How do you extract an Apple Watch? While several extraction methods are available, you need an adapter if you want to get the data directly from the device. There are several different options available on the market, some of them costing north of $200. We tested a large number of such adapters. How do they stand to the marketing claims? In this article, I will share my experience with these adapters.
I will not discuss the extraction methods in this article, but only talk about the hardware parts. In many cases, you can obtain the data collected by the Apple Watch from iCloud. In this case, the data will be limited to Apple Health; and even though Health data is “end to end encrypted”, one can still obtain and decrypt it with Elcomsoft Phone Breaker. Alternatively, a limited amount of information can be extracted from the iPhone the Watch is paired with, or, more precisely, from its backups or via low-level extraction of the iPhone. In order to be able to acquire the data directly from the Apple Watch, one needs connecting to the hidden service and diagnostics port hidden under the Watch band, and here is where the adapter is absolutely necessary.
It all started with IBUS, an adapter for the original Apple Watch (sometimes referred as S0) and Series 1 Watch (S1):

A similar model became available for the S2/S3 models a bit later. Personally, I do not really like these ones: they are relatively cheap, but they do not work well. You’ll see what I mean when you try establishing a reliable connection.
I’s been a long time since the Apple Watch Series 4 release until the S4+ version of the adapter became available. I sourced as many as three, all from different providers, but none of them worked. At around the same time, we have also discovered a new adapters for the S0/S1 and S2/S3 generation watches. This one was slightly more expensive but of a much better quality. In fact, it looks like it might be a copy of the original adapter that was used by Apple itself. Check out Apple Watch Forensics Reloaded for more details.
I was trying to find an adapter that would work with S4 and newer watches, and finally received one. The renders on the seller’s page were really nice; the reality is a bit worse:
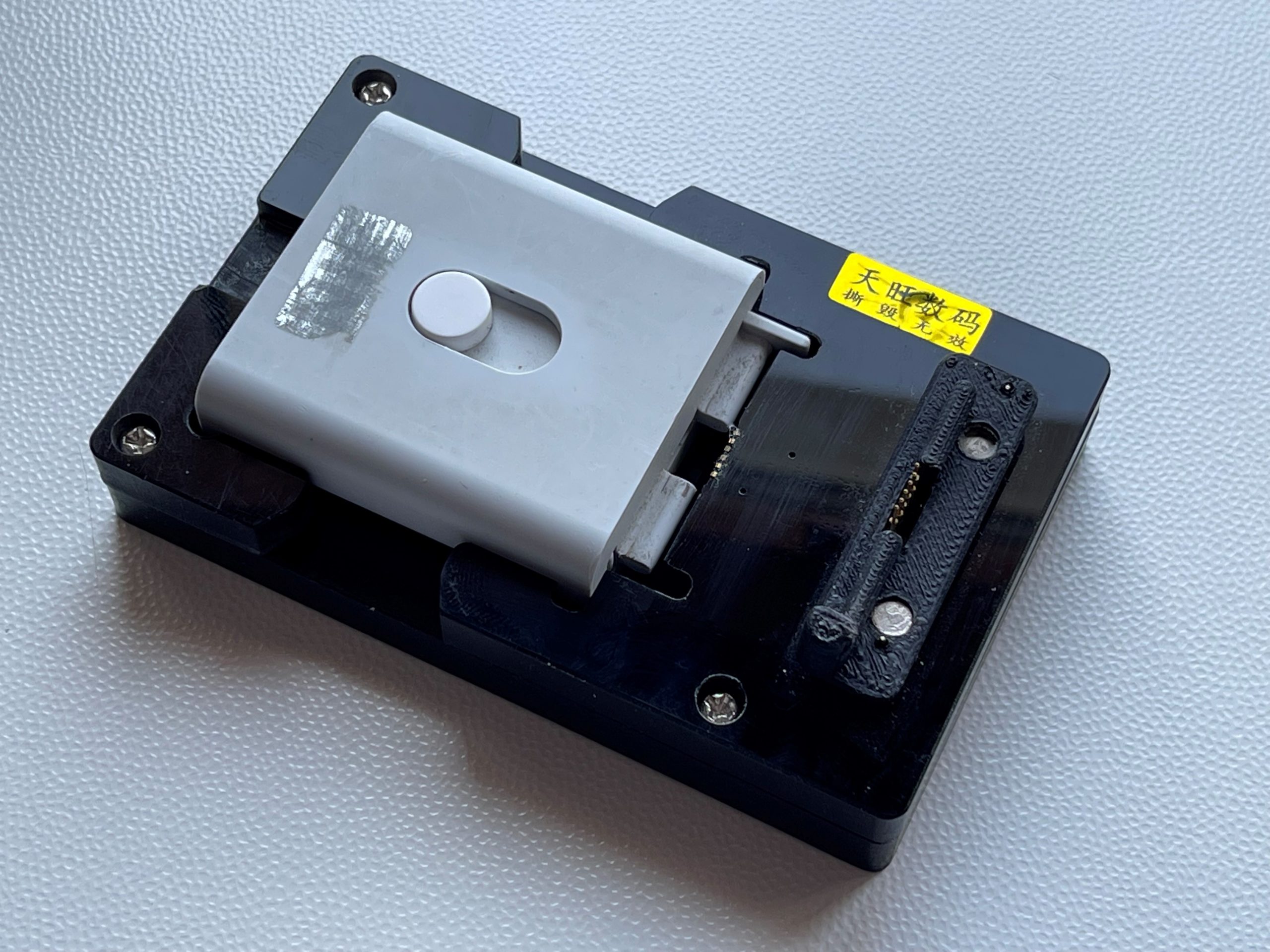
Let’s have a closer look:
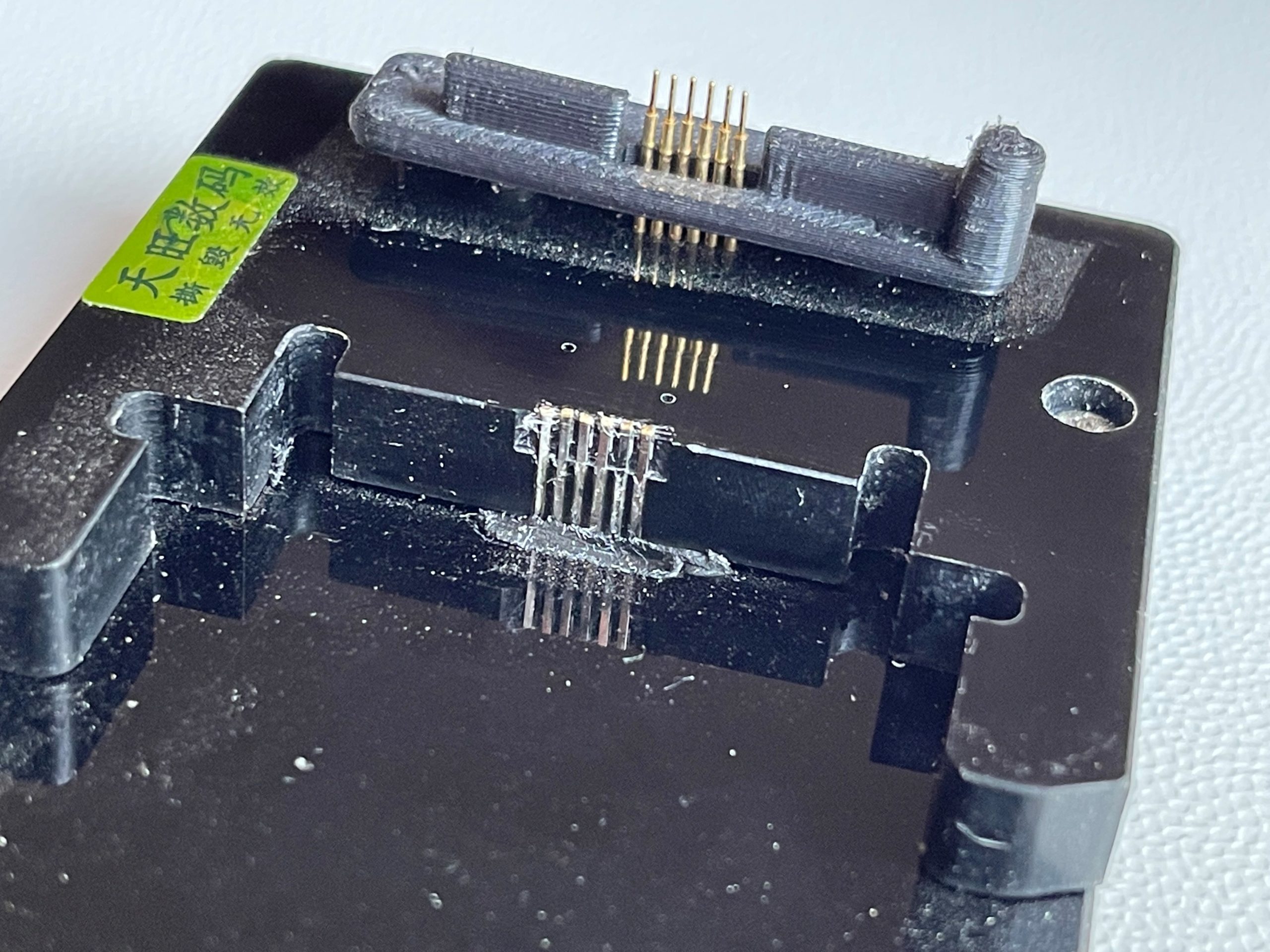
I had to clean the contacts thoroughly before it even worked, but anyway, the result is what really matters, right?
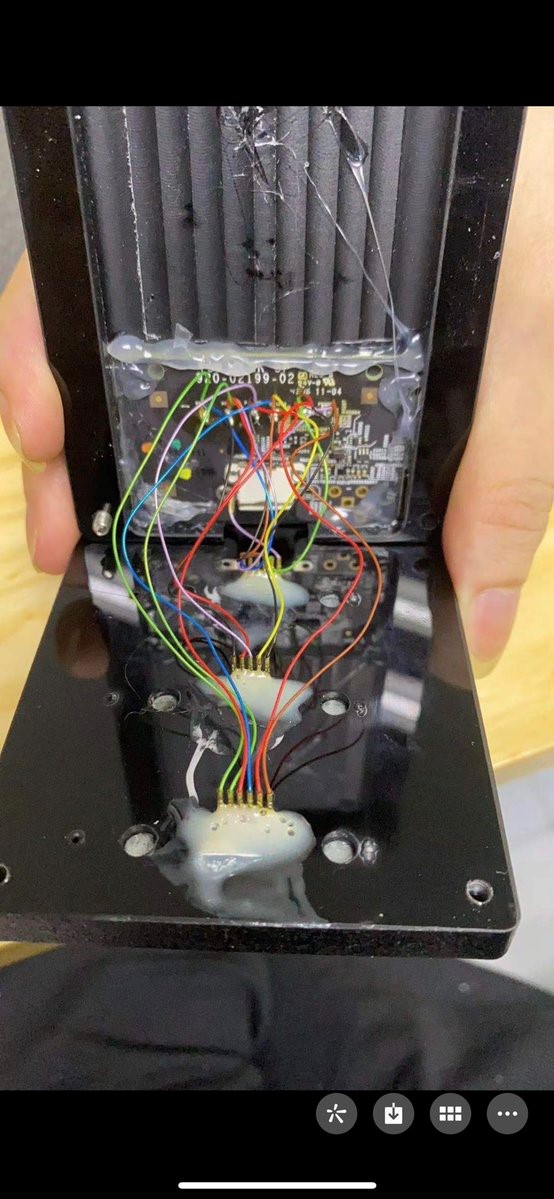
Once I tweeted about it, one of my readers replied with a picture of how it looks from the inside when disassembled:
Currently, the “second version” of this adapter is available, and it looks more convenient compared to the original:

I don’t think I want to try it out.
