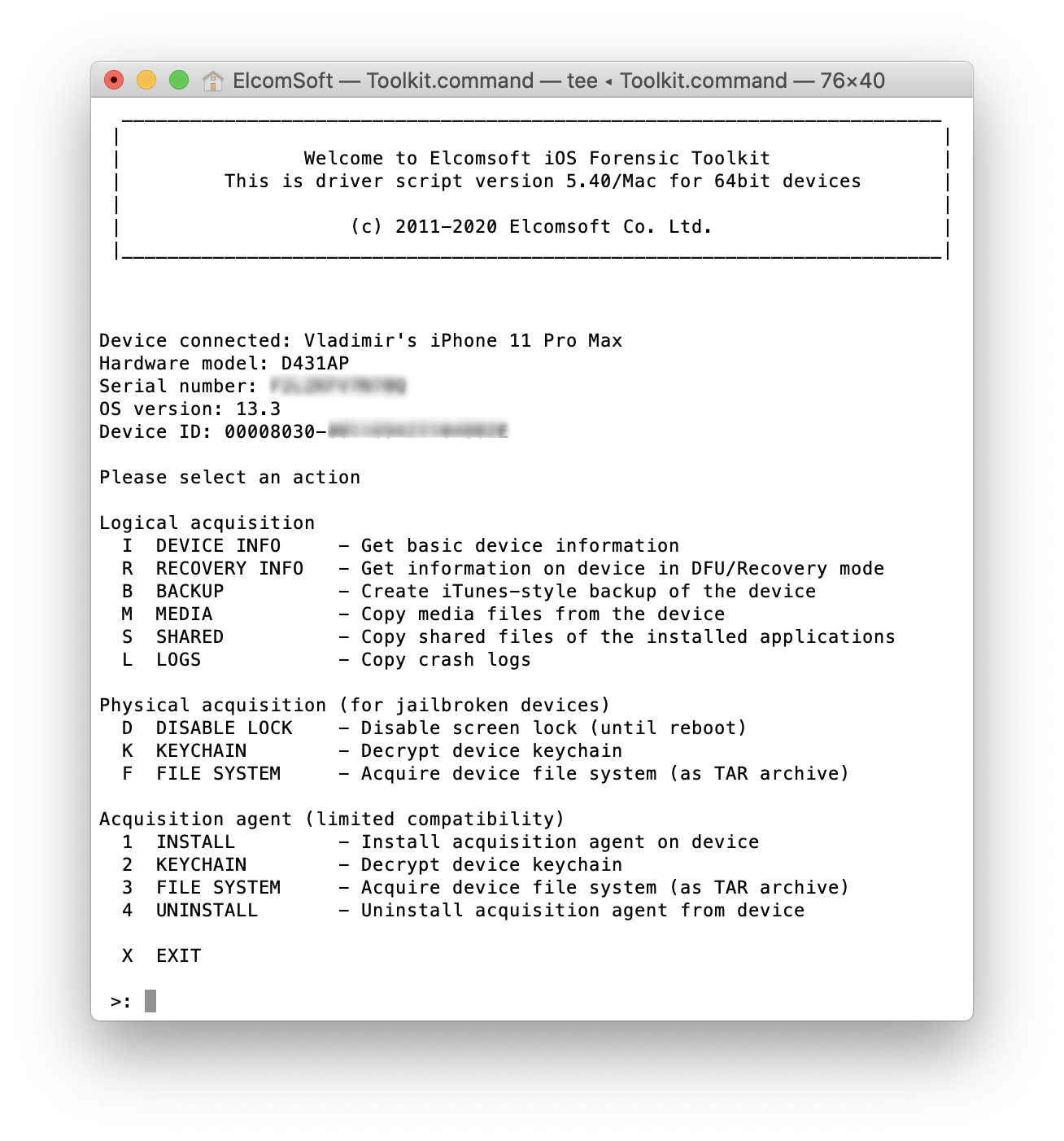
We recently introduced a new acquisition method for iPhone and iPad devices. The fast, simple and safe extraction agent requires no jailbreak, and delivers the full file system image and the keychain. The latest release of Elcomsoft iOS Forensic Toolkit expanded this method to iOS 13 and filled the gaps in some versions of iOS 12 that were missing support (such as iOS 12.3 and 12.4.1). Finally, we now officially support the latest generation of iPhone devices including the iPhone 11, iPhone 11 and iPhone 11 Pro. The new compatibility matrix becomes significantly more diverse with this release, so bear with us to learn which iOS devices can be extracted without a jailbreak.
