This time, we are updating our bread-and-butter mobile forensic tool, Elcomsoft Phone Password Breaker, to version 3.0 (beta). This new version has many things that are new or have changed. Let’s see what’s new, and why.
Cross-Platform Compatibility
No, we haven’t released a Mac OS version yet. But we’ve made the last step we needed to do to make it happen. EPPB 3.0 features an all-new user interface based on the cross-platform Qt library. This was the last obstacle stopping us in porting the code to different platforms. We expect to see a Mac OS version in the next few months.
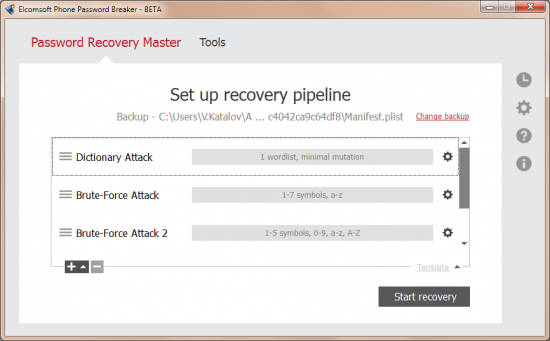
However, the new GUI is not all about cross-platform compatibility. With Qt, we brought in full drag-and-drop support, new controls, and overall better and slicker looks.
BlackBerry 10 Support
When BlackBerry 10 was released, the security model was changed. Unlike before, local backups produced by BlackBerry Link are always encrypted with a highly secure encryption key. This key depends on BlackBerry ID, and is stored deep in the device. Technically speaking, extracting this key is impossible, yet after a lot of research we were able to get it by using a BlackBerry service request.
So what happens when the user creates a backup with BlackBerry 10? At the time a new BlackBerry device is initialized with the user’s BlackBerry ID and password, the device connects to a BlackBerry server and receives a binary encryption key dependent on the BB ID. This key is then written to a secure area in the device. This area is not accessible from the outside; only BlackBerry OS can access information stored in that area.
This key is highly secure. Apparently, it’s tied to the user’s BlackBerry ID, and is stored on the server, allowing the user to initialize a new device with the same data. We don’t know the way it’s generated (and if we do know, we won’t tell). Most probably, the key is some form of hash based on BlackBerry ID. The key is not changed when the user changes BB password, and remains the same with new BB hardware.
So, when the user creates a backup with BlackBerry Link (earlier versions used less secure Blackberry Desktop Software), the tool simply passes the command to the BlackBerry device. The device core encrypts information on the fly, and passes it to BlackBerry Link already encrypted. In a way, BlackBerry Link does not make backups at all; it simply receives an encrypted data stream and saves it into a file.
What happens when the user restores a BB device? The device is first initialized with a BB ID via the BlackBerry server. The encryption key is transmitted from the server, and securely stored in the device. Now, when the device receives encrypted data stream from BlackBerry Link, it can decrypt it and restore data. The decryption occurs in the core; decrypted data never leaves the device, let alone the encryption key itself.
So what did we do, exactly?
We reverse-engineered the initialization request, emulating a fresh BlackBerry device being activated with a certain BB ID (which is stored in the backup file in plain text). Just like with Apple iCloud, you must supply the correct password to that BB ID. If you do, our software will acquire the encryption key from the BlackBerry server, and use it to instantly decrypt local backups. Sounds simple? Believe us, it was a nightmare of a work! However, we did it, and so far we are the only company who can do anything with BB 10 backups.
So what do you get after entering the user’s BB ID and password? Our tool decrypts backup data, producing three archives with the following content:
- Application data
- Media files (pictures and videos)
- Settings
Interestingly, BlackBerry also backs up applications. While we receive the apps, we don’t save them to a file due to copyright reasons.
Most information in these archives is available in plain text or SQLite format. They can be analyzed with commonly available mobile forensic software such as Oxygen Forensic Suite.
Cloud Acquisition of Windows Phone 8
Windows Phone 8 can store data in a cloud service called My Windows Phone. Unlike Apple, Microsoft does not create a full cloud backup. Instead, information is stored in separate pieces in an obscure format. As a result, manually analyzing this data is a nightmare, even if you know the user’s Live ID and password.
In order to acquire data from My Windows Phone cloud, we download information one chunk after another, creating an artificial “backup”. The data in this backup file is stored predominantly in SQLite format, allowing investigators to use readily available forensic tools to analyze its content. In addition, we extract and save the list of devices registered on a certain My Windows Phone account.
Apple Tells You to Make Backups
Always having a fresh backup of your mobile device is a must. We assembled a list of articles from Apple Knowledge Base explaining why to make backups, and how to configure your iOS device to make them.
iCloud: Back up your iOS device to iCloud
iCloud: Restore your iOS device from iCloud
iCloud: Troubleshooting restoring an iCloud backup
iCloud: iCloud storage and backup overview
iOS: Unable to restore from backup of a newer device
iOS: Back up and restore your iOS device with iCloud or iTunes
iTunes: About iOS backups
Choosing an iOS backup method (Should I use iTunes or iCloud to back up my iOS device?)
Recovering iCloud contacts, calendars, and bookmarks from an iTunes backup of an iOS device
iOS: If you can’t back up or restore from a backup in iTunes
iCloud: iCloud security and privacy overview





