When equipping a forensic lab, having a diverse set of tools is extremely important due to their diverse, rarely overlapping capabilities, and the need for cross-checking the results. With that many tools, compatibility is crucial. This is why we went a long way to ensure that any data extracted with our mobile forensic tools can be opened in many popular forensic analysis tools.
Our mobile extraction tools
As we specialize in mobile extractions, our tools have a number of unique features one is unlikely to see in competing products. These include:
Forensically sound checkm8 extraction: Our implementation of the checkm8 exploit enables unparalleled compatibility, spanning from iPhone 3Gs with iPhone OS 3.0 to the latest devices equipped with chipsets that are vulnerable to the bootloader exploit. Our checkm8-based solution is not only the most compatible one, but one of the few tools offering true forensically sound extractions with repeatable, verifiable results.
Low-level extraction agent: We developed a unique extraction agent designed for low-level file system extraction and seamless keychain decryption, offering the widest compatibility and refined usage experience. While many tried to replicate our innovative tool, it’s the seamless compatibility and the “refined” part of the usage experience that our competitors still struggle with.
Support for Apple ecosystem: Our extraction tools boast comprehensive support extending across the entire Apple ecosystem. We can extract data from Apple Watch, Apple TV, and Apple HomePod devices in addition to iPhones and iPads.
However, as we specialize in data extraction, we trust subsequent phases to those who specialize in making analysis tools. While certain types of data might be manually examined, specialized software remains the preferred option. Despite the number of vendors and solution available to forensic experts, Cellebrite Physical Analyzer remains our tool of choice, being the most compatible and arguably the finest product available for analysis.
The analysis stage
Extracting data from the device is just the beginning of a forensic investigation. Once data is obtained, the analysis stage comes into play. While some types of data (such as passwords extracted from the keychain) can be reviewed manually, the sheer amounts of information found in a typical modern device mandate the use of specialized software. This is where the choice of software becomes crucial, impacting the thoroughness and accuracy of the investigation.
Cellebrite Physical Analyzer is one of the better tools in this regard, not only due to its exceptional compatibility but also owing to its robust analytical capabilities, making it indispensable in any forensic lab. Our unique extraction capabilities in Apple ecosystem combined with forensic analysis tools like Cellebrite Physical Analyzer enable thorough and effective forensic investigations.
Remember: trust, but verify. Even if you are using the very best forensic tools, do not blindly rely on something, even if everything looks consistent. Despite the proven quality of the software, errors and omissions, both on the human side and software side, can still occur. It is crucial to manually check and verify everything to ensure accuracy and reliability. There is no magic button labeled “Generate a crime report and add supporting evidence”; you still need thorough manual examination. This principle reminds to stay vigilant and take responsibility for ensuring the integrity of the information you rely on.
Importing extraction agent data
The low-level extraction agent (part of Elcomsoft iOS Forensic Toolkit) returns a file system image (.tar) alongside the keychain (.xml). Unpacking a .tar file is relatively simple (yet it may be rather slow depending on the size of the data set), yet analyzing the keychain is a bit more difficult. The keychain holds vital information, such as the user’s authentication credentials, logins and passwords, tokens, and encryption keys that can be used to decrypt certain types of data, such as Signal conversations. Some products mandated the keychain to simply exist adjacent to the .tar file, possessing a specific name corresponding to the name of the .tar archive. This naming convention does not coincide to what we use in our product, and Cellebrite has ingeniously and elegantly circumvented this limitation (as seen on the screenshot).
Legacy devices
For older 32-bit devices lacking Secure Enclave, we resort to a unique physical extraction method called Perfect HFS Acquisition, preserving the device image in a DMG format. Cellebrite supports this process, with one omission: there is no keychain support when opening .dmg files in Cellebrite Physical Analyzer. We hope the company will fix this issue in future builds, while other vendors drop support for legacy formats altogether.