Compatibility
The extraction agent is supported on the following models and iOS versions:
- iPhone 6s to iPhone X, iPad 5th and 6th gen, iPad Pro 1st and 2nd gen: iOS/iPadOS 11.0 – 13.3
- iPhone Xr, Xs, Xs Max, iPad Mini 5, iPad Air 3rd gen, iPad Pro 3rd gen, iPod Touch 7th gen: iOS/iPadOS 12.0 – 13.3
- iPhone 11, 11 Pro, 11 Pro Max: iOS 13.0 – 13.3
For some older models, compatibility remains unchanged. The following models are supported if running iOS 11-12.2 and iOS 12.4:
- iPhone 5s, 6, 6 Plus
- iPad Mini 2 and 3
- iPad Air (1st gen)
There are two ‘iffy’ models: the iPad Mini 4 and iPad Air 2. While the agent-based extraction method will sure work on these models running iOS 11 through 12.2, we have not tested them with iOS 12.3, 12.4.1 or any version of iOS 13.

Requirements
Make sure that your device model and OS version are compatible, and register an Apple Developer account (here is why). Of course, you will need the latest version of iOS Forensic Toolkit, too. The software is really simple to use, but we still recommend to attend our trainings.
General advantages
The main advantage of this method is its wide compatibility with multiple iPhone and iPad models. In the future, we may add support for older iOS versions (to avoid all the troubles with jailbreaking, see below), and of course will do our best to add compatibility with newer versions (iOS 13.3.1 and up).
Next, the extraction agent is safe and reliable. Nothing wrong may happen; the worst is just a reboot of the device, or our method may simply not work on your device. See the Trobleshooting section below for some tips; sometimes it takes several tries (though usually it works from the first try).
Forensically sound? It depends on what you mean by that. Here is a good definition:
Digital evidence is said to be forensically sound if it was collected, analyzed, handled and stored in a manner that is acceptable by the law, and there is reasonable evidence to prove so. Forensic soundness gives reasonable assurance that digital evidence was not corrupted or destroyed during investigative processes whether on purpose or by accident.
(another good source: When is Digital Evidence Forensically Sound?)
For 64-bit iPhones (starting with the iPhone 5s), there is NO method of data acquisition that does not make ANY changes to the system, despite what other vendors say. Some traces are always left, like records in some system logs.
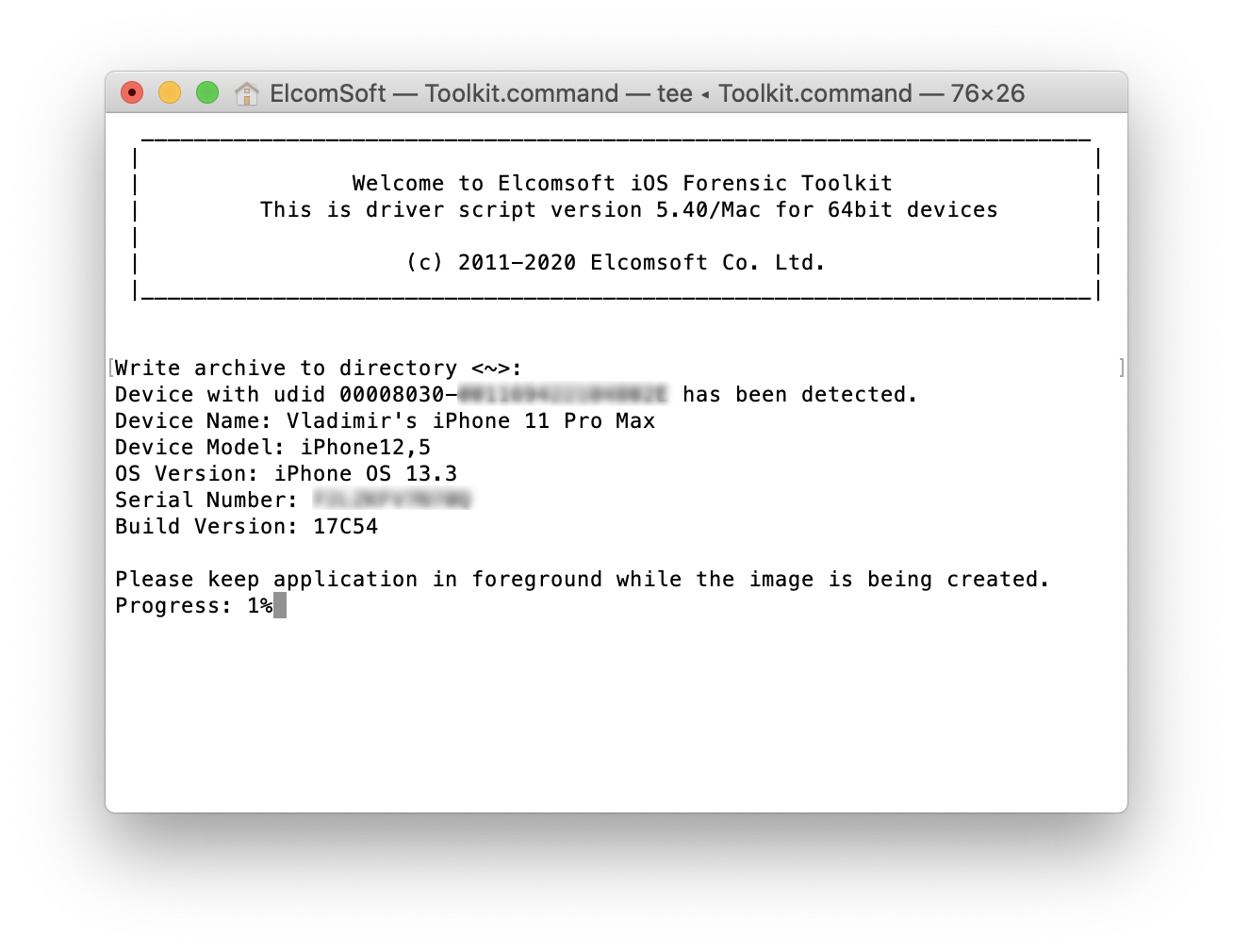
Next, the extraction speed. Instead of re-using ssh, we transfer the data directly over the USB. This method is more reliable and significantly faster; on modern iPhone models, the speed is about 2.5 GB/min.
Finally, the simplicity. No, it is still far from the proverbial “one button” solution, which simply does not exist in the area. Still, we did our best to make acquisition as simple and straightforward as possible, and we are still improving it. Just follow the software manual carefully, and make sure you read the articles published in our blog.
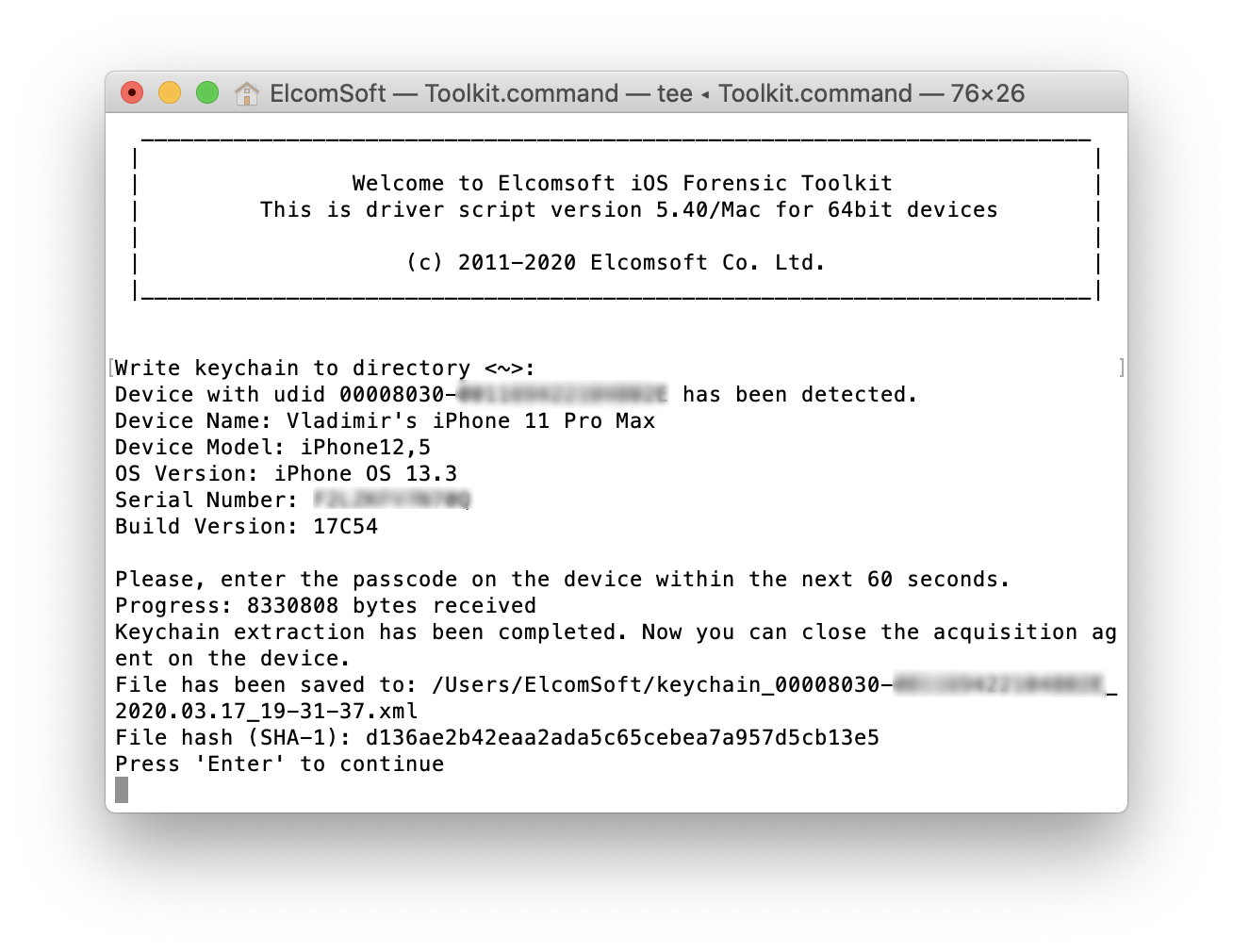
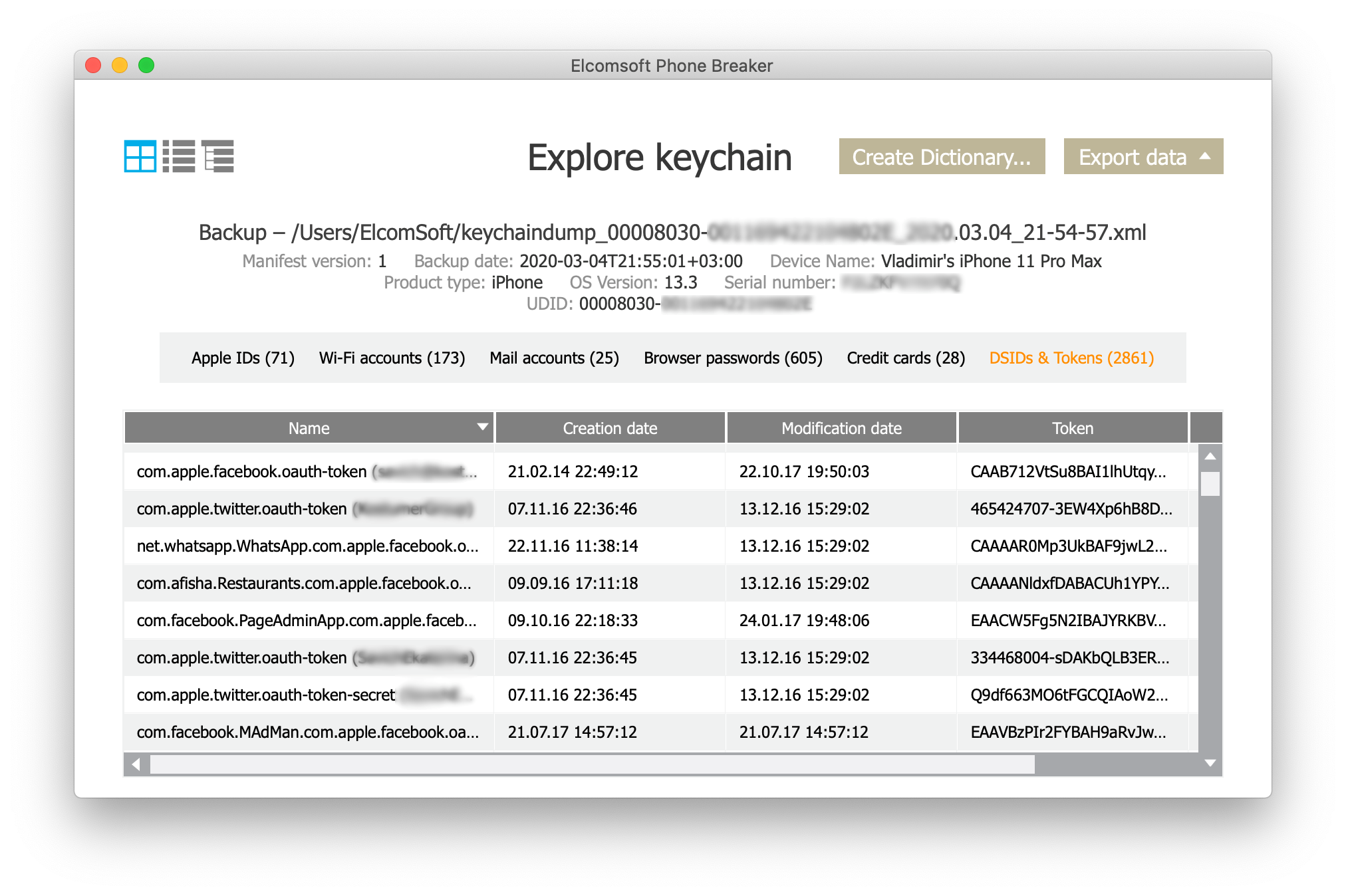
Last but not least. The agent extracts not only the full file system but also the complete keychain. While you can also extract the keychain from iTunes-style-backups, it won’t be complete as a lot of records cannot be decrypted. Use Elcomsoft Phone Breaker to view all the keychain records:
Advantages over jailbreaking
One can also perform full file system acquisition even for latest iPhone models with iOS 13 through jailbreaking. But there are some things you should know.
Jailbreaking is not completely safe. It may brick the device or put it into a boot loop, and it also makes multiple changes to the device file system, even with the rootless jailbreak.
Are there any disadvantages of agent-based extraction? Not a single one, at least for iOS 11.0 to 13.3. Except checkra1n (see below).
One more thing. With iOS 13, some files and folders have improved security attributes and are not accessible by tar over ssh. There is no such problem with agent-based acquisition.
We even made our method compatible with intermediate beta versions of iOS (in the 11-13.3 range) where jailbreaks do not work at all.
Advantages over checkm8 extraction
checkm8-based acquisition is pretty nice, but the devil is in the detail.
First, checkm8 is compatible with a limited number of devices and iOS versions: iPhone 5s to iPhone X, and iOS from 12.3. So forget about the iPhone Xr, Xs, 11 and 11 Pro (as well as many iPads); they are not vulnerable to this exploit. Also, despite the fact that the exploit is hardware-based, the checkra1n jailbreak (and all current checkm8-based acquisition processes) are NOT compatible with iOS 12.2 and below.
Second, the checkra1n jailbreak is not 100% reliable. There are so many compatible devices it does not work on, and the same about direct checkm8 implementation. If there is an error, you’re stuck with it; moreover, you can even ‘brick’ the device with it (it really happened to couple of our test devices). How about the speed? Amazingly low, thanks to ssh and some other things. Some extractions cannot complete in a week, we have no idea why.
The only two real advantages of checkra1n/checkm8 are: they do not require an Apple Developer account, and they allow BFU (Before First Unlock) extractions for devices with an unknown passcode. Also, checkra1n supports iOS 13.3.1 (the latest version at the time of writing this article, though 13.4 is expected very soon). You can use still checkra1n with our iOS Forensic Toolkit to get partial file system and keychain extraction of locked and even desiabled devices.
Usage & troubleshooting
Make sure you have read the iOS Forensic Toolkit manual first, as well as the following two articles:
We described all the steps at iPhone Acquisition Without a Jailbreak (iOS 11 and 12):
- Put the device into airplane mode (this is mandatory!) and connect it to the computer with EIFT. Make sure that Wi-Fi and Bluetooth are disabled from iOS settings (and not from from the Control Centre)
- Establish trust relationship (otherwise you will get the “ERROR: Could not connect to lockdownd, error code -2” message in the EIFT)
- Install the extraction agent though EIFT. You will need to enter Apple ID and app-specific password of the developer’s account, followed by the TeamID; please note that signing the agent requires an internet connection on your computer (but NOT on the iOS device, which should remain offline at all times).
- Once the agent is installed, it is recommended to disable all Internet connections on the computer you perform the acquisition on.
- Tun the Agent on the device and leave it running in the foreground.
- Acquire the keychain and capture the file system; during keychain acquisition, you will have to enter the passcode on the device (sometimes twice), or unlock using Touch ID or Face ID (for devices with Face ID, you will first receive the prompt whether you allow Agent to use it for keychain access)
- Uninstall the agent.
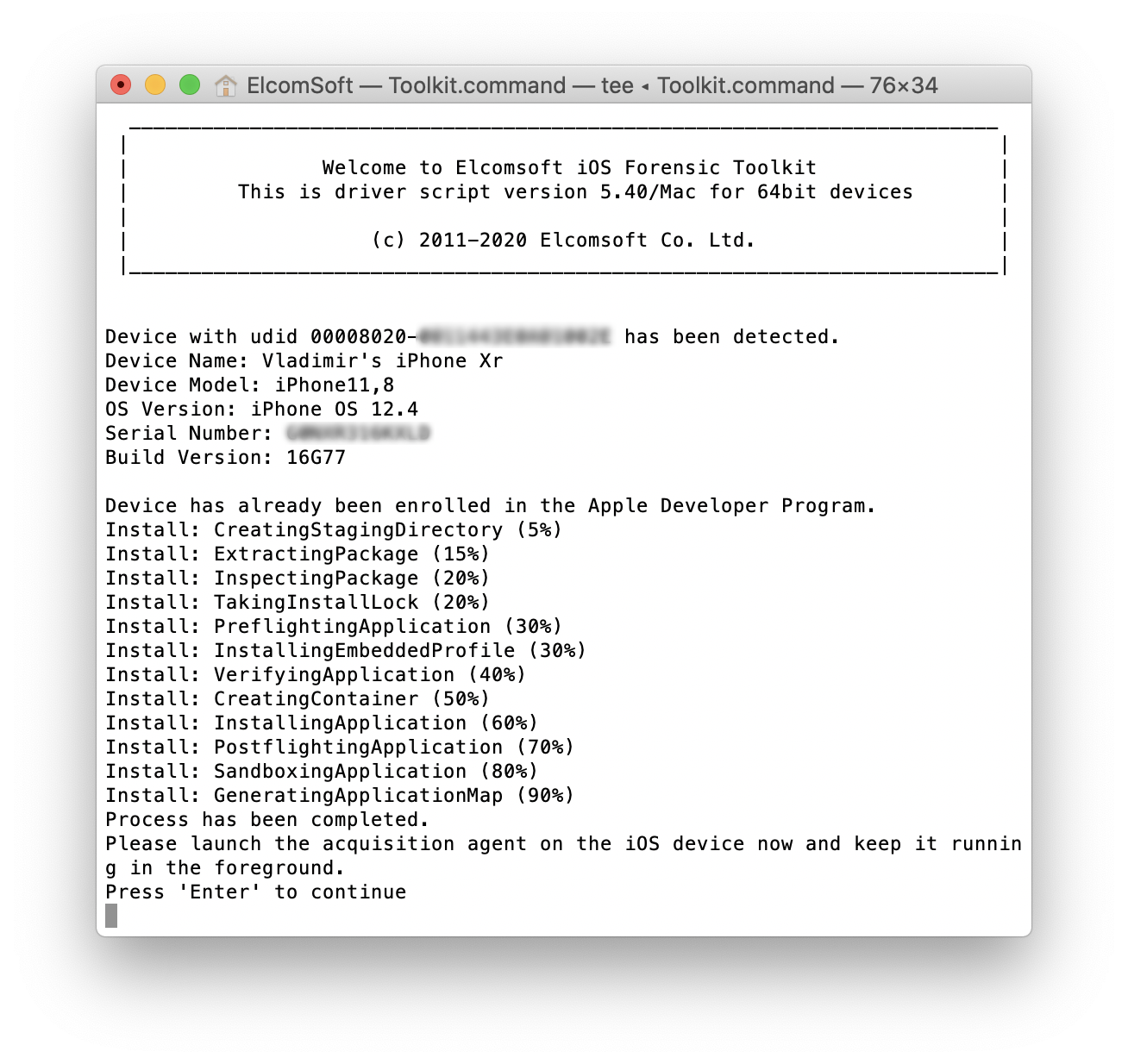
If something goes wrong when you run the extraction agent on the device (e.g. “Can’t connect to device on specified port” message in EIFT), you may need to reboot the device; make sure to wait for at least one minute after rebooting before starting an agent.
Quick tip: if you do not want to enter Apple ID, password and Team ID when installing the Agent on every new device, you can set them up right in the EIFT script (Windows: Toolkit.cmd, lines 20-22; macOS: macosx/Toolkit.sh, lines 42-44):
AGENT_ID=john.doe@gmail.com
AGENT_PASSWORD=abcd-efgh-ijkl-mnop
AGENT_TEAMID=XXXXXXXXXX
Where AGENT_ID is the Apple ID enrolled into Apple Developer Program; AGENT_PASSWORD is app-specific password you should generate on your account, and AGENT_TEAMID is the Team ID (you can easily find it by logging in to Apple’s Developer Center, under Membership Information in Account | Membership).









