iOS Forensic Toolkit: Exploring the Linux Edition
November 30th, 2023 by Oleg Afonin
Category: «General»
The latest update of iOS Forensic Toolkit brought an all-new Linux edition, opening up a world of possibilities in mobile device analysis. The highly anticipated Linux edition preserves and expands the features previously available to macOS and Windows users. Forensic professionals can now perform advanced logical and low-level extractions with the aid of a custom extraction agent and extract information using the bootloader-level exploit, making forensic analysis more accessible on Linux platforms.
But why is the Linux edition such a big deal? For starters, it can run on a large number of existing Linux computers powered by some of the most popular Linux distros, making it more accessible to a broader range of experts. It eliminates the need for expensive Apple hardware, potentially saving costs and making forensic analysis more affordable. Plus, the toolkit being available on Linux means it can run on computers that are more affordable compared to Apple Macs, ensuring accessibility without compromising on functionality. What makes this edition stand out compared to the Windows version of the tool is its support for forensically sound bootloader-level extraction, a feature previously exclusive to macOS.
Elcomsoft on GitHub
As a provider of mobile forensic tools, we at Elcomsoft strongly believe in giving back to the community. Our iOS Forensic Toolkit (EIFT) is a highly complex and powerful mobile acquisition tool, consisting of almost eighty sub-projects, many of which are open source. While we have benefited from the contributions of the community, we also believe in contributing back to the open source community by publishing our changes to those projects as required by their permissive license.
As a company, we are wholly dedicated to providing a solution that complies with licensing regulations, meeting all pertinent legal requirements. In addition to fulfilling our legal obligations, we want to point out the other benefits to open sourcing some of our projects. Collaboration with the open source community can result in faster updates, improved features, and greater security. By sharing our efforts, we can help each other to build better tools, rather than reinventing the wheel. We welcome everyone to check out our GitHub account containing the relevant open-source projects:
Supported Linux distros
The tool has been tested on multiple Linux distributions, officially supporting the current Debian, Ubuntu, Kali Linux, and Mint distros, ensuring seamless operation for forensic professionals using different Linux setups.
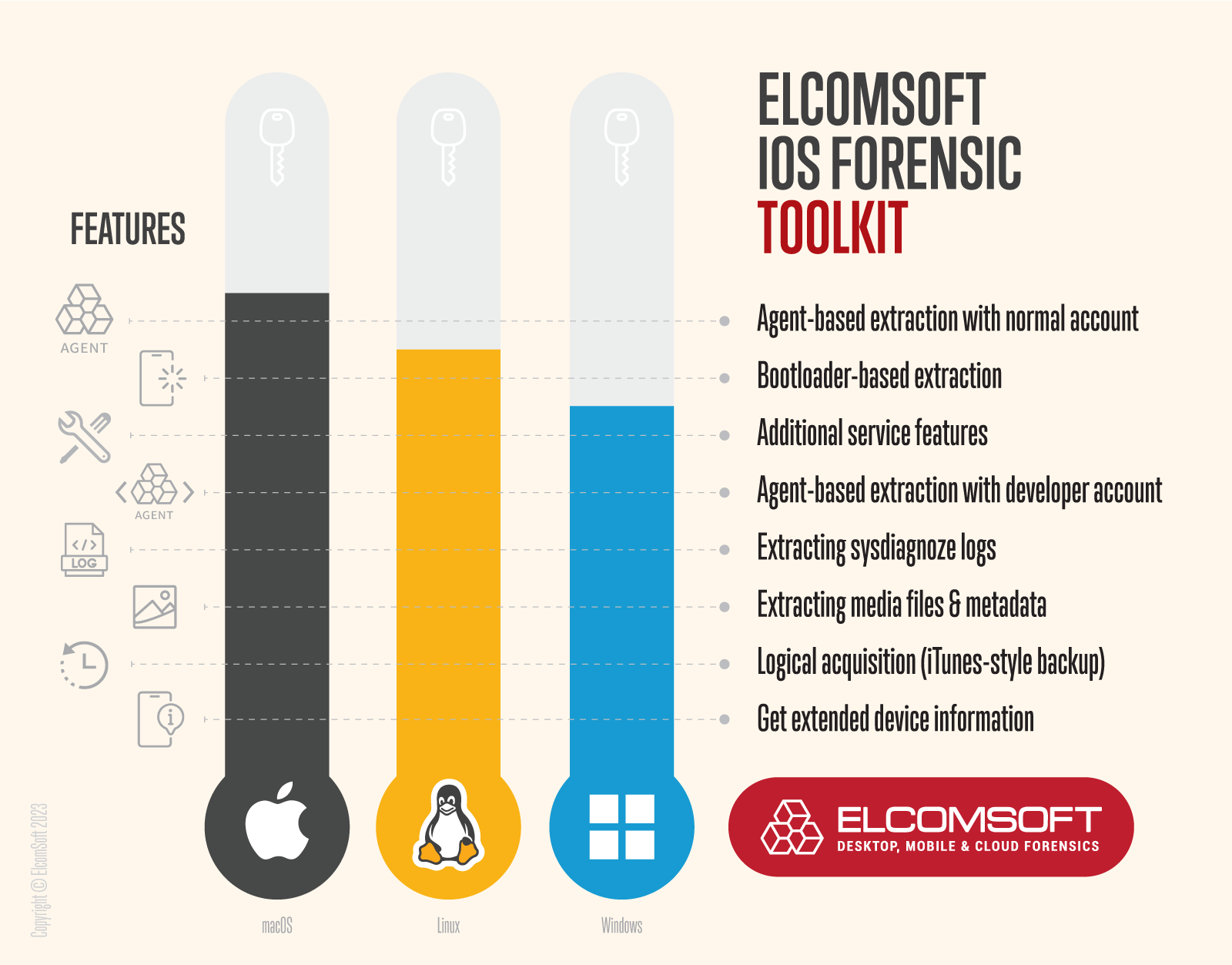
Edition comparison
In a bid to bridge feature gaps between editions, the Linux edition inherits many features previously exclusive to the Mac edition, yet certain differences still remain. The Windows edition of iOS Forensic Toolkit supports logical and agent-based extraction methods, but lacks support for bootloader-based extractions, which are only available for macOS and Linux platforms. The ability to sign the extraction agent using a regular, non-developer Apple ID remains an exclusive feature of the Mac edition. Please refer to the following chart to learn more about the differences between editions. Finally, bootloader-level extraction of iOS 16 devices remains a macOS exclusive feature for the time being.
Installing the Linux edition
The installation process of the Linux edition differs slightly from installing either Mac or Windows versions of the tool. Start by unpacking the archive to a folder of your choice (the installation folder) using the password provided in the registration email. Once this is done, cd to the installation folder and run the following command to download and install dependencies:
sudo apt install ./com.elcomsoft.eift-dependency.deb
If you need Apple Watch extraction support, you will also require this additional package that contains a modified USB driver supporting the newer versions of Apple Watch:
sudo apt install ./com.elcomsoft.usbmuxd2.deb
Obviously, you’ll need Internet connectivity to download the required dependencies.
Command-line interface
iOS Forensic Toolkit for Linux uses the same command-line interface first introduced in macOS and Windows editions, sharing commands and switches across platforms. Leveraging the command line provides complete control throughout the extraction workflow, allowing experts to stay in control if any step of the process requires additional attention.