Opening EIFT data sets in Cellebrite Physical Analyzer
Once you’ve successfully extracted a data set using the Elcomsoft iOS Forensic Toolkit, follow these step-by-step instructions to open and analyze the extracted data in Cellebrite Physical Analyzer:
Select File | Open case…:
- Open Cellebrite Physical Analyzer and navigate to the menu bar.
- Click on “File” and then select “Open case…”
- Under “Load evidence”, press “+ Add”:
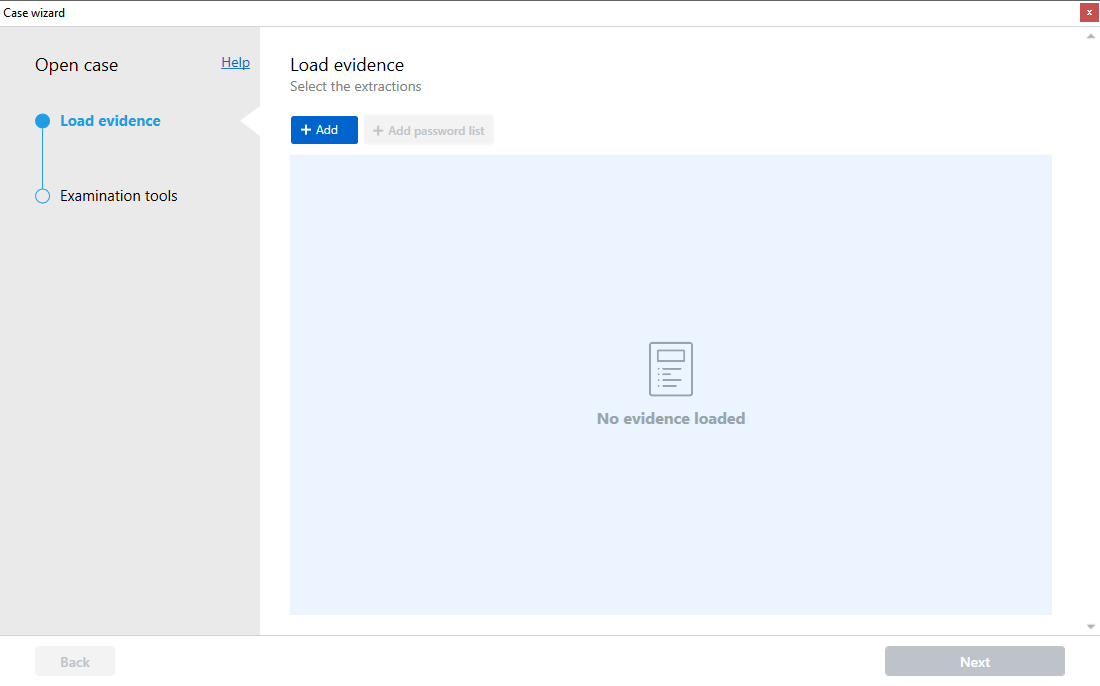
In the “Load Evidence” window, click on the “+ Add” button. Select “Open (Advanced)”:
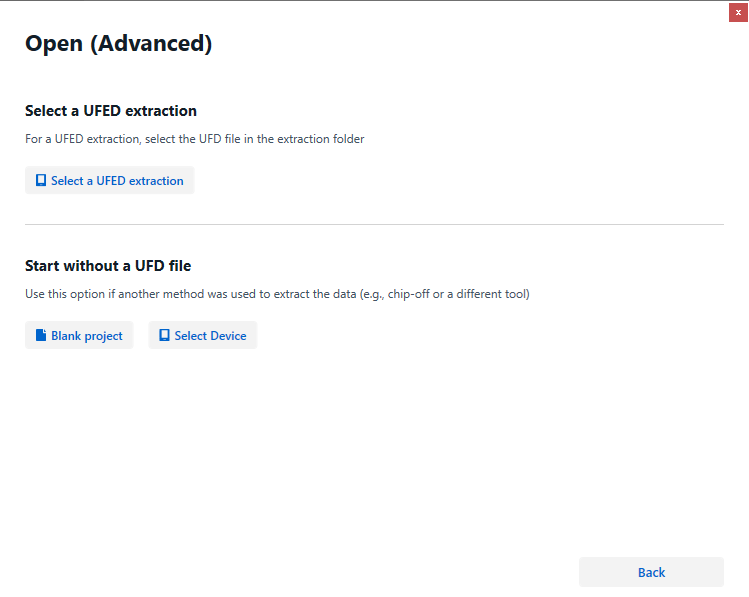
Select “Select Device”:
After selecting “Open (Advanced),” choose the option “Select Device” to specify the extraction type.
For Agent Extraction:
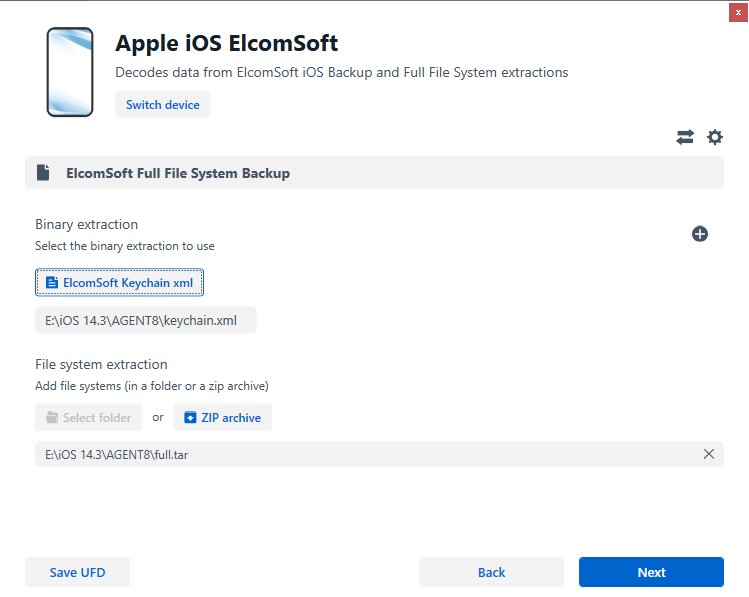
- Search for “Elcomsoft” in the available options and select “Apple iOS ElcomSoft”

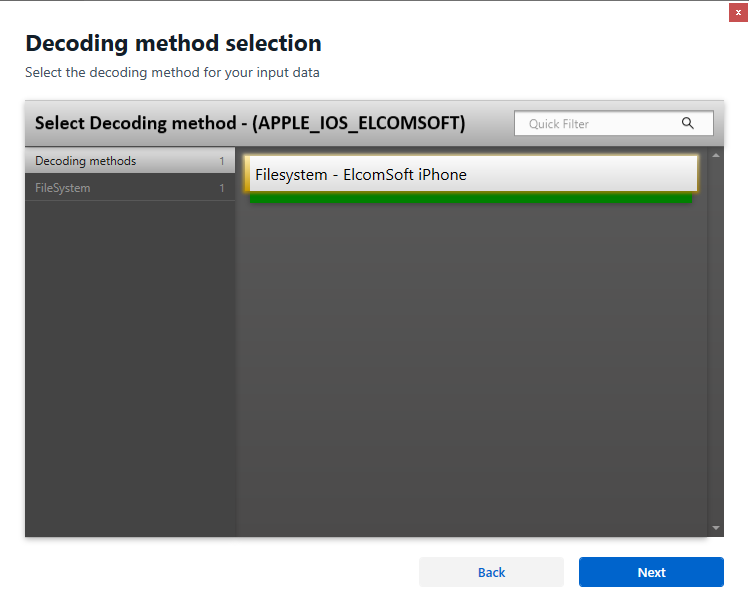
Choose “ZIP archive” and browse for the .tar file containing the full file system image extracted by Elcomsoft iOS Forensic Toolkit.
- Select “ElcomSoft Keychain.xml” and browse for the keychain file extracted by Elcomsoft.
- Proceed to the next step.

