Two-factor authentication a roadblock when investigating an Apple device. Obtaining a data backup from the user’s iCloud account is a common and relatively easy way to acquire evidence from devices that are otherwise securely protected. It might be possible to bypass two-factor authentication if one is able to extract a so-called authentication token from the suspect’s computer.
Authentication tokens are used by iCloud Control Panel that comes pre-installed on macOS computers, as well as iCloud for Windows that can be installed on Windows PCs. Authentication tokens are very similar to browser cookies. They are used to cache authentication credentials, facilitating subsequent logins without asking the user for login and password and without prompting for secondary authentication factors. Authentication tokens do not contain the user’s password, and not even a hash of the password. Instead, they are randomly generated sequences of characters that are used to identify authorized sessions.
Tip: The use of authentication tokens allows bypassing two-factor authentication even if no access to the secondary authentication factor is available.
Extracting an authentication token and re-using it on a different computer may allow to sign in to the user’s Apple ID services, which includes access to iOS backups stored in iCloud and iCloud Drive. In order to make use of authentication tokens, one must install a cloud acquisition tool such as Elcomsoft Phone Breaker.
The Forensic edition of Elcomsoft Phone Breaker comes with the ability to acquire and use authentication tokens from Windows and Mac OS X computers, hard drives or forensic disk images. Authentication tokens for all users of that computer can be extracted, including domain users (providing that their system logon passwords are known). The tools are available in both Windows and Mac versions of the tool.
Authentication tokens are obtained from the suspect’s computer on which iCloud Control Panel is installed. In order for the token to be created, the user must have been logged in to iCloud Control Panel on that PC at the time of acquisition. Authentication tokens can be extracted from live systems (a running Mac OS or Windows PC) or retrieved from users’ hard drives or forensic disk images.
iCloud Control Panel is an integral part of Mac OS systems, and installs separately on Windows PCs. Most users will stay logged in to their iCloud Control Panel for syncing contacts, passwords (iCloud Keychain), notes, photo stream and other types of data without re-typing their password. All this means that the probability of obtaining authentication tokens from PCs with iCloud Control Panel installed is high.
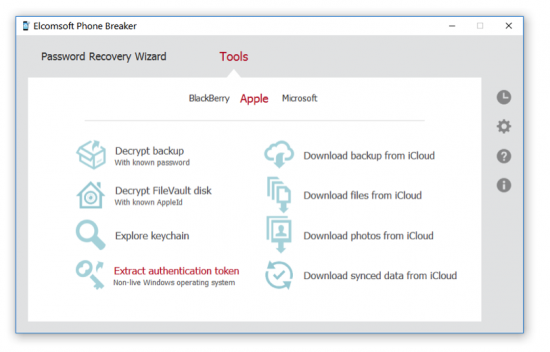
Extracting Authentication Tokens
To extract iCloud authentication token, launch Elcomsoft Phone Breaker (Forensic Edition) and click “Extract authentication token” on the main window.
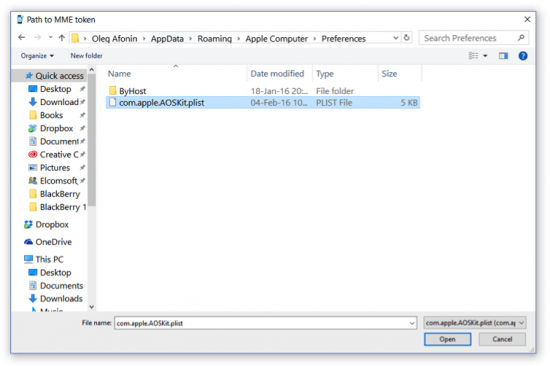
Specify path to the token file (usually %appdata%\Apple Computer\Preferences\)
Specify path to the user’s master key, which is required to decrypt the token, then click “Extract”.
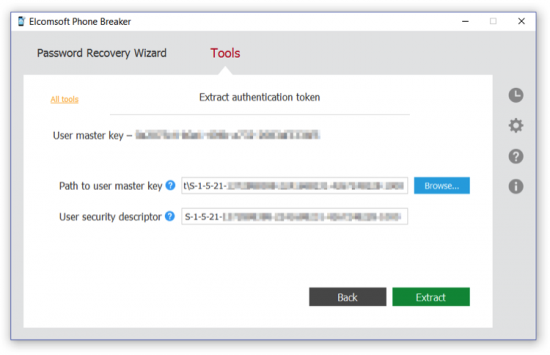
Elcomsoft Phone Breaker will extract, decrypt and display the token. You will be able to export the token into a file. You can now use this token to log into iCloud and download backup from iCloud or download files from iCloud.
If you are using a Mac OS X computer, follow the guidelines published on ElcomSoft Web site:
http://www.elcomsoft.com/help/en/eppb/extracting_authentication_mac.html
Up to date information on extracting authentication tokens is available at
https://www.elcomsoft.com/help/en/eppb/index.html?extracting_token_on_non-live_w.html
Using Authentication Tokens to Download iCloud Backups
Downloading an iCloud backup using an authentication token works very similar to using Apple ID and password. Instead of using the Apple ID and password combination, you’ll need to supply an authentication token. Note that two-factor authentication is successfully bypassed if you use the token.
- In the Tools menu, select the Apple
- Select Download backup from iCloud.
- On the Download backup from iCloud page, define authentication type as Token.
- Copy the token from the file, and paste it into the “Token” box.
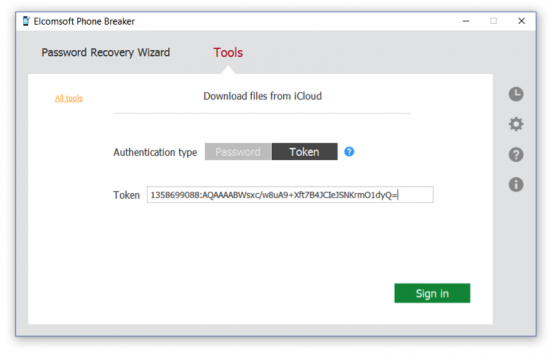
- Click Sign In to continue downloading the backup. If the token has not expired, you will be able to sign in without entering the user’s Apple ID, password, or the secondary authentication code.

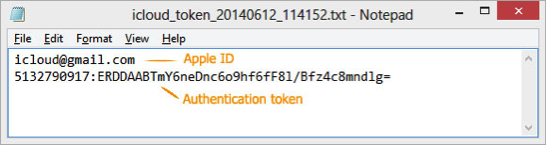
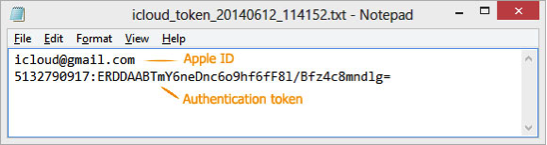
Note that you need to copy the full Authentication token string from the text file you’ve extracted. On the following screen shot, the entire second line of the text file represents the authentication token: