Accessing a locked system is always a challenge. While you might be tempted to pull the plug and image the disk, you could miss a lot of valuable evidence if you do. Full-disk encryption, EFS-encrypted files and folders and everything protected with DPAPI (including the passwords stored in most modern Web browsers) are just a few obstacles to mention. Recovering the original Windows logon is a must to access the full set of data, while resetting the logon password may help unlock working accounts in emergencies.
Dealing with Full Disk Encryption
Full-disk encryption presents an immediate challenge to forensic experts. When acquiring computers with encrypted system volumes, the investigation cannot go forward without breaking the encryption first.
Traditionally, experts would remove the hard drive(s), make disk images and work from there. We are offering there is a faster and easier way to access information required to break full-disk encryption by booting from a flash drive, extracting the system’s hibernation keys and obtaining encryption metadata required to brute-force the original plain-text passwords to encrypted volumes.
We have a comprehensive walkthrough on dealing with encrypted system volumes in A Bootable Flash Drive to Extract Encrypted Volume Keys, Break Full-Disk Encryption
No Encryption: Do I Still Need a Password?
What if the boot volume is NOT encrypted? Do you still need the user’s logon password? It depends. A Windows account (or Microsoft Account) password protects all of the following.
EFS-encrypted files and folders. If you encounter EFS-encrypted files while analyzing the disk images, the only way to decrypt them would be recovering the original password to the user’s Windows account.
Stored passwords, tokens and other sensitive data protected with DPAPI. Windows Data Protection API (DPAPI) was introduced way back in Windows 2000 to provide developers a way to protect sensitive information.
Traditionally, Microsoft had used DPAPI-based Windows Credential Manager to store saved passwords, authentication tokens, network and Web credentials.
Windows Credential Manager was actively used to keep passwords saved by Internet Explorer and Edge Legacy users; more on that in Extracting Passwords from Microsoft Edge Chromium. Other Web browsers such as Google Chrome and modern Edge no longer use Credential Manager to store users’ Web passwords. However, their password databases are protected with AES 256 GCM encryption, while DPAPI is still used to protect the vault encryption key. Other Web browsers that are based on the Chromium engine are using the same encryption scheme. This includes, among others, the latest versions of Opera, and Chromium browser.
DPAPI protection is based on the user’s logon credentials. Should you reset or remove the user’s original password, the entire set of DPAPI-protected data becomes unrecoverable.
Important: in order to decrypt EFS files and data protected with Windows DPAPI, you must recover the user’s original logon password as opposed to analyzing a ‘cold’ disk image or resetting the logon password.
Why Not Reset the Password?
While you may simply reset the Windows logon password, if you do that, you will lose access to EFS files and data protected with Windows DPAPI, such as network stored credentials and encryption keys protecting the user’s passwords stored by Web browsers.
Resetting the password can be used as an emergency measure if you urgently require access to the user’s account and are content with not accessing encrypted data. Alternatively, you may grant administrative privileges to the Guest user, thus gaining access to unencrypted files stored in other users’ accounts.
Launching the Chain Reaction
Once you recover the user’s original Windows account password, you will be able to instantly extract that user’s passwords from multiple Web browsers. Google Chrome, Microsoft Edge, Opera, Chromium and many other Web browsers protect their password databases with a key protected with DPAPI. By using a tool such as Elcomsoft Internet Password Breaker, you’ll be able to instantly extract those account credentials complete with login and password information. Using those passwords, you may be able to sign in to the user’s email and social network accounts.
Can you launch the chain reaction without breaking the Windows password? It may not be that easy, but you may still be able to create a high-quality dictionary by extracting and indexing text files, documents and spreadsheets and launching a dictionary-based attack on the user’s Windows logon password.
Recovering Windows Logon Password
Recovering a Windows logon password may be as simple as booting from a flash drive and rushing through an automated attack, or as complex as extracting hash images and letting Elcomsoft Distributed Password Recovery do its work for the next days or weeks.
The latest build of Elcomsoft System Recovery (version 7.03 and newer) ship with enhanced, smarter and significantly more efficient algorithms for recovering Windows account passwords in-place. When requested to recover the original plain-text password to the user’s Windows account, Elcomsoft System Recovery will attempt to extract passwords that the user stored or cached in their account (the ones without DPAPI protection). ESR will then make a dictionary out of these passwords and run an automated preliminary attack.
While many types of stored passwords can be extracted including various system passwords as well as the passwords stored in the Firefox browser, they’ll only make for a very short dictionary. We try targeting the human factor and password reuse by automatically applying the most common modifications (e.g. adding digits to the end of the password or changing the case of the first character, but not limited to that), thus implementing attacks on similar passwords.
If Elcomsoft System Recovery fails to recover the password, you’ll have to transfer the hash files and open them with Elcomsoft Distributed Password Recovery to run a more complex attack.
Elcomsoft System Recovery allows starting the investigation sooner by booting the computer from a portable flash drive with read-only access to computer’s storage devices. To create a bootable flash drive, just launch the tool on your computer (not the suspect’s computer) and follow the wizard.
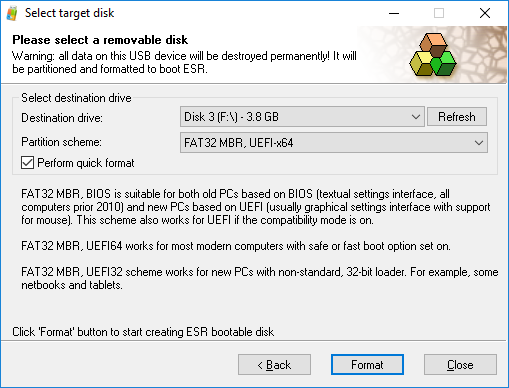
In order to attempt unlocking a Windows account by recovering the original plain-text password with an in-place automated attack, boot from the flash drive and configure the attack. In order to recover the user’s original Windows logon password, select the “Change local user account” option:
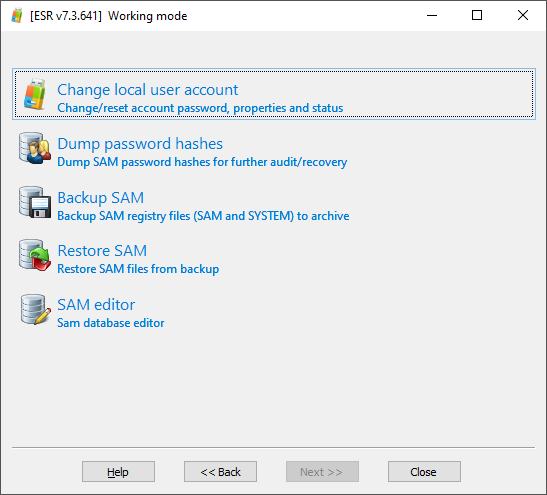
Then set up the attack by selecting the “Scan target system for plaintext passwords” option:
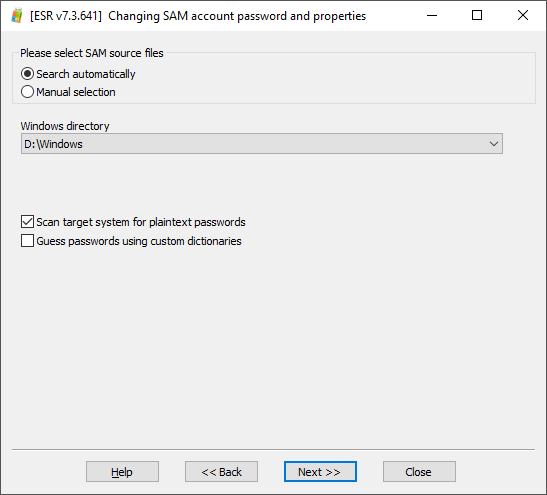
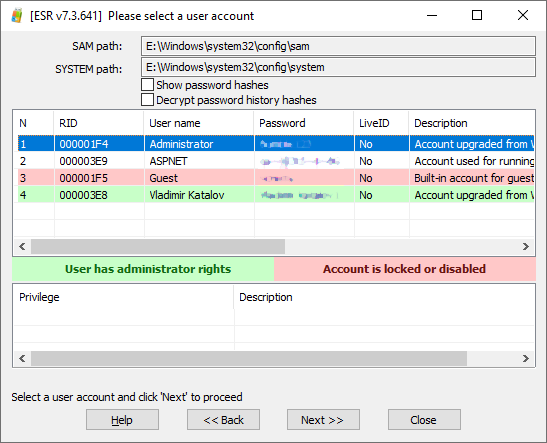
After several minutes, any passwords discovered will be displayed as shown on the screen shot below:
Conclusion
Whether or not you are able to recover the password with a preliminary attack is a matter of luck, especially if there are multiple users or a domain controller in place. If you were unable to recover the particular user’s Windows logon password, as a last resort, you may reset the account password (or remove account lock if it was locked). This option is safe to use as ESR creates a backup allowing to roll back to the user’s original configuration. Recovering the original plain-text password is the forensically sound way, yet shortcuts may be taken should the need arise.









