The previous article was about the theory. In this part we’ll go directly to practice. If you possess a turned on and locked iOS device and have no means of unlocking it with either Touch ID or passcode, you may still be able to obtain a backup via the process called logical acquisition. While logical acquisition may return somewhat less information compared to the more advanced physical acquisition, it must be noted that physical acquisition may not be available at all on a given device.
Important: Starting with iOS 8, obtaining a backup is only possible if the iOS device was unlocked with a passcode at least once after booting. For this reason, if you find an iPhone that is turned on, albeit locked, do not turn it off. Instead, isolate it from wireless networks by placing it into a Faraday bag, and do not allow it to power off or completely discharge by connecting it to a charger (a portable power pack inside a Faraday bag works great until you transfer the device to a lab). This will give you time to searching user’s computers for a lockdown record.
If you have a powered-on but locked iPhone, using a lockdown record to obtain a backup may be your only chance to perform acquisition. In most cases, this will be the only method that can extract keychain items.
Very important: You can obtain a backup of a locked device only if you possess a non-revoked pairing record, and the device has been unlocked at least once before the seizure. If the device has been turned off or rebooted at least once after the seizure, you will not be able to use the lockdown record unless you are able to unlock the device with a passcode. You’ve seen this warning before, maybe more than once. We’ll keep repeating it because it’s really, really important to keep the phone powered on all the time between the seizure and acquisition.
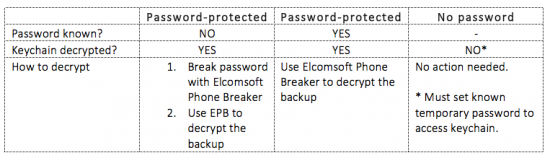
Password-Protected vs. Unencrypted Backups
Users of iOS devices have the ability to protect backups with a password. This option can be set in iTunes as they an offline backup. If a backup password is specified, you will not be able to change or remove that password without entering it first. In other words, you will need to break that password using Elcomsoft Phone Breaker (see below for a practical guide).
An important difference between password-protected iOS backups and backups that have no password is encryption. If the user specifies a backup password, the full content of the backup will be encrypted with that password.
If, on the other hand, there is no backup password specified, the backup will come out partially unencrypted. In this case, “partially unencrypted” means that some data (such as the keychain) will still come out encrypted. However, as opposed to password-protected backups, the keychain will be encrypted with a strong, hardware-dependent key that cannot be recovered or extracted from any 64-bit device equipped with Secure Enclave (iPhone 5s and newer models).
 If the user specified a backup password in iTunes, no unencrypted data ever leaves the phone. All encryption is performed by iOS inside the device (iPhone, iPad). iTunes acts as a simple receiver, pulling encrypted data stream from the device and saving it into files on your hard drive. There is no way to intercept plain data since there is none.
If the user specified a backup password in iTunes, no unencrypted data ever leaves the phone. All encryption is performed by iOS inside the device (iPhone, iPad). iTunes acts as a simple receiver, pulling encrypted data stream from the device and saving it into files on your hard drive. There is no way to intercept plain data since there is none.
If you find a phone set up with an unknown backup password, produce a backup nevertheless. Use Elcomsoft Phone Breaker to recover the original password by running an attack.
Acquisition of iOS Devices Post Shut Down/Reboot
What happens if you find the device that is turned off, or if you attempt to acquire a device that was turned off or allowed to reboot before you started acquisition? In this case, even if you have a valid, non-revoked and unexpired lockdown record, you will not be able to use it to obtain a backup. Not before you unlock the device at least once, in which case you won’t need bothering with a lockdown file at all. In other words, you’ll need to know the passcode to obtain a backup.