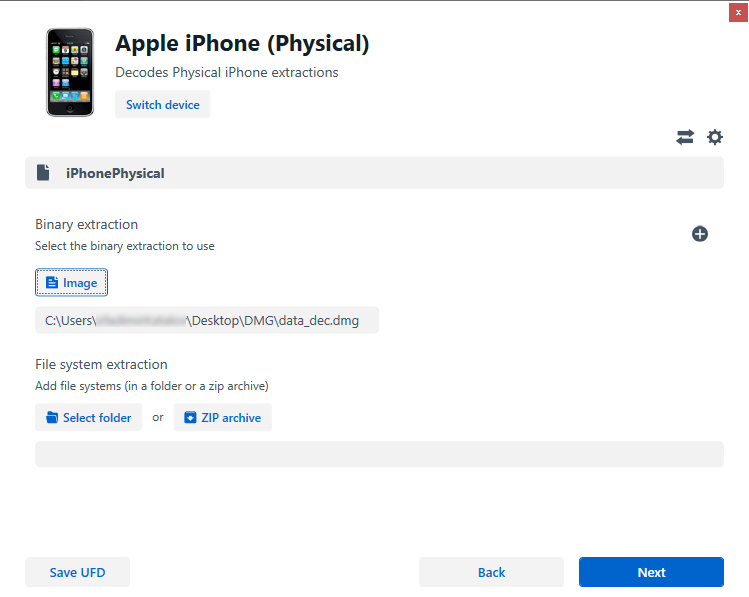
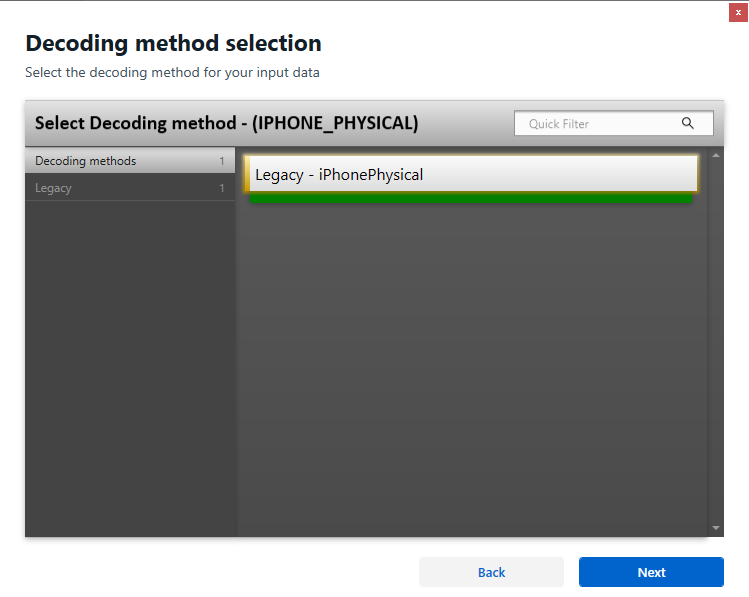
For DMG Extraction:
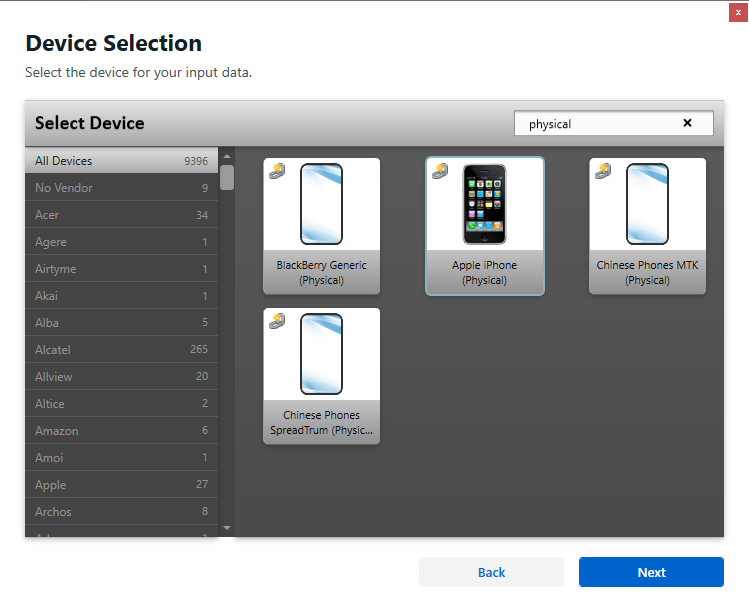
- Search for “physical” to filter the available extraction types.
