Regular or disposable Apple IDs can now be used to extract data from compatible iOS devices if you have a Mac. The use of a non-developer Apple ID carries certain risks and restrictions. In particular, one must “verify” the extraction agent on the target iPhone, which requires an active Internet connection. Learn how to verify the extraction agent signed with a regular or disposable Apple ID without the risk of receiving an accidental remote lock or remote erase command.
What’s this all about
Elcomsoft iOS Forensic Toolkit utilizes a special technique for extracting the file system and decrypting the keychain from iOS devices without a jailbreak. This technique uses an in-house app that serves as an extraction agent. While agent-based acquisition provides numerous benefits over jailbreak-based acquisition, it requires the use of an Apple account to sign the extraction agent. Using a regular (non-developer) Apple ID to sideload the agent requires the expert to “trust” the signing certificate by “verifying” the extraction app. This, in turn, requires allowing the device to connect to an Apple server.
Allowing the device being investigated connecting to the internet is risky due to potential sync issues and the probability of receiving a remove lock or remote wipe command from the Find My iPhone service. Mitigating this risk is possible by restricting on-device connectivity to a single subdomain of apple.com that is required to verify the signing certificate.
Mitigating the risks
The easiest way to avoid the risks is eliminating the need for the iPhone to check the signing certificate. If the extraction agent is signed with an Apple ID enrolled in Apple’s Developer Program, the iPhone may remain offline when you sideload the extraction agent.