Walkthrough: How to Use Lockdown Records to Obtain a Backup
In order to use lockdown records to make a backup of an iOS device, you will need all of the following:
- An iOS device that is powered on and that was unlocked with a passcode at least once after last reboot
- A lockdown file extracted from the user’s Mac or PC
- A copy of Elcomsoft iOS Forensic Toolkit (to obtain a backup using a lockdown file)
- A copy of Elcomsoft Phone Breaker (to decrypt backups; to break unknown backup password)
Extracting Lockdown Files
You must extract the correct lockdown record from the user’s computer in order to use it with Elcomsoft iOS Forensic Toolkit for logical acquisition. Lockdown records are stored at the following locations:
Windows Vista, 7, 8, 8.1, Windows 10: %ProgramData%\Apple\Lockdown
(Sample path: C:\ProgramData\Apple\Lockdown\6f3a363e89aaf8e8bd293ee839485730344edba1.plist)
Windows XP: %AllUsersProfile%\Application Data\Apple\Lockdown
(Sample path: C:\Documents and Settings\All Users\Application Data\Apple\Lockdown\6f3a363e89aaf8e8bd293ee839485730344edba1.plist)
macOS: /var/db/lockdown
Note: On systems running macOS Sierra, administrative privileges are required to extract lockdown files. Use “sudo cp (source path)/lockdown/{id}.plist (destination path)” when extracting lockdown files from live systems (password required). Alternatively, lockdown files may be extracted from a forensic disk image.
In these folders, you may see multiple .plist files. Their names correspond to UUID identifiers or iOS devices that were paired with the computer. Discovering the UUID of the device being investigated is as easy as using the “I” command in Elcomsoft iOS forensic Toolkit and analyzing the resulting XML document:
<?xml version=”1.0″ encoding=”UTF-8″?>
<!DOCTYPE plist PUBLIC “-//Apple//DTD PLIST 1.0//EN” “http://www.apple.com/DTDs/PropertyList-1.0.dtd“>
<plist version=”1.0”>
<dict>
<…>
<key>UniqueDeviceID</key>
<string>0a226c3b263e004a76e6199c43c4072ca7c64a59</string>
</dict>
</plist>
Tip: You may want to copy these files to a new folder on your computer, and give them shorter names for easier reference. Since Elcomsoft iOS Forensic Toolkit is a tool based on the command line, you’ll have to type these names when using them with the product.
More information about lockdown files and their location is available at
https://support.apple.com/en-us/HT203887
Obtaining a Backup
In order to obtain a backup, do the following.
- Launch Elcomsoft iOS Forensic Toolkit by using the “Toolkit-JB” command. Make sure the license protection dongle is attached to a USB port.
- Connect iOS device being extracted to another USB port.
- In Elcomsoft iOS Forensic Toolkit, select option “B – Create iTunes-style backup of the device”. If this option does not appear in the main menu, make sure you are using iOS Forensic Toolkit 2.1 or newer, and that you are using the “Toolkit-JB” command as opposed to the legacy “Toolkit”.
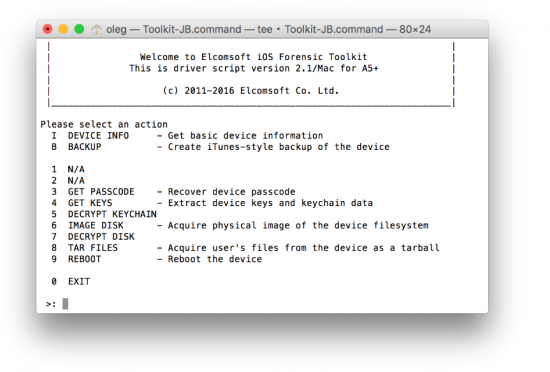 Note that iOS Forensic Toolkit does not require Apple iTunes to be installed on the computer in order to perform the backup.
Note that iOS Forensic Toolkit does not require Apple iTunes to be installed on the computer in order to perform the backup.
- When prompted, enter path to lockdown record you extracted. Giving lockdown files shorter names makes this step easier.
- If a lockdown record is not accepted, try other lockdown files corresponding to the same UUID if available (e.g. extracted from other computers).
- If an iOS device being acquired is configured to produce backups without a password, iOS Forensic Toolkit will automatically set a known backup password prior to acquisition. The temporary password is “123”. If this is the case, skip directly to “Viewing and analyzing backups”.
- If the backup password is set by the user and you don’t know it, obtain a backup nevertheless. You will have to perform an attack (brute-force, dictionary, or combination) with Elcomsoft Phone Breaker in order to recover the password.
Conclusion
It may be possible to perform acquisition of iOS devices found locked but powered-on. Lockdown files may exist on the user’s Mac or PC. Those files can be used to obtain backup from an iOS device provided that the device was never allowed to power off or reboot after the seizure. Following established guidelines on seizing and storing mobile devices is a must for successful acquisition.
Tools and References
This article references multiple KB articles, whitepapers, and tools.
Tools:
References:




