While the iPhone is Apple’s bread and butter product, is not the only device produced by the company. We’ve got the Mac (in desktop and laptop variations), the complete range of tablets (the iPad line, which is arguably the best tablet range on the market), the music device (HomePod), the wearable (Apple Watch), and the Apple TV. In today’s article, we are going to cover data extraction from Apple TV and Apple Watch. They do contain tons of valuable data, and are often the only source of evidence.
Acquisition Methods
Generally speaking, there are only three data extraction methods available for the range of Apple devices. Logical extraction (the backup, media files, shared files, crash logs and diagnostic logs) is the most straightforward, albeit somewhat limited method. File system acquisition, while being available for some specific devices and OS versions is the most difficult yet the most advanced method. Cloud acquisition with access to information backed up or synced from all devices sharing the same Apple ID is great, but requires the correct login credentials. Each of these methods produces a different set of data that partly overlap, so we recommend using all of them if you can. Speaking of Apple Watch and Apple TV, the same rules apply.
Apple TV
There are two versions of Apple TV we’ll be discussing here: the Apple TV 4 (recently rebranded Apple TV HD) and Apple TV 4K, the company’s latest effort. From our standpoint, the major difference between the two device is the USB port. While the Apple TV 4 (Apple TV HD) offers a USB Type-C port on the back, the newer Apple TV 4K lacks USB connectivity. The lack of USB connectivity on the newer device requires using specific hardware (a macOS-based PC or laptop) and software (Xcode) to connect.
Apple TV acquisition is somewhat similar to the iPhone except just one thing: there is no backup service on Apple TV. This in turn means that logical acquisition is limited to extracting media files acquisition via the afc protocol. This could be quite a lot as most Apple TV units have iCloud Photos enabled.
There are also good news. First, the Apple TV cannot be protected with a passcode, and there is no need to pair it with a computer in order to extract data. Second, jailbreaks exist for many versions of tvOS, meaning you can capture an image of the file system and decrypt the keychain.
Before you install a jailbreak, make sure to use other such as extracting media files (Photos.sqlite can be pretty useful, as it may contain some information on files that are NOT on that Apple TV):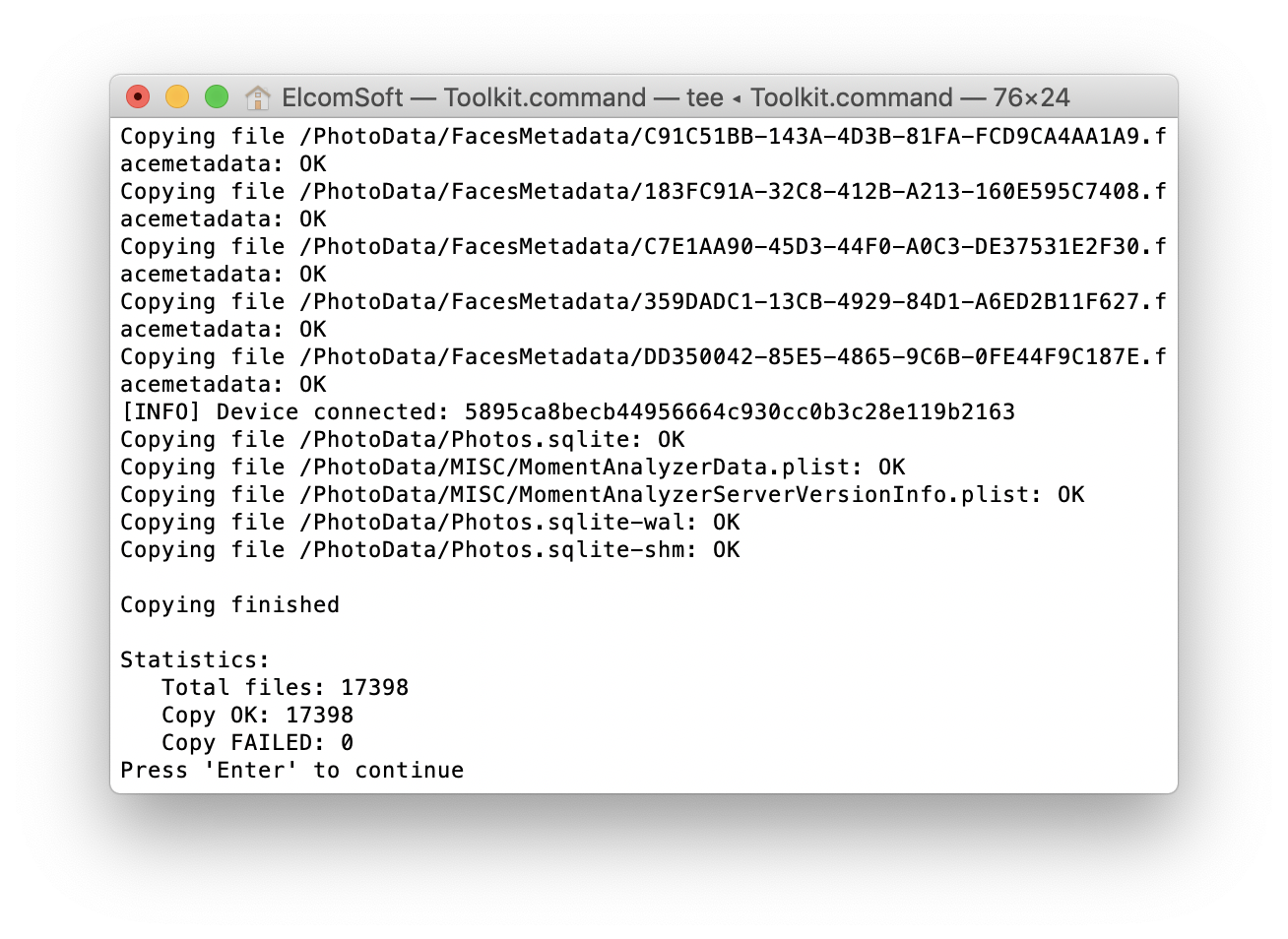 What about the Apple TV jailbreak? You have a choice of at least the following tools covering tvOS 10 through 12.1.1:
What about the Apple TV jailbreak? You have a choice of at least the following tools covering tvOS 10 through 12.1.1:
