Windows backups are rarely targeted during investigations, yet they can be the only available source of evidence if the suspect’s computer is locked and encrypted. There are multiple third-part backup tools for Windows, and most of them have password protection as an option. We are adding the ability to break password protection of popular backup tools: Acronis True Image, Macrium Reflect, and Veeam.
Windows backups: why third-party tools?
If you are an Apple user, you might be familiar with Time Machine, the macOS built-in backup tool. Time Machine backups can be protected with a password; we’ll get to that in subsequent articles. Windows does not have a truly convincing built-in system backup tool aside of the ancient “Backup and Restore (Windows 7)” tool that is severely lacking compared to its macOS counterpart. Users cannot encrypt these backups with a password (unless they opt to store them on an encrypted disk, which is a different story).
This is why there are numerous third-party Windows backup tools on the market. There are seemingly hundreds of tools, many of which are long abandoned by their developers. Some of the most popular tools are made by three companies: Acronis, Macrium, and Veeam.
Acronis True Image and Acronis Cyber Protect Home Office
Acronis claims to have over 5.5 million home users and 500,000 companies, which makes its backup tools among the most common among Windows users. The company’s backup tools include Acronis True Image 2020, Acronis True Image 2021, and Acronis Cyber Protect Home Office 2022, which is a rebranding of the company’s older tools. The backups are saved in .tib or .tibx files depending on the version.
