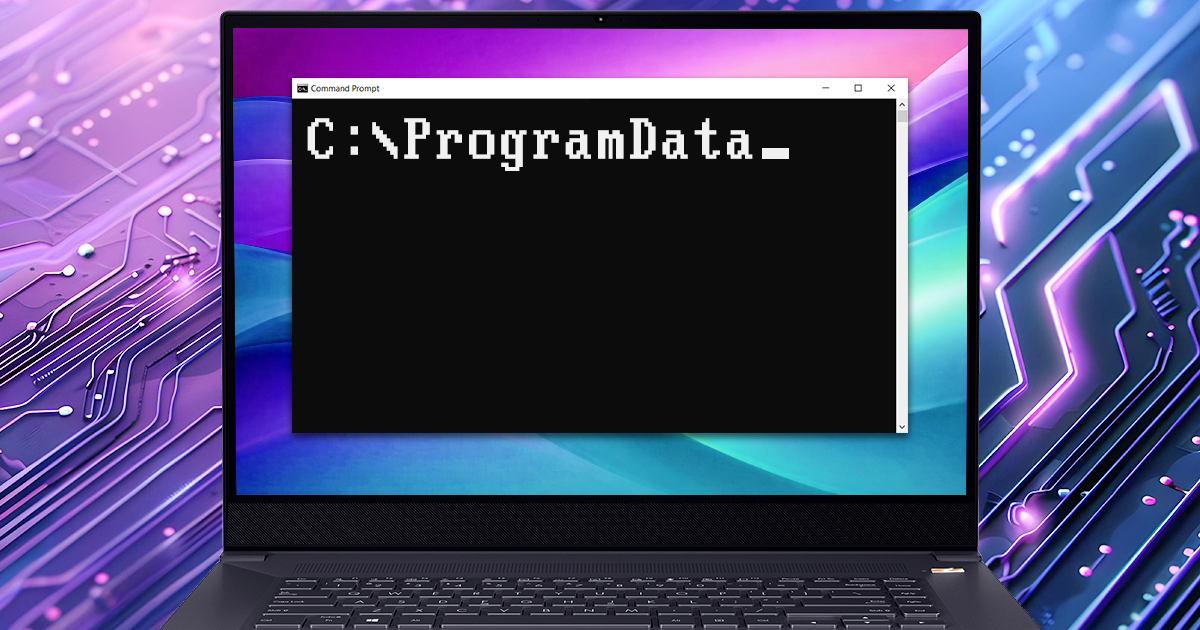
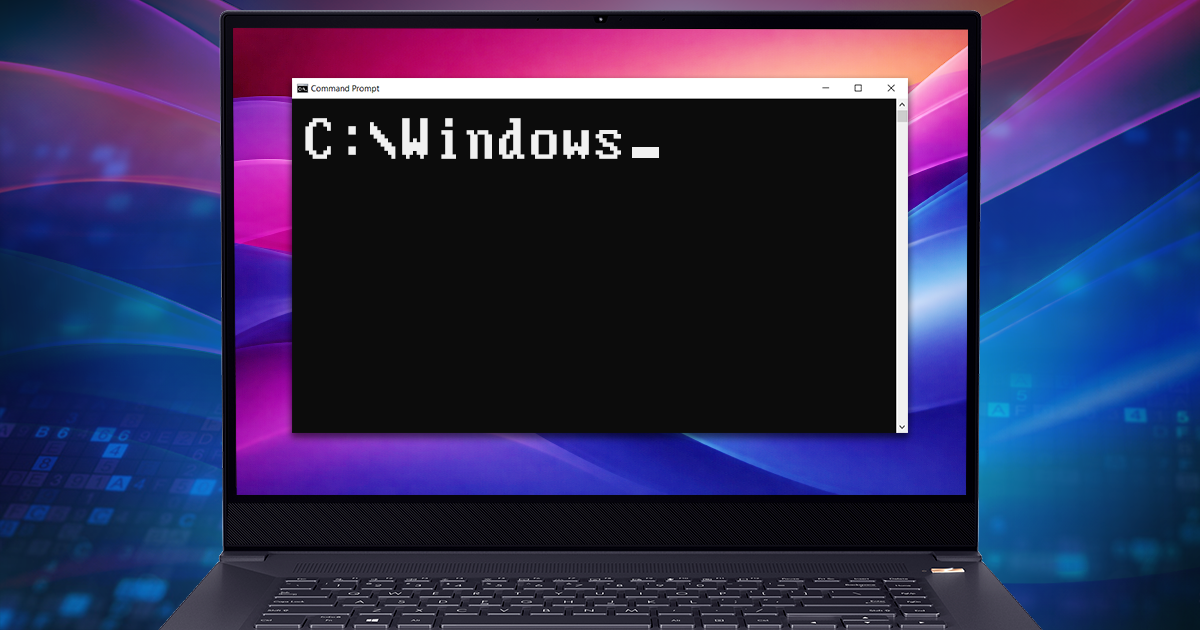
The release of the checkm8 exploit was a breakthrough for mobile forensics, finally granting investigators verifiable access to the file systems of various Apple devices. This accessibility established the current “gold standard” for extraction: using the bootloader exploit to access the file system and dump it into a simple tar archive. While convenient, a tar archive is merely a logical copy, not a physical one. It may fail to capture the device’s true state, missing certain low-level nuances. Truth be told, these nuances are rarely relevant to real investigations, but why settle for less when a better method is available? More importantly, this approach avoids the “teething problems” of traditional bootloader extraction – such as the mishandling of large sparse files – that continue to plague even the largest forensic vendors.
Read the rest of this entry »