ChimeraTV
tvOS 12.0 – 12.1.1
https://chimera.sh/
LiberTV
tvOS 10.0-10.1, 11.0, 11.1
http://newosxbook.com/libertv/
Electra
tvOS 11.0-11.4.1
https://coolstar.org/electra/
The installation is similar to the process of jailbreaking iOS devices. Assuming your Apple TV runs tvOS 12.0 through 12.1.1, first download Cydia Impactor and ChimeraTV. Connect your Apple TV 4 to your computer via a USB Type-C cable (or use a Mac and Xcode to establish a wireless connection to your Apple TV 4K), sideload the IPA file (signing it with a developer’s certificate, if possible), and run the Chimera app from the main Apple TV screen:

At this point, your Apple TV has an SSH connection up and running, and full root access is provided:

Now you can easily capture the image of the file system with Elcomsoft iOS Forensic Toolkit: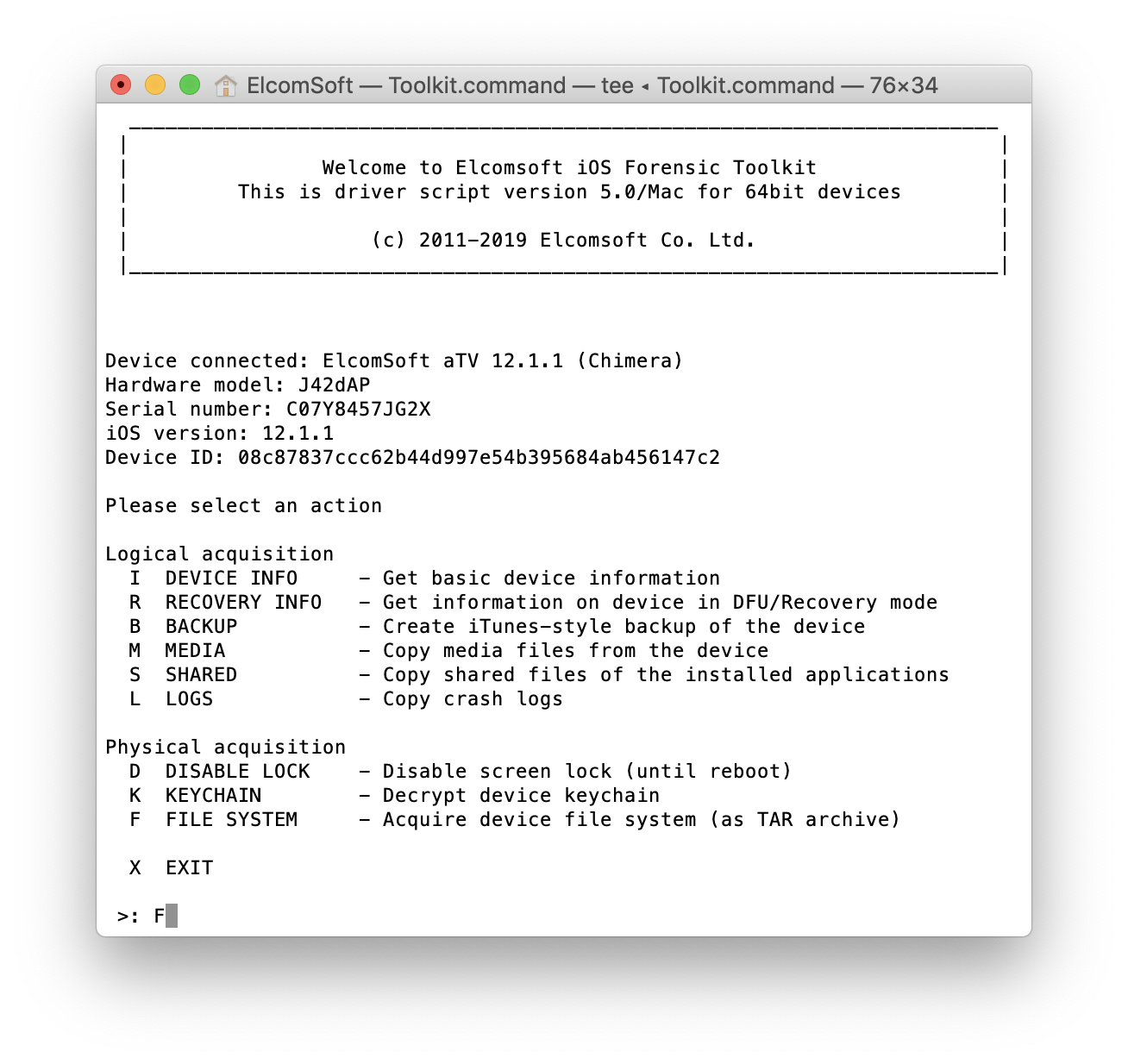 You can even access the keychain (even if it is not as comprehensive as on iOS devices, but often contains iCloud token, or at least the password to W-Fi networks, as well as some other ones):
You can even access the keychain (even if it is not as comprehensive as on iOS devices, but often contains iCloud token, or at least the password to W-Fi networks, as well as some other ones):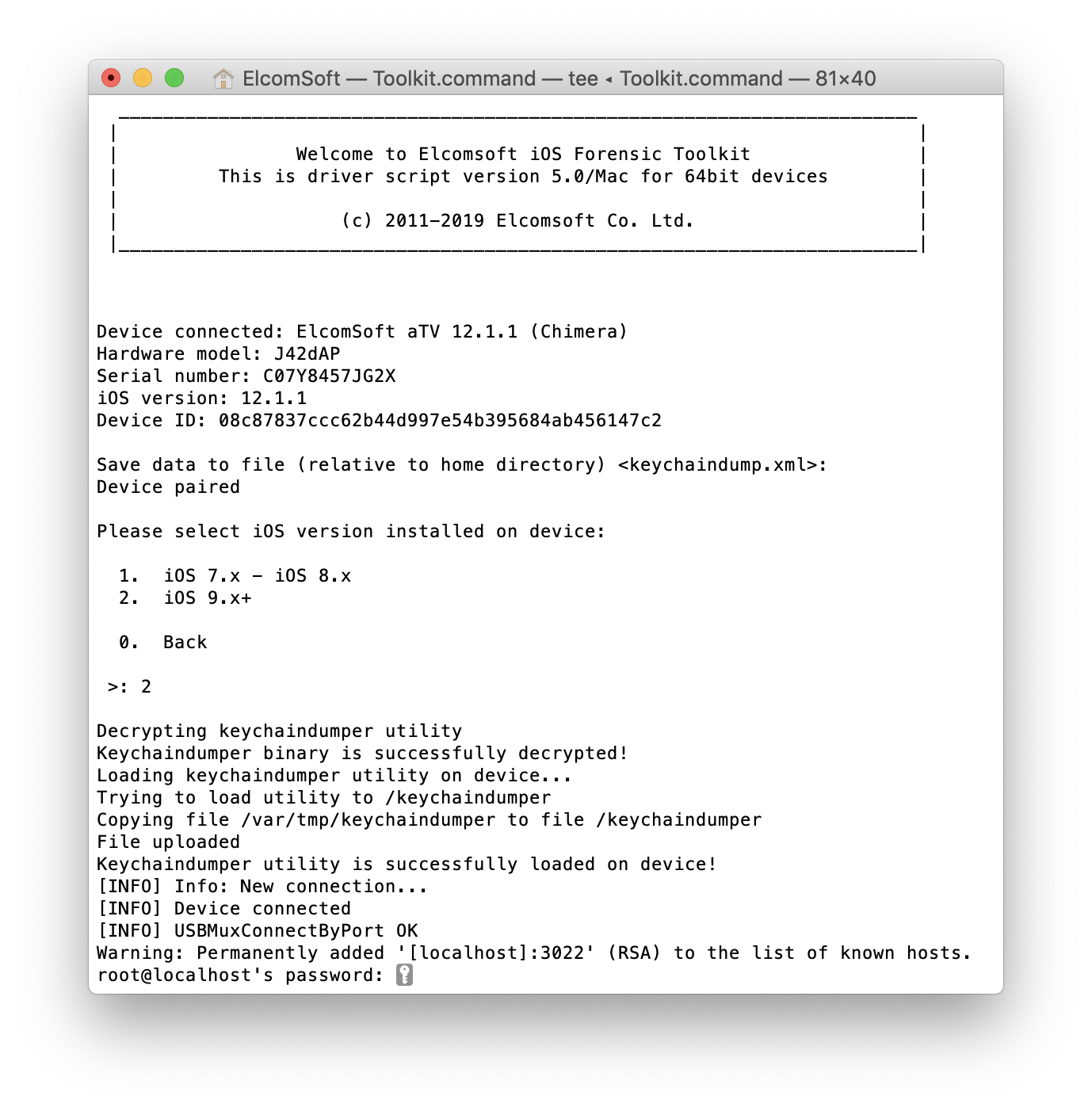
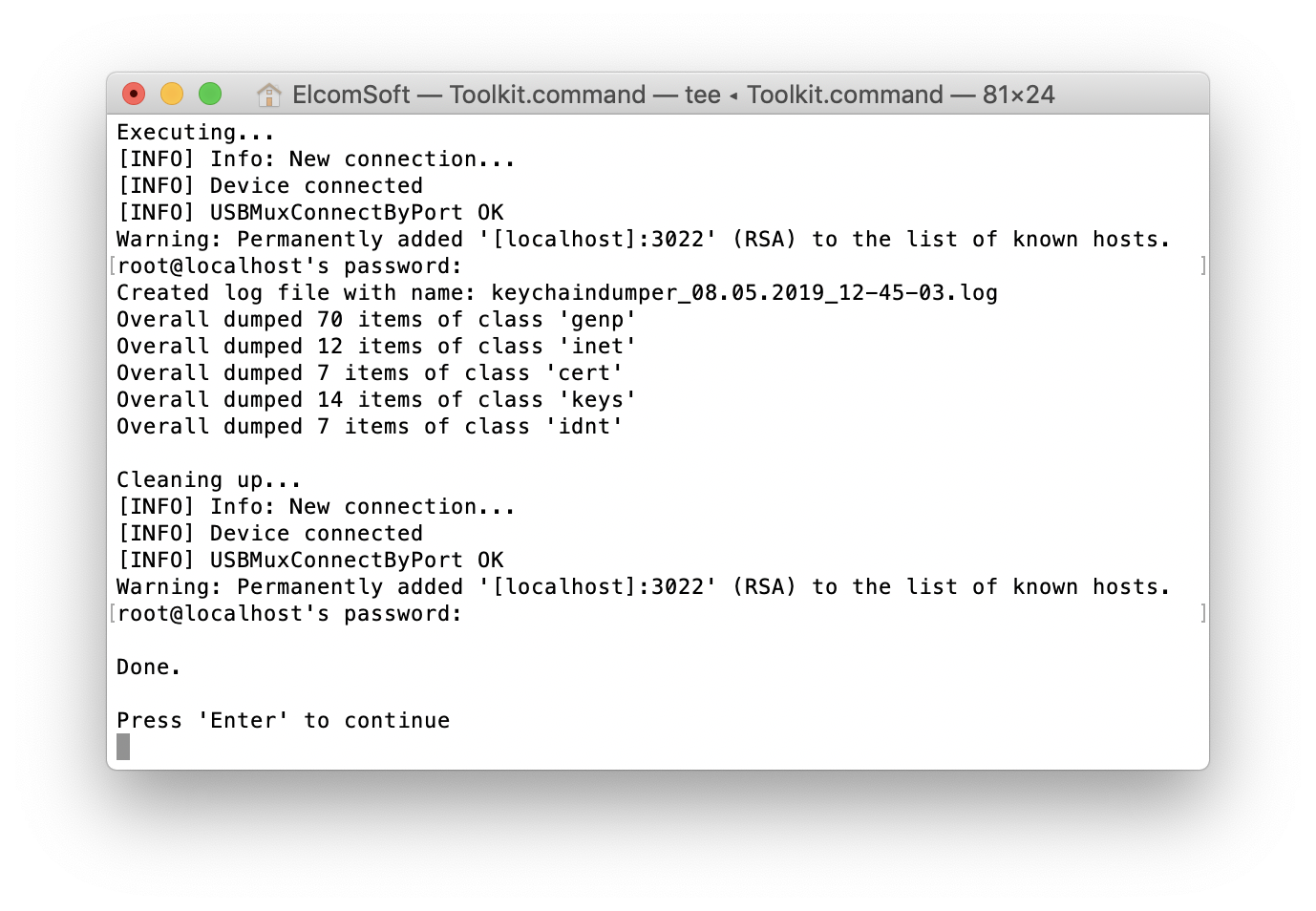 Finally, you can load the file system into forensic software (e.g. Elcomsoft Phone Viewer) or analyse it manually.
