As we wrote back in May, Apple is toying with the idea of restricting USB access to iOS devices that have not been unlocked for a certain period of time. At the time of publication, our article received a lot of controversial reports. When this mode did not make it into the final build of iOS 11.4, we enjoyed a flow of sarcastic comments from journalists and the makers of passcode cracking toolkits. Well, there we have it: Apple is back on track with iOS 11.4.1 beta including the new, improved and user-configurable USB Restricted Mode.
What’s It All About?
The USB Restricted Mode first made its appearance in iOS 11.3 beta. The idea behind this mode is well covered in our previous article iOS 11.4 to Disable USB Port After 7 Days: What It Means for Mobile Forensics. At the time of 11.3 beta, the feature had the following description:
“To improve security, for a locked iOS device to communicate with USB accessories you must connect an accessory via lightning connector to the device while unlocked – or enter your device passcode while connected – at least once a week.”
The idea behind USB Restricted Mode was pretty ingenious. The feature appeared to be directly targeting passcode cracking solutions such as those made by Cellerbrite and GrayShift. The device running iOS 11.3 beta would disable the USB data connection over the Lightning port one week after the device has been last unlocked. The feature was not user-configurable, but it could be disabled via corporate policies and device management solutions.
Apparently, the feature did not make it into the final release iOS 11.3. While we had reasons to believe it would be included with iOS 11.4, Apple skipped it in iOS 11.4, replacing it instead with a toned-down version that would require unlocking the iOS device after 24 hours in order for it to communicate with a USB accessory. While this toned-down feature would complicate the work of forensic experts by effectively disabling logical acquisition with lockdown records, it had zero effect on passcode cracking solutions such as those offered by Cellebrite and GrayShift.
The “proper” USB Restricted Mode, the one that would completely shut down all data communications between the iOS device and the computer, was still missing in iOS 11.4. Only to reappear – in a much refined form – in iOS 11.4.1 beta.
USB Restricted Mode to Optionally Disable USB Port after Just One Hour
Our May publication made a lot of noise. Some users were excited to receive this additional protection levels, many asking for the feature to be even more restrictive, and most prompting for the feature to become user selectable.
Here’s one example:
Apple Insider: Apple’s iOS 11.4 update with ‘USB Restricted Mode’ may defeat tools like GrayKey
“Can they go a step further and have a toggle that prevents any data connection via USB?” asks one of the readers in the comments. “I’m not a power user, but I can’t remember the last time I connected my phone to anything to transfer data. Everything is cloud based (backup, sync, etc), AirDrop, or just email/imessaged as far as I know.”
It seems that someone in Apple does read such publications, and does care about user’s voices (kudos to them if this is true). Without much fuss (“Bug fixes and improvements” is all that’s mentioned in iOS 11.4 Release Notes), Apple introduces a major new security feature.
Say hello to the new and improved USB Restricted Mode.
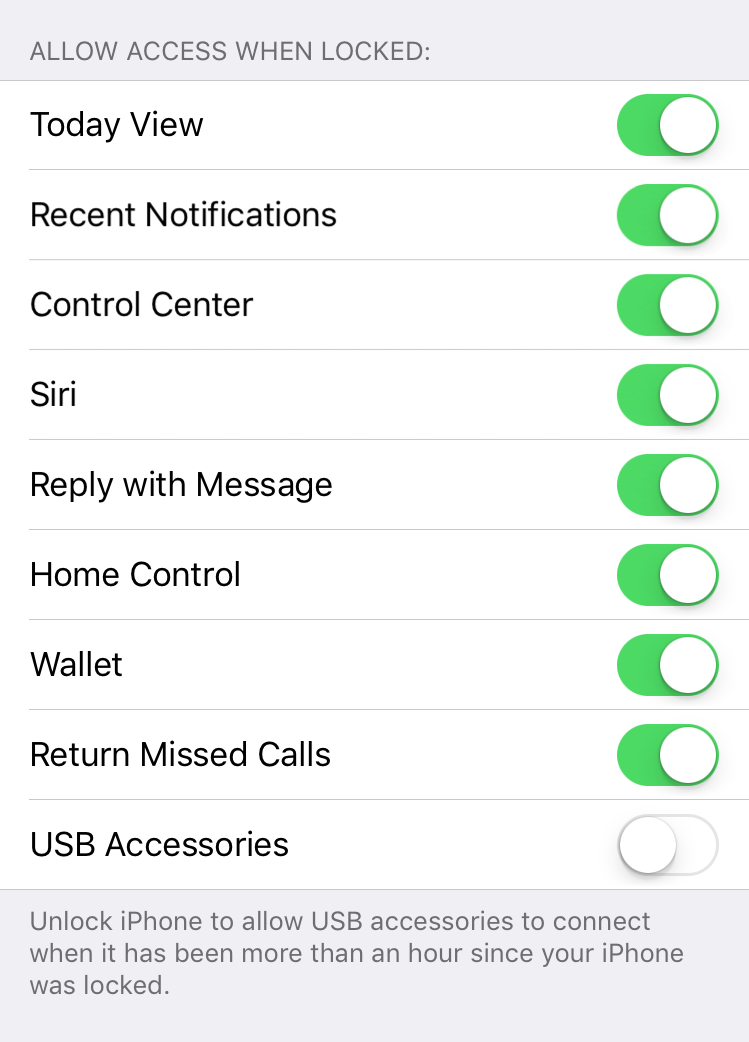
Once the user toggles the “USB Accessories” switch, the iPhone will require you to “Unlock iPhone to allow USB accessories to connect when it has been more than an hour since your iPhone was locked”.
This is what happens if you activate the feature, wait for an hour and try connecting your iPhone to the computer:
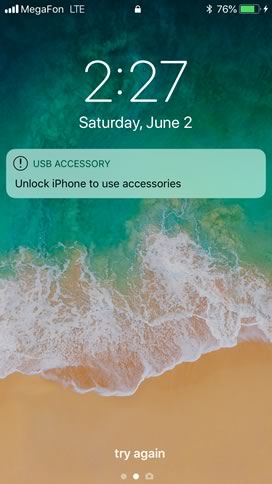
How do we know this is the “proper” USB Restricted Mode this time? Because, unlike before, there is zero data communicated over the USB port once this feature kicks in. iTunes does not see the device at all; no “unlock this device to access” and no pairing request. The iPhone just charges off the computer’s USB port, transmitting no information. We have not been able to access even the basic information about the device using the Elcomsoft iOS Forensic Toolkit I(nfo) command, the very same command that returns identification information about an iOS device even if it has never been paired with the computer.
The End of Forensic Use of Lockdown Records?
The police were frequently using lockdown records extracted from suspects’ computers to access the content of locked devices and produce iTunes-styles backups; all that without knowing the passcode or unlocking the phone with Touch ID/Face ID. The toned-down version of USB Restricted Mode that was included in previous versions of iOS already put a limit of only 24 hours, after which the iPhone would have to be unlocked (24-48 hours: with Touch ID/Face ID or passcode; after 48 hours: passcode only) in order to make use of the existing lockdown record.
The new USB Restricted Mode puts significantly more severe limitations in place. Not only will the experts have an extremely small window of opportunity of just one hours, but they may lose the ability to do just about anything with the device once it shuts down the USB port – including the ability to run a password cracking tool.
The End of Forensic Unlocks?
Will this really be it? Will the new USB Restricted Mode really prevent tools such as Cellebrite and GrayShift from breaking passcodes on devices running iOS 11.4.1 (beta)? At this time, we have no idea. But it certainly looks like this was what Apple planned all along.
A Workaround?
As was the case in iOS 11.3 beta, the clock starts ticking after the device is locked or after the device is disconnected from a trusted (paired) computer or USB accessory (we were able to positively verify the latter by running a simple test). In order to keep the USB port unlocked, the police would have to connect the iPhone to a trusted device during the first one hour, and keep it connected at all times before they have a chance to attempt acquisition.
Conclusion
The exact effect of USB Restricted More on the forensic community remains to be seen. While we currently don’t know how (or if) the new mode will affect unlocking efforts performed by Cellebrite and GrayShift, one thing is for sure: lockdown records will lose much of their forensic appeal due to severely restricted lifespan. It is still to early to say if this option will make it into the final release of iOS 11.4.1, and how exactly it will work if it gets included.




