“Significant Locations” are an important part of the evidence logged on iPhones. Forensic experts doing the acquisition will try accessing Significant Locations. At the same time, many iPhone users are completely unaware of the existence of this feature. What are Significant Locations, where are they stored, and how to extract them, and what value do they serve in investigations?
Privacy Issues
iOS 11 and iOS 12 after it supposedly come with a slew of privacy enhancements. When it comes to Significant Locations, what we see is quite the opposite. There is an unresolved privacy issue instead.
Speaking strictly of “significant locations”, iOS 10 and older versions used to retain this data no longer than 45 days. Older records would be purged from the device. In iOS 11.4, the current release, location data is kept for at least 120 days (or 4 months). Apple does not provide ANY information about how or when it collects your location data; moreover, there is no official statement about how this data is being used. The only article that we were able to discover is “Location Services & Privacy“. Have a look at the following quote:
Significant Locations – Your iPhone will keep track of places you have recently been, as well as how often and when you visited them, in order to learn places that are significant to you. This data is transmitted end-to-end encrypted between your iCloud connected devices and will not be shared without your consent. It will be used to provide you with personalized services, such as predictive traffic routing, and to build better Photos Memories.
Wait… why do I see iCloud? I sure did not give my any permission so save my location data in the cloud, and it looks like there is no option to keep location data exclusively on my local device. We all know what Google does to location data, but at very least Google offers an option to opt-out (though we have not checked whether it really works).
Let’s look at “Legal Process Guidelines” too see what data Apple can provide to the law enforcement. It’s quite a lot, but speaking of locations it’s just the “Find My Phone” data, which is all about the current location at the time of submitting the request.
GDPR? You bet. Let’s have a look at “Get a copy of the data associated with your Apple ID account“. Nothing about location data here either.
Apple, we’ve got a simple question. Do you collect location data in the cloud when “Significant locations” is enabled? If not, what exactly is “…data is transmitted end-to-end encrypted between your iCloud connected devices”? Can we access that data and do we have the ability to delete it from the cloud?
Significant Locations
Unlike Google who collects massive amounts information and processes it on its servers, Apple positions itself as a privacy advocate. Consecutively, the company does not deliberately store information about the user’s locations on its servers. Instead, all location data is stored on the device itself. As iOS collects enough points, it then makes assumptions about the places the user frequently visits. Since iOS rarely invokes the GPS receiver (unless a dedicated navigation app is used), these locations are estimates based on triangulation of the signal across the various cellular towers. As a result, what users get is a guesstimate of the places they’ve been to.
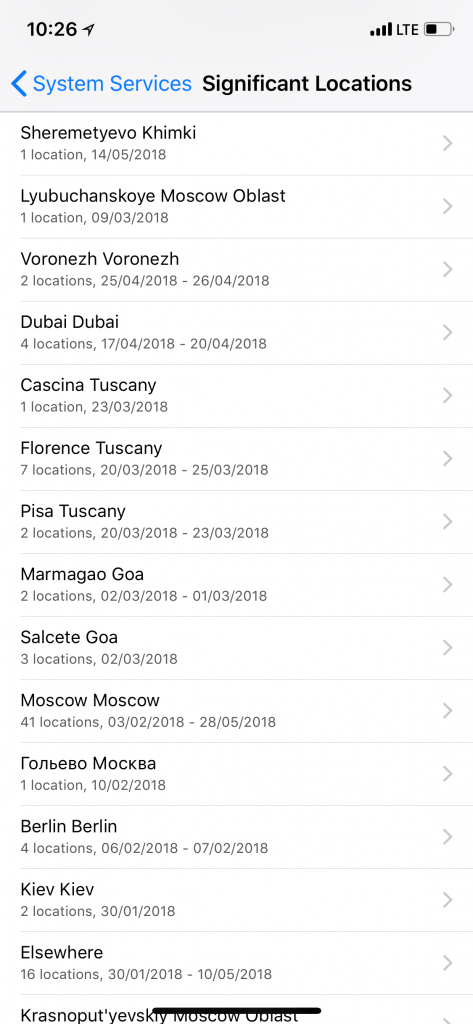
