Just a few days ago we updated iOS Forensic Toolkit with iOS 10 support. At that time, no jailbreak was available for iOS 10.2. As a consequence, physical acquisition was impossible.
A working jailbreak materialized much sooner than we could’ve hoped. Luca Todesco released a working Yalu102 jailbreak, allowing enthusiasts to mod their devices and enabling forensic experts perform physical acquisition of select iOS devices.
The new jailbreak has limited hardware and software support. At this time, the jailbreak supports most 64-bit iOS devices except iPhone 7, iPad Air 2 and iPad mini 4. iOS 10.0.0 through 10.2 is supported; there is no support for iOS 10.2.1.
Currently supported:
| Device |
iOS Version |
| iPad Pro |
iOS 10.0.0 -> iOS 10.2 |
| iPhone 6S |
iOS 10.0.0 -> iOS 10.2 |
| iPhone SE |
iOS 10.0.0 -> iOS 10.2 |
| iPhone 5S |
iOS 10.0.0 -> iOS 10.2 |
| iPad Air |
iOS 10.0.0 -> iOS 10.2 |
| iPad Mini 2 |
iOS 10.0.0 -> iOS 10.2 |
| iPhone 6 |
iOS 10.0.0 -> iOS 10.2 |
| iPad Mini 3 |
iOS 10.0.0 -> iOS 10.2 |
| iPod touch (6G) |
iOS 10.0.0 -> iOS 10.2 |
Future versions of this jailbreak may add support for the following devices:
| Device |
iOS Version |
| iPad Air 2 |
iOS 10.0.0 -> iOS 10.2 |
| iPad Mini 4 |
iOS 10.0.0 -> iOS 10.2 |
| iPhone 7 |
iOS 10.0.0 -> iOS 10.1.1 |
Keep following https://github.com/kpwn/yalu102 and https://yalu.qwertyoruiop.com/ for more news.
Physical Acquisition Tutorial
Physical acquisition of 64-bit devices has the following benefits over logical acquisition via option “B” (Backup):
- Extracts comprehensive location history
- Extracts Safari cache and temporary files
- Extracts downloaded mail
- Extracts data from apps that explicitly disallow backups
- Offers insight into Apple Home, Apple Pay and other services that made their appearance in iOS 10
- Important information about keychain decryption: physical acquisition will NOT decrypt the keychain. In order to extract the keychain, use the “B” (BACKUP) command to make the device produce a local backup. If no password is set, iOS Forensic Toolkit will automatically use “123” as a password. Use this password to decrypt the backup. The keychain will also be decrypted. If the backup is protected with an unknown password, you will need to recover it first using Elcomsoft Phone Breaker.
Please note that, while it is still possible to downgrade from 10.2.1 to 10.2, this is meaningless in the context of physical acquisition as downgrading wipes the device.
Even with jailbreak, physical acquisition is still subject to conditions. Your iOS device and its version of iOS must both be supported by the jailbreak. You must be able to unlock the device in order to install the jailbreak, and you must be able to remove the passcode from device settings in order to perform physical acquisition. To help you get through, we compiled the following tutorial.
Pre-requisites:
- Supported iOS device (see compatibility matrix above)
- Supported version of iOS (currently, iOS 10.0 through 10.2 are supported; there is no iOS 10.2.1 support at this time)
- Elcomsoft iOS Forensic Toolkit 2.20 or newer
- The latest version of Yalu jailbreak: download from https://yalu.qwertyoruiop.com/
- Cydia Impactor: download from http://www.cydiaimpactor.com/
Physical acquisition tutorial:
- Unlock the iOS device and ensure it is running a supported version of iOS. Connect it to your computer.
- Install jailbreak
- Launch Cydia Impactor on your computer
- Drag and drop the Yalu IPA file onto Cydia Impactor
- You will be prompted for Apple ID and password. These will be used for signing the IPA. You may use any valid Apple ID credentials. If the Apple ID you use has two-factor authentication enabled, you will need to supply an app-specific password.
- Once Cydia Impactor successfully uploads the IPA (an icon of the Korean leader appears on the home screen of the iOS device), open General > Profiles & Device Management or General > Device Management and tap Trust on the Apple ID that you used to sign the jailbreak IPA.
- Return to home screen. Tap on the icon of the Korean leader. The jailbreak will throw a few messages. The device will respring. The Cydia icon will be added.
- If you have a problem installing jailbreak, please review the following tutorials:
- Install OpenSSH from Cydia
- Remove passcode protection (you will be asked for the original passcode). On the iOS device, open Settings > Touch ID & Passcode. Tap Turn Passcode Off.
- Connect iOS device to your computer (Mac or PC). Insert iOS Forensic Toolkit protection dongle to available USB port. Launch iOS Forensic Toolkit (version 2.20 or newer is required).
Note: we recommend disabling Wi-Fi and cellular connectivity on the device you are acquiring. In addition, disable Wi-Fi on all other iOS devices connected to the same network as your computer.
From iOS Forensic Toolkit main menu, enter “8” to select the TAR FILES command. This will extract the file system and save it as a tarball on your computer.
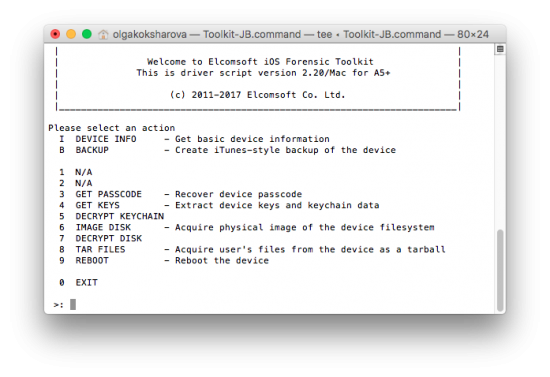
Depending on the amount of data in the target device, the extraction may take a while. Once finished, you will gain access to (almost) everything there is in a local backup, and more.
Get Elcomsoft iOS Forensic Toolkit
[sgmb id=”2″ customimageurl=”” ]



