When accessing a locked system during an in-field investigation, speed is often the most important factor. However, maintaining digital chain of custody is just as if not more important in order to produce court admissible evidence. We are introducing new features in Elcomsoft System Recovery, our forensic triage tool, to help establish and maintain digital chain of custody throughout the investigation.
In order to preserve digital evidence, the chain of custody begins from the first point of data collection. For this reason, the traditional workflow used in computer forensics involves powering off the computer, pulling and imaging its storage media through a write-blocking device. These steps helps ensure that digital evidence collected during the investigation remains court admissible. With Elcomsoft System Recovery, we introduce a viable alternative to hardware-based write blocking disk imaging devices while offering real-time access to crucial evidence. Elcomsoft System Recovery is a digital triage tool for examining computers in the field. The tool helps overcome the challenge of accessing a locked system, delivering a straightforward workflow for investigating computers in the field. From the technical standpoint, Elcomsoft System Recovery is a Windows PE based bootable tool designed to safely image the target computer’s internal media, locate encrypted volumes and unlock encrypted virtual machines. In its latest release, the tool offers write-blocking, verifiable disk imaging.
Write-blocking disk access
Elcomsoft System Recovery 8.0 helps producing court admissible evidence with write-blocking mode and read-only disk imaging. The write-blocking mode is engaged by default during the first steps of running Elcomsoft System Recovery, ensuring that no data is modified on the target computer. In this mode, you can image disks and partitions, locate encrypted disks and extract encryption metadata, and use the supplied two-panel file manager to analyze the file system.
From this release onwards, write-blocking disk access becomes the tool’s default behavior. You will have to explicitly untick the “read-only” check box to access system management functionality such as resetting Windows user and administrative passwords.
Verifiable disk imaging
You can image connected disks into verifiable .E01 images. Together with read-only access, the use of hashing helps establish digital chain of custody, while employing the industry-standard .E01 format makes the images compatible with third-party forensic tools for comprehensive analysis.
Producing a verifiable disk image in write-blocking mode
To enable read-only access and produce a verifiable disk image, follow these steps.
- Download and run Elcomsoft System Recovery 8.0 or newer on your computer (not on the target computer).
- Prepare Elcomsoft System Recovery bootable USB drive. Check Elcomsoft System Recovery: a Swiss Army Knife of Desktop Forensics | ElcomSoft blog for step by step instructions.
- Configure target computer to boot from a USB device.
- Boot target computer to Elcomsoft System Recovery.
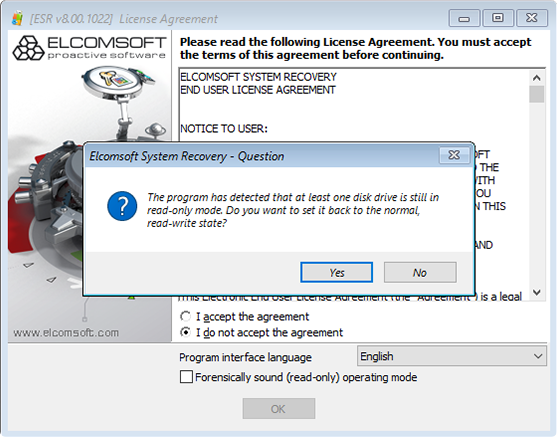
- You will be prompted to accept the License Agreement. At the bottom of the prompt you will see a check box enabling forensically sound, read-only access to the computer’s storage media. This check box is selected by default. Click Next to continue in read-only mode.
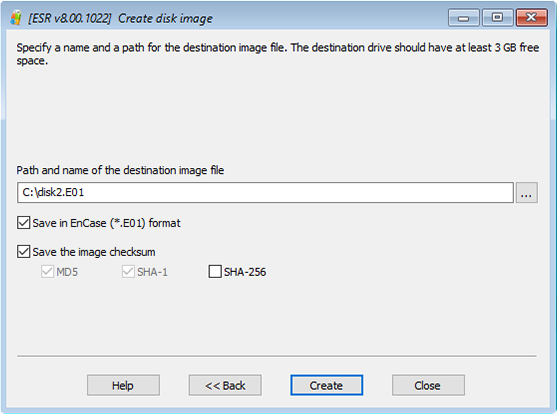
- Create forensic disk images for further in-lab analysis. To produce a verifiable forensic disk image, choose the .E01 format. Multiple checksums will be embedded into the image to ensure data integrity, and the entire image will be signed with a hash value once the process completes.
