Elcomsoft Distributed Password Recovery and Hashcat support a number of different attacks ranging from brute-force all the way to scriptable, dictionary-based attacks. The costs and performance are extremely important factors. We charge several hundred dollars for what, in the end, can be done with a free tool. Which tool has better performance, and are the extra features worth the price premium? Let’s check it out.
The attacks
When recovering a tough password, almost everything depends on the quality of the wordlist and the type and configuration of the attack. Let us see how the two tools compare.
Brute force and mask attacks
Plain brute force attacks almost never succeed on anything but the simplest passwords, yet they still might be effective against shorter passwords and uncomplicated protection.
In Hashcat and hashtopolis, you specify the attack through the command line or list the attacks in a text file. In Hashcat, brute force attacks are a subset of the mask attack. As an example, if you want to try all passwords that consist of small Latin letters and are 1 to 5 characters long, you can specify the following attack:
?l
?l?l
?l?l?l
?l?l?l?l
?l?l?l?l?l
If you are using hashtopolis, you’ll need to enter these five strings into the corresponding text field.
Elcomsoft Distributed Password Recovery supports a similar concept, but allows specifying the minimum and maximum password length as well as the character set either globally (for the whole password) or in groups or characters, allowing to quickly build an attack that takes into consideration the human factor. Brute-force and masks attacks are configured in the GUI.
Dictionary attack
The two tools implement dictionary attacks differently. Hashcat accepts the dictionary as a wordlist, trying each entry the way it is stored in the dictionary. There are no pre-defined mutations and no ability to add a mask when running a dictionary attack (these are parts of the rule-based attack). No automatic distribution of the dictionary file is available if you are running hashtopolis; agents will only use the dictionaries that are already installed.
Elcomsoft Distributed Password Recovery provides automatic dictionary distribution to all connected agents including those working in the virtual instances. Dictionary attacks support a large number of pre-defined mutations, allowing to try the most common combinations of dictionary words such as Password, password1, Pa$$w0rd, password1965 and a lot more. We recommend our users trying a small dictionary with certain mutations first, as this often finds frequently used passwords. We also include the dictionary of the top 10,000 most popular passwords from several major leaks, which may help breaking up to 30% of cases in English-speaking countries.
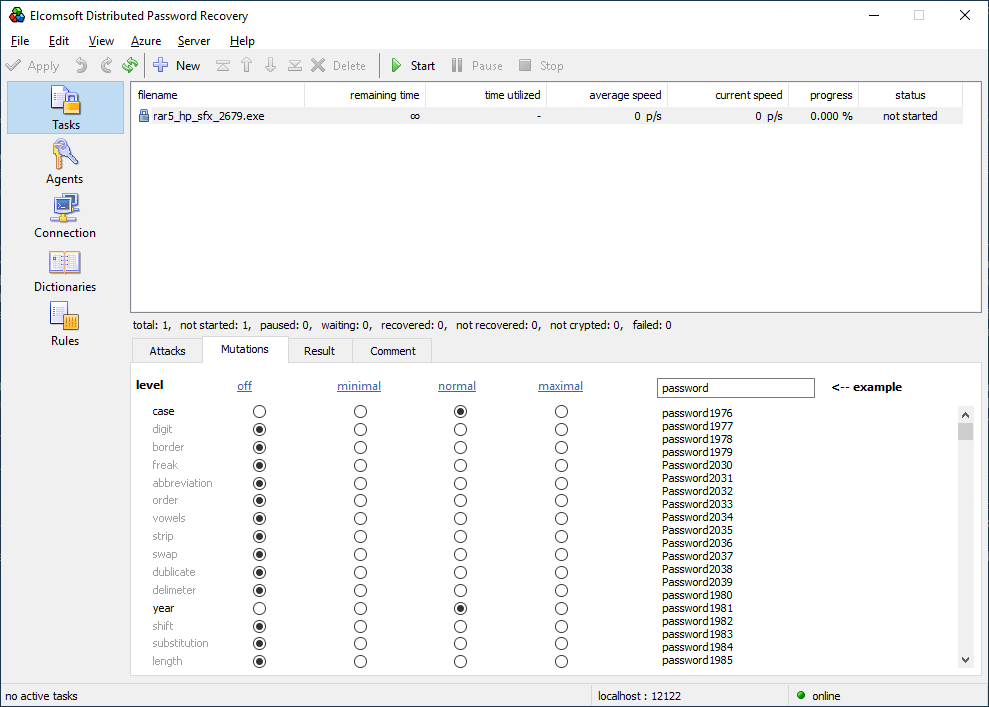
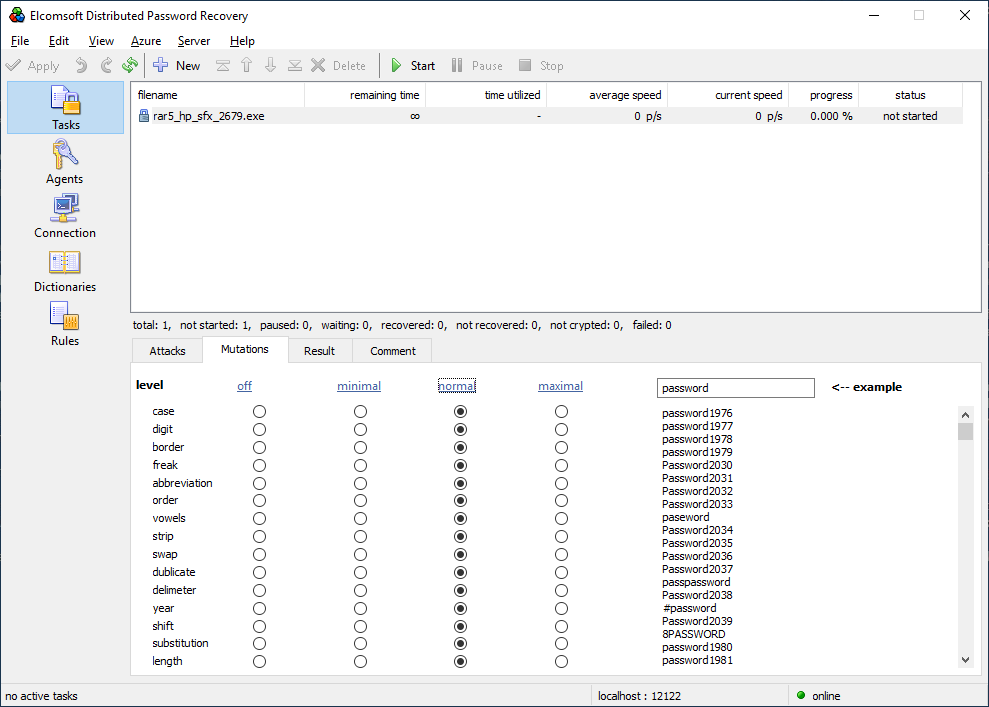
Combinator attack
This is a simple combination of two dictionary words from two dictionaries (same or different files). Both Hashcat and Elcomsoft Distributed Password Recovery support this attack.
Hybrid attack
While both tools support hybrid attacks, the term is used in different meanings.
Hashcat-style hybrid attacks combine one dictionary word (from a single dictionary) with one mask. This would be considered a particular case of a mask attack in Elcomsoft Distributed Password Recovery. In our tool, one can use multiple dictionaries, where any part of the mask can be a dictionary word. We believe that our solution has an edge over Hashcat here.
What Elcomsoft Distributed Password Recovery calls a “hybrid attack” is classified as a “rule-based attack” in Hashcat.
Rule-based attack
The “rule-based attack” in Hashcat is called “hybrid attack” in Elcomsoft Distributed Password Recovery. Otherwise, the implementations are very similar; we would even call them identical, as booth tools are following the same syntax as John The Ripper, the tool that originated this attack. Elcomsoft’s makes using John The Ripper style attacks much easier than Hashcat thanks to the use of the newly developed visual Rule editor. The Rule editor brings John the Ripper’s syntax directly to the user interface, eliminating the need for manually editing text files.
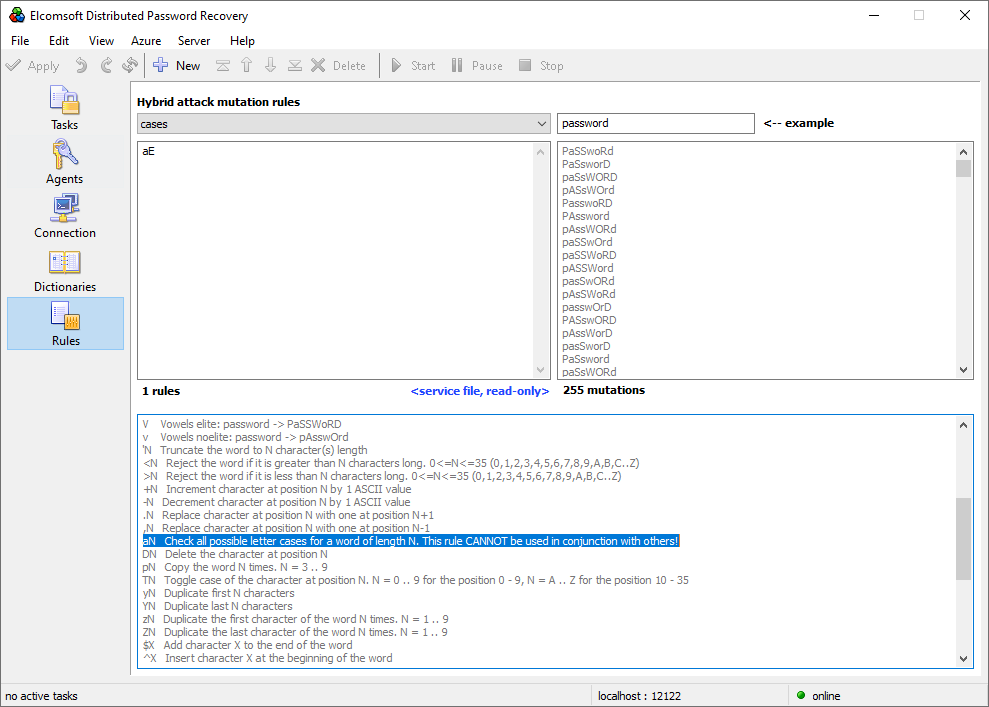
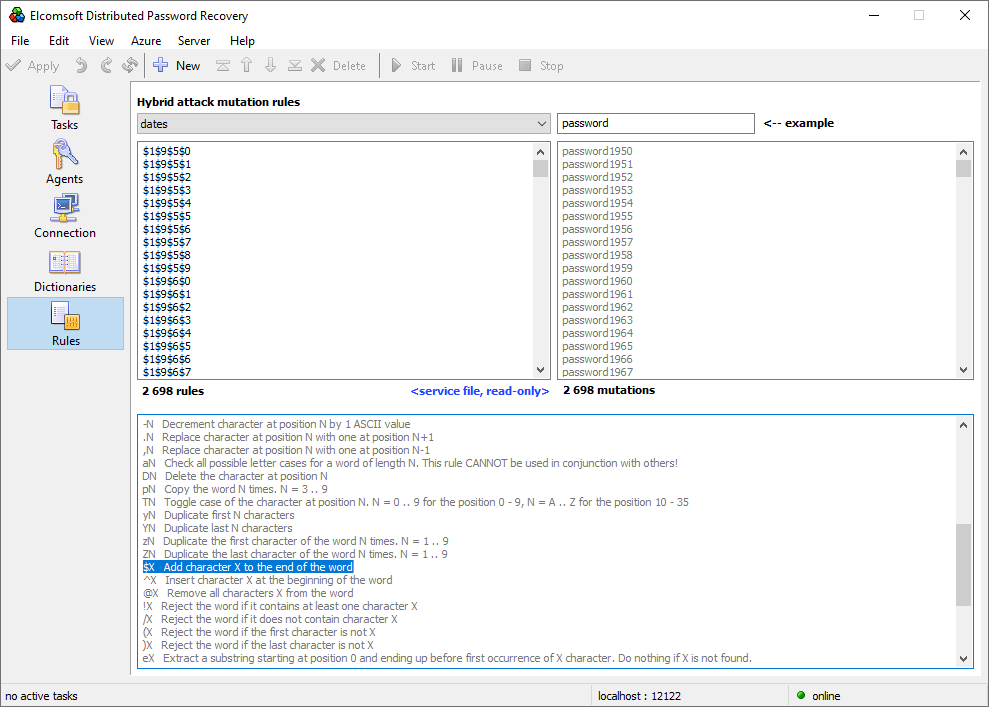
Attacks: conclusion
Booth tools support a wide range of attacks. Dare we say, setting up attacks in Elcomsoft Distributed Password Recovery is simpler and more straightforward compared to Hashcat. Everything is configured from the graphical user interface. A live preview of sample passwords is displayed for every mask or mutation enabled.
To its credit, Hashcat has the ability to run a set of several consecutive attacks, a feature that Elcomsoft Distributed Password Recovery lacks. One can, however, create multiple individual attacks on the password, and run them in the regular job queue.
Benchmarks
If you read to this point, you must be interested which tool is faster. While we could make and post numerous benchmarks, the truth is that both tools are highly optimized, and both can exploit the available hardware resources to the maximum. Trying over a hundred formats, we’ve seen performance fluctuations of around 10 per cent. For many formats, Elcomsoft Distributed Password Recovery offers a (very) slight edge over Hashcat thanks to the additional utilization of available CPU cores (Hashcat, as you remember, is GPU-only). Whichever tool you choose, you’ll be happy with its raw performance – or, at least, it doesn’t get much better if you jump ship.
The costs
If you are an open-source fan, you’re going to like this chapter; less so of you are a (paid) customer.
Hashcat is free. Hashcat, hashtopolis, most hash extraction scripts and the host OS (Linux) are absolutely free to use, modify, recompile, or make a custom version just for you, on one condition: you do it yourself or you pay someone to do it for you. Using Hashcat requires skills and experience. Setting up Hashcat on a single computer requires deeper skills, more experience and quite some time. Preparing the tool to run on a distributed network requires skills and experience in Linux administration, a lot of time and a bit of trial and error. Writing attack scripts takes time, and even adding an agent to hashtopolis when you expand your distributed network takes time. It takes time processing disk images of encrypted disk, and it takes time to obtain hash extraction scripts for the occasional new file format.
Elcomsoft Distributed Password Recovery is as much plug-and-play as a forensic grade distributed computing tool can be. Installing the tool on a single computer is no different from installing any other Windows program, while deploying agents to network computers is similar to deploying any other package in your Windows domain. Prepackaged agents make cloud instances straightforward to set up and to use. The attacks are as fast or slightly faster than Hashcat, while being significantly easier to set up.
That level of user-friendliness and simplicity comes at a cost. We charge $599 for a license covering the parallel use of 5 agents. If you are expanding into the cloud, you will notice the differences in cost between Linux and Windows-powered VMs. It is also
The cost of hardware should be the same for both products. The more and the faster video cards you install, the faster the attacks.
Technical support
If you have a problem, Hashcat has a wide community of users and an active forum where you can search for or post questions about issues. What you may not like is the answers. While we had no problem finding the answers to our issues (e.g. attacking a large ZIP archive), finding that what you want is simply not an option can be a little… discouraging.
Elcomsoft Distributed Password Recovery is supported by us via the standard ticket system. We stand behind our product, quickly resolving the issues once they are reported.
The extra features
There are a few features that can greatly improve usability of Elcomsoft Distributed Password Recovery over Hashcat.
Password cache
If we find a password to one job, we add that password into a custom dictionary. Once the next job is started, we’ll try passwords from that dictionary first. This helps save time if the same password is reused across multiple files or data formats.
Non-ASCII characters and Unicode support
Hashcat supports non-ASCII and Unicode characters, but adding those to the attack requires a concise effort. If you want to add certain non-ASCII characters, you’ll have to use the –hex-charset option and add the extra characters as HEX codes. If you want to use a dictionary with non-ASCII words, you’ll have to do the same.
Elcomsoft Distributed Password Recovery is Unicode throughout.
Running as a service
Elcomsoft Distributed Password Recovery agents do not require an authenticated user session to work. Agents can run as a system service, starting along with the system.
Hashcat can do the same in Linux. However, the Windows version requires an authenticated session to run hashtopolis Python scripts.
Distributed updates
When you update Elcomsoft Distributed Password Recovery, all components of the distributed network are updated automatically including all connected agents.
Hashtopolis makes updates a journey. While Hashcat and hashtopolis can be updated automatically, updating the agents requires an effort. You’ll have to manually stop each agent, obtain the updated version from the server, and manually install it on each computer.






