We updated iOS Forensic Toolkit to bring two notable improvements. The first one is the new acquisition option for jailbreak-free extractions. The new extraction mode helps experts save time and disk space by pulling only the content of the user partition while leaving the static system partition behind. The second update expands jailbreak-free extraction all the way back to iOS 9, now supporting all 64-bit devices running all builds of iOS 9.
Extracting user data
In addition to the complete file system extraction, which gives you a copy of all files and folders in the user partition and also the content of the OS system partition, we are now offering a simplified extraction option. In this simplified extraction mode, iOS Forensic Toolkit will only copy parts of the file system that belong to the user data, skipping the OS system partition entirely.
Why skip the system partition during the extraction? The content of the system partition is far less relevant for the investigation compared to user data. The data in the system partition consists of read-only executable files, system libraries and other things that are required for the operating system to run. System logs? These are parts of the user data, and will be extracted along with the rest of the data when using the new simplified option.
Why would you want the system partition? If the iOS device was ever jailbroken, the content of the system partition could be modified, and you could see the traces of the jailbreak, even if the jailbreak was removed later on. Other than this, there is no point in extracting the system partition as the data does not vary across devices of the same model running the same version of iOS.
The benefits of simplified extraction? For small-capacity iPhones, the new option can speed up the extraction two to three times compared to full device extraction. Higher capacity devices offer comparatively lesser time savings, yet the user-targeted set is still easier to analyze.
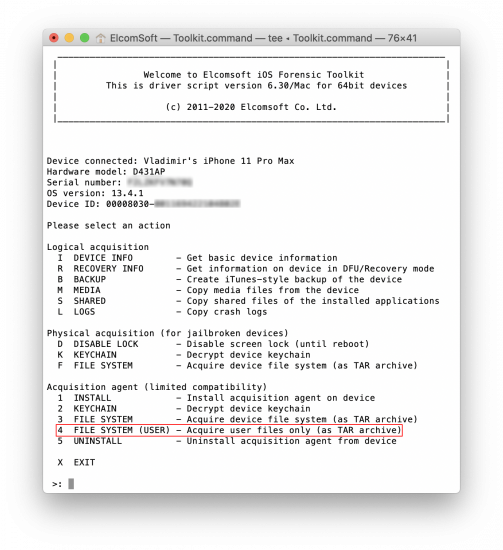
To extract user data only using agent-based extraction method:
- Press 1 to sideload the agent onto the device
- Press 2 to extract and decrypt the keychain if needed (highly recommended!)
- Press 4 to extract the file system image (user data only)
- Press 5 to remove the extraction agent from the device
iOS 9 extraction without a jailbreak
Originally released in September 2015 with the iPhone 6s and 6s Plus, iOS 9 was backported to a massive number of older devices. The 64-bit iPhone models capable of running iOS 9 range from the iPhone 5s to iPhone 6s and 6s Plus, as well as the iPhone SE (original 4-inch model). While one is hardly likely to encounter an iOS 9 device in the wild, forensic labs still have a backlog of devices running, specifically, iOS 9.3.4 and 9.3.5, the two versions of iOS 9 that lack a working jailbreak. In this iOS Forensic Toolkit update, we brought support for jailbreak-free extraction for the entire range of 64-bit devices capable of running all versions of iOS 9 up to and including iOS 9.3.5. Let’s see what it takes to extract an older iPhone without a jailbreak.
Why supporting iOS 9 in 2020?
iOS 9 was available on three SoC generations used in 64-bit devices ranging from the iPhone 5s all the way to the iPhone 6s, 6s Plus and the first model of the iPhone SE. While many users regularly update their OS, many others don’t, and some users just keep their iPhones on whatever iOS version was installed in the factory. This means a not insignificant chunk of iPhone 6s and iPhone SE devices processed in forensic labs are still running the original version of iOS 9 (or 9.3 in the case of the iPhone SE).
iOS 9 jailbreaks
Since iOS 9 is already old, there are plenty of jailbreaks for almost the entire range. However, exactly because it is that old, there are multiple caveats with many of these jailbreaks. With iOS 9 jailbreaks, there are issues with Kernel Patch Protection (KPP). The nature of public jailbreaks at the time required KPP Bypass, a technique that was used by both Pangu9 jailbreaks, Yalu+mach_portal, Yalu+extra_recipe, Yalu102, and Saïgon jailbreaks targeting the many versions of iOS. This technique was one of the reasons making iOS 9 jailbreaks less than perfectly stable, difficult and sometimes plain out dangerous to install.