- Choose “Apple iPhone (Physical)” as the device type.
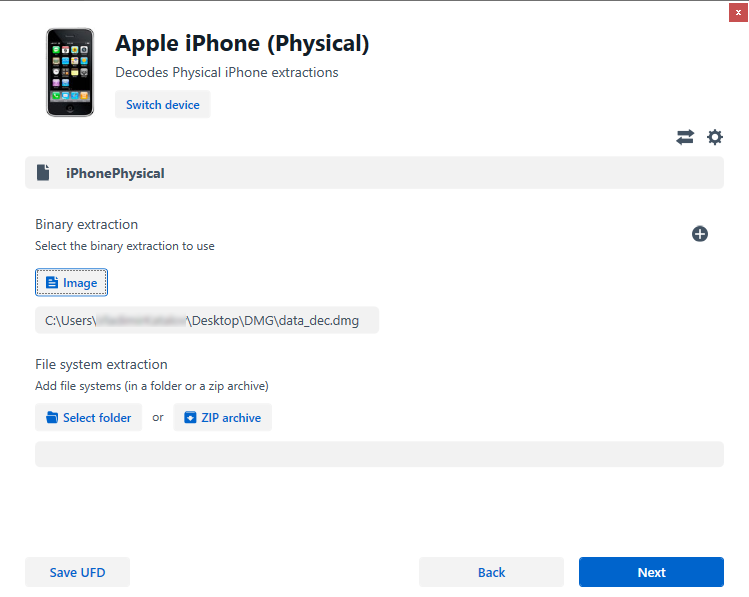
- Select “Image” and browse for the .dmg file extracted using Elcomsoft iOS Forensic Toolkit.
- Proceed to the next step.
Agent Extraction Details:
For agent extraction, confirm the selected files (.tar and keychain) are correctly loaded and displayed in the respective fields. Review the details to ensure accurate selection and mapping of the extracted files.
DMG Extraction Details:
For DMG extraction, verify the selected .dmg file is accurately loaded in the specified field. Review the details to ensure the correct .dmg file is chosen for analysis.
Proceed as Usual:
- Once all necessary files are selected and confirmed, proceed by clicking “Next” to initiate the analysis process.
- Follow the instructions provided in the wizard to continue with the analysis in Cellebrite Physical Analyzer.
By following these steps, you will be able to seamlessly import and analyze the extracted data set from Elcomsoft iOS Forensic Toolkit in Cellebrite Physical Analyzer.
Future development
We are currently in the process of examining the compatibility of our software output with another top-tier tool, Magnet AXIOM, and will provide a separate update on this. Additionally, we want to say that we are open to partnerships and collaborations, offering our software and detailed format specifications to other vendors such as MSAB and Compelson to facilitate compatibility efforts on their end. As part of our efforts, we are also working on converting DMG images to tar archives, aiming to simplify processes for those who prefer convenience. However, it’s essential to note that this is not the optimal solution overall, as DMG contains more file metadata.
Conclusion
In conclusion, the synergy between ElcomSoft’s cutting-edge extraction capabilities and meticulous analysis using specialized software, like those exemplified by Cellebrite’s solutions, is crucial for investigations that involve data retrieved from Apple devices. When used together, the two products empower forensic experts to delve deeper into digital evidence, facilitating a comprehensive and meticulous investigative process that stands at the forefront of modern forensic techniques.