Users can access the list of Significant Locations on the device at Settings > Privacy > Location Services > System Services > Significant Locations. This is not the most obvious place to look into, so many iPhone users are completely unaware of the feature. In order to access Significant Locations, the user must enter their passcode. Once you’re there, you can see a list similar to this:

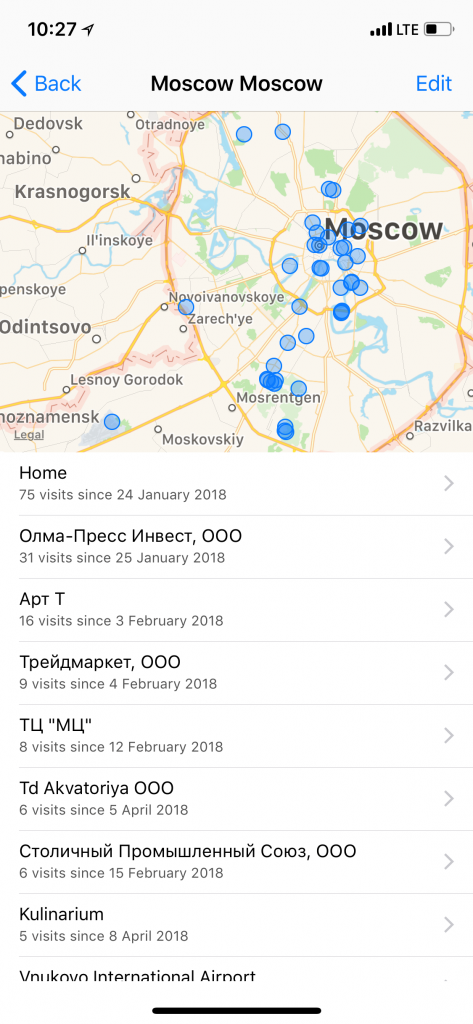
More detailed view:
Extracting and Analysing Significant Locations
Logical acquisition is the easiest way to go when analysing iOS devices. However, Significant Locations are not included with either cloud or local backups, not even in password-protected backups (they used to be, in the past, but Apple decided to remove location data from local backups following a privacy scandal). As a result, the only way to extract Significant Locations from an iPhone is via physical acquisition – such as the TAR acquisition process performed with iOS Forensic Toolkit.
The good news, however, is that you don’t have to capture and decrypt the entire data partition or use a hardware-backed key to decrypt the data. A ‘normal’ file system image (the “TAR file”) is all that you need to extract Significant Locations.
Once you’ve extracted the TAR file containing the image of the file system, Significant Locations can be found at the following path:
iOS 10 and below
- private/var/mobile/Library/Caches/com.apple.routined/StateModel1.archive
- private/var/mobile/Library/Caches/com.apple.routined/StateModel2.archive
iOS 11 and higher
- private/var/mobile/Library/Caches/com.apple.routined/Cloud.sqlite (note the “cloud” in file name!)
- private/var/mobile/Library/Caches/com.apple.routined/Local.sqlite
- private/var/mobile/Library/Caches/com.apple.routined/Cache.sqlite
By analysing these files, you’ll be able to find out which locations the user frequently visited.
These databases contain both processed (sorted/filtered) and raw location data. In addition, information such as latitude and velocity can appear. We don’t know how (and when) Apple collects these samples. However, these files are not the only databases containing location data; we’ll have a separate publication on location data later on.
Do note that Significant Locations are nothing more than guesstimates. Even if iOS suggests that a certain place (such as a business, shop or restaurant) was visited, take this with a grain of salt. Even Google makes mistakes when trying to determine the exact place you’re in; iOS uses a much, much simple algorithm and a significantly less precise, low-energy positioning mechanism when determining locations.
Conclusion
So let us sum it all up. Significant Locations show iOS best guesstimates on user’s frequent whereabouts. They can serve as valuable evidence during many types of investigations. Significant Locations are only collected when the user has Location Services enabled (or, rather, does not have them disabled). Since Significant Locations are buried deep in the user interface (Settings > Privacy > Location Services > System Services > Significant Locations) and require a passcode to access, they are little known to an average user.
Significant Locations are stored on the device, and can be extracted with file system acquisition (TAR imaging). They are not additionally encrypted.
Significant Locations are not part of cloud or local backups, even if the backup is encrypted with a password. Physical acquisition is the only way to extract this piece of evidence.