In certain cases, Elcomsoft System Recovery may be unable to mount one or more disks in read-only mode. This may happen in the following cases:
- You are booting Elcomsoft System Recovery from read-only media (such as a bootable CD/DVD drive, SD card in read-only mode, or a USB flash drive in read-only mode), or if there is not enough free space on the ESR bootable drive. We suggest installing Elcomsoft System Recovery onto a regular USB flash drive, a portable SSD drive or a portable hard drive with no write protection and plenty of available free space.

- The name of the logical volume is “X”. All other volumes can be mounted read-only, except for disk “X:”, which is a Windows PE limitation.
If this happens, the following occurs:
- If Elcomsoft System Recovery is unable to mount one or more disks read-only, it will display a warning.
- Once you close the warning, the “read-only access” check box remains selected. If you want to continue without write blocking, you’ll have to manually unselect the check box and click Next. Alternatively, you may choose to stop using Elcomsoft System Recovery, power off the computer, pull the hard drives and image them offline.
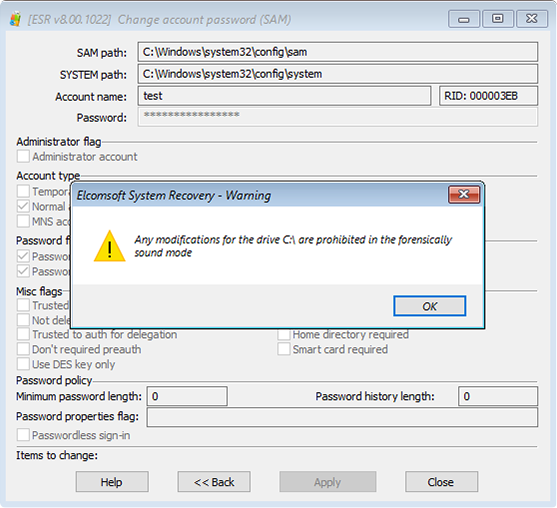
While working in read-only mode, you will be able to make disk images, extract page and hibernation files, locate and mount BitLocker volumes, and extract encryption metadata. System management activities such as resetting passwords to Windows user accounts are not permitted in this mode. If you attempt to perform a management task, you will see the following warning:
Notes and troubleshooting
Note that any BitLocker volumes you mount after engaging the read-only mode will be also mounted read-only. The read-only mode will be deactivated when you shut down the computer via Elcomsoft System Recovery. If the computer locks up or the power is lost during the investigation, the disks on the target computer will remain read-only, which will prevent the computer’s normal operation. To fix this, you will have to boot into Elcomsoft System Recovery again, after which the tool will automatically detect the issue and will prompt to re-mount the disks in the regular read-write mode.
About Elcomsoft System Recovery
Elcomsoft System Recovery is a digital triage tool for examining computers in the field. The tool is particularly useful if the computer being analyzed is locked or is inaccessible due to unknown account passwords and/or full disk encryption. Elcomsoft System Recovery helps overcome the challenger of accessing a locked system, delivering a straightforward workflow for investigating computers in the field. The tool helps access information in encrypted disks and encrypted virtual machines, extract passwords and access encrypted file systems.
Conclusion
The already powerful tool can now maintain digital chain of custody. The combination of write-blocking access and verifiable disk images make Elcomsoft System Recovery a viable alternative to hardware-based write blocking disk imaging devices while offering a faster and easier forensic analysis workflow.









Whether the disk is imaged into a RAW/DD or the newly supported .E01 format, Elcomsoft System Recovery calculates a hash file and places it alongside with the image. For RAW/DD files the hash is calculated on the fly at the time of the imaging, and does not slow down the process. For .E01 files, which feature data compression, the hash must be calculated after the imaging is complete. Depending on the size of the image and the speed of the target storage media calculating the hash may take a long time. We recommend using fast SSD drives when possible. Elcomsoft System Recovery creates a pair of MD5 and SHA1 hashes; you can additionally enable the third SHA256 hash. The hashes are technically different from digital signatures that require signing the value with a trusted certificate, yet, with proper documentation, they can be used to validate the authenticity of the image.
Using hash values to authenticate evidence
According to Peter Callaghan, Pagefreezer’s Chief Revenue Officer, hash values can be used to authenticate evidence. In Why Hash Values Are Crucial in Evidence Collection & Digital Forensics (pagefreezer.com), he writes:
To validate the image, you can use the command-line certutil:
If the verification is successful, you will see the result as in the following example: