It’s been 10 years since we have released one of our flagship products, Elcomsoft Phone Breaker. The first version appeared in April 2011, and was named “iPhone Password Breaker”. Since then, we made tons of improvements. The tool lost the “iPhone” designation, and the “Password” part was dropped from its name because it was no longer limited to iPhones or passwords. Today, the tool can offer unmatched features for the mobile forensic specialists.
The initial release was quite simple with its one and only feature: breaking passwords of iOS backups created with iTunes. At that time, we already had over 20 password recovery products for more than two hundred different file formats and algorithms, but iTunes backups are something very special; The Most Unusual Things about iPhone Backups has more details. This tool was actually our first mobile forensics product that marked the beginning of our long journey in the mobile and cloud forensics.
The new tool enables forensic access to password-protected backups for iPhone 2G, 3G, 3GS, and iPod Touch 1st, 2nd, and 3rd Gen. Elcomsoft iPhone Password Breaker performs customizable wordlist-based attacks. The tool supports multi-core CPUs, extended CPU instructions, and acceleration with NVIDIA video cards (ATI support coming soon). Recover the original plain-text password to encrypted backups containing address books, call logs, SMS archives, calendars, camera snapshots, voice mail and email account settings, applications, Web browsing history and cache. (source: ElcomSoft news)
Why iPhone backups are so important? They contain most of the content of the device. Accessing a backup was be the only way to get the data when the device is broken, lost, erased, locked after 10 unsuccessful attempts and so on (remember, there was no iCloud at the time).
Just a few months later, we added an exciting feature, giving experts the ability to decrypting the iOS keychain. At the time, that was a real breakthrough.
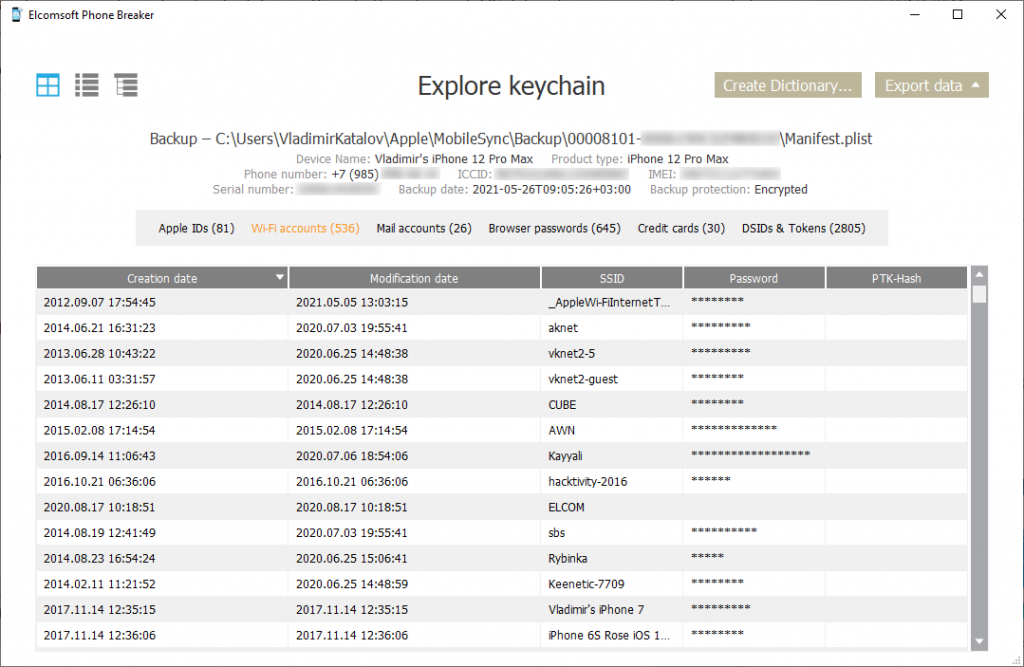
In Apple iPhone devices, passwords to email accounts, Web sites, and certain third-party software are stored securely in keychains that are encrypted with hardware keys unique to each individual device. Prior to the release of iOS 4, keychains remained encrypted with a device-specific key even when exported to an off-line backup file. With iOS 4 this is not necessarily the case.
With the release of Apple’s new OS, iOS 4, the keychains can now be stored in device backups encrypted only with backup’s master password. Knowing the password protecting the off-line backup, it is now possible to gain access to encrypted keychains. (source: ElcomSoft news)
I do not think I need to explain why the keychain is so important with all the passwords and account authentication data it contains.
