Is it possible to extract any data from an Apple Watch? It’s relatively easy if you have access to the iPhone the device is paired to, or if you have a backup of that iPhone. But what if the watch is all you have? If there is no paired iPhone, no backup and no iCloud credentials, how can you connect the Apple Watch to the computer, and can you backup the watch?
As you might know, all models of Apple Watch all models have a hidden service and diagnostics port. The port exposes the Lightning interface; for more information, check Apple Watch Teardown. The multiple extraction methods available for older versions of the Apple Watch (up to and including Series 3) are covered in the following articles:
The Series 3 is a popular model, but now we have the Apple Watch 4 and 5, the SE, and the new Apple Watch 6. The old connectors are not compatible with the new models, and that is the first problem you will encounter when attempting to extract the Watch.
In our previous research, we used iBUS adapters. There is the one for the S1 series, and another one for S2/S3 series. Recently, a new model for the S4/S5 has been introduced, and we purchased one, but…

Connecting older adapters to the S1, S2 and S3 series was a huge hassle. The attachment is not fixed to the watch, and even if you manage to establish a connection, it can be interrupted at any time. As for the S4 and S5, whatever we did, the new adapters simply failed to connect. At this time, we cannot recommend iBUS adapters for use in regular forensic work.
Recently we stumbled upon a different kind of adapters sold by JinStore. These are currently available for S1 through S3 devices only, and they don’t have the fancy aluminum look, featuring unpainted industrial plastic on the outside. They looked much more reliable, and bingo! They worked flawlessly from the first try, and the connection is very reliable. Highly recommended! The store also has an adapter for the Apple TV 4K (we covered it in Jailbreaking Apple TV 4K article), and it also looks solid and works perfectly.

Once the Apple Watch is connected, Finder immediately recognizes it:
The Watch prompts for pairing:

It’s time to use Elcomsoft iOS Forensic Toolkit!
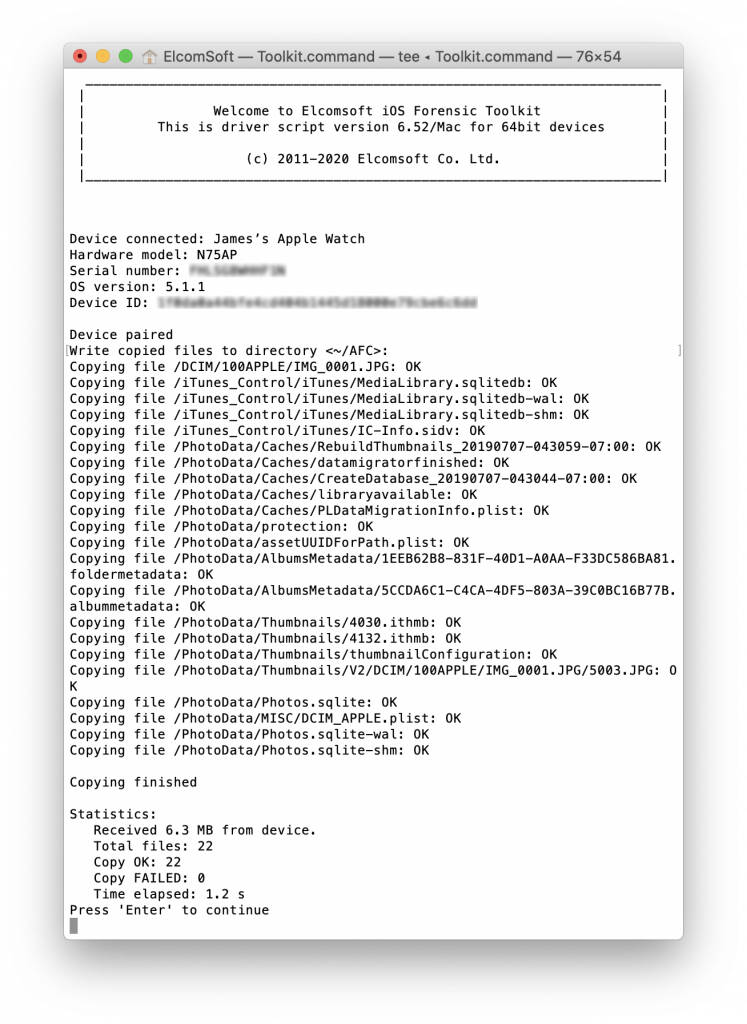
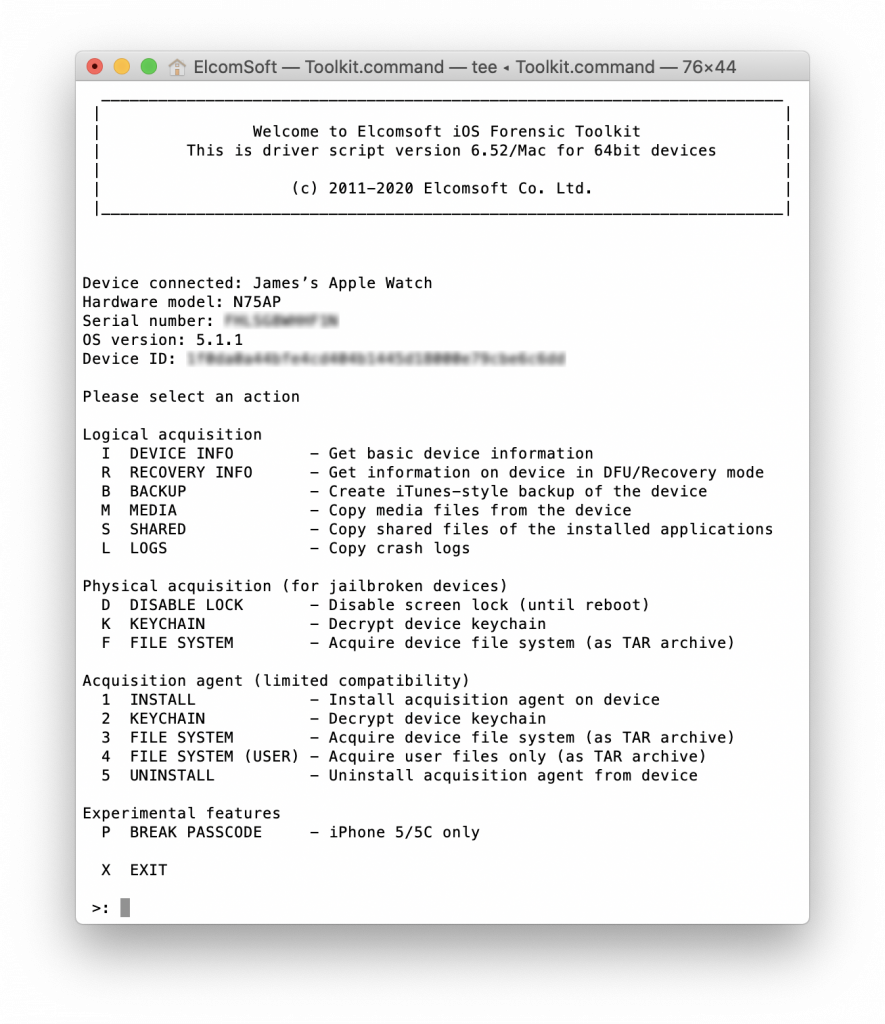 For Apple Watch, acquisition options are very limited; only logical acquisition is partially available. We first obtained the detailed device info:
For Apple Watch, acquisition options are very limited; only logical acquisition is partially available. We first obtained the detailed device info:
The list of installed apps is also extracted, along with detailed information about each app:

Then we proceeded to media files. There are usually a few media files here and there (also, they are resized). However, they contain EXIF data, which includes location tags. Metadata is also available, and sometimes it may contain additional information such as some info on deleted photos, album information, more locations (in well-known ZGENERICASSET table) etc.
 The diagnostics logs:
The diagnostics logs:
 Below is the list of files we’ve extracted from the Apple Watch:
Below is the list of files we’ve extracted from the Apple Watch:
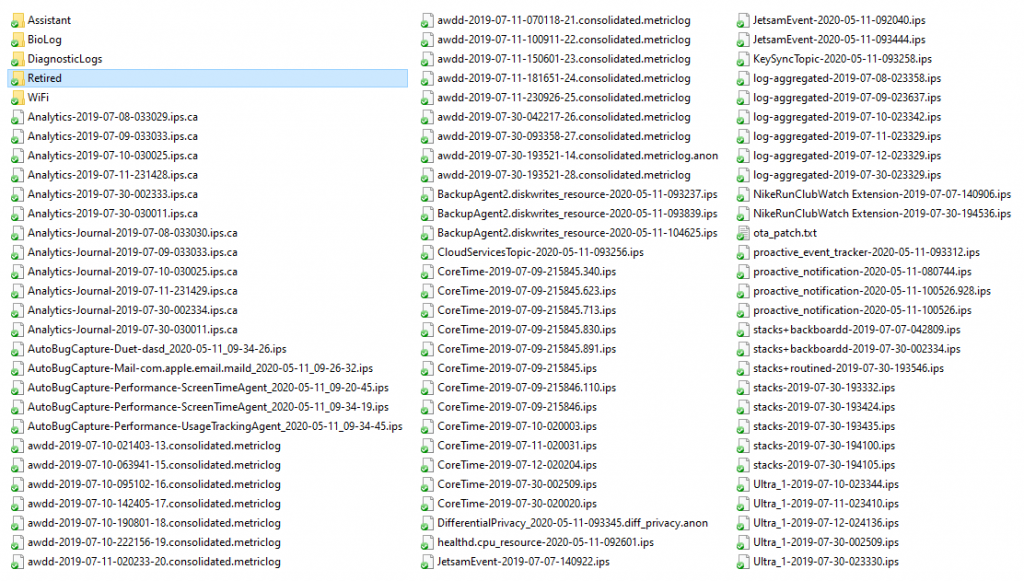
For some reason, forensic specialists rarely analyze the logs; we strongly recommend using iOS sysdiagnose forensic scripts for that purpose.















