Backups are the primary way to preserve data. On smartphones, backups are handled automatically by the OS. Windows lacks a convincing backup app; numerous third-party tools are available, some of which feature strong encryption. Computer backups may contain valuable evidence that can be useful during an investigation – if you can do something about the password.
Mobile backups
For mobile devices such as smartphones and tablets backups are generally not an issue. Apple users enjoy the convenience of fully automated and highly comprehensive iCloud backups (with an option to create local, encrypted backups via iTunes or Finder). Google Android also offers backups, yet Google’s solution relies largely on synchronized data as opposed to backups. Since Android 9, Google backups are end-to-end encrypted with the user’s passcode. Apple, on the other hand, does not employ end-to-end encryption for iOS cloud backups, yet it uses the technology to protect some types of synchronized data (such as the user’s passwords). Apple’s local and cloud backups along with synchronized data (including end-to-end encrypted types) can be obtained with Elcomsoft Phone Breaker.
When it comes to local backups, Apple offers the ability to create plain or password-protected backups with the iTunes app (or Finder in modern versions of macOS). Password-protected backups contain more usable evidence compared to their unencrypted counterparts, yet the encryption of iOS backups is extremely strong. Breaking a password to a local iOS backup will be as slow as some 10 to 50 passwords per second even if you use a fast GPU. While it may be possible to reset the backup password, this requires access to the device itself, and you will have to enter its screen lock passcode. If the backup is all you have, your options will be limited.
The slow password recovery speed rules out the brute-force approach. You will need to target your attacks based on the human factor using custom dictionaries, masks and mutations in Elcomsoft Distributed Password Recovery.
Desktop backups
For Apple and Google smartphones, the backups are generally not an issue. macOS computers have Time Machine, a truly excellent backup system. Time Machine backups can be protected with a password, and we are yet to cover that. The Windows OS, however, lacks a convincing built-in backup tool. The Backup and Restore (Windows 7) is severely limited in functionality, and does not support encryption at all (Microsoft recommends saving backups onto a BitLocker-encrypted disk if security is important). There is also File History, which is far from comprehensive.
The lack of built-in backup tools made numerous third-party developers release their own Windows backup tools. There are perhaps too many of them, making it difficult to choose just the right one. Some of these tools offer password protection and backup encryption; we’ll talk about that in the next article. The upcoming January release will support passwords to some desktop backup tools; stay tuned for updates!
Encrypted backups: breaking the password
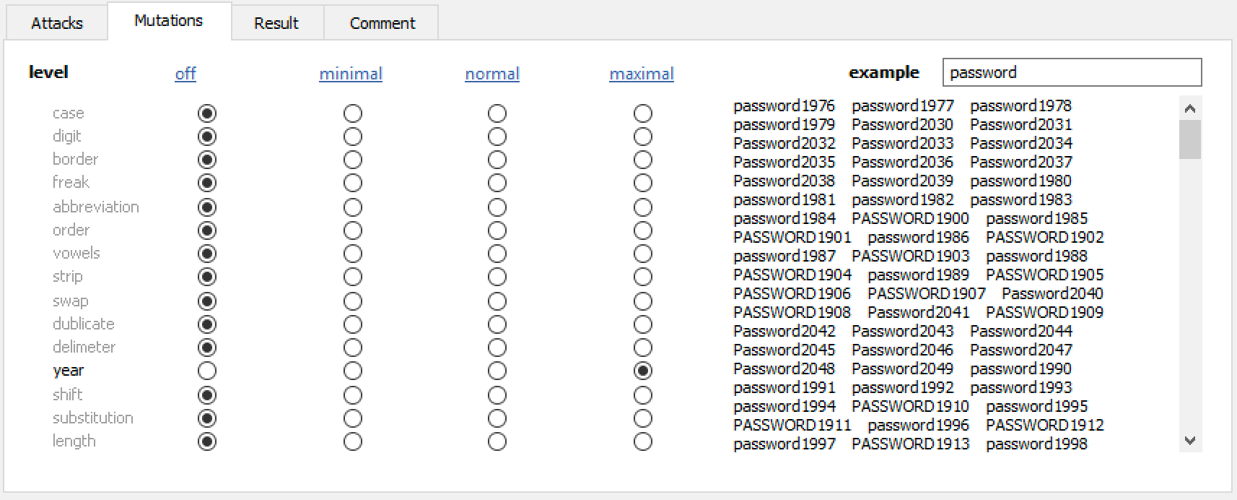
As mentioned above, the brute-force approach is no longer sufficient to break modern backups even if you use a high-end GPU for accelerating the recovery process. You must target the human factor to break most passwords. These attacks include using targeted dictionaries based on known passwords, dictionaries based on leaked password, automated mutations and smart attacks supported by Elcomsoft Distributed Password Recovery.
You can use Elcomsoft Internet Password Breaker to extract the list of the user’s passwords from their computer. You can also extract their passwords from their Google or iCloud account, macOS or iOS keychain, or the user’s Microsoft Account. The user’s existing passwords give a hint at what character groups are likely used:
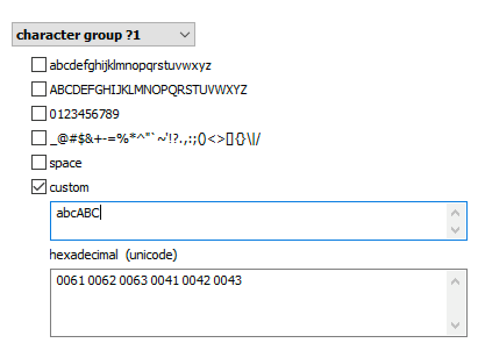
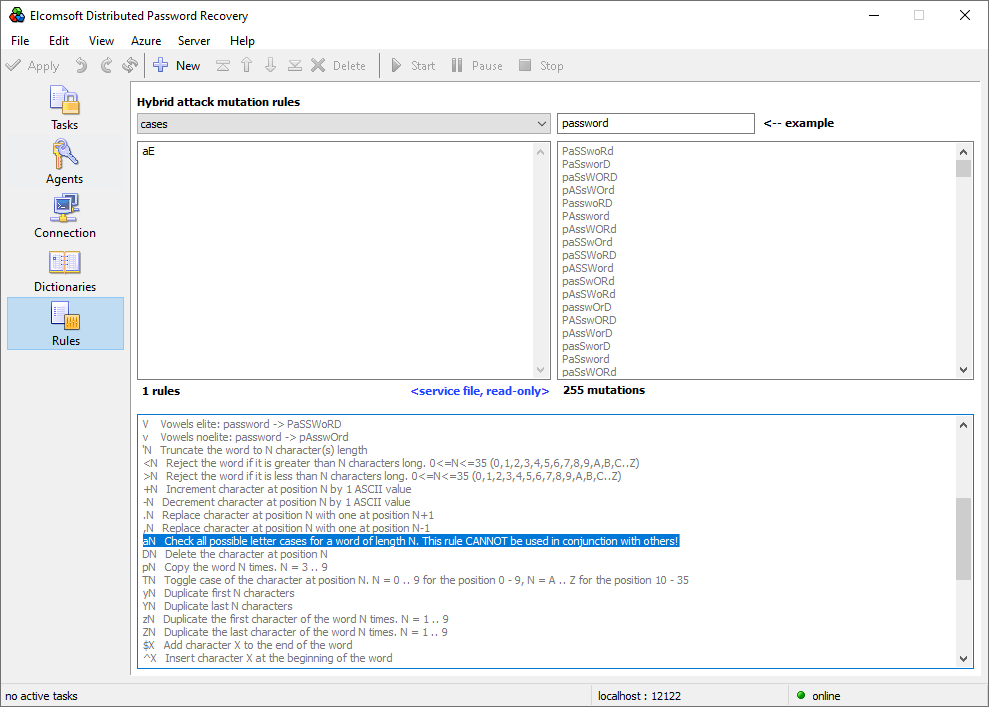
Elcomsoft Distributed Password Recovery offers a number of options to automatically try the most common variations of your password (such as the Password1, password1967 or pa$$w0rd):
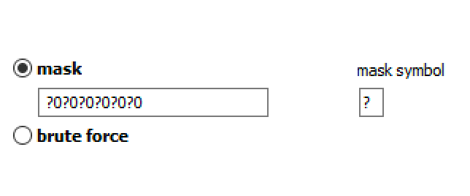
Masks can be used to try passwords matching established common patterns:
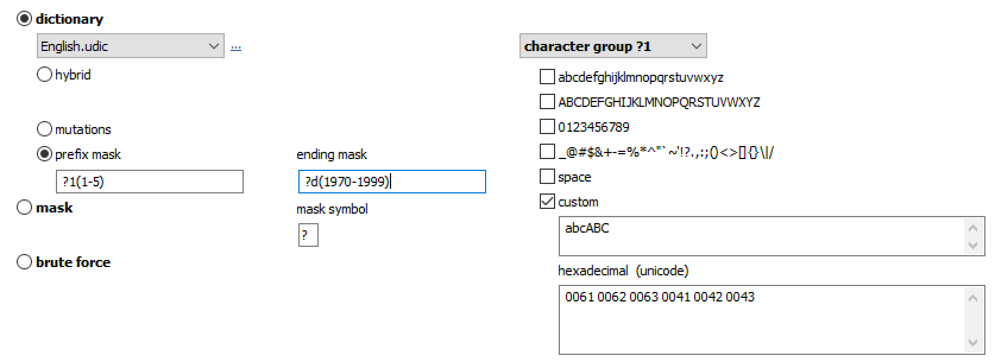 Advanced techniques allow composing passwords with up to two dictionaries and scriptable rules:
Advanced techniques allow composing passwords with up to two dictionaries and scriptable rules:
Conclusion
Backups are a valuable source of digital evidence. Backups are often protected with a password; strong encryption makes the recovery slow even on modern hardware. Accessing encrypted evidence requires using a combination of hardware acceleration and smart attacks targeting the human factor.







