Probing Linux Disk Encryption: LUKS2, Argon 2 and GPU Acceleration
August 16th, 2022 by Oleg Afonin
Category: «General»
Disk encryption is widely used desktop and laptop computers. Many non-ZFS Linux distributions rely on LUKS for data protection. LUKS is a classic implementation of disk encryption offering the choice of encryption algorithms, encryption modes and hash functions. LUKS2 further improves the already tough disk encryption. Learn how to deal with LUKS2 encryption in Windows and how to break in with distributed password attacks.
Disk Encryption Basics
Disk encryption tools rely on symmetric cryptography to encrypt data. The default encryption algorithm today is hardware-accelerated AES-256 encryption, although Microsoft BitLocker defaults to using AES-128. Some disk encryption tools offer the choice of encryption algorithms, while others can only alter the key length and/or encryption mode.
The symmetric encryption keys are derived from the user’s password (or other data) by using a Key Derivation Function (KDF). The KDF employs multiple rounds of one-way transformations (hashing) of the user’s input to produce a binary key. This binary key is rarely used directly to encrypt or decrypt data. Instead, it is typically used to protect and unprotect (wrap/unwrap) the actual symmetric encryption key. Different hash functions and with numerous hash iterations are used to slow down the speed of potential brute force attacks.
The Original LUKS Encryption
LUKS is a platform-independent disk encryption specification originally developed for the Linux OS. LUKS is a de-facto standard for full-disk encryption in Linux, facilitating compatibility among various Linux distributions and providing secure management of multiple user passwords. Today, LUKS is widely used in nearly every Linux distribution on desktop and laptop computers.
When attacking an encrypted disk, one must know the exact combination of encryption and hashing algorithms, as well as the number of hash rounds. Attacking a disk using the wrong parameters will not result in a successful recovery. LUKS offers users the choice of various encryption algorithms, hash functions and encryption modes, thus providing many possible combinations. The default encryption settings for LUKS encrypted disks are aes-cbc-essiv:sha256 with 256-bit symmetric encryption keys, but these can be changed by the user or the developers of a Linux distro. The exact encryption settings are stored in metadata in the encrypted disk’s header.
Elcomsoft Distributed Password Recovery automatically detects LUKS encryption settings by analyzing the encryption metadata, which must be extracted with Elcomsoft Forensic Disk Decryptor prior to launching the attack.
LUKS2: A Stronger LUKS
LUKS2 is a newer, better, and more secure version of LUKS. According to the developers, LUKS2 extends LUKS with more flexible ways of storing metadata, redundant information to provide recovery in the case of corruption in a metadata area. It also introduces an interface to store externally managed metadata for integration with other tools.
What is probably more important is the change in how LUKS2 implements the default Key Derivation Function (KDF). Instead of infinitely bumping the number of hash rounds to the millions, LUKS2 developers decided to go with Argon2, a key derivation function that was selected as the winner of the 2015 Password Hashing Competition. The new default KDF is designed to maximize resistance to GPU cracking attacks. The new KDF is as fast as the one used in the original LUKS when mounting the encrypted disk or performing other operations, yet by design it makes it very costly to perform large-scale hardware-accelerated attacks. This in turn required us to make use of the computer’s CPU instead of the much faster GPU to attack LUKS2 disks protected with argon2id .
The choice of Argon2 as a KDF makes GPU acceleration impossible. As a result, you’ll be restricted to CPU-only attacks, which may be very slow or extremely slow depending on your CPU. To give an idea, you can try 2 (that’s right, two) passwords per second on a single Intel(R) Core(TM) i7-9700K CPU @ 3.60GHz. Modern CPUs will deliver a slightly better performance, but don’t expect a miracle: LUKS2 default KDF is deliberately made to resist attacks.
What if a LUKS2 disk is protected with a KDF other than Argon2, such as PBKDF2+SHA-256? In this case, full GPU acceleration is available with much better speeds. The Intel(R) Core(TM) i7-9700K CPU @ 3.60GHz can enumerate 29 passwords per second, while using a NVIDIA GeForce RTX 2070 GPU results in 381 p/s, which is about 190 times faster than the speed of a CPU-only attack on Argon2.
Breaking LUKS2 Encryption Step 1: Extracting Encryption Metadata
To secure access to the data stored in the encrypted device, you must first recover the original, plain-text password. There are several steps involved requiring the use of several different tools.
- Extract the encryption metadata from the encrypted device or disk image using Elcomsoft Forensic Disk Decryptor or Elcomsoft System Recovery.
- Use the extracted metadata (a small file) to launch an attack on the password with Elcomsoft Distributed Password Recovery.
- Once the password is found, mount the disk volume, or decrypt the data.
We have two different tools for extracting LUKS encryption metadata. The choice of the right tool depends on whether you are working in the field or in a lab. If you are analyzing the suspect’s computer, Elcomsoft System Recovery can be used to boot the system from a USB flash drive and extract the encryption metadata from the storage devices connected to the computer.
Note: LUKS2 encryption is supported in Elcomsoft System Recovery 8.30 and newer. If you are using an older version of the tool, please update to the latest version to obtain LUKS support.
- Download Elcomsoft System Recovery, launch the installer and create a bootable USB drive.
- Use the USB drive to boot the target system into the Windows PE environment.
- Elcomsoft System Recovery will be launched automatically.
- Review the attached disks.
- Select LUKS2-encrypted partitions and click “Dump” to extract the encryption metadata.
- Transfer the encryption metadata on your computer and use it with Elcomsoft Distributed Password Recovery to launch an attack on the LUKS2 encryption password.
If you are working in a lab and processing disks or disk images, you’ll be using Elcomsoft Forensic Disk Decryptor. Extracting encryption metadata with Elcomsoft Forensic Disk Decryptor is simple.
Note: LUKS2 encryption is supported in Elcomsoft Forensic Disk Decryptor 2.20 and newer versions. If you are using an older version of the tool, please update to the latest version to obtain LUKS2 support.
- Launch Elcomsoft Forensic Disk Decryptor.
- Select “Extract/prepare data for further password recovery”.
- Open the physical device or disk image containing LUKS2 volume(s). In the example below, we’re dealing with a physical device.
- EFDD will display the list of encrypted volumes. Select the volume you are about to extract encryption metadata from.
- Click Next to extract the encryption metadata and save it into a file.
Breaking LUKS2 Encryption Step 2: Attacking the Password
While LUKS2 offers strong protection against brute force attacks by using Argon2(id), we have significant advances in password recovery attacks compared to what we had in the past. Brute-forcing a password today becomes significantly faster due to the use of CPU optimizations across the board, distributed and cloud computing. Up to 10,000 computers and on-demand cloud instances can be used to attack a single password with Elcomsoft Distributed Password Recovery.
To set up the attack, do the following.
- Launch Elcomsoft Distributed Password Recovery.
- Open the file containing the encryption metadata that you obtained with Elcomsoft Forensic Disk Decryptor during the previous step.
- The available key slots along with the number of hash iterations will be displayed. Specify the key slot to attack.
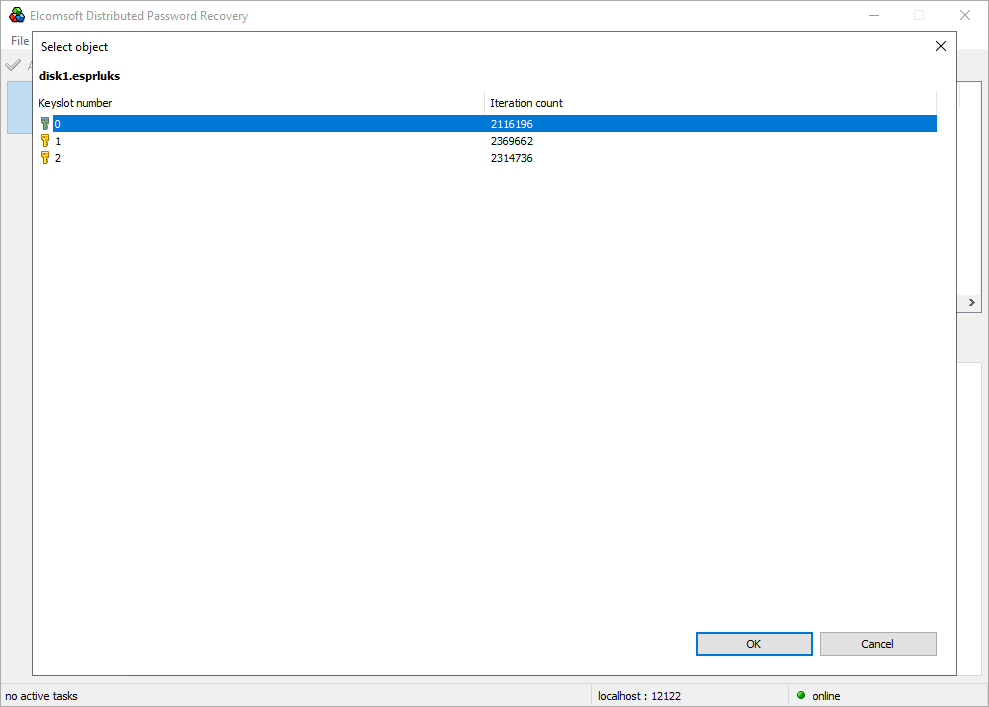
- Configure and launch the attack.
Brute force attacks became not just faster, but much smarter as well. The user’s existing passwords are an excellent starting point. These passwords can be pulled from the user’s Google Account, macOS, iOS or iCloud keychain, Microsoft Account, or simply extracted from the user’s computer. The user’s existing passwords give a hint at what character groups are likely used:
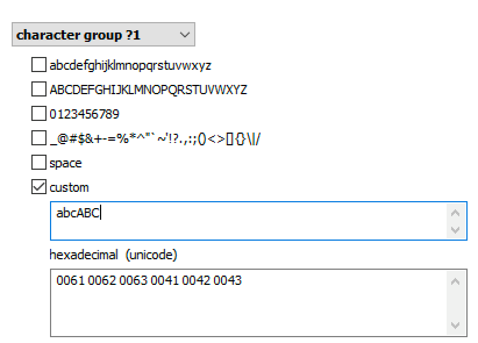
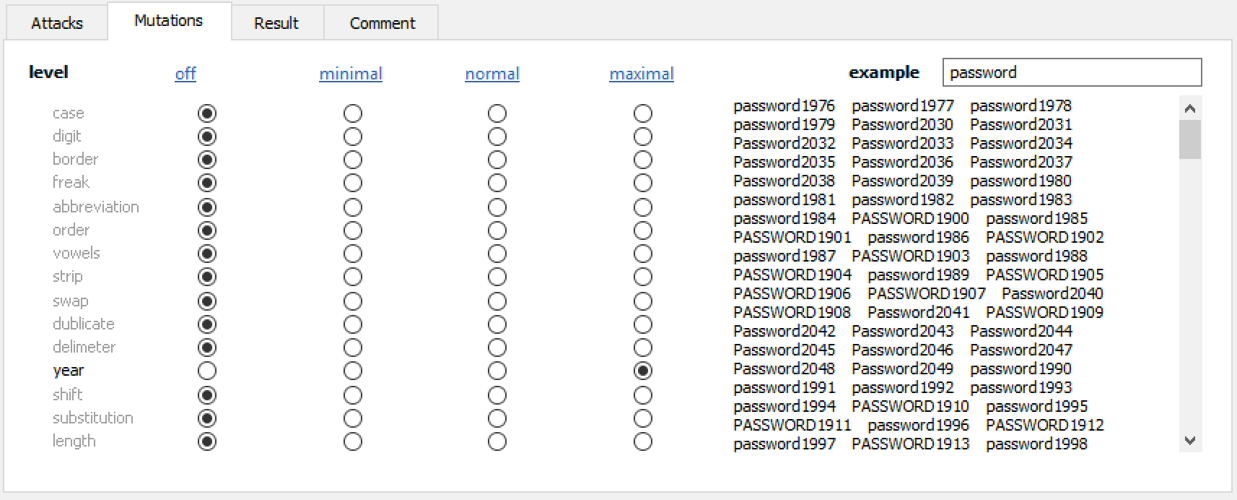
Elcomsoft Distributed Password Recovery offers a number of options to automatically try the most common variations of your password (such as the Password1, password1967 or pa$$w0rd):
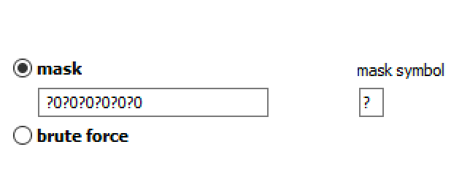
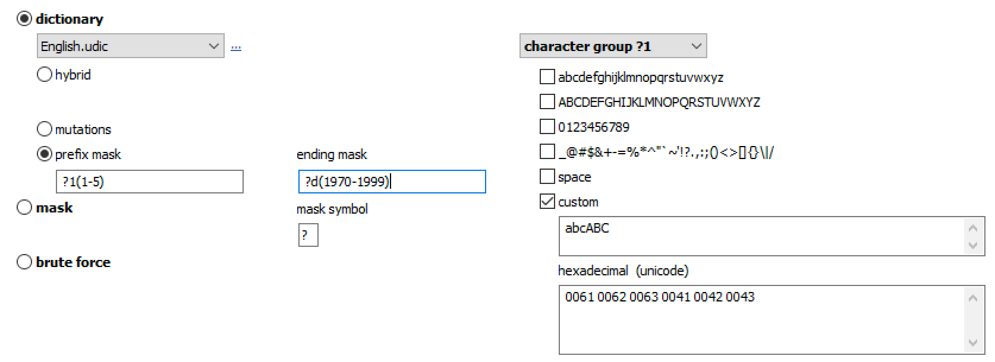
Masks can be used to try passwords matching established common patterns:
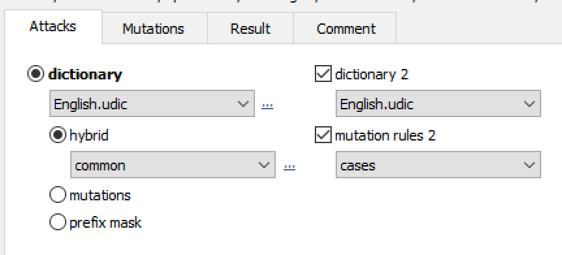
Advanced techniques allow composing passwords with up to two dictionaries and scriptable rules:
Conclusion
The original LUKS is still among the most commonly used encryption specifications in Linux. LUKS2 makes Linux disk encryption even more secure with a new Key Derivation Function, effectively banning GPU acceleration when attacking LUKS2 volumes.