A completely new universal adapter was recently released under the name of MagicAWRT. The provider claims support for all generations of the Apple Watch including S0, S1, S2, S3, S4, S5, S6, and SE. I ordered one immediately; hope it is going to work as good as it looks:

While the new toy is on its way from China (I am going to test it as soon as it arrives), I was able to find another interesting adapter for S4/S5/S6/SE series:


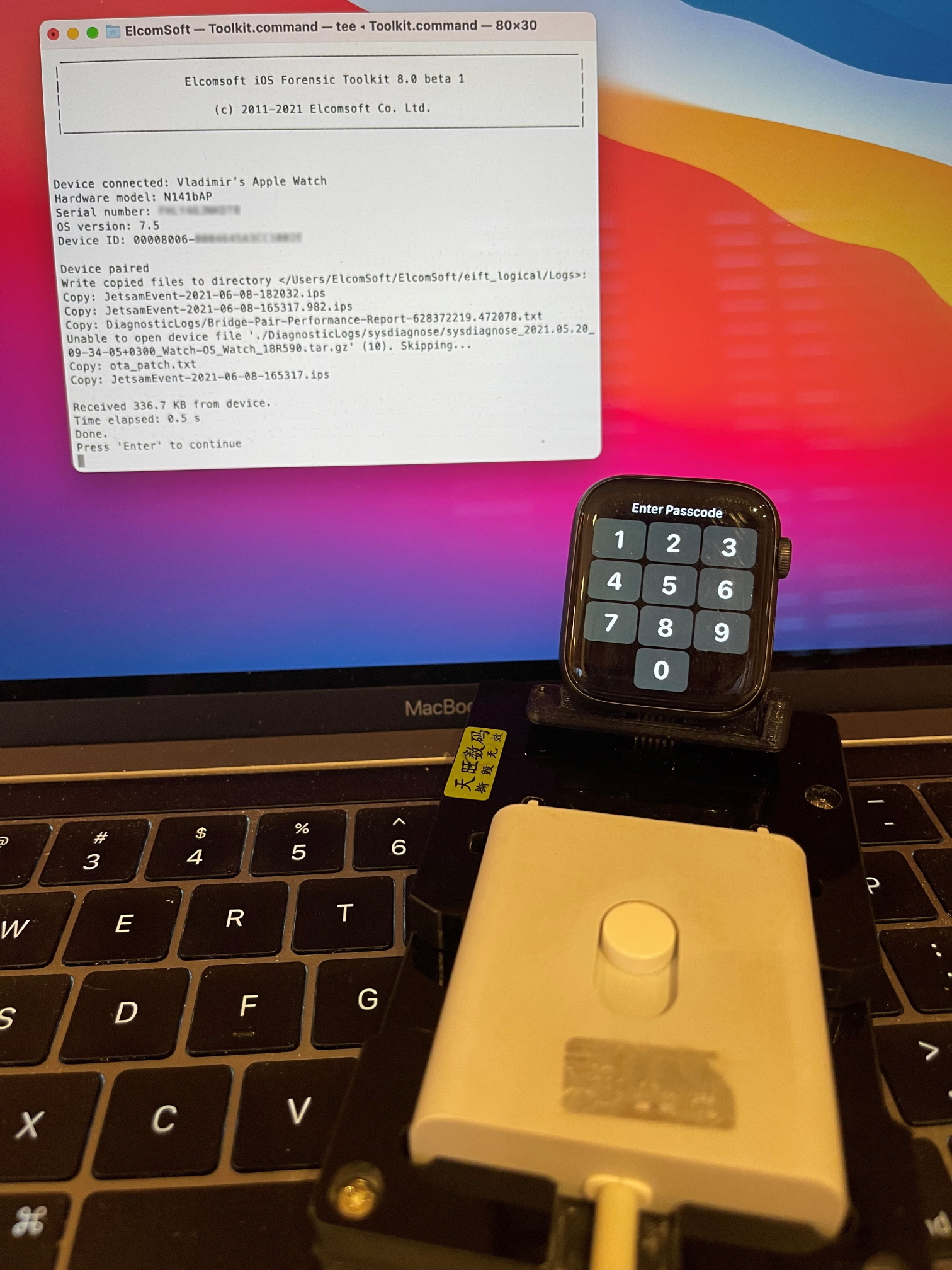
It’s difficult to say whether it this is an authentic Apple adapter or a good copy, but it works like a charm with Elcomsoft iOS Forensic Toolkit:
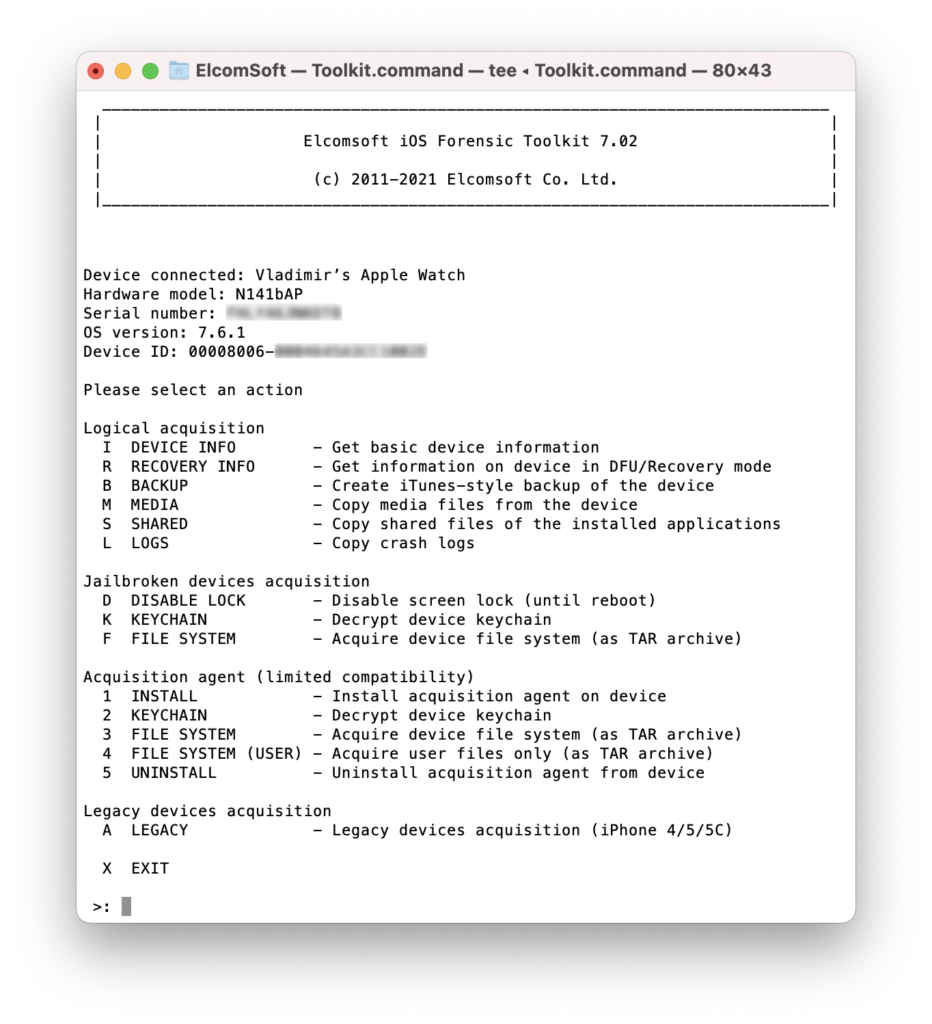
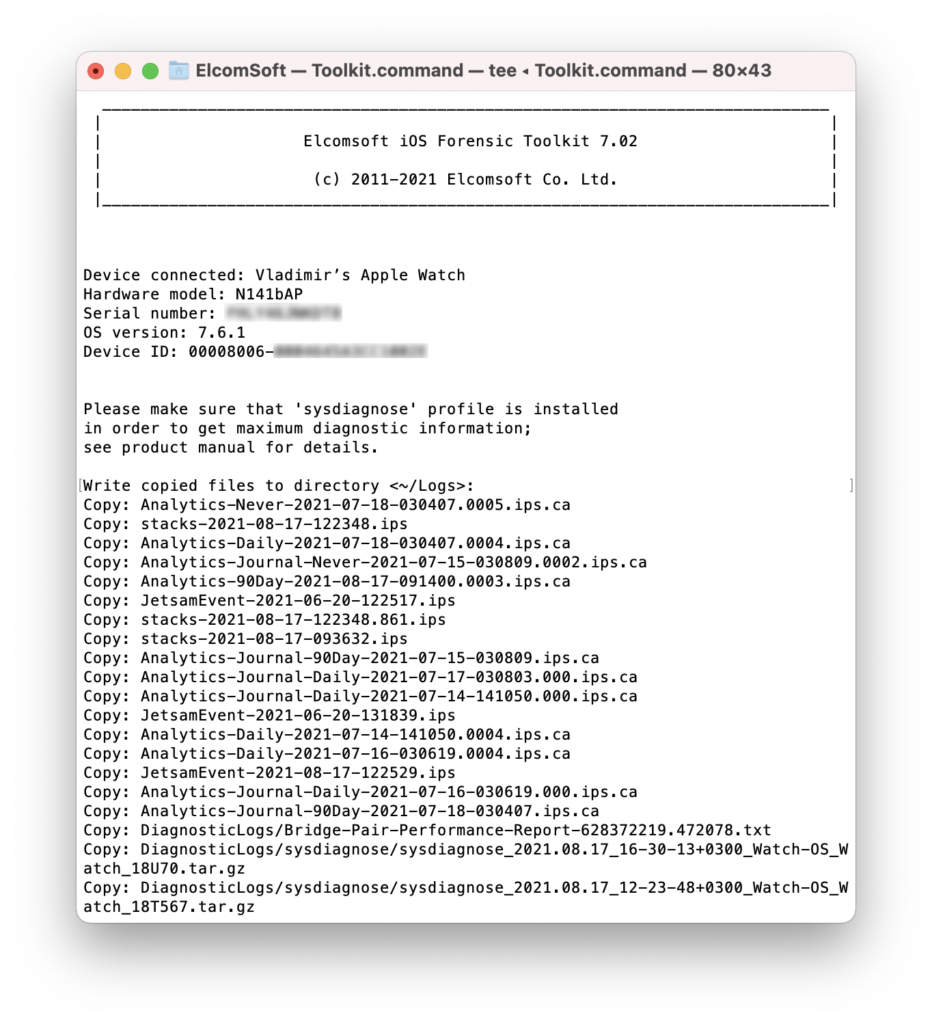
Before you begin, make sure to install the sysdiagnose profile. After that, press and hold both buttons on the Watch for 2 seconds. A few minutes after, a large .tar.gz archive will be created with lots and lots of valuable data. If you fail to install the profile or press the two buttons, you can still do the extraction, but EIFT will only extract a very limited set of largely uninteresting data.
Steps to extract the logs:
- Install sysdiagnose profile (this is how).
- Press and hold both Watch buttons for 2 seconds.
- Wait a few minutes, then extract diagnostic logs.
 Happy Apple Watch forensics!
Happy Apple Watch forensics!













