We’ve just updated Elcomsoft Distributed Password Recovery with the ability to break master passwords protecting encrypted vaults of the four popular password keepers: 1Password, KeePass, LastPass and Dashlane. In this article, we’ll talk about security of today’s password managers, and provide insight on what exactly we did and how to break in to encrypted vaults.
Password managers are nothing new. They’ve been around for years, helping users store, organize, and use passwords. Password managers are designed to solve the problem of password reuse, which gets more attention every year as the number of online accounts used by an average consumer grows. Various researches conducted in 2015 and 2016 suggest that, while an average consumer has 20 different online accounts, that same consumer only uses 7 different passwords, and even those 7 are actually based on as few as 3 truly unique passwords. The rest are variations of one or more strings such as “password”, “password1”, “password1959”, “Password1”, and so on.
20 online accounts. 7 different passwords. Only 3 of them are unique.
At least in theory, the use of password managers can increase overall security by relieving users from having to memorize a number of unique, strong passwords. This in turn would allow users providing secure authentication credentials without reusing the same password on different resources. Most password managers keep authentication credentials (logins, passwords and other data) in an encrypted vault, and use a single user-provided master password to encrypt those other passwords.
Obviously, if the master password is compromised, all other passwords stored in the vault are compromised as well. Back in 2012, we conducted a research of then-popular password keepers. The report indicated that very few of those products were significantly more secure compared to storing passwords in a plain-text file. In 2017, we have a different picture, with quite a few secure options available. This includes 1Password, KeePass, LastPass and Dashlane.
Today, password managers overall security is debatable. On the one hand, using unique, secure passwords for different accounts is strongly recommended for security reasons. On the other hand, if the one master password is compromised or can be recovered, the attacker gains access to the full and complete database containing all user’s passwords and authentication credentials.
Are password managers more secure than keeping a list of passwords in a single Excel spreadsheet? Not necessarily, but this lack of security is easily offset by the extra convenience offered by password managers compared to an Excel spreadsheet.
Elcomsoft Distributed Password Recovery 3.40 now supports four major password manager apps including 1Password, KeePass, LastPass and Dashlane. The tool allows experts attacking a single master password and gaining access to the content of the encrypted vault, exposing any passwords, authentication credentials and other sensitive information (identity documents, credit card data etc.)
The full list of password managers supported by Elcomsoft Distributed Password Recovery 3.40 includes:
1Password
1Password is one of the more secure password keepers. EDPR can attack master passwords protecting encrypted vaults in all versions of 1Password including Windows, macOS, iOS, and Android apps. In addition, we support encrypted vaults backed up to Dropbox and iCloud Drive. In other words, full support for 1Password vaults is available regardless of source and platform.
LastPass
LastPass is one of the most popular cloud-based password managers. Unlike KeePass, its Android version properly uses protected storage area by keeping the data in its own private sandbox (/data/data/com.lastpass.lpandroid); as a result, root access is required to extract the data.
EDPR supports LastPass plug-ins for desktop Web browsers running on Windows, macOS, and even Linux. Android version is supported if you are able to extract the encrypted vault and metadata (root access is required).
Note: in order to extract LastPass encrypted vault and meta data, you must use EDPR Disk Encryption Info. EDPR Disk Encryption Info is a supplemental utility shipped with EDPR. The tool is used to make it easier for experts to extract and de-obfuscate the password hash using this metadata.
KeePass
KeePass does not have built-in backup capabilities. However, it uses two distinctly different vault formats: .kdb (KeePass 1.x) and .kdbx (KeePass 2.x). EDPR supports both vault formats created by KeePass apps and most of its clones on all platforms.
Interestingly, when researching KeePass, we discovered that one of the popular Android apps KeePassDroid keeps its encrypted vault in public storage:
/storage/emulated/0/keepass/keepass.kdbx
This file is easily accessible and extractable. Why developers decided not to protect the database by placing it in the app’s sandboxed storage is a mystery.
DashLane
EDPR supports Windows and macOS versions of this password manager.
Benchmarks
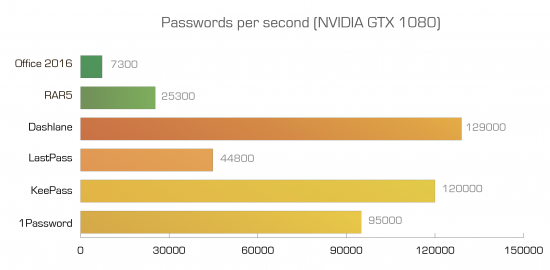
Different password managers employ different approaches to security. As an example, LastPass generates the encryption key by hashing the username and master password with 5,000 rounds of PBKDF2-SHA256, while 1Password employs even more rounds of hashing. This is designed to slow down brute-force attacks, and it almost works. Granted, these are still nearly an order of magnitude less secure than, say, Microsoft Office 2016 documents, but even this level of security is much better than nothing.
Therefore, this is the benchmark. We’ve added RAR5 and Office 2016 to the chart for comparison sake. Higher numbers represent higher recovery speeds.
Conclusion
Password managers become increasingly common, and their forensic support is essential. Our solution provides industry fastest GPU-accelerated, distributed recovery of master passwords that protect password managers’ encrypted vaults, allowing experts to gain access to users’ most sensitive information. The current release of Elcomsoft Distributed Password Recovery supports encrypted vaults produced by the four popular password managers. With the exception of LastPass, which requires using the supplied EDPR Disk Encryption Info tool in order to extract encryption metadata, the additional formats can be attacked by using exactly the same workflow as most other supported formats.
Additional Resources
We collected a short list of resources you may find useful.