The troubles arise when you don’t have a Developer Account to hand, and still need to fulfil a device extraction. Note that you can only use a non-developer Apple ID to sign the extraction agent if you are using a Mac. Windows users must use an Apple ID enrolled in the Developer Program as there is no workaround available for that platform.
To reduce the risks of exposing the iPhone device being remotely tampered with, we’ll need to restrict it’s online connectivity. Ideally, the iPhone should be only able to connect to a single certificate validation server – with all other communications being terminated.
Apple Certificate Validation Server: ppq.apple.com (17.173.66.213), port 443.
There are several ways one can achieve the goal. For some, the easier method would be configuring a dedicated Wi-Fi network and setting up a router whitelist. Others will prefer to leave the device’s radios disabled, using a pre-configured wired connection instead (with Lightning to Ethernet adapter like this one, or a cheaper alternative, or a combination of the Lightning to USB Adapter and the USB Ethernet Adapter).
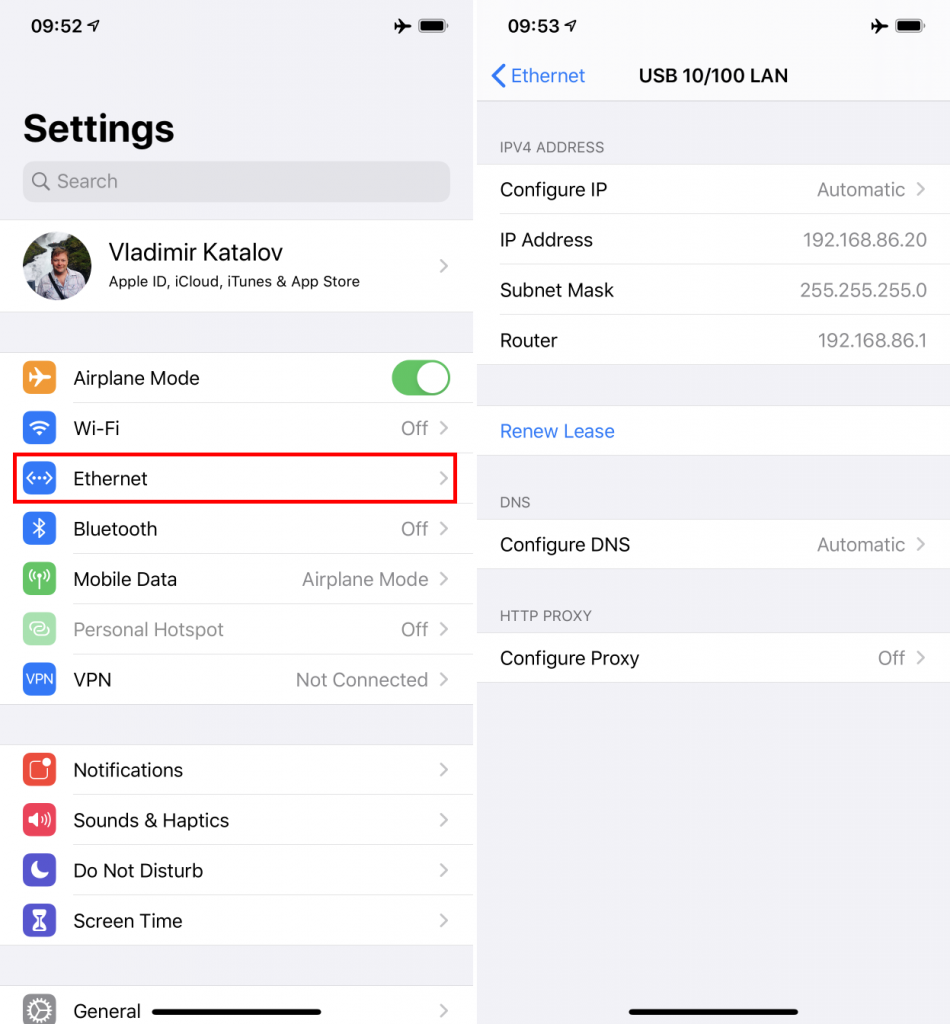
However, once you have a Mac, there is no requirement for any extra hardware, and you’ll be able to share the Internet connection from it to the iPhone, limiting access an easier way.
Step 1. Connect any iPhone (jut not the one being extracted!) to the Mac. Open [Settings] | [Shared] and make sure that Internet Sharing in “To computers using:” contains the “iPhone USB” item.
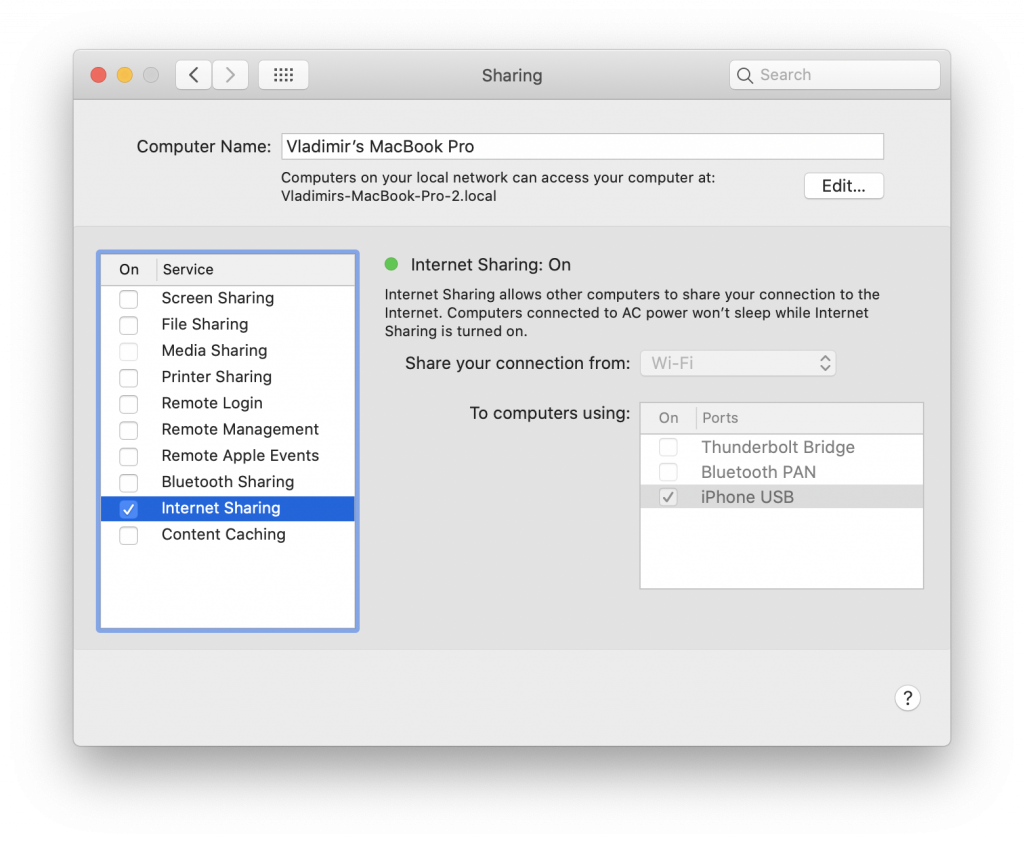
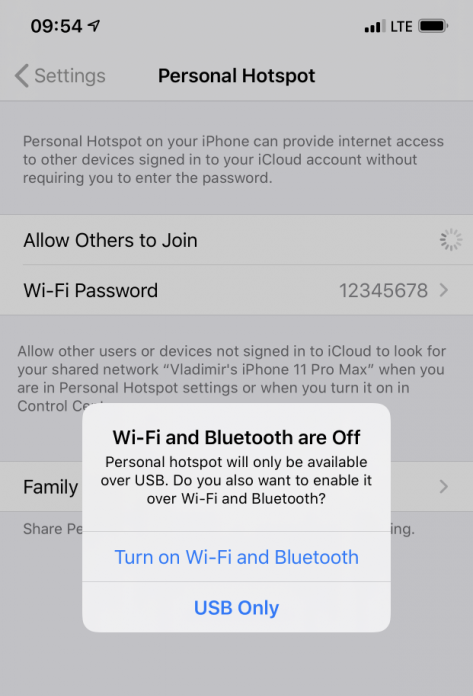
If there is no such item, temporarily enable Personal Hotspot (USB only). The item should appear. After that, you can disconnect the iPhone and disable the personal hotspot.
Step 2. Make sure that no iPhone is connected to the Mac, and activate firewall (for this specific interface only, i.e. iPhone USB), allowing access to ppq.apple.com only. That can be easily done by running our script as a root user, e.g.:
sudo ./install_firewall.sh
The content of the script is quite simple:
#!/bin/bash
cp /etc/pf.conf /etc/pf.conf.backup
echo -e "\ntable <allowed-hosts> { ppq.apple.com, 192.168.2.0/24 }" >> /etc/pf.conf
echo -e "block drop in quick on bridge100 proto tcp from any to !<allowed-hosts>" >> /etc/pf.conf
pfctl -f /etc/pf.conf
Step 3. Connect the iPhone being investigated. The agent should be already installed (if it not installed yet, you can do it at this point), and enable Internet Sharing to iPhone USB.
Step 4. Approve/verify the certificate (issued to the Apple ID you used for sideloading the agent).
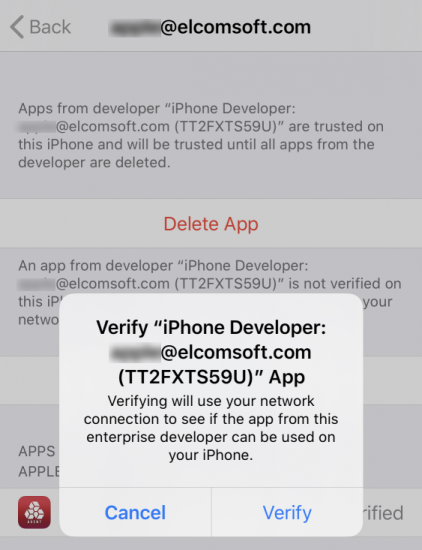
Step 5. Do the extraction with EIFT.
Step 6. You can uninstall the firewall now (and restore the original configuration, as it has been backed up at the second step) by running the second script, again as a root user:
sudo ./uninstall_firewall.sh
This script is actually even simpler:
#!/bin/bash
cp /etc/pf.conf.backup /etc/pf.conf
pfctl -f /etc/pf.conf
You can also keep the current setup for further extractions (if you ever need to install the agent onto other iPhones). From now on, any iPhone connected to this Mac (after the firewall setup) will only have access to the particular Apple server required for certificate approval; it will not sync (neither the system nor any applications) or have access to any remote lock/wipe commands.
That’s it, you can now acquire the data from the device, including the full file system and keychain; more details here: Extracting iPhone File System and Keychain Without an Apple Developer Account.