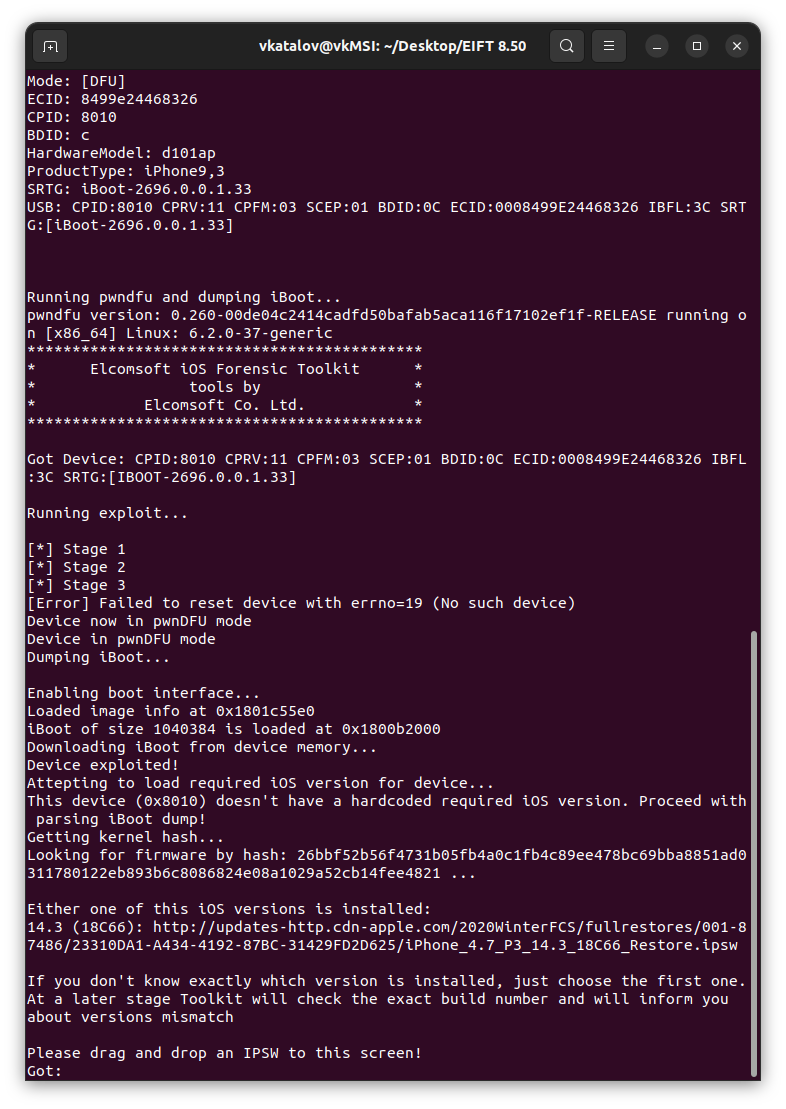
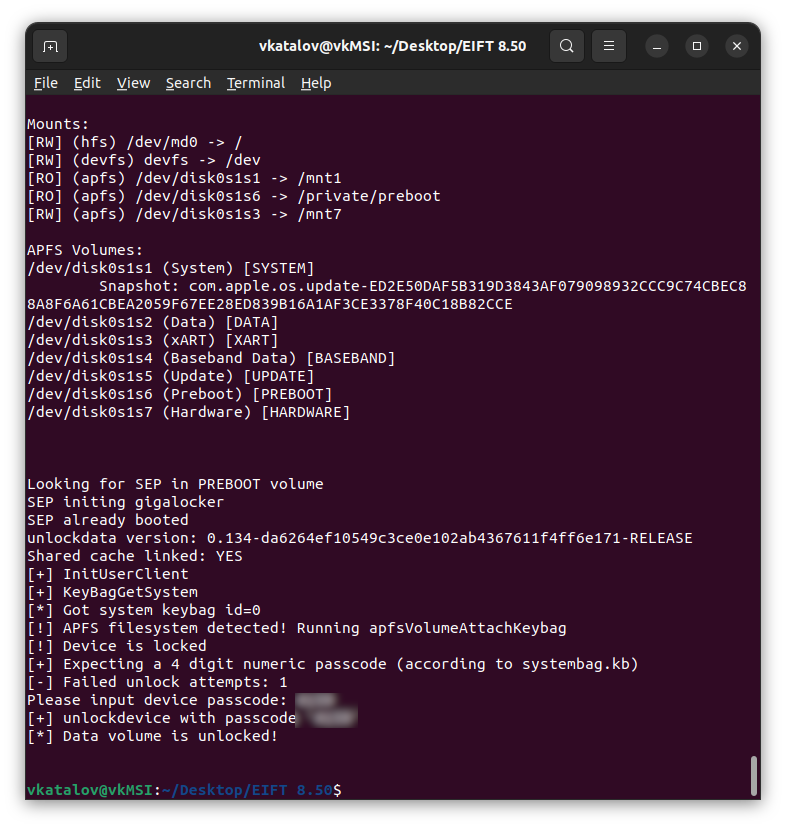
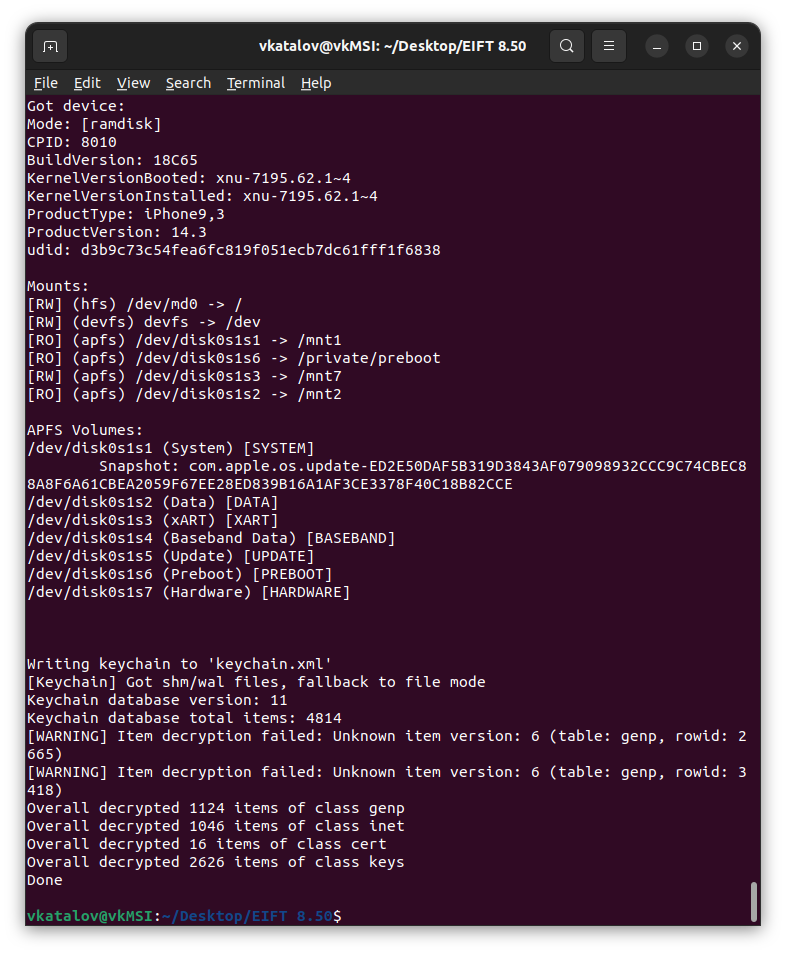
One more thing
Last but not least, this update brings a significant improvement in precise iOS version identification during bootloader-level extraction. Formerly, the toolkit attempted to guesstimate the installed iOS version based on the version of iBoot, which sometimes resulted in multiple download links in cases where we could not pinpoint the exact version of iOS. The new approach achieves a nearly 100% accurate identification of the iOS version, eliminating any ambiguity in the extraction process.
Last but not least, we’ve added advanced logical extraction support for devices running iOS 17.






