With nearly half a billion users, Telegram is an incredibly popular cross-platform instant messaging app. While Telegram is not considered the most secure instant messaging app (this title belongs to Signal), its conversation histories do not appear in either iTunes or iCloud backups. Moreover, Telegram secure chats are not stored on Telegram servers. As a result, Telegram secret chats can be only extracted from the device of origin. Learn how to extract and analyse Telegram secret chats from the iPhone file system image.
Extraction options that do not work: Telegram cloud
Most instant messengers, including Telegram, synchronize and store communication histories in their own cloud services. Telegram maintains its own proprietary cloud service to deliver messages, synchronize user information and store conversation histories. This information is available to the law enforcement with one exception: Telegram secret chats. Telegram developers emphasize end-to-end encryption for secret chats, which makes secret chats device specific. They are not part of the Telegram cloud, they cannot be extracted with cloud acquisition and they cannot be obtained from Telegram the company with a government request.
Telegram does not store secret chats in the cloud. There is nothing to request and there is nothing to access even if one signs in with the user’s credentials. However, regular chats can be extracted from the Telegram cloud or obtained with a legal request.
iTunes and iCloud Backups
Some messengers do keep their conversation histories in backups and some don’t. For example, iMessages can be extracted from password-protected backups if (and only if) the Messages in iCloud option is not enabled in the device settings. With Telegram app for iOS, neither the regular conversation history nor secret chats are backed up. The conversation history is not saved to iTunes or iCloud backups; as a result, Telegram chats cannot be obtained from the device by using logical acquisition.
Telegram does not allow its conversation histories (including regular and secret chats) in local backups, even those that are protected with a password.
What does work: file system images
The complete Telegram conversation history including the content of secret chats can be only obtained from the device of origin. The working database must be extracted from a file system image obtained with agent-based or jailbreak-based extraction.
Telegram databases are stored in plain SQLite format; they are never encrypted (other than using the iOS file-based encryption feature).
Extracting and Analyzing Telegram Secret Chats
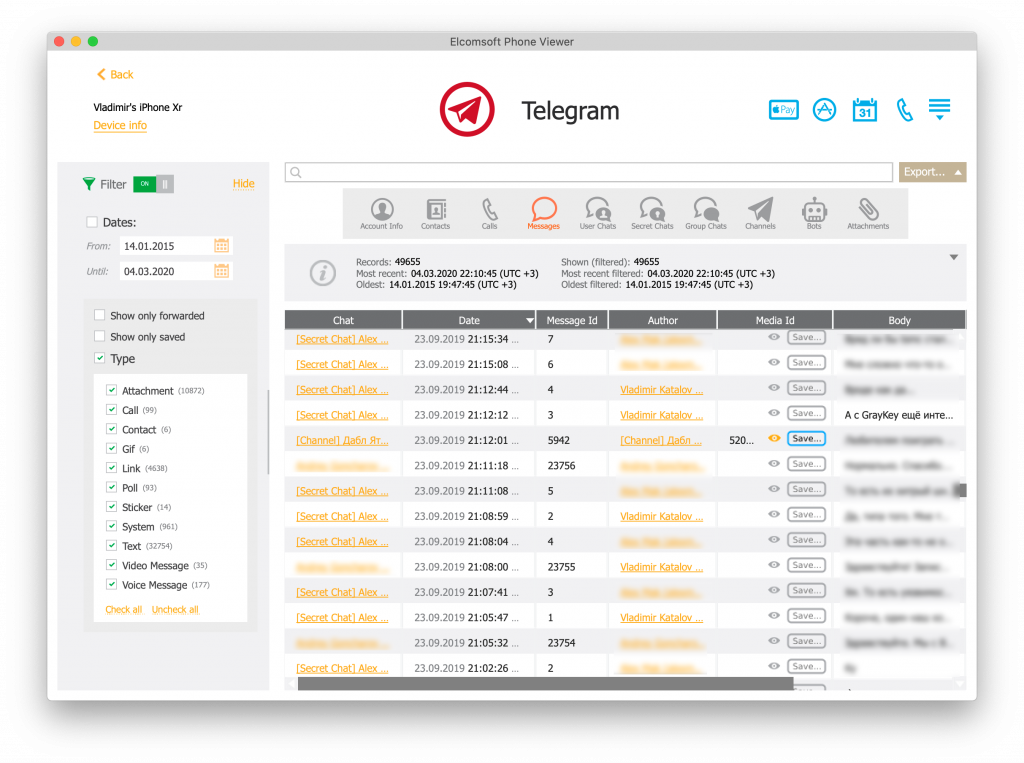
To decrypt and analyze a Telegram conversation history, open the file system image in Elcomsoft Phone Viewer and use the extracted file system image to access the Telegram database.
Follow these steps to view the Telegram database:
- Have the following readily available: file system image (.tar) extracted with Elcomsoft iOS Forensic Toolkit and the latest version of Elcomsoft Phone Viewer (EPV 5.0 or newer).
- Launch Elcomsoft Phone Viewer and open the file system image.
- Once the file system image fully loads, click on the Telegram icon.
- You can now browse and view Telegram chats and other information.
Conclusion
Of the three vectors of attack (logical, physical and cloud extraction) secret chats can be only acquired via physical acquisition. Regular chats, however, can be also extracted from the Telegram cloud service or obtained via a legal request.



