There was a 3-fold increase in identity theft and more than 2-fold increase in phishing attacks registered in 2020 compared to 2019 according to IC3 report. A whopping 50 – 81% of attacks (depending on who you read) are targeting both corporate and private sectors to steal users’ login credentials; that is, passwords. No matter what changes happen in data security, passwords remain the most wide-spread means of protection.
Being a global digital forensic solution provider for more than 25 years now, ElcomSoft has already established itself as an expert in this field. In the extensive articles in our blog and during the conferences, we regularly share information on how to break into a smartphone or decrypt crypto containers, access encrypted information and extract as much evidence as possible with GPU-accelerated smart attacks or little-known but legitimate workarounds. We provide solutions and train digital forensic practitioners on how to gain access to and decrypt protected information, how to download data from cloud services with or without a password, and how to bypass two-factor authentication.
Today we would like to share our list of must-dos when using password protection. So, here are our recommendations for better password habits – not that we are going to discover America here, but it will help you to brush up your current security habits.
-
Make alphanumerical passwords that aren’t based on dictionary words
By analyzing the regularly leaked password databases, it’s obvious that most users are still choosing easy-to-guess dictionary words as their passwords, making them an easy prey for a dictionary attack. Combining two dictionary words (e.g. GingerBun) or adding numbers in front of or at the end of the word (e.g. 1999Aliceor Alice1999) is not a solution since these are accounted for and targeted with GPU accelerated smart attacks.
Dictionaries can also be constructed from passwords extracted from other sources (e.g. from the user’s Web browser). ElcomSoft offers tools such as Elcomsoft Internet Password Breaker allowing to extract the available passwords from the user’s computer and automatically build a custom dictionary.
-
Make it long enough and unique per application
A password is as strong as much time it takes to break it. When it comes to a randomly chosen non-dictionary password that would require brute-forcing, the time to break a password is defined by the password length, or the number of characters in the password. The time to break a password also heavily depends on the file format and the hardware available to the attacker. The user, of course, cannot influence this, although we must assume that the attacker can use the latest equipment.
In our recent tests, a single NVIDIA RTX 3090 card, called the Big Ferocious GPU, achieved the speed of 1.2 million WPA/WPA2 passwords per second (WPA passwords are just an example). The new card delivers a significant performance boost over the previous high-performance NVIDIA GeForce GTX 1080 that could reach 334,000 passwords per second and 500x win over the CPU-only attacks.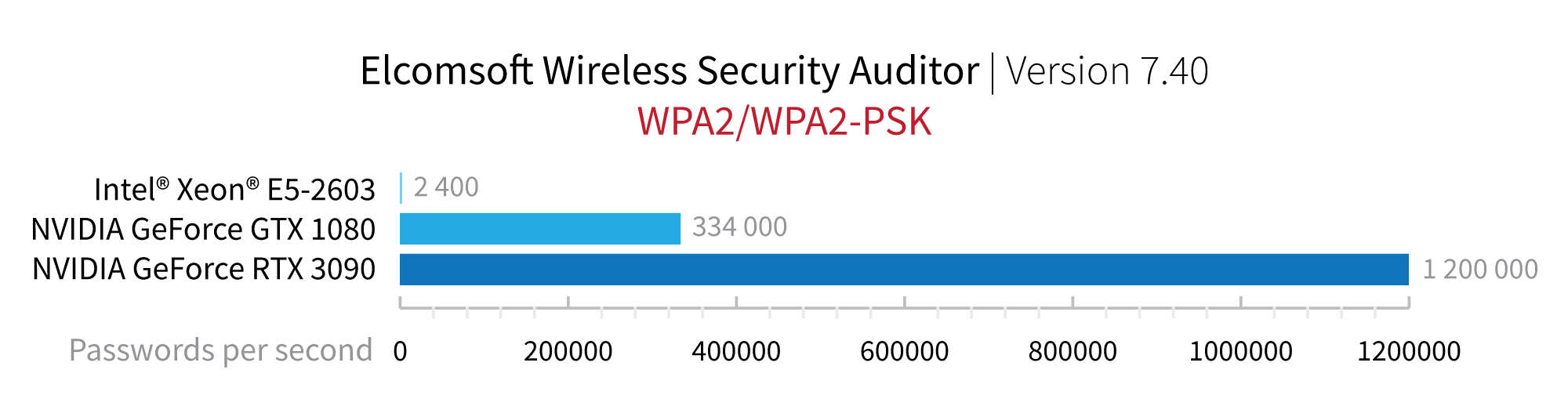
-
Add more layers of protection when possible
We’ve been writing about multi-factor authentication for Apple devices and Google services for a long time. Companies concerned about real data security do not believe that a password alone is enough protection for the security of personal data. Phishing attacks, frequent leaks of password databases, and bad password habits (aka the human factor) make password protection insecure. The combination of something you haveand something you know greatly improves security. If possible, be sure to enable two-factor authentication, even if it requires additional effort on your part. With today’s advanced technologies, multi-factor authentication is the new normality.
-
Be careful resetting passwords
A recently made public data breach at dating service Manhunt demonstrated that a tool made by a reputable company can be compromised to force users change and leak their new passwords to attackers. While this should not normally happen, there are still millions of tools with unknown vulnerabilities around.
Conclusion
Digital security and password protection are a complex multi-pronged issue. In simpler terms your security is a double-sided coin. The one side is technical protection and the other one is your comfort at using it. The trick is to find your own balance, while the technical side is constantly getting more complicated and the other side is gravitating to more comfort.