Sounds bad enough? You haven’t tried installing OpenSSH on any of these jailbreaks without compromising the device by opening an Internet connection. Adding salt to injury, no public jailbreak was ever released for the two last versions of iOS 9: 9.3.4 and 9.3.5.
Using an acquisition agent removes the guesswork and risks associated with jailbreaking, making the acquisition process simple and straightforward.
Devices compatible with iOS 9
iOS 9 was supported on the following iPhone devices:
- iPhone 5S (iOS 9.0-9.3.5)
- iPhone 6 & 6 Plus (iOS 9.0-9.3.5)
- iPhone 6s & 6s Plus (iOS 9.0-9.3.5)
- iPhone SE (1st gen) (iOS 9.3-9.3.5; the iPhone SE uses the same SoC as the iPhone 6s, but was released at a later date with iOS 9.3 on board)
The following iPad models are using compatible SoC and capable of running iOS 9:
- iPad Air (iOS 9.0-9.3.5)
- iPad Air 2 (iOS 9.0-9.3.5)
- iPad Mini 2 (iOS 9.0-9.3.5)
- iPad Mini 3 (iOS 9.0-9.3.5)
- iPad Mini 4 (iOS 9.0-9.3.5)
- iPad Pro 9.7 (1st Gen) (iOS 9.3-9.3.5)
- iPad Pro 12.9 (1st Gen) (iOS 9.1-9.3.5)
As already mentioned, public jailbreaks were only available for iOS 9.0 through 9.3.3. No public jailbreaks are available for iOS 9.3.4 and 9.3.5. Elcomsoft acquisition agent supports all versions of iOS 9 including the two last versions by backporting an exploit that was discovered at a much later date.
Notably, iOS 9 was also available for the iPhone 4s (it’s the last major iOS release for this phone) and iPhone 5/5c models (these can also run iOS 10). However, instead of agent-based extraction, we are planning a much better solution for the 5 and 5c, including the passcode recovery option.
What about iOS 9.3.6? This specific version of iOS was released late in July, 2019. Only available on a handful of 32-bit hardware such as the iPhone 4S and cellular models of the iPad Mini (1st generation), iPad 2 (CDMA model), and cellular models of the iPad 3, the purpose of this release was to address an issue with GPS location performance causing the system date and time to be incorrect. Since this release is specific to old, 32-bit devices, it is not supported on newer 64-bit hardware, and, as such, is not supported in iOS Forensic Toolkit.
Prerequisites
There are no iOS 9 specific requirements to perform file system extraction or keychain decryption. You will need iOS Forensic Toolkit 6.30 or newer, and you must be able to unlock the iPhone you are extracting (the screen lock passcode must be known or empty). Note that we do not recommend removing the screen lock passcode as some information may go missing if you do so.
Similar to other cases, agent-based extraction requires the use of an Apple Developer Account. We wrote a comprehensive article about that: Why Mobile Forensic Specialists Need a Developer Account with Apple.
File System Extraction Limitations and Future Work
The recent updates had changed the compatibility table.

If you look carefully, you may notice that some systems lack the ability to extract the keychain when using jailbreak-free extraction. These include:
- iOS 12.3-12.4.8 (iPhone 5s, iPhone 6 and 6 Plus)
- iOS 13.3.1-13.4.1 (all device models capable of running these iOS builds)
For these combinations, we’ve used a very robust exploit covering most versions of iOS up to 13.4.1. However, this exploit does not provide the full capabilities of the root account, making the keychain inaccessible. In addition to the keychain, this exploit does not enable access to certain folders, most notable being the omission of the /private/var/root folder containing location data. We are working on integrating the latest exploits to decrypt the keychain and access previously locked folders in all versions of iOS including iOS 13.3.1-13.5.