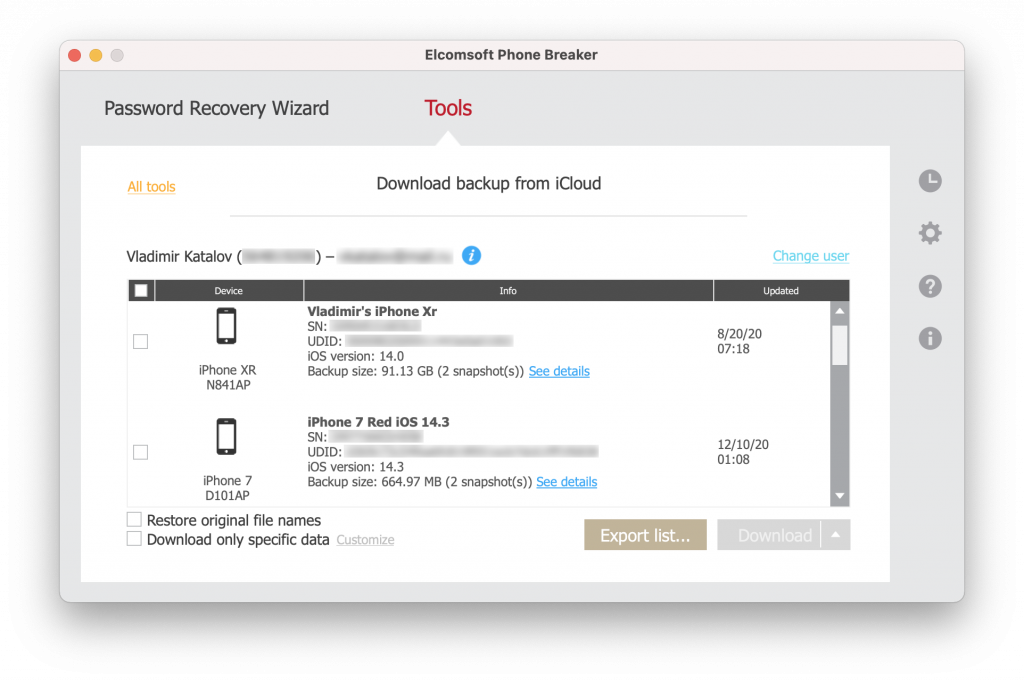
In May 2012, we made another breakthrough: downloading iCloud backups! Nobody did that before. I can say that it was extremely difficult to break into iCloud. We had to jailbreak the phone, sniff the traffic while restoring from a cloud backup, learn the iCloud protocol (of course, undocumented), and get the knowledge of how the data is stored and encrypted to learn how to decrypt everything, then compile the complete backup from the parts. That was an exciting challenge worth another blog article.
ElcomSoft Co. Ltd. discovers yet another way to access information stored in Apple iOS devices by retrieving online backups from Apple iCloud storage. The company updates Elcomsoft Phone Password Breaker, a tool to retrieve user content from password-protected backups created by Apple iOS devices and BlackBerry smartphones, with the ability to retrieve iPhones’ user data from iCloud. No lengthy attacks and no physical access to an iPhone device are required: the data is downloaded directly onto investigators’ computers from Apple remote storage facilities in plain, unencrypted form. Backups to multiple devices registered with the same Apple ID can be effortlessly retrieved. Investigators need to know user’s original Apple ID and password in order to gain access to online backups. (source: ElcomSoft news)
The reaction from the community was… mixed. While some people said “hey, anybody can access the iCloud having the credentials in hands”, the others complained “these pesky Russians broke Apple” (neither is true, actually).
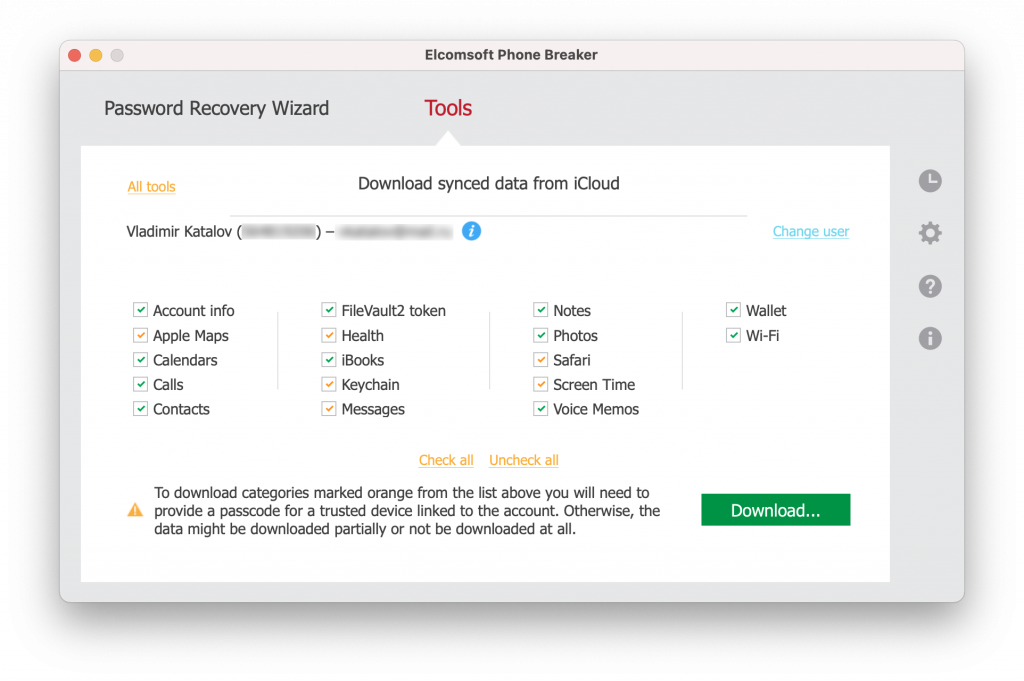
The era of cloud forensics had begun. Even today, Elcomsoft Phone Breaker remains the only product on the forensic market that is able to get the full set of data from Apple iCloud. This includes the backups, synced data (including “end-to-end” encrypted Messages, Health and more, which is unavailable even directly from Apple via Law Enforcement Requests), and third-party app data from iCloud Drive (inaccessible by other means).
Anything else about Phone Breaker worth mentioning? It’s a lot. We discovered a way to break BlackBerry devices using encrypted media cards, and we learned how to decrypt BB 10 backups (the key was stored in the BlackBerry ‘cloud’). We implemented 1Password master password recovery for databases extracted from the device itself or from iCloud. We added Windows Phone support, and we can extract lots of data from Microsoft accounts, from contacts to Skype conversations and Edge browsing history. We added a feature to access iCloud without the password using authentications tokens. All iPhone and iPad models are supported, as well as all iOS/iPad versions down to the latest iOS beta, with all 2FA methods (SMS, push messages and offline codes generated on the device); no extra hardware or spare iPhone devices are needed. And there is more to come.