When it comes to Windows forensics, some of the most valuable evidence can be stored deep inside system directories the average user never touches. One such source of evidence is the System Resource Usage Monitor (SRUM) database. Introduced in Windows 8 and still shipping today with the latest Windows 11 updates, SRUM collects detailed historical records about application usage and network activity. This database is a perfect source of data for reconstructing the user’s activities during an investigation. In this article, we’ll review the available types of data and demonstrate a way to access the SRUM database by using a bootable tool.
What is SRUM?
Basically, SRUM maintains records of networks connections made and applications launched on a system during the past 30 days. Its database, stored at %WinDir%\System32\sru\SRUDB.dat, uses the Extensible Storage Engine (ESE) format, the same format that is also used in Windows Search, Active Directory, and Exchange databases. By default, SRUM keeps this data for up to 30 days, although system administrators can change the retention period through Group Policy. Because it operates entirely in the background, most users have no idea it exists, and forensic specialists often overlook it as well.
Detailed application and network activity logs
From a forensic perspective, SRUM is highly valuable. It can show which applications were run, including their their file names and full locations on the disk, the accounts under which they were executed, and the exact times they started and stopped. The logs distinguish between foreground and background activity. Additional data such as CPU usage, disk I/O, and energy consumption (on portable devices) is also logged. Notably, SRUM also contains information about applications that have already been uninstalled, making it possible to analyze activity even after the corresponding software has been removed from the system.
The SRUM database also contains detailed logs about the computer’s network activities. Each network connection logged is linked to the process that initiated it, including the amount of data sent and received, the connection type (Wi-Fi, Ethernet, or mobile), network interface and any applicable network identifiers such as SSIDs or adapter names. Importantly, outgoing IP addresses and port numbers are also recorded, giving forensic experts a detailed look at where exactly the system was connecting. This is not only helpful during criminal investigations, but can be invaluable during incident investigations.
SRUM can be useful in various scenarios. For example, events from the SRUM database can be used to reveal presence, detect and identify certain types of malware, or discover the destinations of suspicious outbound traffic. During investigations, events from the SRUM database can show which programs have been run at specific times, and reveal and document the use of software that may no longer present on the computer.
Limitations of the SRUM database
Of course, SRUM has its share of limitations, the most important one being its volatility: once a system is booted, the contents of the SRUM database is constantly trimmed to only contain information for the past 30 days. For this reason, offline extraction is often recommended as opposed to live system analysis.
Importantly, SRUM only records information about remote IP addresses and ports. Local connections are not recorded. In addition, SRUM only logs the first packet of the connection (for identification purposes), not the full connection details. It is important to realize that SRUM does not capture the actual network traffic; it only records metadata. Finally, SRUM is stored in a binary format, and parsing it requires specialized tools.
Accessing the SRUM database
There are multiple ways to access and extract the contents of a SRUM database. Various commercial forensic tools typically bundle the ability to extract SRUM records. If you are analyzing a live session, a mounted disk image, or just have access to the srudb.dat extracted from a Windows PC, you can use an open-source tool srum-dump (GitHub) by Mark Baggett. The tool, as the name suggests, extracts all records from the SRUM database (administrative privileges are required if analyzing a live system) and exports them into an Excel spreadsheet. srum-dump is a great training tool, which can help you get accustomed to what’s inside a SRUM database.
If you are not doing live system analysis, you can quickly analyze or export the content of the SRUM database with Elcomsoft System Recovery, a portable, bootable field analysis tool designed for rapid decision-making during on-site investigations. Built on a preconfigured Windows PE environment, Elcomsoft System Recovery offers a forensically sound environment for digital investigations. With its latest update, the tool gained the ability to parse and analyze the SRUM database on the computer being investigated. Investigators can directly access and review records of application launches, network activity, resource consumption, and more, presented in a human-readable format. (Note that this functionality was added into Elcomsoft System Recovery 8.32, so you need at list this version of the tool to access it).
Technically, the SRUM analysis is located among the other Forensic Tools, which also include the ability to list the installed apps, review the timeline, access recent files and folders, access records from the event log, and search for diverse forensic artifacts.
There is only one SRUM database file per Windows installation, so it will be detected, loaded, and parsed automatically.
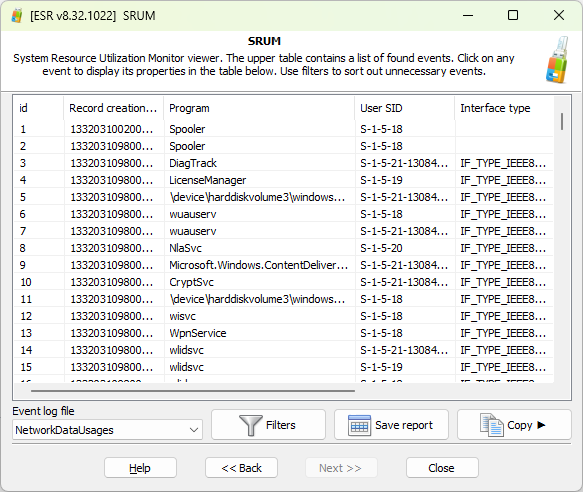
When analyzing the contents of the SRUM database, you can select the desired source or events (under “Event log file”), such as network data usage; apply custom filters, or save a plain text report.
Conclusion
It is hard to overestimate the value and significance of the SRUM database. Relatively little known, SRUM is rarely cleared by computer users, often enabling access to events that have already been cleared from sources that are better known – such as the Windows Event Log.




