Last month we introduced forensically sound low-level extraction for a range of iPhone devices. Based on the renowned checkm8 exploit, our solution supported devices ranging from the iPhone 5s through 6s/6s Plus/SE. Today, we are extending the range of supported devices, adding checkm8 extraction of the iPhone 7 and 7 Plus.
Prior work
Exactly one month ago, we released the second beta version of iOS Forensic Toolkit 8.0. The second beta became the first publicly available one. That release introduced true forensically sound extraction for a range of iPhone and iPad devices that have a bootloader vulnerability making them susceptible to the checkm8 exploit.
What is “forensically sound” extraction, why you may need it, and how our extraction process differs from competing implementations? These questions are addressed in the Forensically Sound Extraction for iPhone 5s, 6, 6s and SE writeup.
To sum it up, our solution delivers true forensically sound extraction of the iPhone file system, including the keychain. Since all the patching occurs entirely in the device’s RAM, we never boot (and don’t even need) the operating system installed on the device. The result is reliable, verifiable and repeatable extraction. If you use iOS Forensic Toolkit to image the iPhone file system, power off the iPhone, store it for any period of time, then repeat the extraction process, you are guaranteed to get exactly the same result; the checksums of the two images will match.
The new beta also changes the UI. Instead of the menu-driven console, we are readying the tool for the new user experience. In the meanwhile, the beta version is driven via the command line. The experience differs significantly from iOS Forensic Toolkit 7, so much so that we published a manual: How to Use iOS Forensic Toolkit 8.0 b2 to Perform Forensically Sound Extraction of iPhone 5s, 6, 6s and SE
iPhone 7 support
The second beta supported quite a few devices ranging from the iPhone 5s through iPhone 6s, 6s Plus, and the original iPhone SE. Missing from the list were the iPhone 7, 7 Plus, and the entire iPhone 8/8 Plus/iPhone X range of devices. While we are still working on the latter, the iPhone 7 and 7 Plus support has arrived.
Meet iOS Forensic Toolkit 8.0 beta 3 for Mac! The tool expands the range of supported devices, adding support for iPhone 7 and 7 Plus devices, enabling bootloader-based, forensically sound extraction of supported devices running the latest available versions of iOS. The following models are added:
iPhone 7 (iPhone9,1 and iPhone9,3)
- A1778 (Global)
- A1660 (USA & China)
- A1780 (China)
- A1779 (Japan)
- A1853
- A1866
iPhone 7 Plus (iPhone9,2 and iPhone9,4)
- A1784 (Global)
- A1661 (USA & China)
- A1785 (Japan)
- A1786 (China)
The iPhone 7 support breaks down into the following parts. For iPhone 7 and 7 Plus devices that run iOS 10.0 through 13.x the complete, forensically sound checkm8 extraction experience. The tool can extract the file system and decrypt the keychain with zero modifications to the device, thus helping maintain the chain of custody. There is no need to remove the passcode.
For iPhone 7 and 7 Plus devices running iOS 14 and 15 (up to and including iOS 15.2), you’ll have to remove the screen lock passcode to apply the exploit. Since removing the passcode requires booting the device into the original OS, this process is not forensically sound. Once the passcode is removed, the tool makes full file system extraction and decrypts the keychain.

The full compatibility matrix is outlined below.
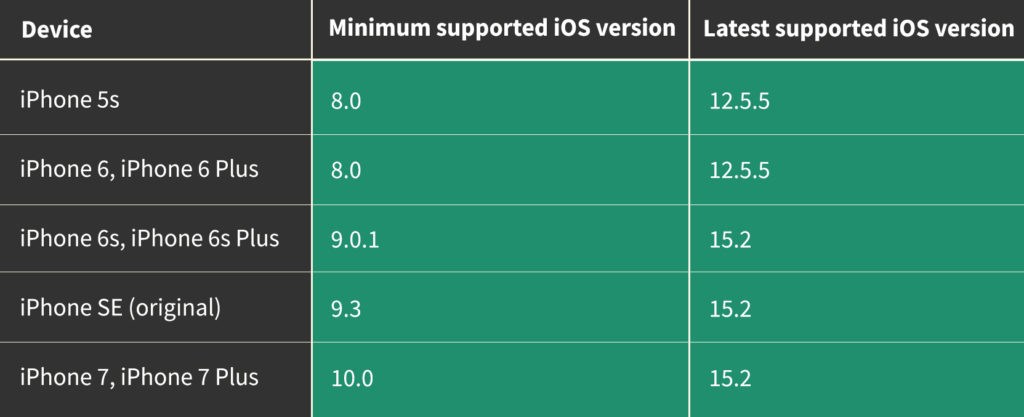
Note: the iPhone 6s and 6s originally shipped with iOS 9.0.1 onboard, while the iPhone SE was shipped with iOS 9.3. The iPhone 5s originally shipped with iOS 7.0, which is currently not supported for checkm8 extraction.
Placing the device in DFU mode
Placing the device in DFU mode can be tricky, especially if you’ve never done it before. DFU is different from Recovery in that Recovery was designed to be used in emergency situations by the end user, while DFU was never meant for the end user.
Steps to enter DFU are less than obvious, and there is no on-screen indication of successfully entering DFU. You must follow the steps while carefully observing the timings, and the end result will be a blank screen. To make the process easier, iOS Forensic Toolkit implements real-time guidance, indicating which buttons are to be pressed and implementing countdown timers.
The instructions are described in the following article: DFU Mode Cheat Sheet
If any of the device buttons is broken, follow these instructions instead: How to Put an iOS Device with Broken Buttons in DFU Mode
Also note that you may need a hub to install the exploit if you are using an Apple Silicon Mac: More on checkm8 and USB Hubs, Upcoming iPhone 7 Support.
Why the keychain is important
The keychain extracted from the device via low-level acquisition is very important. It contains all the passwords, authentication tokens and encryption keys to the most secure apps such as Signal. While most of these are included in password-protected local backups, some of the most secure parts (such as the Signal encryption keys) won’t be backed up at all. The only way to access these bits and pieces is performing the low-level extraction.
With this release, EIFT can extract the full keychain via the checkm8 exploit from all supported devices running all versions of iOS up to and including iOS 15.2. This feature is unique to iOS Forensic Toolkit.
Limitations and future work
There is one limitation about the iPhone 7 extraction with checkm8. For older devices, we could use the detected iBoot version to identify the iPhone iOS version. We do our best to guesstimate the iOS version, but using one version up or one version down usually does the trick as well. This is no longer the case for the iPhone 7; you must use the firmware that matches the installed iOS build exactly. If you use the wrong version, the iPhone will either reboot or fail to unlock the data partition. This means that you may have to try several times until the correct version of firmware is found.
We are in the middle of the journey. Our original checkm8 implementation now covers most devices that are vulnerable to checkm8. These range from the iPhone 5s all the way to the iPhone 7 and 7 Plus, with caveats. Currently, you must remove the screen lock passcode from iPhone 7 and 7 Plus devices running iOS 14 or 15, which breaks the “forensically sound” part. We are working on these restrictions; keep an eye on our blog for news to come.
What about the passcode? In order to use our solution, you must know the screen lock passcode if one is enabled on the device. The exploit cannot be used to crack the passcode, at least at this time.
Getting the beta version
iOS Forensic Toolkit for Mac beta 3 is a public build available to everyone with a non-expired license. You’ll need your EIFT dongle (and, obviously, a Mac) to run the tool.

Conclusion
With this update, Elcomsoft iOS Forensic Toolkit becomes the most advanced iOS acquisition tool on the market. The toolkit now supports all possible acquisition methods (with known limitations we’re working on). Agent-based extraction and checkm8-based extraction via device RAM are some of the tool’s unique features.





