The recent update to Elcomsoft Advanced Archive Password Recovery, our go-to tool for breaking passwords to encrypted archives, brought compatibility with RAR5 and 7Zip formats, and enabled multithreaded dictionary attacks. Which archive formats are the most secure, and which ones are the toughest to break? Read along to find out!
A Bit of History
For us, Advanced Archive Password Recovery is a product we have nostalgic feelings for. Under the name of Advanced Zip Password Recovery, it became the first password recovery tool we released back in 1997. Back then, it looked like this:
Do you remember the term “shareware”? It was all the rage in the 90’s and early 2000’s, and this had became our first shareware product, too.
It all started from breaking a ZIP archive for one of our customers. We made a command-line tool specifically for that archive and were able to brute-force the password. Several months after that, we released the first GUI version of the tool. Once we added more compression formats, we gave the tool its current name, Advanced Archive Password Recovery.
What makes Advanced Archive Password Recovery special compared to other tools? It’s the special kinds of attacks exploiting weaknesses in ZIP encryption allowing to quickly unlock encrypted archives without brute-forcing all possible password combinations. So let us talk about the ZIP encryption.
ZIP encryption
There are generally two encryption standards available for ZIP archives: Zip 2.0 (Legacy) encryption and AES encryption, which, in turn, comes in 128-bit AES and 256-bit AES strengths. WinZip has a comprehensive write-up on ZIP encryption, particularly mentioning the following:
“Legacy (Zip 2.0) encryption: this older encryption technique provides a measure of protection against casual users who do not have the password and are trying to determine the contents of the files. However, the Zip 2.0 encryption format is known to be relatively weak and cannot be expected to provide protection from individuals with access to specialized password recovery tools.”
“You should not rely on Zip 2.0 encryption to provide strong security for your data. If you have important security requirements for your data, you should instead consider using WinZip’s AES encryption, described above.”
For many years, AES has been the default encryption option in WinZip. Yet, other products largely rely on open-source components for implementing ZIP encryption. The freely reusable open-source components made ZIP compression the format of choice among Windows developers, resulting in ZIP becoming a de-facto compression standard for many users. The use of open-source components often comes with a penalty of using the legacy, extremely outdated, pre-AES encryption scheme employed in early versions of WinZip but still used today by multiple apps built with the same open-source components. As a result, we’re seeing about as many AES-encrypted ZIP archives as we do legacy-encrypted ZIP files.
How much stronger is the new AES encryption compared to the classic protection scheme? If you were using a single Xeon E5-2603 CPU, you’ll be able to try 54 million passwords per second for archives protected with ZIP classic encryption. Attacking a ZIP AES archive on the same computer will only produce some 2400 passwords per second, which is 22500 times slower. If you need a faster recovery, consider using a GPU-accelerated tool such as Elcomsoft Distributed Password Recovery. A good old NVIDIA GTX 1080 board helps attack a ZIP AES archive at the speed of 203000 passwords per second, which is roughly 85 times faster compared to using a CPU alone. If you manage to obtain one of the newer Ampere-powered boards, the recovery speeds will double.

It is the legacy ZIP encryption we are after in two major attacks allowing to break legacy ZIP encryption faster: the known plaintext attack and guaranteed recovery attack.
ZIP: known plaintext attack
The known plaintext attack enables the decryption of certain types of encrypted ZIP archives without performing a lengthy attack on the original password. Obviously, this attack is only applicable to ZIP archives protected with legacy encryption. AES-encrypted archives are immune to this attack.
The core of this attack is the requirement to have exactly at least one unencrypted file (or part of such file) matching those inside the encrypted archive. If you have a file like that, as well as a ZIP archiver using the same legacy encryption algorithm, you can use the known plaintext attack in Advanced Archive Password Recovery to quickly find the password. Notably, the attack does not need to recover the original plain-text password to decrypt the archive, although shorter passwords can be recovered quickly.
ZIP: guaranteed WinZip recovery
Back in the 1990’s and early 2000’s, WinZip (and other tools based on the then-current Info-ZIP sources) used to have a vulnerability in the random number generator. This vulnerability allowed us to build an attack that is similar to the known-plaintext attack, but does not require to have any files from the archive. The only limitation was the number of files in the archive: there must be at least 5 files in the archive to break. WinZip patched this CVE in version 8.1 released in August 2001.
This attack can break about 99.6% of supported ZIP archives created with a vulnerable version of WinZip, or 255 out of 256 archives.
Note that AES-encrypted ZIP archives never had this vulnerability, or any other known vulnerabilities if that matters.
RAR5 and 7Zip Archives
Neither RAR nor 7Zip formats have any known vulnerabilities when it comes to encryption. For these formats, one is stuck to trial and error with brute-force and dictionary attacks.
While both RAR and 7Zip employ AES encryption to protect the archives, the implementations of password protection are different. More interestingly, the implementation of password protection differs greatly between the ‘old’ and ‘new’ RAR formats (RAR4 and RAR5 correspondingly).
RAR4 encryption
In the RAR4 format, WinRAR employed AES encryption with 128-bit or 256-bit encryption keys. However, the archiver had never checked a password at all when the user attempted to deflate an encrypted archive. Instead, it simply performed the decryption, and only checked the checksum in the end, once the file was fully processed. This made attacks painfully slow: one had to decrypt the whole file to find out whether the password matched or not. For archives containing large files, the attacks were particularly struggling.
RAR5 difference
The development of the new RAR5 format had moved things in a different direction. WinRAR now stores a password hash within the compressed archive, checking the password before attempting the extraction. The design goal was speeding up the extraction. The developers mentioned that the chosen hash function was intentionally slow and based on PBKDF2 to slow down the attacks. However, this is still much faster and mush easier than extracting a file and calculating the checksum the way it was done in the RAR4 format. In the end, we’ve been able to build an attack that works significantly faster on the new RAR5 format compared to the older RAR4.
7Zip encryption
According to 7-zip.org, 7Zip encrypts files with AES-256 algorithm in CBC mode. The encryption key is derived using 524288 (2^19^) iterations of the SHA-256 hash algorithm. Interestingly, 7Zip does not currently use salt to further strengthen security of its archives, which seems like a big omission to us.
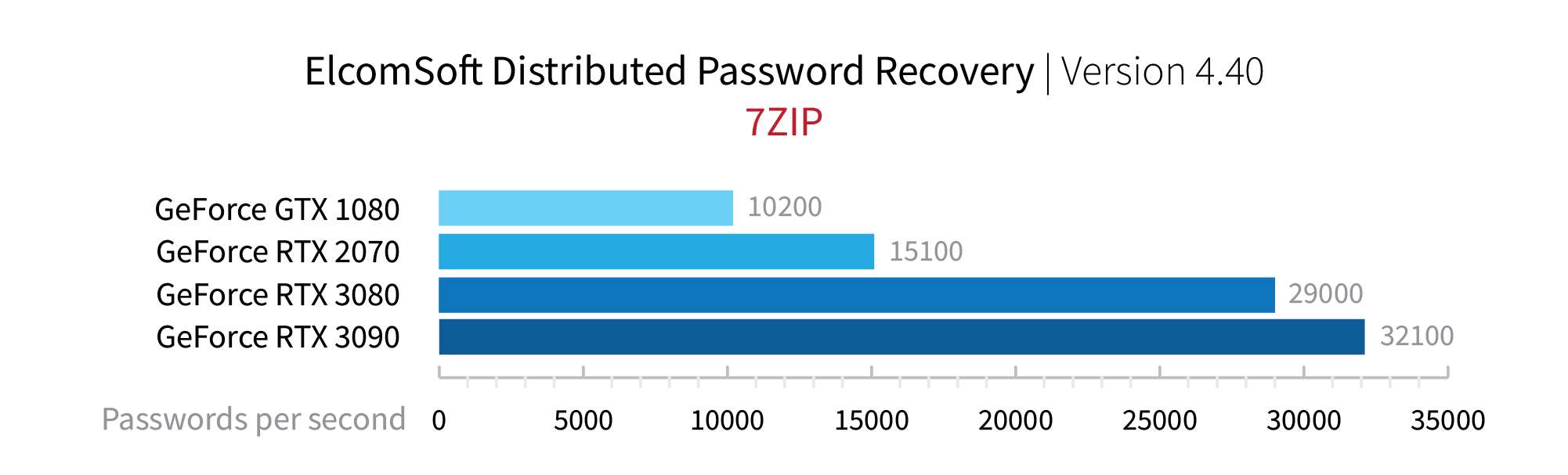
What about the speed? While I don’t have benchmarks for Advanced Archive Password Recovery, I have the numbers for Elcomsoft Distributed Password Recovery, a (much) faster and (vastly) more expensive tool in our arsenal. For 7Zip, we have the following numbers:
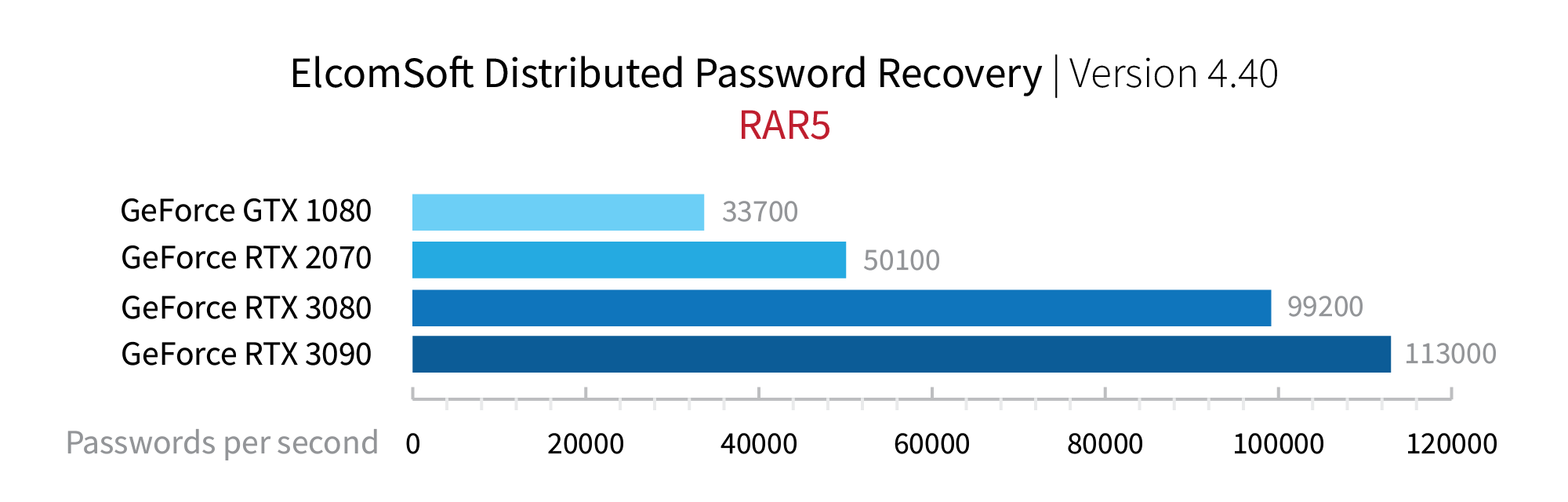
For RAR5, the numbers are higher. In fact, RAR5 archives can be attacked about three times faster than 7Zip archives: