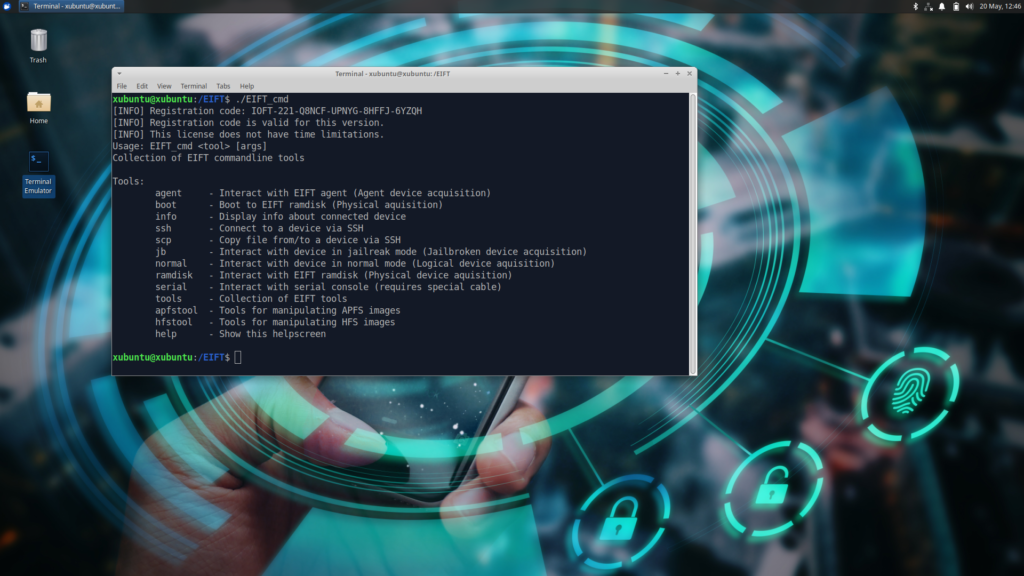
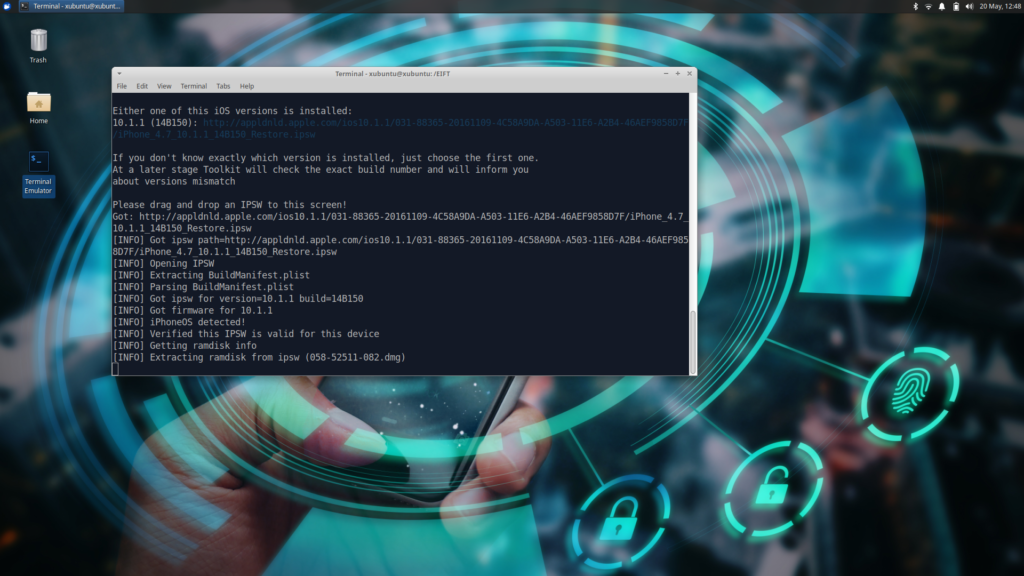
Acquiring data from iOS devices can be a complex task, particularly when performing bootloader-based extractions leveraging the checkm8 exploit. Traditionally, these extractions required access to a macOS computer. However, the Linux edition of iOS Forensic Toolkit offers a practical and efficient solution for forensic investigators who may not have macOS readily available. With minimal functional differences between the Mac, Windows, and Linux editions, the toolkit’s new, bootable Live Linux version allows for seamless bootloader-level extractions, booting from an external device and utilizing all the necessary tools without the need for a Mac.
This edition is especially beneficial for examiners working with Apple devices based on older chips, where the checkm8 exploit is applicable. By utilizing a flash drive or external SSD, users can quickly boot into a fully operational environment for low-level, bootloader-based extractions, ensuring they face no functional limitations. Support for recent versions of Apple Watch via wireless adapters is also exclusive to macOS and Linux editions. Essentially, the Live Linux edition is not limited to checkm8 extractions, supporting all the functions available in the Mac and Windows editions. There used to be a limitation disalloving the sideloading of the extraction agent (a different low-level extraction method) in certain circumstances in Linux and Windows, but this restriction had been effectively lifted.
The Live Linux edition is functionally identical to iOS Forensic Toolkit for Linux, yet in this edition we pre-configured the Linux environment with all dependencies already installed. Currently, the Live Linux edition only supports systems with an Intel or AMD CPU. We also have a version for ARMv8 computers (such as the Raspberry Pi 5), which is already available but still need more time to finalize.
Technical specifications and system requirements
- Host OS: Ubuntu
- iOS Forensic Toolkit: latest version preinstalled
- How to update: download and flash the latest Live Linux version from your Elcomsoft account
- System requirements: an Intel or AMD computer with x64/amd64 instruction set; 2GB RAM
- Storage: you will need an internal or external storage media formatted with NTFS or exFAT amd enough free space to fit extracted iOS images
Creating bootable media
You will need a fast, preferably solid-state storage device to boot from. We strongly recommend an external SSD drive, but a reasonably fast USB flash stick works just as well.
First, download a copy of the boot ISO. To access the download area, open https://www.elcomsoft.com/key.html and enter your EIFT registration key into the corresponding box. If you’ve lost your key, please contact us by filling out a form.
Once you have entered the key, you will see the following list of available editions:
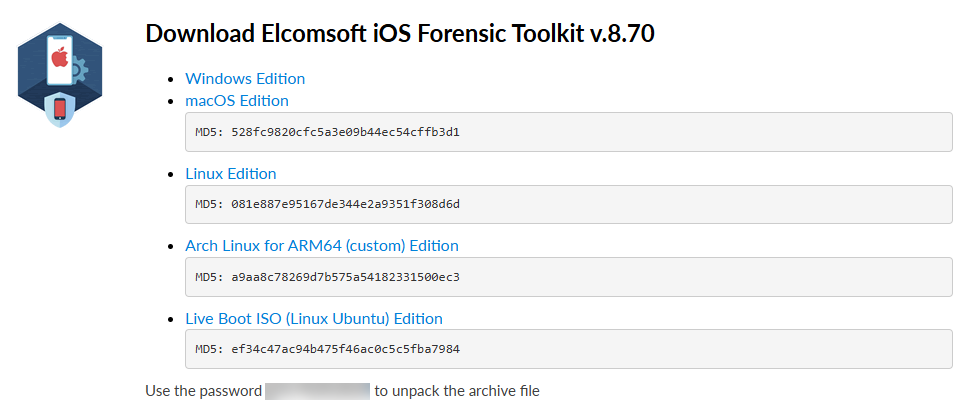
Important: make sure to verify the checksum after downloading the image. Corrupted or interrupted downloads will cause instability.
Next, burn the downloaded ISO onto an external storage device. Note that all data on that device will be erased. We recommend balenaEtcher, a free cross-platform open-source tool to flash OS images onto USB drives.
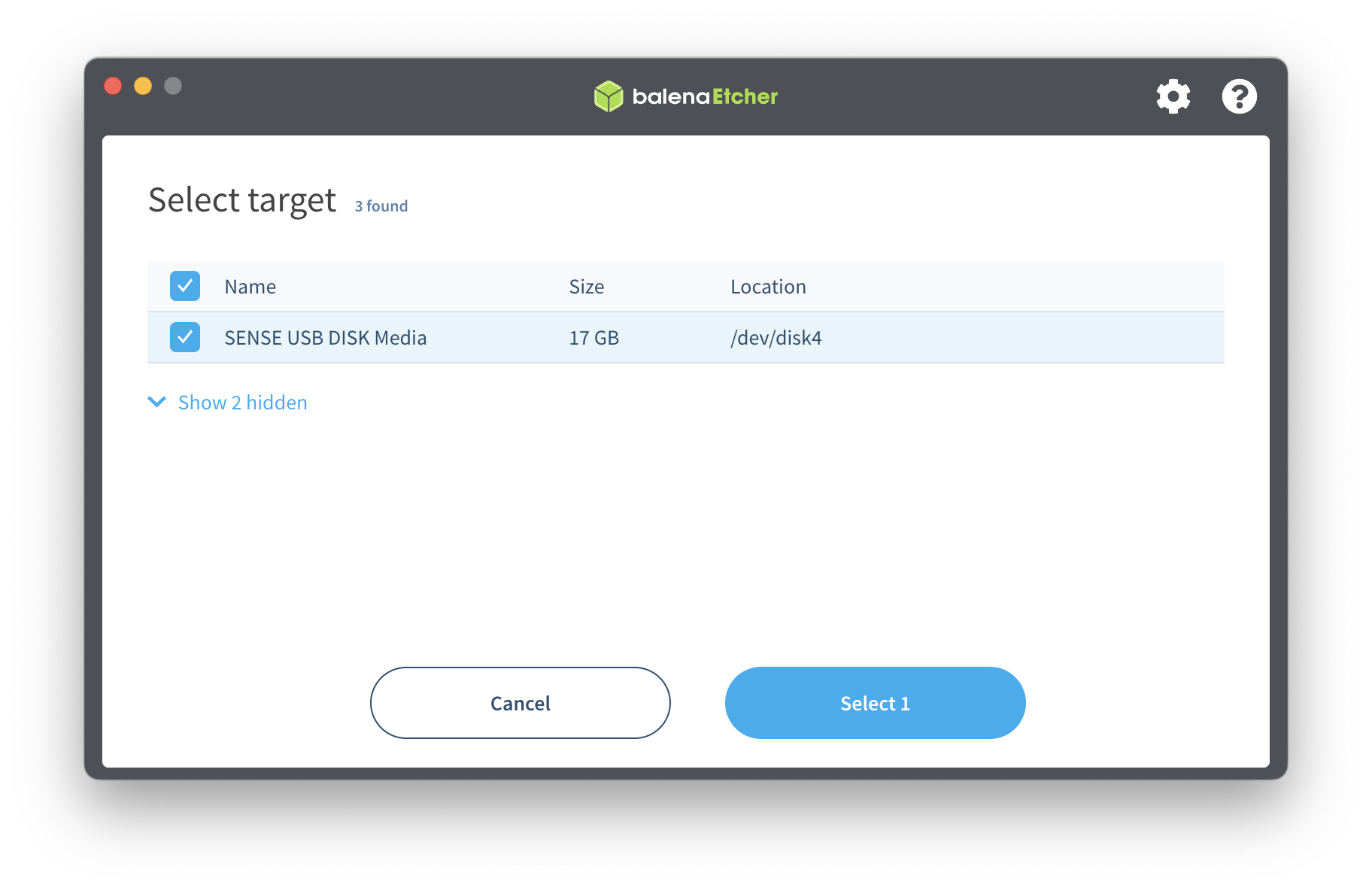
Select USB device and pick your ISO image, then click Flash.
If you use a slow flash drive, flashing may take a while. If this is the case, use a faster USB drive or burn the smaller Lite version instead.
Next, you will need to boot your computer from the flash drive you have just burned. To do that, you may need to enter your computer’s UEFI BIOS and allow booting from external devices and/or change boot order. These settings differ wildly across BIOS manufacturers, so there is no point in providing comprehensive instructions here as the steps will likely be different on your system.
Finally, when your computer is booted, you will be presented with a command line. At this time, you will need to plug in your EIFT USB license dongle; the toolkit will cease to work without it. Once you have the dongle inserted, you may start using iOS Forensic Toolkit.