Cloud acquisition is arguably the future of mobile forensics. Even today, cloud services by Apple and Google often contain more information than any single device – mostly due to the fact that cloud data is collected from multiple sources.
The two biggest challenges of cloud extraction have always been the account password and the secondary authentication factor. Without the correct password, accessing information in the user’s iCloud or Google Account was nearly impossible, the only alternative being the lengthy and complex legal process. Several years back, we developed a workaround, allowing experts to use binary authentication token to access Apple iCloud backups and synced data without the password. Today, we are introducing the same thing for Google accounts. If you have access to the user’s computer (Mac or PC), you can extract a binary authentication token from that computer and use it to bypass the password and two-factor authentication protection. So let us have a look at what these tokens are, where they are stored, what’s inside, and how to use them to access and extract information from the Google Account.
Passwordless Authentication
The first release of Elcomsoft Cloud Explorer only supported the most straightforward authentication path, requiring you to provide the user’s login and password in order to access data. Subsequent releases added support for two-factor authentication, starting with six-digit backup codes and including support for the newest Google Prompt and exotic FIDO/Yubico USB keys. Since you had to supply a Google Account and password anyway, we were frequently asked what the big deal was compared to Google Takeout. If ECX needs a password anyway, could you just do the same by some standard means?
Elcomsoft Cloud Explorer always extracted a lot more information than Google Takeout ever gave away, and did it in a much faster and in a much easier way compared to Google’s tool. This, for example, is the result of Google Takeout I obtained when trying to extract data from my very own account:
“Please note that archives may take a long time (hours or possibly days) to create. You will receive an email when your archive is complete.”
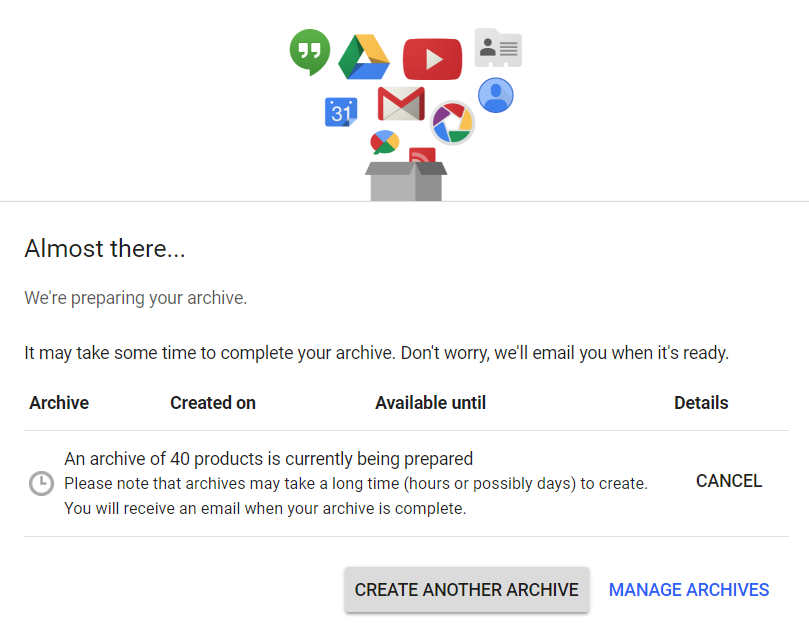
Four hours after, still no download link from Google. On the other hand, Elcomsoft Cloud Explorer has finished the download in less than two hours (for 4.47GB of data in my account).
Today, we’re adding one more highly usable feature: the ability to access information without a password – and without triggering an email alert!
How does it work, exactly?
In order to achieve passwordless authentication, we had to research Google authentication tokens. Authentication tokens are small XML files stored on the user’s hard drive (or in the Keychain in mac OS) after they sign in to any Google service with Chrome (or the Google Drive app for Drive tokens). The data from that XML file is then used for authentication of the ongoing and subsequent sessions without asking the user to re-enter the password or confirm the two-factor authentication prompt.
The token is generated by Google servers after the user first passes authentication. While the token works as a password replacement, it cannot be used to attack or recover the password: the data is just a random identification string, which is not a hash function of the password itself. The use of authentication tokens makes the system not only more convenient (no need to re-authenticate for the user) but in a way more secure since the password is not saved anywhere.
We researched where Chrome and Google Drive tokens are stored on Mac and PC computers, and discovered a way to use them for passwordless authentication into Google services with Elcomsoft Cloud Explorer. Passwordless authentication is available if Google Chrome is installed on the user’s computer, and if the user has signed in to any Google service via the browser.
This is where Google stores the authentication tokens on the user’s computer.
For Google Chrome tokens:
Windows:
%appdata%\Local\Google\User Data\<Profile_name>\Web Data
Mac:
/Users/<username>/Library/Application Support/Google/Chrome/<profile_name>/Web Data
For Google Drive tokens:
Windows (in the Registry):
HKEY_CURRENT_USER\SOFTWARE\Google\Drive\
Мас (in the Keychain):
/Users/<username>/Library/Keychains/<keychain_name>Generic Keychain/Google Drive
We developed a new tool we called Google Token Extractor (GTEX). This tool automatically searches the user’s computer (Windows or Mac) for authentication tokens saved by the Google Chrome browser or the Google Drive app. Once the authentication token is located, GTEX saves it alongside the ECX executable file (Windows) or the user’s default directory (Mac).
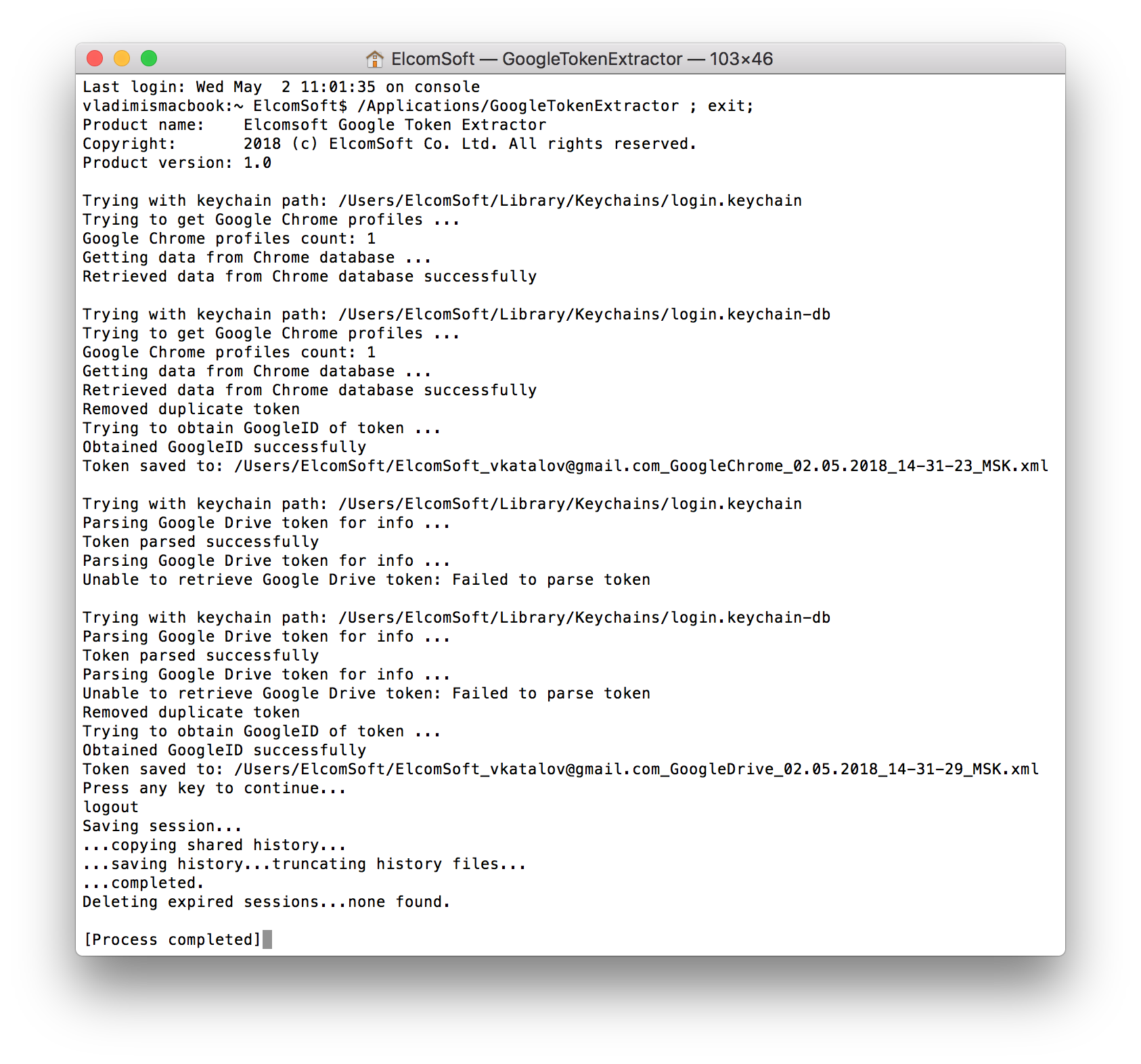
Once Google Token Extractor extracts the token, the file is named according to the following format:
<user_name><Google ID><token_type><date><time>.xml
Example:
Google Chrome:
john.smith_test.account@gmail.com_GoogleChrome_01.02.2017_15-05-16_UTC.xml
Google Drive:
john.smith_test.account@gmail.com_GoogleDrive_01.02.2017_15-05-16_UTC.xml
Inside, the token may look like this:
Google Chrome (Windows):
<?xml version="1.0" encoding="UTF-8" standalone="yes" ?>
<ExtractedToken>
<GTEXVersion>1</GTEXVersion>
<Platform>Windows</Platform>
<GoogleID>test.account@gmail.com</GoogleID>
<Token>1/ukM2X_qTUU-viA-8Yn6LqzLjcGQ-nmHjsh254RYAOF4</Token>
<TokenType>GoogleChrome</TokenType>
<ClientID>77185425430.apps.googleusercontent.com</ClientID>
<ClientSecret>OTJg....</ClientSecret>
<ExtractedAt>03.04.2018 09:12:35</ExtractedAt>
</ExtractedToken>
Google Drive (МаcOS)
<?xml version="1.0" encoding="UTF-8" standalone="yes" ?>
<ExtractedToken>
<GTEXVersion>1</GTEXVersion>
<Platform>macOS</Platform>
<GoogleID>other.test.account@gmail.com</GoogleID>
<Token>1/ukM2X_qTUU-viA-8Yn6LqzLjcGQ-nmHjsh254RYAOF4</Token>
<TokenType>GoogleDrive</TokenType>
<ClientID>645529619299.apps.googleusercontent.com</ClientID>
<ClientSecret>nu6p....</ClientSecret>
<ExtractedAt>27.02.2018 16:46:55</ExtractedAt>
</ExtractedToken>
Once the token is extracted, it can be used with Elcomsoft Cloud Explorer to access information stored in the user’s Google Account without the need to re-enter the password or perform the secondary authentication step.
By using a token extracted from Chrome, you’ll gain access to all of the following data categories: Chrome (including browsing history, bookmarks and passwords), Calendars, Dashboards, History, Google Drive, and Hangouts. Note that tokens extracted from the Google Drive app will only allow accessing Google Drive data.
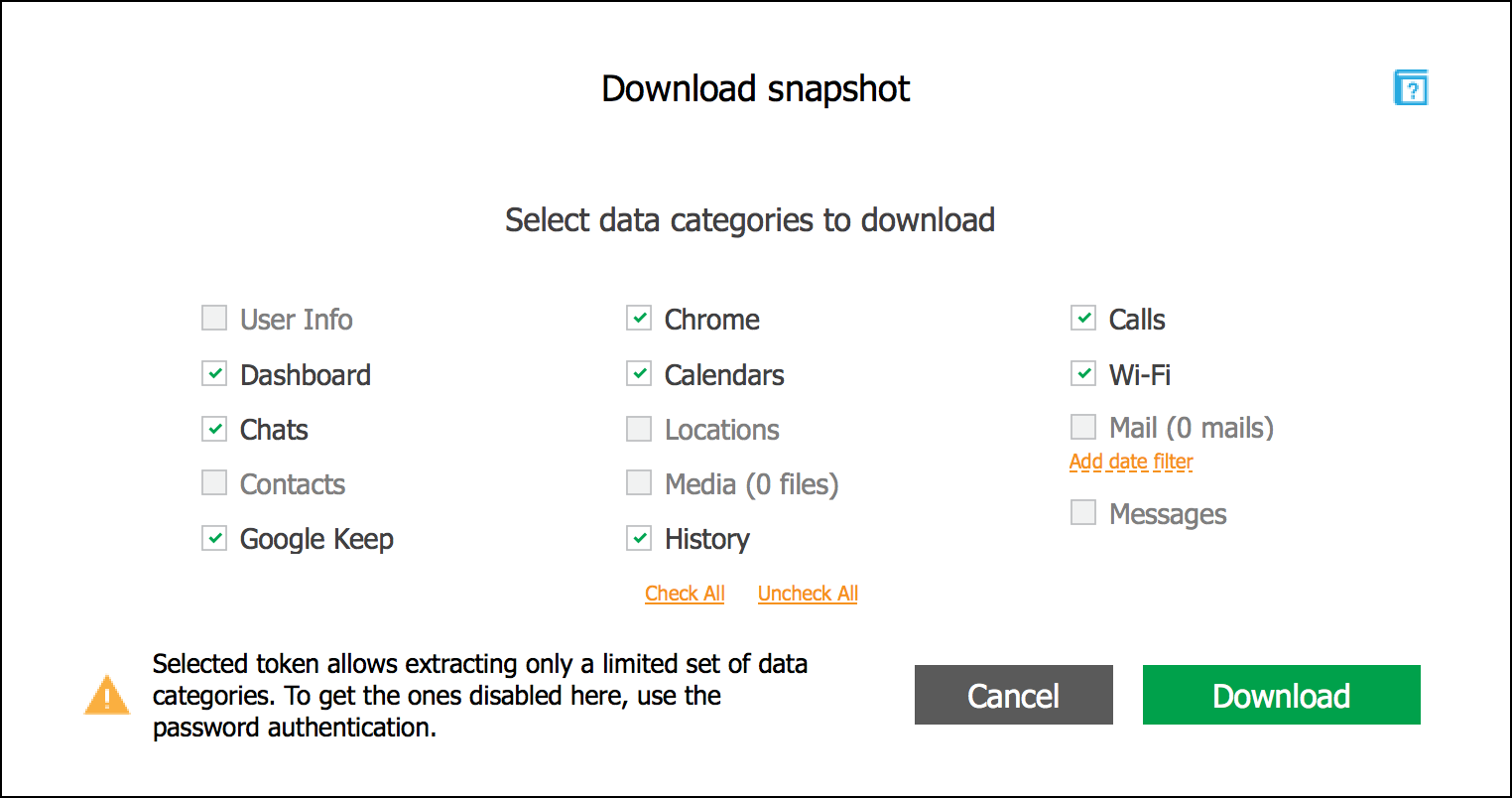
Note that some categories such as email, media files and locations, are unavailable when using token-based authentication. Access to these categories is protected with a password.






