With over half a million users, Signal is an incredibly secure cross-platform instant messaging app. With emphasis on security, there is no wonder that Signal is frequently picked as a communication tool by those who have something to hide. Elcomsoft Phone Viewer can now decrypt Signal databases extracted from the iPhone via physical (well, file system) acquisition, and that was a tough nut to crack.
What exactly makes Signal so difficult to crack? Let us first look at how one can gain access to users’ communications occurring in other instant messengers.
Interception: the MITM attack
The first method is interception. One can attempt to intercept conversations in transit. This in turn is very difficult as everyone is touting point-to-point encryption. While technically the traffic can be intercepted, decrypting it will require a malicious app installed on the end-user device (such as the infamous NSO Group spyware). Without direct government intervention or proposed encryption backdoors one can hardly ever intercept messaging with a MITM attack. It is very important to understand that even if your iPhone is secure, the other party’s device running the iOS, Android or desktop app (which is much easier to break) might be compromised. If the other party is compromised, all your communications with that party will be compromised as well.
Signal implements special protection measures against MITM attacks, making certificate spoofing useless and complicating malware-based attacks.
Cloud Extraction
Fortunately for the law enforcement, most instant messengers sync and store communications using their own cloud service. Apple syncs iMessages through iCloud, Microsoft keeps Skype conversations in the user’s Microsoft Account, Telegram has its own cloud service to sync all but private chats, and so on. While all of those companies tell users their data is stored securely encrypted, all but Apple readily provide data to the law enforcement when served with a legal request. (Apple does not as the company allegedly does not have access to the encryption keys; this didn’t stop us from accessing cloud messages anyway.)
Let us make it clear. With cloud storage readily available, one can access the user’s conversation histories by either serving a legal request or by logging in with the user’s account credentials. We’ve been able to do the latter for iMessages; while difficult it’s not impossible.
Signal does not store messages, conversation histories or encryption keys in the cloud, period. There is nothing to request (except some metadata, may be) and there is nothing to access even if one signs in with the user’s credentials.
Backups
Some messengers do keep their conversation histories in backups and some don’t. For example, iMessages can be extracted from password-protected backups if (and only if) the Messages in iCloud option is not enabled in the device settings. We haven’t seen Telegram conversations backed up, but WhatsApp allows its database in the iCloud backup and also in its own stand-alone backup in iCloud Drive for iOS or Google Drive for Android. While stand-alone backups are encrypted, one can decrypt them using Elcomsoft eXplorer for WhatsApp.
It can be hit or miss with other messengers. Signal does not allow its conversation histories or encryption keys in local backups, even those that are protected with a password.
Extracting from the Device
Extracting a working database always works. WhatsApp, Skype, Telegram and iMessage databases are stored in plain SQLite format; they are never encrypted (other than using the system’s full-disk encryption feature).
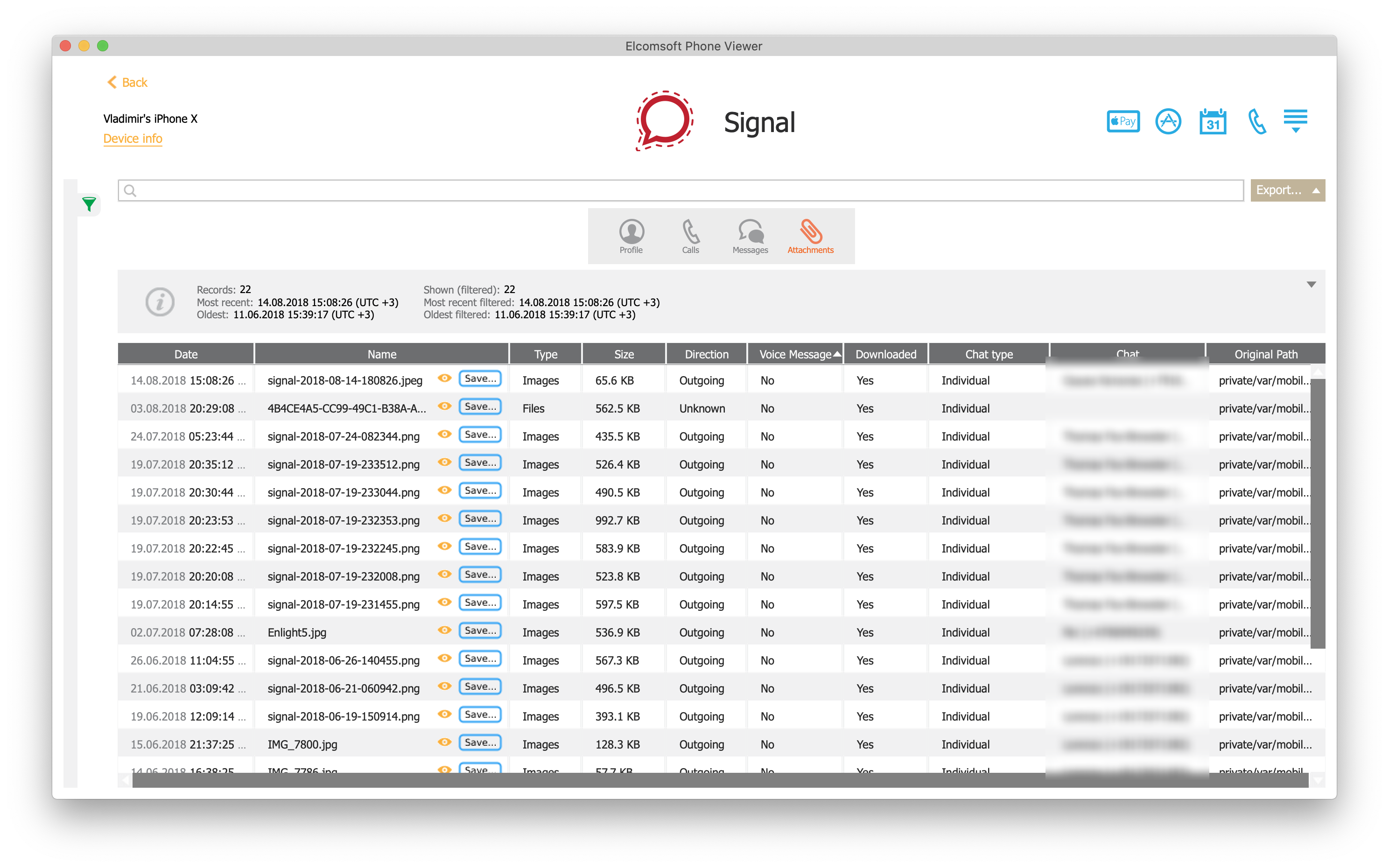
Unlike all of those other messengers, Signal encrypts its working databases. The encryption key is generated the first time the user signs in to Signal on the device. The key is then stored in the keychain, protected with a high protection class. Without that key one can only extract attachments (pictures, documents, voice messages etc.)
Why Signal Is Secure
Just like Telegram, Skype and WhatsApp, Signal protects communications with secure point-to-point encryption. What makes it different to many every other instant messaging app on the market is the fact that Signal never syncs conversations with the cloud. In addition, the app for Android and iOS platforms takes care to never back up conversation histories into the corresponding cloud service (Google Drive and iCloud respectively). As a result, there’s nothing to get in the cloud, and there is virtually no relevant information about the user’s communications that law enforcement could request from Apple, Google or Signal itself. The icing on the cake is the fact that Signal does not allow its working database to be backed up locally (via iTunes or third-party tools); not even into encrypted backups.
According the the developers, “Signal messages and calls are always end-to-end encrypted and painstakingly engineered to keep your communication safe. We can’t read your messages or see your calls, and no one else can either.” As we have seen, this statement true. However, the app must still have access to conversations, which means they must be stored somewhere on the device.
The point is, of the three vectors of attack (logical, physical and cloud) neither cloud nor logical acquisition are available. The only way to obtain Signal data that includes the user’s communications is physical acquisition and physical acquisition only.
The Issue of Encryption
Okay, great, physical (sort of) acquisition it is. After extracting the Signal database from the iPhone’s file system image, accessing the data will be extremely difficult due to the custom encryption scheme implemented by Signal. There is no password protecting the database; the encryption key is generated from random seed during initialization, then stored in the iOS keychain with a high protection class. The high protection class means that the key is not exported into iCloud (in fact, it is exported, but encrypted with the device-unique hardware key) and cannot be decrypted when analyzing a password-protected backup.
Breaking Signal Encryption
In order to decrypt Signal conversation databases extracted from the iPhone via file system acquisition, you will also need to extract the encryption key from the keychain. If you are using Elcomsoft iOS Forensic Toolkit, make sure to capture the keychain along with the file system image.
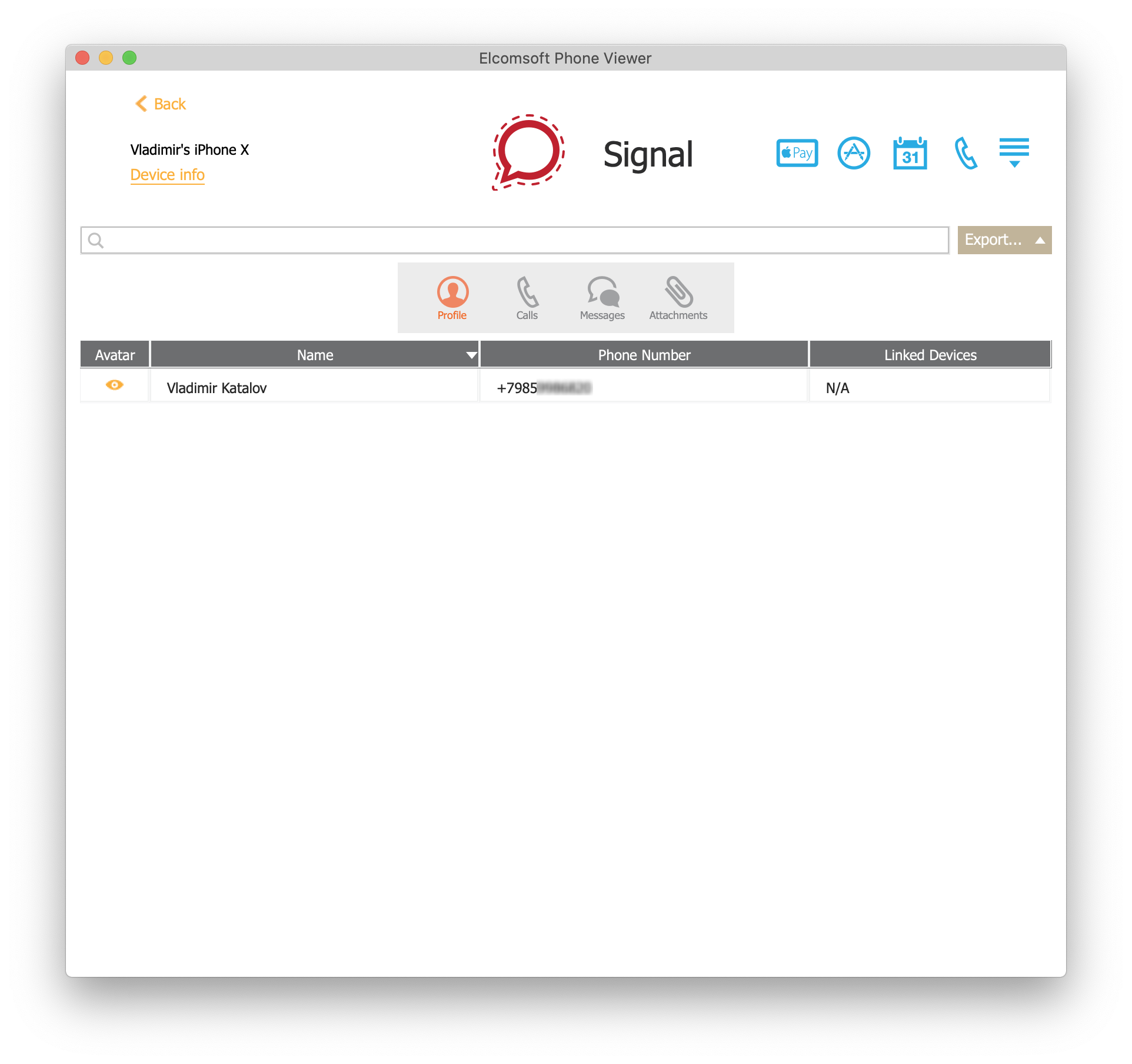
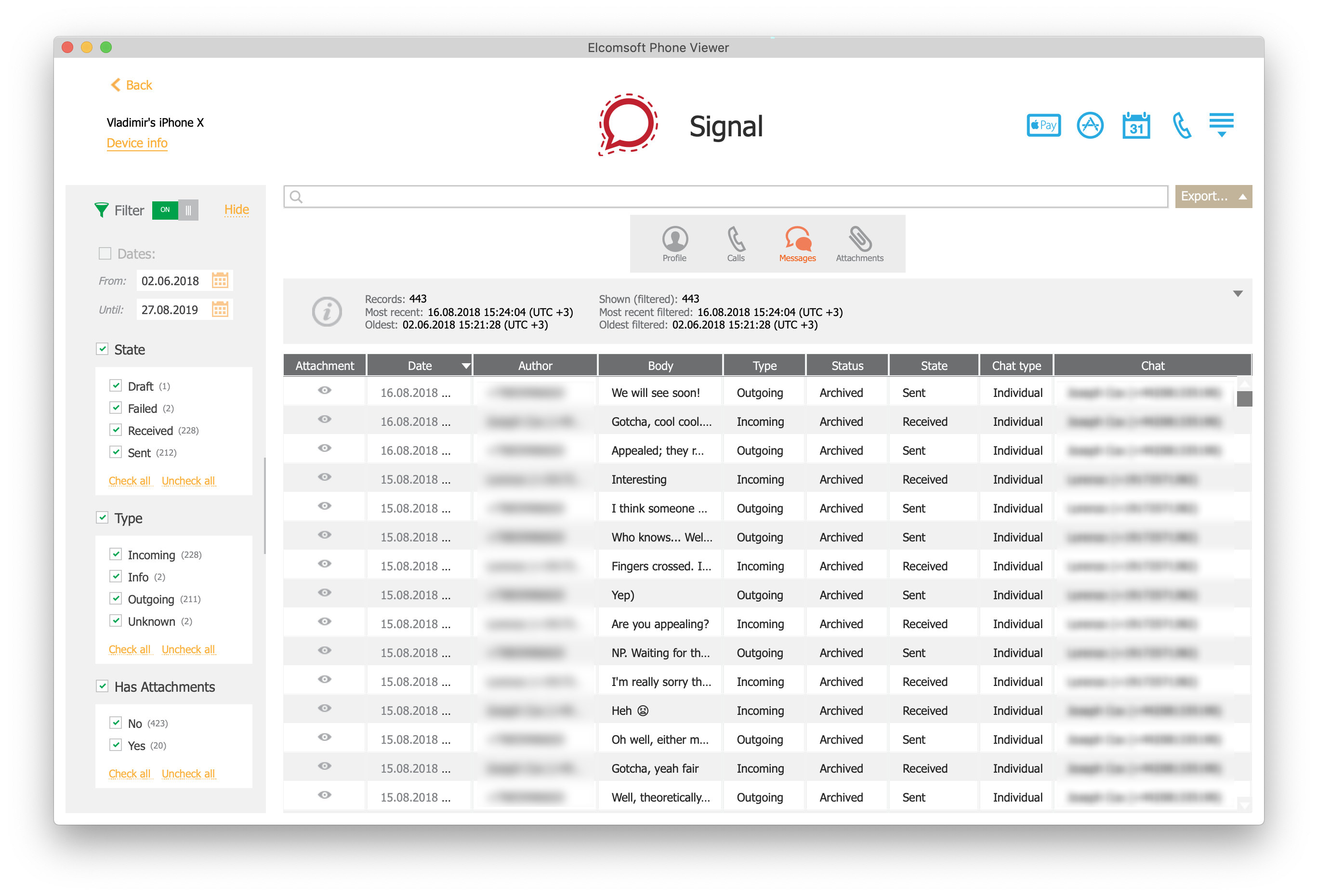
To decrypt and analyze a Signal conversation history, open the file system image in Elcomsoft Phone Viewer and use the extracted keychain file to decrypt the Signal database. Elcomsoft Phone Viewer will then decrypt the database and display its content in a blink of an eye.
Follow these steps to decrypt the Signal database:
- Have the following readily available: file system image (.tar or .zip) and decrypted keychain extracted with Elcomsoft iOS Forensic Toolkit (keychaindump.xml by default).
- Launch Elcomsoft Phone Viewer and open the file system image.
- Once the file system image fully loads, have a look at the Signal icon. Note the red “encrypted” key on that icon.
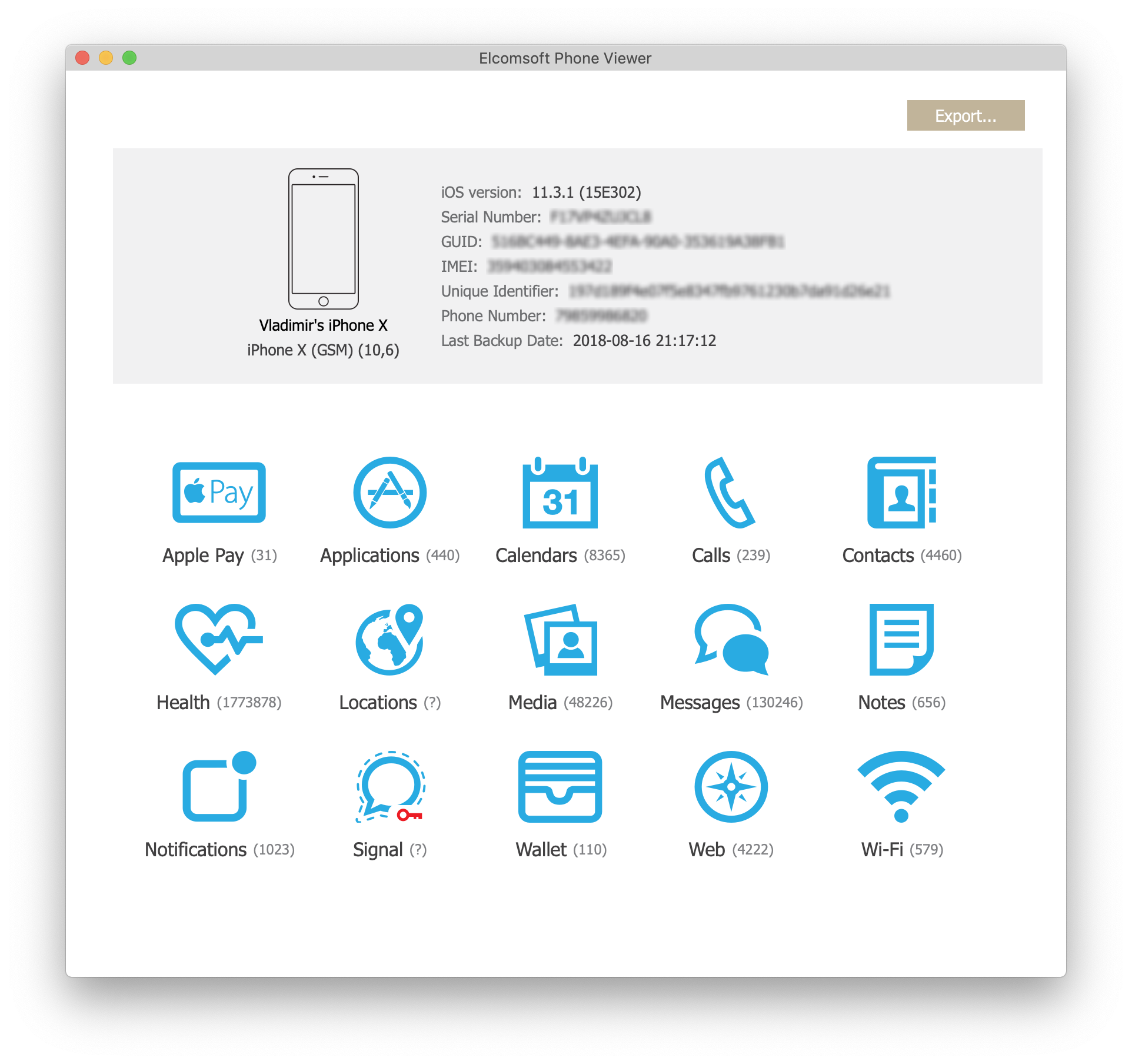
- Click on the Signal icon. You’ll be prompted to provide path to the keychain file. Select the keychain file to decrypt the database. The icon will change to “decrypted” (no red key anymore).
- Once the database is decrypted, you can browse and view its content.