Acronis tools use AES encryption with user-selectable 128, 192, or 256-bit keys. Considering the AES-NI instruction set accelerating the encryption, this selection of encryption methods seems rather pointless. It is not immediately obvious why the user would choose a less secure option versus AES-256. The choice of encryption algorithm does not affect the recovery speed in a meaningful way; in our tests, the results were very close regardless of the encryption used.
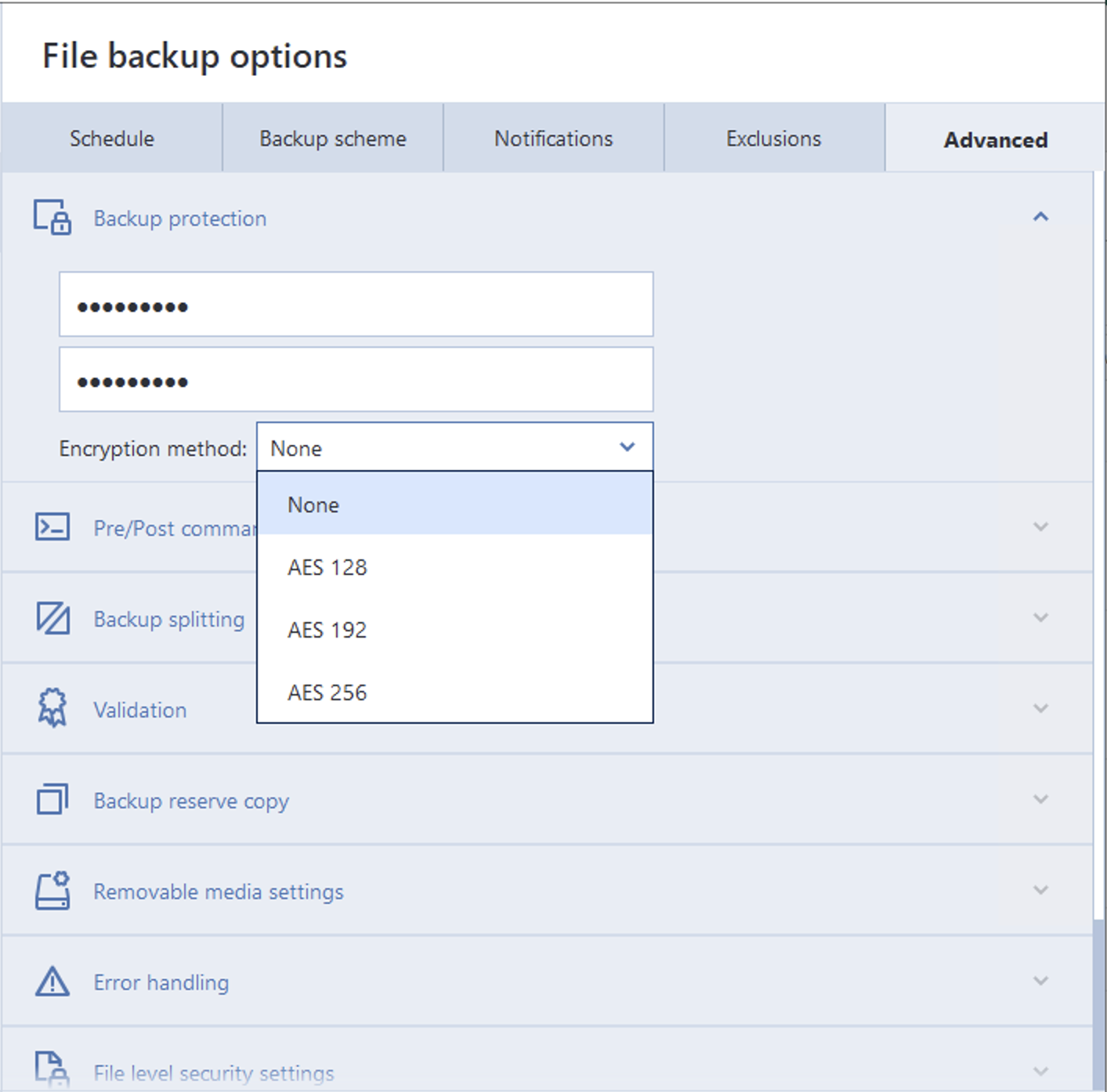
The older .tib format uses the old MD5 algorithm for hashing the password, resulting in a very high speed of 55,000 passwords per second when performing a brute-force attack using a CPU alone. Newer formats use a different password transformation function, resulting in significantly slower attacks.
Macrium Reflect
Macrium targets IT professionals and companies with its range of backup tools. The company does not disclose the number of users, yet we see Macrium as one of the more popular backup tools among the target group.
While there is a free version of Macrium Reflect, encryption is only available in the paid edition. The available encryption choices are AES-128, AES-192, and AES-256. In a rather counterintuitive way, Macrium limits the choice of available encryption methods depending on the user’s choice of the password. Users who set an 8- to 15-character password are limited to the weakest AES-128 encryption. Setting a 16+ character password unlocks the AES-192 encryption option, while the strongest AES-256 option is only available if the user opts for a 32-character or longer password. This choice of encryption is rather backwards; the stronger (and slower) protection is commonly used to compensate for shorter passwords.
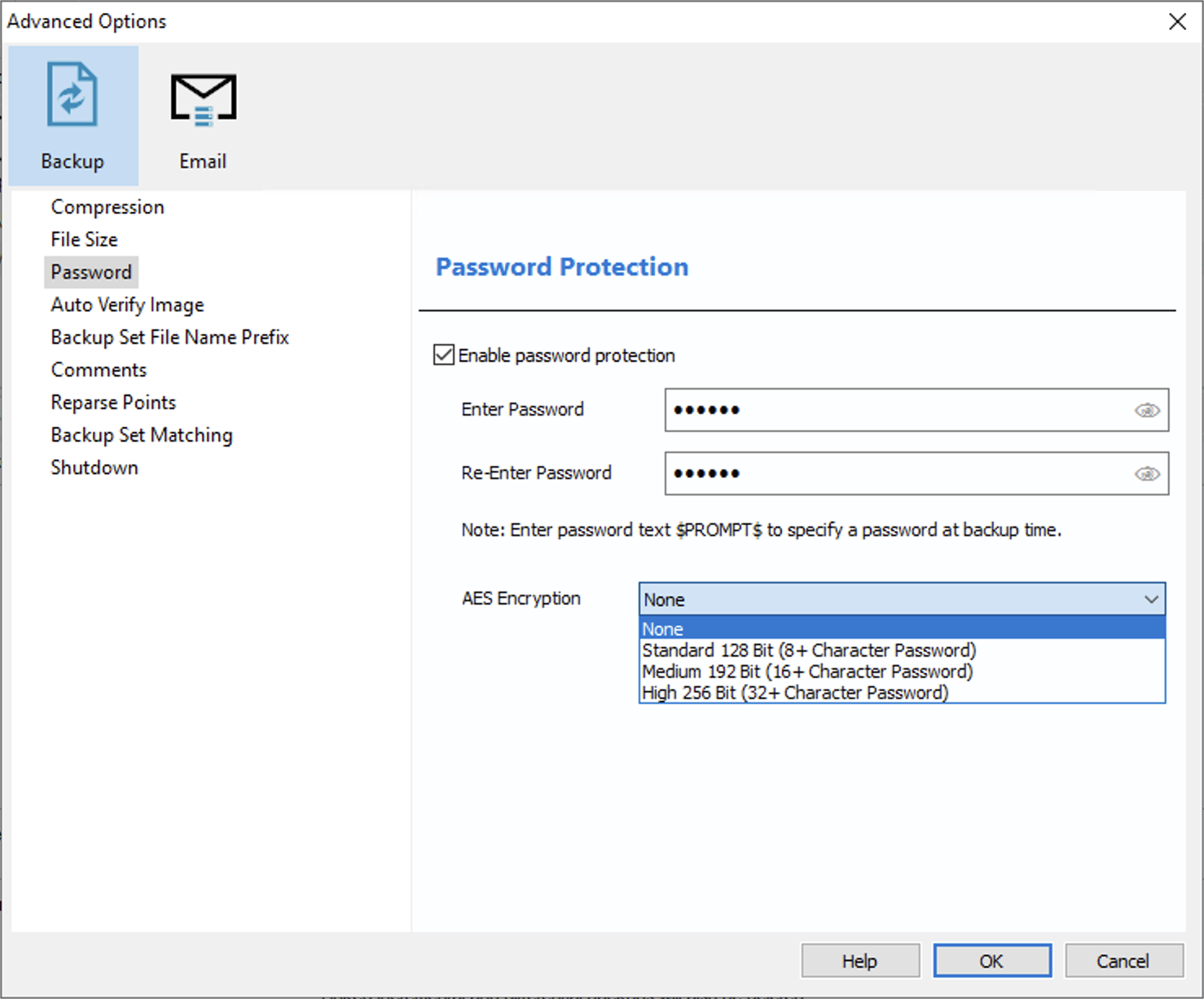
In the case of Macrium Reflect, there is no meaningful difference between the encryption options when it comes to attacking the password. We are getting the speeds of 457 passwords/second on a single Intel i7-9700K CPU, while GPU-accelerated speeds range from 2500 to 7100 p/s or even higher depending on the GPU used, regardless of the encryption algorithm.
Veeam Backup & Replication
Veeam claims to have over 400,000 customers worldwide, which makes Veeam Backup & Replication one of the more common Windows backup tools.
When making an encrypted backup, Veeam Backup & Replication creates several files. Metadata is typically saved into a .vbm file (backup metadata file), while the content is stored in .vbk (full backup) or .vib (incremental backup) files; however, the extensions depend on the source workload (virtual machines, physical machines or NAS):
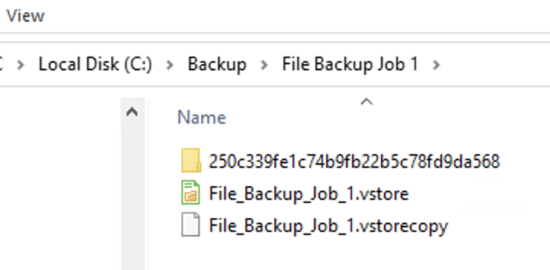
For this reason, we advise to look for the corresponding file in the file system when extracting Veeam encryption metadata:
If the user enables password protection, Veeam Backup & Replication uses AES-256 in CBC mode to encrypt the data. There is no choice of encryption algorithms or key lengths, and there are no artificial limitations when it comes to the password length.
The PBKDF uses SHA1, which is considered a less secure hash function due to the recently discovered collisions. The resulting speeds of brute-force attacks are high: using a single Intel i7-9700K CPU results in 7500 passwords per second, while GPU-accelerated recovery can break passwords at a rate of 45,000 to 120,000 passwords per second.
Benchmarks
We compared the speed of password recovery attacks among the three backup tools in different hardware configurations.
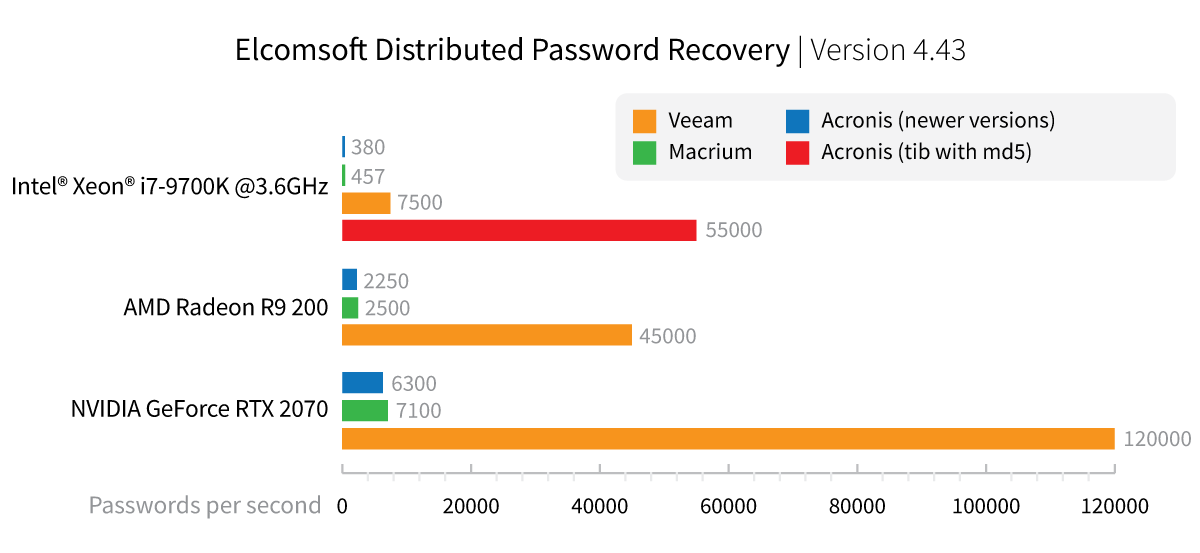
The older Acronis .tib format is the least secure of the three, with 55,000 passwords/s on a single CPU. Veeam offers comparatively weak protection with rather high recovery speeds using GPU acceleration. Macrium Reflect and recent versions of Acronis offer comparable protection.
How to Break Backup Passwords
When attacking a password, the traditional forensic workflow requires uploading the entire encrypted file or document into a password recovery tool. This approach, while simple and intuitive, has a major drawback when it comes to larger files such as system backups. The solution is obvious: use just the required minimum of information to run the attack. In the case of backups, this means you would only need a very small part of a file that contains the encryption metadata such as the hash and salt values. To use encryption metadata, you will need two tools working together: a tool to extract the encryption metadata from the files you are about to attack, and the tool that can use the extracted data to perform the attack.
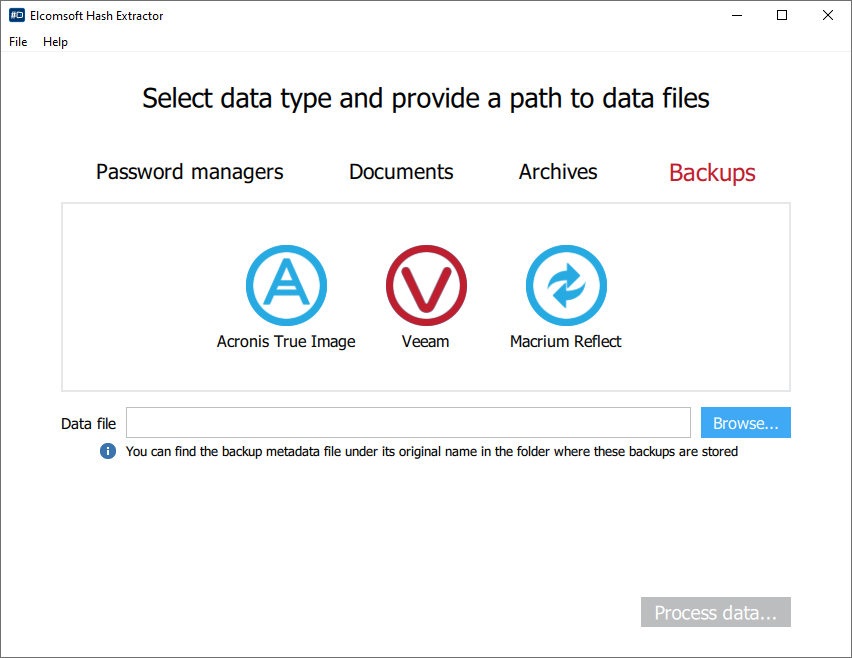
When using Elcomsoft Distributed Password Recovery, the encryption metadata is handled by a small tool: Elcomsoft Hash Extractor, which is included in the package. You will first need to run Elcomsoft Hash Extractor to extract encryption metadata from Acronis, Macrium, and Veeam backups, then open the extracted metadata in Elcomsoft Distributed Password Recovery to launch the attack.
To extract encryption metadata, follow these steps.
- Launch Elcomsoft Hash Extractor.
- From the main window, specify the type of files or documents you are about to extract hashes from.
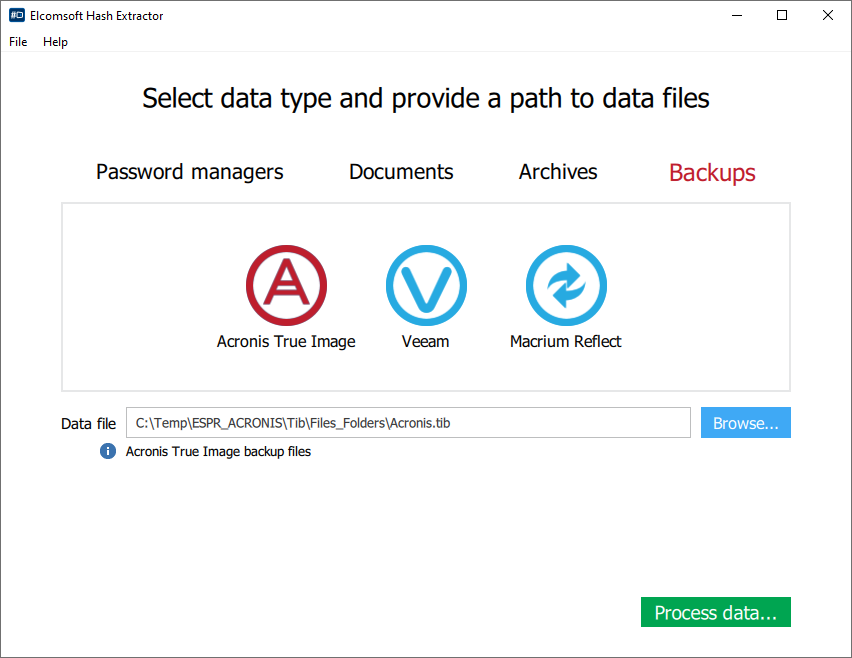
- Open the files and click Process.
- Save the resulting file.
Once you are done, collect the extracted hash files and open them in Elcomsoft Distributed Password Recovery instead of the original backups.