Finally, you can load the file system into forensic software (e.g. Elcomsoft Phone Viewer) or analyse it manually.
As already mentioned, Apple TV 4K is a bit harder to jailbreak as it does not have a USB Type-C port. You’ll have to use XCode to establish a wireless connection instead; the rest of the steps are the same.
We did an extensive testing of the Chimera jailbreak and discovered it works fine on our test devices; however, you may sometimes need several tries before the exploit really works.
Apple Watch
There are five generations of Apple Watch, and from the point of acquisition there is only one difference: there is currently no way to connect 4th Generation watches to the computer. There is no over-the-air acquisition option for the Apple Watch.
Just like the Apple TV, Apple Watch (or more exactly, watchOS) does not have a backup service. However, backups can still be created. A watch backup will be stored in the backup of the iPhone the watch is connected to. There is only one way to force a Watch backup: you have to unpair the watch from the iPhone. However, it looks like watch backups may still occur periodically, under some unknown conditions. See Back up your Apple Watch for more details.
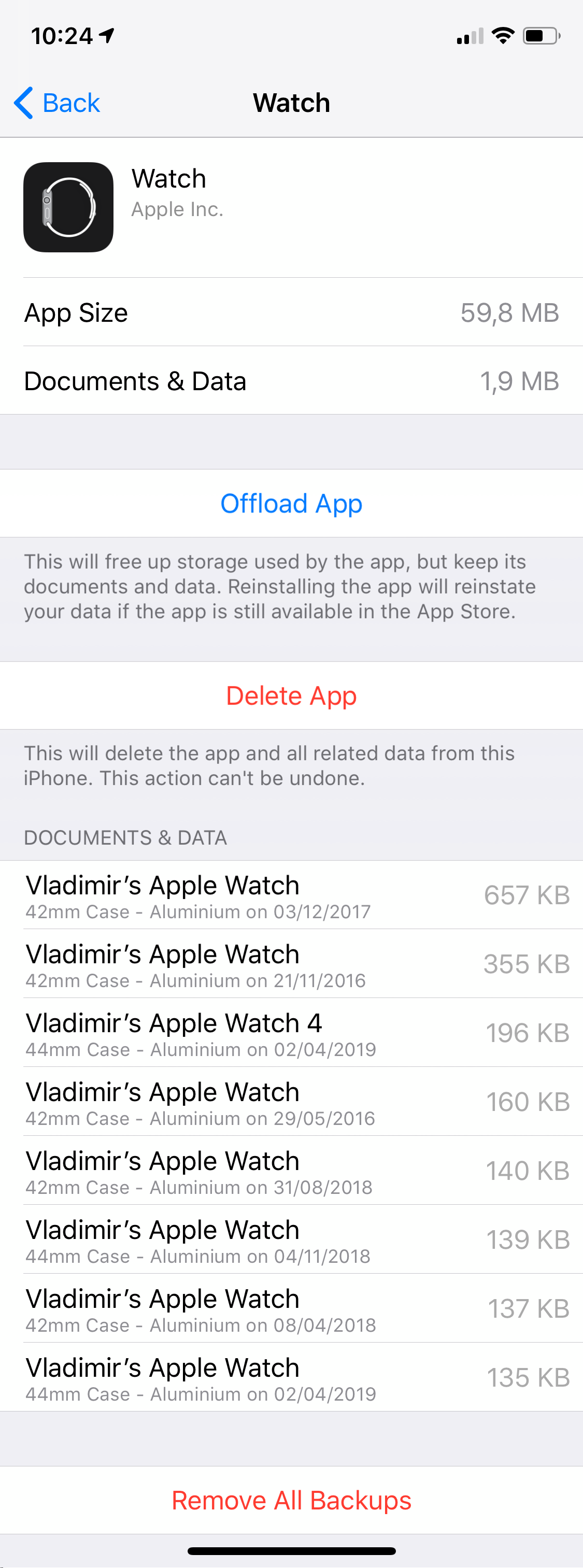
So once you get the iTunes backup of the iPhone (or access to the phone itself), you can extract the watch data from that backup.
A different way of obtaining the data would be connecting the Watch directly to the computer. At this time, it is easily possible for S1/S2/S2 models. The Apple Watch has a diagnostic port hidden under the belt; you will need a very thin pin to open the cover. Next, you will need a special adapter; the only one we know of is called IBUS:

Connecting the adapter to the watch is not that easy. But once you get it done right:

iTunes prompts to establish a trusted relationship with the computer, just like with the iPhone:
iTunes will then show some info on the watch you’ve connected (just the OS version and unique ID):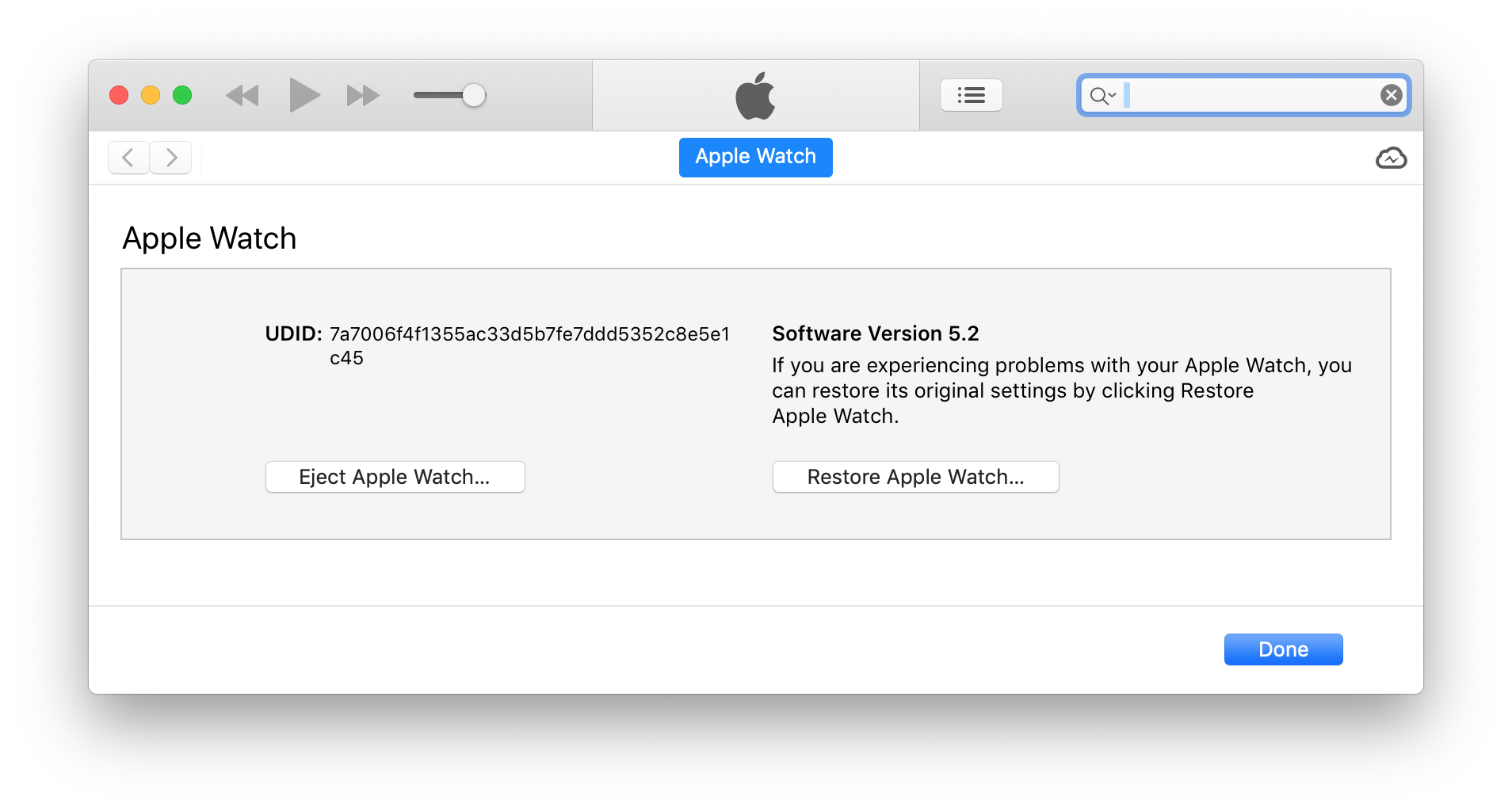 Now proceed with Elcomsoft iOS Forensic Toolkit:
Now proceed with Elcomsoft iOS Forensic Toolkit: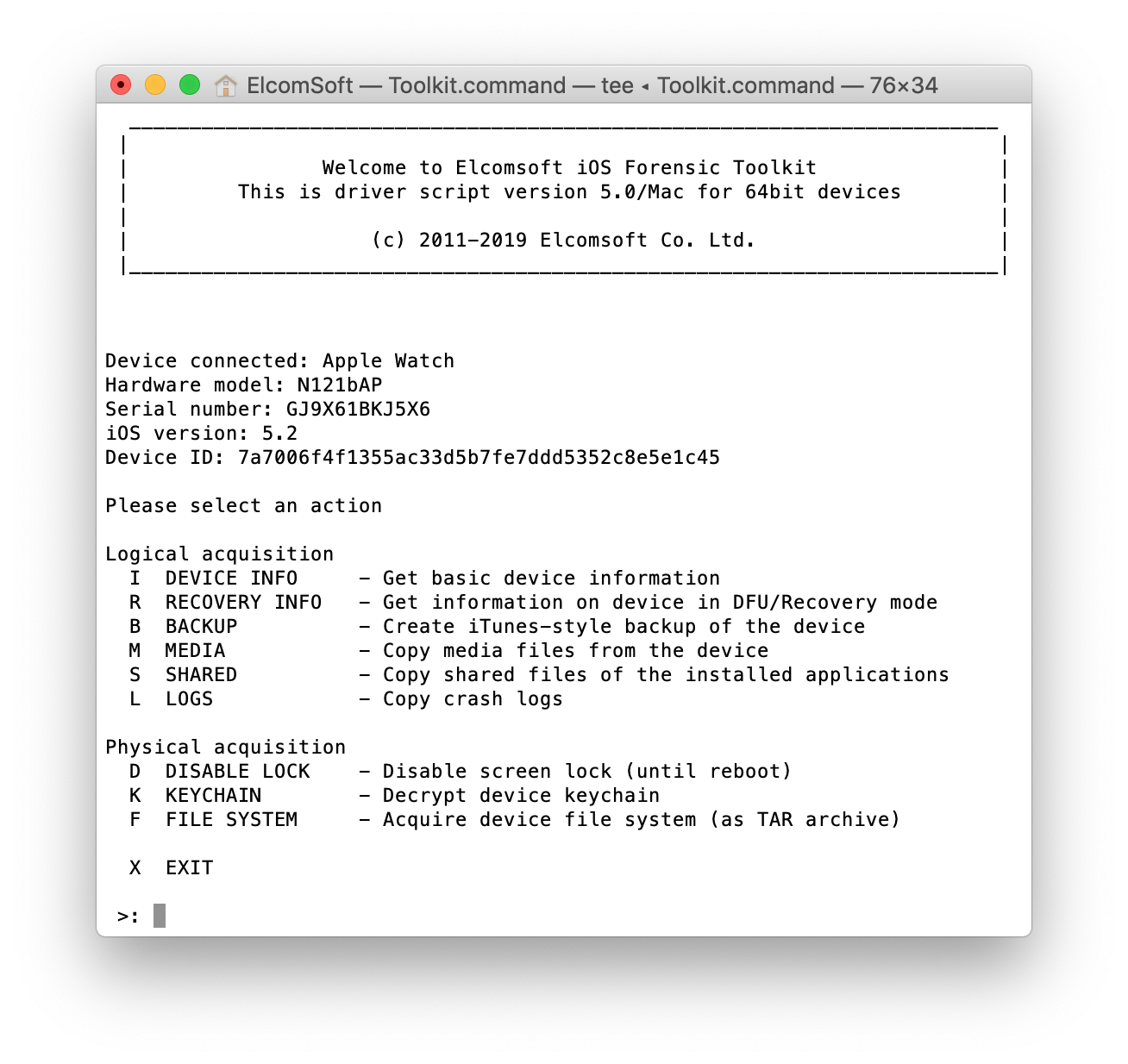 You can extract the list of apps installed on the Watch:
You can extract the list of apps installed on the Watch: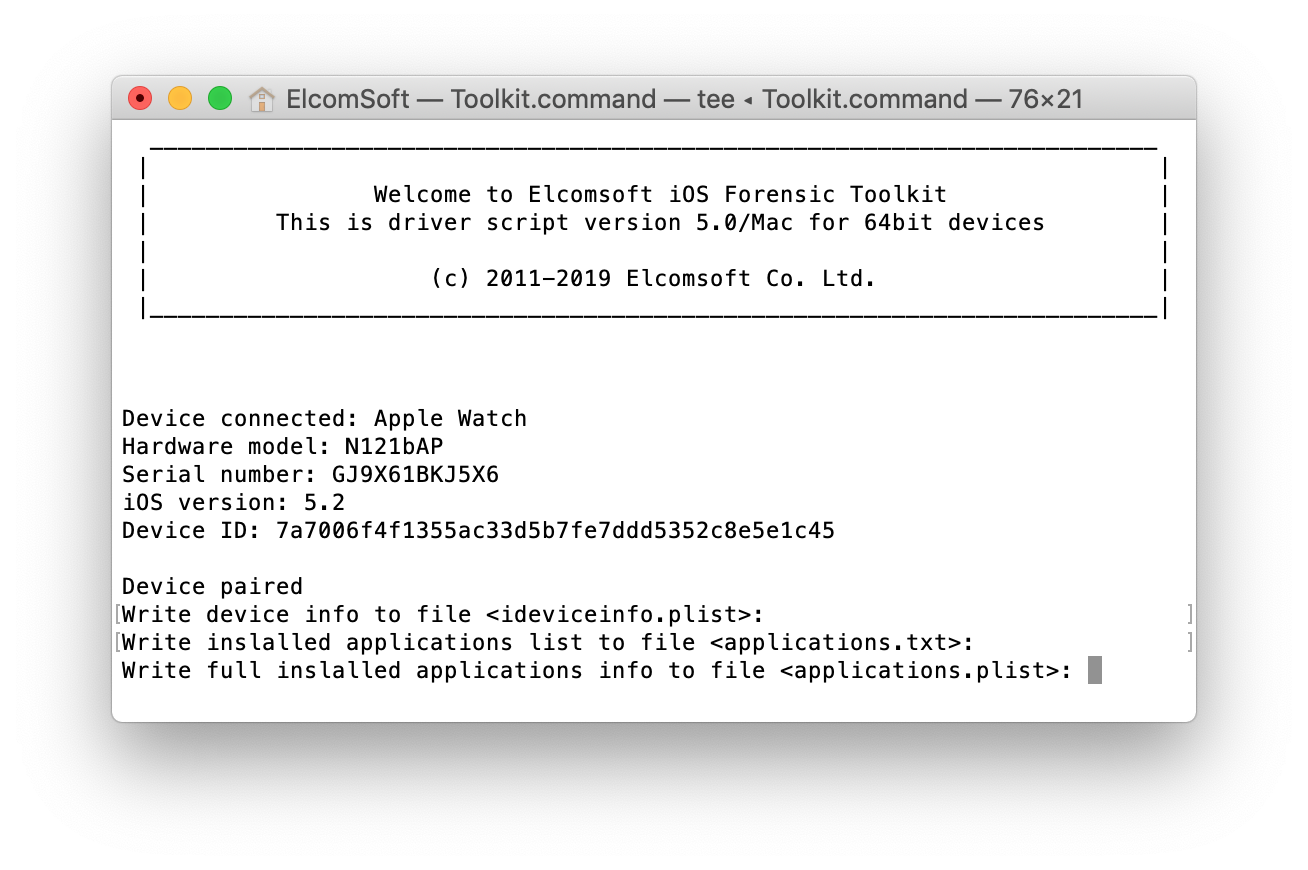
Acquire the logs: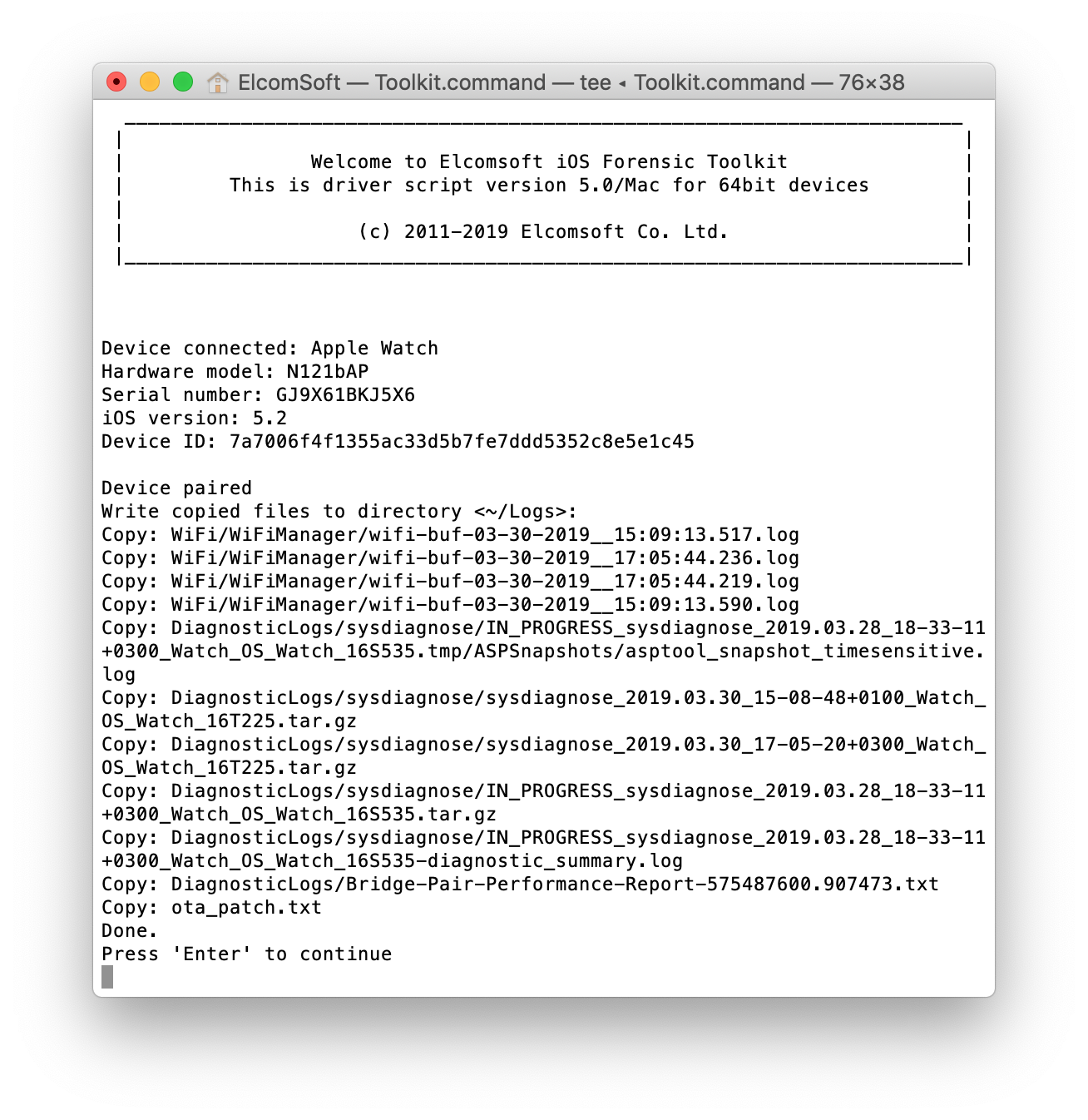 And finally, the media files (again, pay special attention to the Photos.sqlite database):
And finally, the media files (again, pay special attention to the Photos.sqlite database):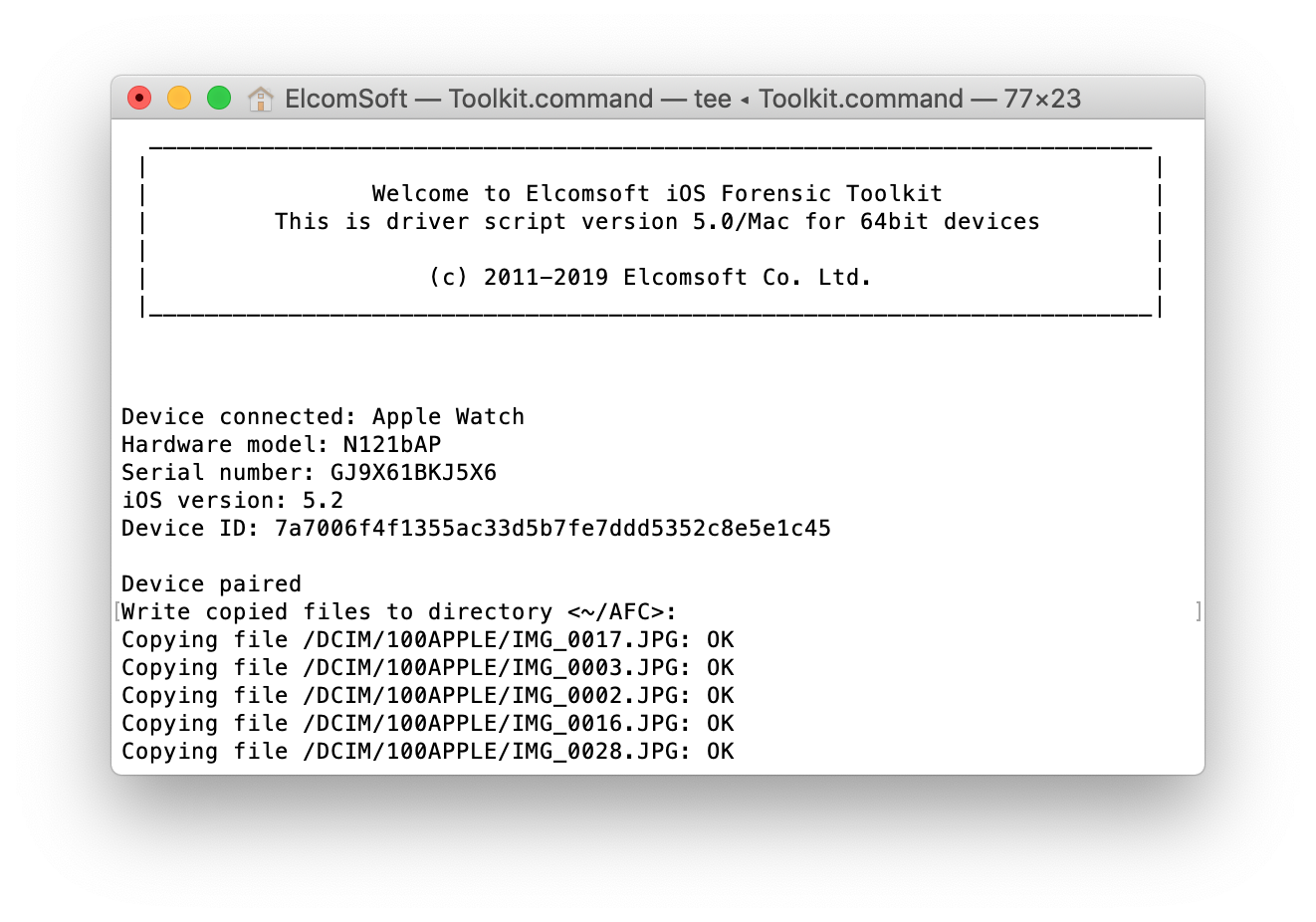 Jailbreaking? Sorry, no way; it seems that there was a single proof of concept called jelbrekTime for tvOS 4.0-4.1; no word for newer models.
Jailbreaking? Sorry, no way; it seems that there was a single proof of concept called jelbrekTime for tvOS 4.0-4.1; no word for newer models.
Anything else you can get from Apple Watch? Technically speaking, you can’t, but there is one more thing originating from the Apple Watch that lands in iCloud. You will need Elcomsoft Phone Breaker to download Health data from iCloud (the tool extracts even the data that uses additional encryption and never delivered by Apple when fulfilling legal requests). You will then use Elcomsoft Phone Viewer to browse it:
 Data analysis
Data analysis
Once the data is extracted, the next step is analysis. We are going to cover that in our next article; stay tuned! While waiting, check out the excellent work by Mattia Epifani, a SANS instructor and a co-author of Learning iOS Forensics:


















