Modern wireless networks are securely protected with WPA/WPA2. The most frequently used method of securing access to a wireless network is pre-shared passphrase, or, simply put, a text password. The WPA standard enforces the minimum length of 8 characters for all Wi-Fi passwords. Considering the relatively low performance of WPA/WPA2 password attacks, brute force attacks are rarely effective even when performed with a network of GPU-accelerated computers. In this article, I will show how to attack wireless passwords for the purpose of security audit.
Pre-Requisites
First and foremost, you’ll need a WPA/WPA2 handshake dump. This dump is essentially a file you’ll be using in the password recovery app when attacking Wi-Fi passwords. In order to capture the WPA/WPA2 handshake, use the built-in Wi-Fi sniffer in Elcomsoft Wireless Security Auditor.
The traditional approach to capturing a WPA/WPA2 handshake was using a dedicated AirPCap wireless adapter and specialized software. Elcomsoft Wireless Security Auditor takes AirPCap out of the equation, delivering a software-based Wi-Fi sniffing solution that works on regular Wi-Fi adapters. The custom NDIS driver for 32-bit and 64-bit Windows systems is digitally signed by Microsoft, and can be installed on all compatible versions of Windows including the latest builds of Windows 10. With this tool, you can automatically intercept Wi-Fi traffic and launch an attack on selected Wi-Fi networks.
Note: you must install a WinPCap driver to enable Wi-Fi sniffing. A compatible WinPCap driver is provided with Elcomsoft Wireless Security Auditor.
Please refer to Elcomsoft Wireless Security Auditor manual for information on installing WinPCap and NDIS drivers and capturing a WPA/WPA2 handshake.
You can attack passwords within Elcomsoft Wireless Security Auditor for GPU-accelerated recovery, or Elcomsoft Distributed Password Recovery, which can use multiple computers and multiple GPU units to accelerate attacks.
The Attacks
The WPA/WPA2 always consists of at least 8 characters. Even if the password is exactly 8 characters long, can you break it using a brute-force attack? Let’s calculate!
An 8-character password that contains characters from the extended character set (small and capital letters, number and special characters) has 6,634,204,312,890,625 possible combinations. A single NVIDIA Tesla V100 can try as many as about 650,000 WPA/WPA2 passwords per second.
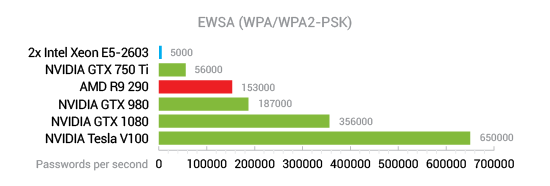
As a result, you’ll need an estimated 323 years to break that password using a single Tesla V100 board. Granted, you can cut this number by utilizing a thousand computers, each with eight V100 boards, and get a much more reasonable estimate, but why would anyone spend that much effort breaking a Wi-Fi network protected with just an 8-character password?
A smarter attack won’t cost you anything, but may result in significantly higher success rate in significantly less time.
Try Phone Numbers First
If you are not auditing a Pentagon network, a good starting point will be the list of local phone numbers. While passwords like these are relatively uncommon, we’ve still seen them in 1 to 3% of the cases. Considering the very short duration of this attack, the list of local phone numbers is totally worth checking.
All-Digit Passwords
A good number of Wi-Fi access points are protected with passwords consisting of exactly 8 digits. While this attack takes longer than trying the list of local phone numbers, it may be worth running depending on your computational resources. A single video card will crunch through these all-digit passwords in under three minutes, making it worth a try.
Targeting the Human Factor
Wi-Fi passwords are meant to be shared and used by a number of people. More often than not, these passwords are made to be easy to memorize and easy to type, especially on mobile devices. As a result, many passwords are based on combinations of one to three dictionary words, some numbers, and very few special characters. In other words, we recommend using automatically adjusted dictionary attacks when auditing Wi-Fi passwords. If a wireless network can withstand a GPU-assisted dictionary attack with mutations during a given timeframe, one can consider the network to be secure.
Leaked passwords
Every year, millions of user accounts are compromised, and millions of passwords are leaked. We strongly recommend obtaining the list of the most commonly used passwords such as the Top 10,000 passwords or Top 10 million passwords, and run a simple, straightforward attack through the dictionary of leaked passwords.
The dictionaries of the most common passwords can be obtained from GitHub.
Dictionaries
Wi-Fi passwords frequently contain one or more words in natural language. You can often recover such passwords by running a dictionary attack. A dictionary attack against a Wi-Fi password requires one or several dictionaries; a dictionary of English words is a good starting point, but dictionaries of local languages should not be forgotten.
Mutations
Users frequently attempt to “secure” a password using a well-known word and applying some modifications. Sometimes, the among of modifications is just enough to pass the enforced security policy. For example: JohnSmith1, J0hnSm1th, Eva-1980, Peter1$ and so on.
To help attacks target passwords selected by average users, we developed an automated mutations engine. The mutations engine automatically alters dictionary words to mimic common patterns. You can easily apply mutations to dictionary words. More time is required when more mutations or higher mutation level are selected.
Elcomsoft Wireless Security Auditor offers a dozen different mutations. Enabling all of these mutations at the same time enormously expands the number of passwords to try, making it difficult or impossible to reach the end of the list in reasonable time. For this reason, we strongly recommend using a reasonable number of mutations and choosing only those mutations that are likely to be used in a given case.
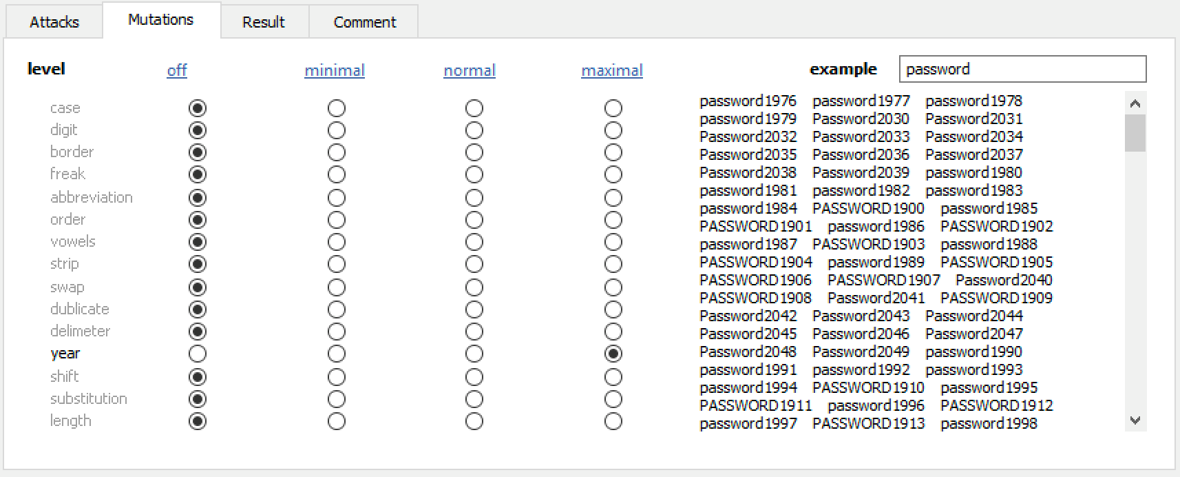
In real life, we’ve witnessed the following three mutations being the most popular:
Case mutation: different variations of uppercase and lowercase characters.
Digit mutation: one or more digits added to the beginning or at the end of the password.
Year mutation: a four-digit year appended to the end of the password.
You can read more about mutations in the Attack Settings and Dictionary Mutations sections of the manual.
Masks
Some organizations have strict password security policies requiring the use of a certain number of small characters, capital letters, numbers and special characters. If you know the rules, the mask attack helps you use such policies to your advantage by only checking for passwords that match the known structure.
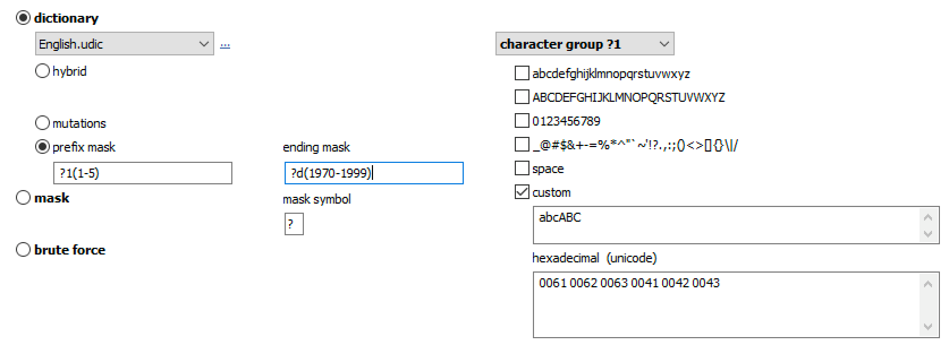
Note: while the Mutations attack expands the number of passwords to try, Masks do the opposite by skipping checks on passwords that don’t match the set mask.
You can read more about the masks in the Attack Settings.
Combination and Hybrid attacks
In real life, encountering passwords made of a single dictionary word is rare. More often than not, passwords consist of two or three words combined with some numbers and special characters. The Combination and Hybrid attacks target this kind of passwords by allowing you to try passwords made of two words, each of them taken from the dictionary. You can use the same or different dictionaries for the first and second words. We recommend enabling the check for upper-case and lower-case combination, word delimiters and extra mutations.
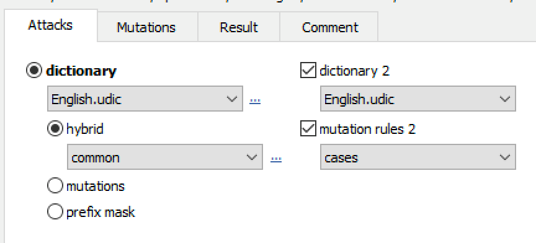
With the first option, the program will try to capitalize the first letter of each word, i.e. testing all four combinations. The second option (Use word delimiters) allows to set the different characters (like dash and underline, though you can set any other ones as well) to be used between words. Finally, you can apply extra mutations to all resulting passwords (Dictionary mutations options will be used). The program tries to estimate the total number of passwords instantly, but mutations will not be counted.
Hybrid attacks are even more complex, allowing to specify scriptable rules desribing the passwords. Combination and Hybrid attacks are documented in the Attack Settings section of the manual.
Suggested Wi-Fi Password Auditing Workflow
Our suggested workflow for auditing Wi-Fi passwords consists of the following steps.
- Prepare the list of local phone numbers and save it as a text-based dictionary file. Run a plain, straightforward, zero-mutation attack through that dictionary.
- Try all-digit passwords. Depending on the available computational resources, you may be able to try passwords containing 8 to 10 digits in a matter of minutes. From the technical standpoint, this is considered a brute-force attack configured as follows: minimal password length = 8; maximum password length = 10; character set: 0123456789
- Run an attack through the Top 10,000 and Top 10 million password lists. Again, no mutations, just straightforward dictionary attacks.
- Run a dictionary attack with mutations (single dictionary).
- Optional: run a dictionary attack with masks.
- Run a hybrid attack with two dictionaries and mutations (note: the two dictionaries may be the same or different to help you try combinations of two words).







