According to Jim Baker, FBI General Counsel, the bureau can access information on most smartphones they are dealing with, even if encryption is enabled. In this article, we tried to find out which devices they can and cannot unlock, and why.
The FBI Can Unlock 87% Mobile Devices
According to Jim Baker, the agency can unlock some 87% of mobile devices, and get access to the data. So which devices they can and cannot unlock, exactly? Before we start crunching the numbers, please have a look at the following infographics:
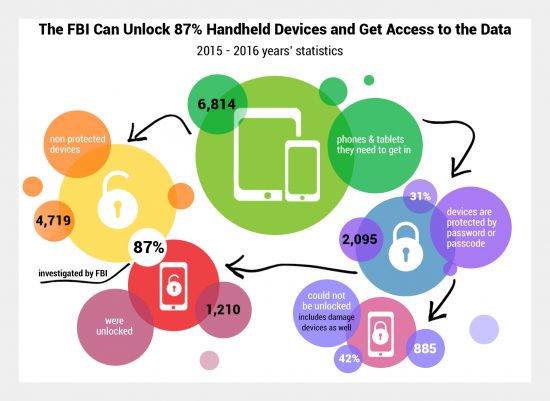
In the fiscal year 2016 (Oct 1, 2015 through Sep 30, 2016), the FBI investigated 6,814 devices in its forensic lab. Only 31% of those (or 2,095 devices) were protected with a password or passcode. This means that 69% of all mobile devices they’ve got were relatively easy targets: no password means nearly a 100% success rate for working devices, and significant chances to extract information even if the device is damaged but its storage chip is still intact.
69%: No Password, Easy Targets
What about those devices that were locked? The FBI were able to break in to 1,210 of 2,095 devices, which is a success rate of about 58%. The other 885 or 886 devices could not be unlocked or extracted.
Only 58% of Password-Protected Devices Could Be Extracted
886 – “I would suggest that is hardly an insignificant number.” – Jim Baker
The data does not include devices that local and state officials were able to deal with on their own.
What These Numbers Teach Us
Speaking of 87% success rate would not be entirely correct without also mentioning that just 31% of all devices processed by the FBI forensic lab featured any kind of protection at all. With no passcode protection, a smartphone is an easy target. It might be more difficult to obtain a full unencrypted disk image out of an iPhone 5s and newer due to full-disk encryption, but comprehensive acquisition is still available even for encrypted devices if they are not protected with a passcode.
Full-disk encryption alone is not enough to block the investigation
What about the other 31% of devices, those that came with a passcode or password? The FBI was able to unlock some 58% of those, which is really impressive in terms of how secure today’s smartphones are if their users make a small effort and set the damned password. We’re not speaking of Android devices just yet; for many of those, a password can be either bypassed or recovered with proper techniques. However, recent generations of iOS devices such as iPhone 6s and 7 can be secured to the point of becoming completely inaccessible even for such a large and experienced organization as FBI.
We know of techniques allowing investigators to break into most 32-bit iPhones, even if they are locked with a passcode. A similar technique is available for iPhone 5s and 6. So far no known exploits exist for iPhone 6s and 7.
Conclusion
Worried about the FBI getting into your phone? Check if you have a lock screen password. If you are using an Android smartphone, check if you have encryption enabled. If your Android smartphone runs Android 5.1.1 or older and it uses a fingerprint reader, make sure the fingerprint login is disabled. If you’re using Android and Smart Lock is active on your device, disable Smart Lock. If you’ve done all that, you’ve already dome enough to reduce their chance of getting in to 58% or less, which does not mean the FBI cannot use other acquisition options (such as acquiring information directly from your Google Account).
Using an iPhone? A simple 4-digit passcode is all you need on your iPhone 6s or 7 to prevent FBI unlock. For older devices, a stronger passcode (6-digit or alphanumerical) is required to secure access to your data. Have iTunes sync to your iPhone? The lockdown record on your PC can be used to make your phone produce a local backup even if the phone itself is locked with a passcode. Set a very long and tough backup password (in iTunes) to protect your backups. Finally, if you have iCloud backups enabled, those can be targeted by the FBI as well. Disabling iCloud backups will block this acquisition path, but it will also leave you without emergency backups should anything happen to your iPhone.



