Full-disk encryption presents an immediate challenge to forensic experts. When acquiring computers with encrypted system volumes, the investigation cannot go forward without breaking the encryption first. Traditionally, experts would remove the hard drive(s), make disk images and work from there. We are offering a faster and easier way to access information required to break full-disk system encryption by booting from a flash drive and obtaining encryption metadata required to brute-force the original plain-text passwords to encrypted volumes. For non-system volumes, experts can quickly pull the system’s hibernation file to extract on-the-fly encryption keys later on with Elcomsoft Forensic Disk Decryptor.
What’s It All About?
It’s about an alternative forensic workflow for accessing evidence stored on computers protected with full-disk encryption. Once the system partition is encrypted, there is nothing one can do about it but break the encryption. Elcomsoft System Recovery helps launch password recovery attacks sooner compared to the traditional acquisition workflow, and offers a chance of mounting the encrypted volumes in a matter of minutes by extracting the system’s hibernation file that may contain on-the-fly encryption keys protecting the encrypted volumes.
This new workflow is especially handy when analyzing ultrabooks, laptops and 2-in-1 Windows tablet devices such as the Microsoft Surface range featuring non-removable, soldered storage or non-standard media. With just a few clicks (literally), experts can extract all information required to launch the attack on encrypted volumes.
Elcomsoft System Recovery offers unprecedented safety and compatibility. The use of a licensed Windows PE environment ensures full hardware compatibility and boot support for systems protected with Secure Startup. The tool mounts the user’s disks and storage media in strict read-only mode to ensure forensically sound extraction.
Using Elcomsoft System Recovery to Make a Bootable Windows PE Flash Drive
In order to extract information required to brute-force the original password, you’ll need a small part of the encrypted volume. You can just boot the system from a Windows PE flash drive and run Elcomsoft System Recovery, a tool for unlocking Windows accounts and accessing encrypted volumes. If making a bootable drive with Windows PE doesn’t sound “fast” or “easy” to you, do not despair: Elcomsoft System Recovery (the downloadable version) will make one for you in just a few clicks.
- Install Elcomsoft System Recovery
- Insert an empty flash drive and launch the tool.

- Select target drive and specify the file system. Note: make sure to select the correct partition scheme. While FAT 32 MBR, BIOS works on older PCs, FAT32 MBR, UEFIx64 is required on most newer computers with Secure Boot. Some devices equipped with 64-bit processors running in 32-bit mode (e.g. Lenovo ThinkPad 8) require FAT32 MBR, UEFIx32 partitioning.
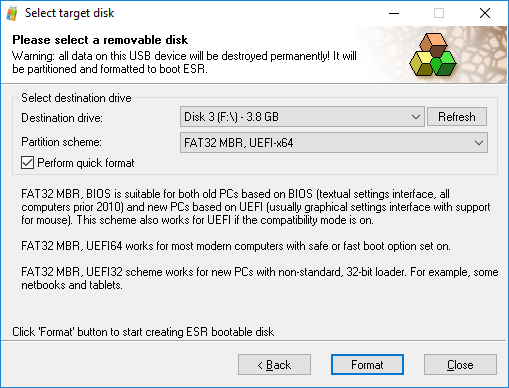
- Click Format. Elcomsoft System Recovery will create a bootable flash drive with Windows PE and ESR utility preinstalled and preconfigured.
There are two distinctly different methods for accessing evidence stored in encrypted disk volumes.
Method 1: Extract Hibernation File to Access Encryption Keys
Crypto-containers are designed to withstand brute-force attacks on their passwords. Moreover, some full-disk encryption methods do not employ a password at all (for example, BitLocker Device Encryption, the most common encryption method for 2-in-1 devices and ultra-thin laptops such as the Microsoft Surface range).
Since brute-forcing the password may be extremely time consuming, we developed tools implementing a workaround.
All encrypted containers have the same feature that is, at the same time, a security vulnerability. We’re talking about on-the-fly encryption keys (OTFE keys). These keys are the actual binary keys that are used by the system to encrypt and decrypt information during normal operations. The keys are stored in the system’s volatile memory at all times while the encrypted volume is mounted to facilitate read/write access to encrypted data. Extracting these keys directly from the device’ memory is possible (Elcomsoft Forensic Disk Decryptor) but is out of scope of this article. Instead, let’s talk about hibernation.
When the user puts their computer to sleep (as opposed to shutting it down), Windows default behavior is so-called hybrid sleep. During hybrid sleep, Windows saves a copy of the device volatile memory on the computer’s hard drive or SSD drive so that the saved state could survive power cut off. At the same time, the computer’s RAM chips are still powered on to retain information. If the power is not cut off through the duration of the sleep, the computer will resume near instantly. If, however, there is a power outage (or depleted battery), Windows will load the saved RAM content from the hard drive. The file that stores the content of the computer’s memory is called hibernation file. Windows stores hibernation files under the name “hiberfil.sys”. Hibernation files are encrypted; however, we were able to break this encryption.
Do you see the point? If the computer was hibernated while the encrypted partition was mounted, the OTFE keys could be stored straight in the system’s hibernation file. If we boot from a flash drive, we can obtain the hibernation file and use it to locate the OTFE keys to all encrypted volumes that were still mounted at the time the computer was put to sleep. You’ll need Elcomsoft Forensic Disk Decryptor to extract the OTFE keys and use them to instantly mount or decrypt the encrypted volumes.
In order to extract the system’s hibernation file, do the following.
- Install Elcomsoft System Recovery 6.0 or newer to your computer (not the suspect’s computer).
- Create a bootable flash drive. Make sure to specify the correct configuration of the target system (BIOS or UEFI, 32-bit or 64-bit). As hibernation files can be quite large, we recommend using a flash stick of at least 32GB.
- Boot the target system from the flash drive you have just created.
- Elcomsoft System Recovery will be launched once the boot sequence is complete. From the following window, select Disk tools.
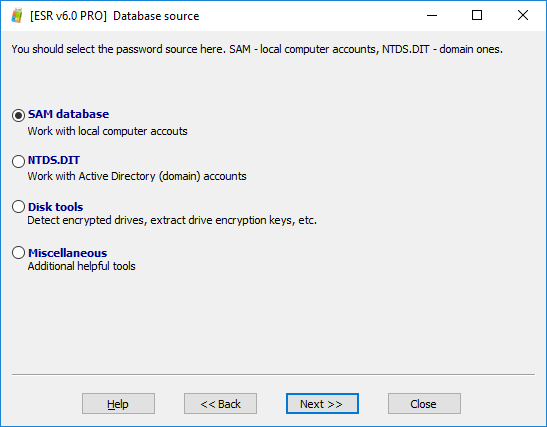
- Select Copy hiberfil.sys. The entire hibernation file will be copied to the flash drive you’ve booted the system from, so make sure you have enough space on that USB drive.
- Specify where the file should be stored. By default, ESR will suggest using the drive it was booted from. If you don’t have enough space on that USB drive, you can specify a different media.
- You can now transfer the hibernation file to your computer. Elcomsoft Forensic Disk Decryptor to extract the OTFE keys and use them to instantly mount or decrypt the encrypted volumes. The process may take several minutes, especially if the size of the hibernation file is large.
If the encryption keys are not found in the hibernation file (which may happen if the encrypted volume was configured to automatically dismount on sleep or hibernation), you will need to attack the encrypted volume’s password. In order to launch the attack, you will need a few kilobytes worth of encryption metadata extracted from the encrypted volume.
Method 2: Extract Encryption Metadata and Brute-Force the Password
The traditional acquisition approach requires disassembling the computer, removing and imaging all of its storage devices. However, all one really needs to start the attack on the password of an encrypted volume is a few kilobytes worth of encryption metadata. The metadata can be extracted significantly faster without removing the hard drives.
Elcomsoft System Recovery allows starting the investigation sooner by booting the computer from a portable flash drive with read-only access to computer’s storage devices. The tool automatically detects full disk encryption on all built-in and removable drives, and allows extracting encryption metadata that is required to brute-force the original password to encrypted disk volumes. Since crypto-containers, by design, are making attacks on the passwords extremely slow, we recommend executing a dictionary-based distributed attack with Elcomsoft Distributed Password Recovery.
TrueCrypt? VeraCrypt?
Since TrueCrypt and VeraCrypt containers use similar formats, there is no way for us to tell them apart. Unfortunately, the two tools differ when it comes to breaking encryption, so you must specify the correct tool before you can launch a password attack.
Moreover; both TrueCrypt and VeraCrypt offer users the choice of a range of encryption algorithms. Each algorithm can be optionally configured with a different the number of iterations (the number of hash operations to produce the OTFE key from the password). If the user specifies a non-standard number of hash iterations, you won’t be able to break the password unless you know that number (or try all possible combinations, which greatly increases the time of attack).
In order to extract encryption metadata, do the following.
- Install Elcomsoft System Recovery 6.0 or newer to your computer (not the suspect’s computer).
- Create a bootable flash drive. Make sure to specify the correct configuration of the target system (BIOS or UEFI, 32-bit or 64-bit). In general, we recommend using a high-speed flash stick of at least 32GB.
- Boot the target system from the flash drive you have just created.
- Elcomsoft System Recovery will be launched once the boot sequence is complete. From the following window, select Disk tools.
- Select Copy Drive encryption keys.

- Elcomsoft System Recovery will automatically detect full-disk encryption on all fixed and removable drives.
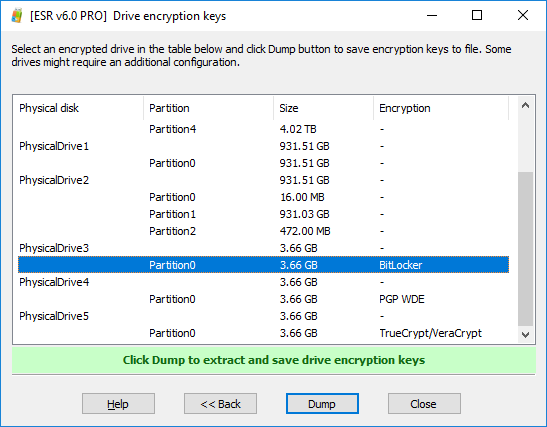
- You can select the volume(s) to process. For example, let’s try this TrueCrypt/VeraCrypt volume:
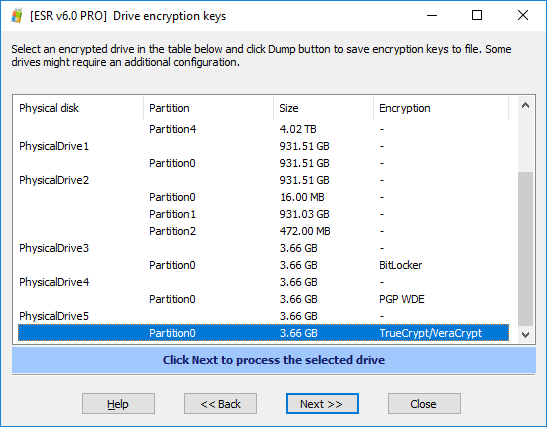
- Since TrueCrypt and VeraCrypt volumes are using the same volume format, we cannot automatically distinguish between the two. You will need to manually specify the type of the crypto container.
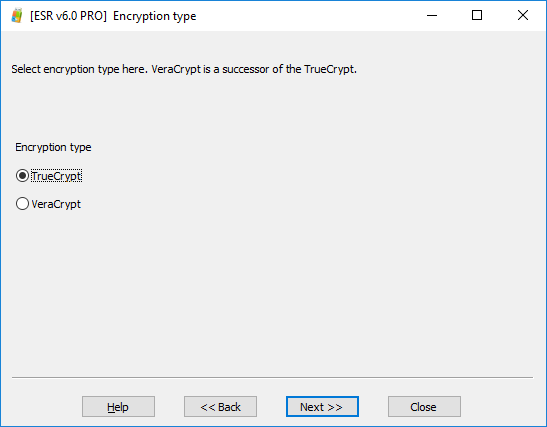
- Both TrueCrypt and VeraCrypt allow using different encryption and hash algorithms. If you know which encryption and hash algorithms were used to encrypt the volume, specify them during the next step.
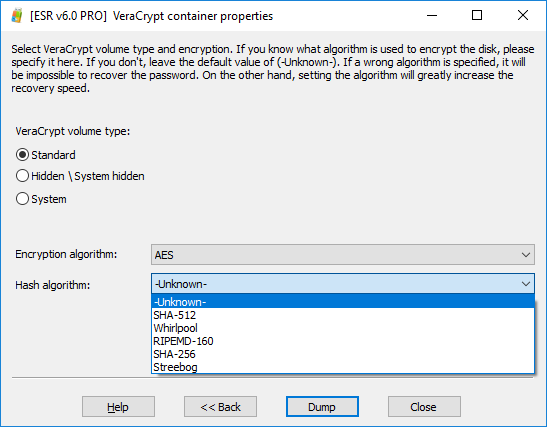
- If, however, you have the slightest doubt about the user’s choice of encryption algorithm and hash algorithm, do leave these values as “Unknown”. This will slow down the attack as we’ll have to try multiple combinations; however, this is still better than specifying the wrong encryption type and failing to discover the password.
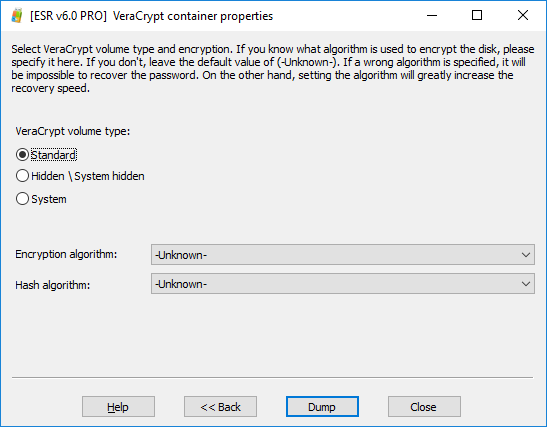
- Once you have finished dumping the encryption metadata, transfer the files to Elcomsoft Distributed Password Recovery to recover the original plain-text password. Note that password attacks may take significant time even with powerful hardware.
If the password is found, you can either mount the encrypted volume or decrypt it for offline analysis by using Elcomsoft Forensic Disk Decryptor.
The Bonus Chapter: Making a Memory Dump
If you are analyzing a live system, and the user is logged in, you have yet another option for capturing the OTFE keys by making a volatile memory dump. In order to capture the RAM image, you would have to run Elcomsoft Forensic Disk Decryptor on the user’s live system (so forget about the “read-only” part). The user must be logged in, and the account must have administrative privileges.
Note: live system analysis is dangerous. While Elcomsoft System Recovery offers the convenience and safety of read-only operation, live system analysis is its direct opposite.
To capture the memory dump, install Elcomsoft Forensic Disk Decryptor onto a flash drive, connect that flash drive to the target system and run the small capturing tool.
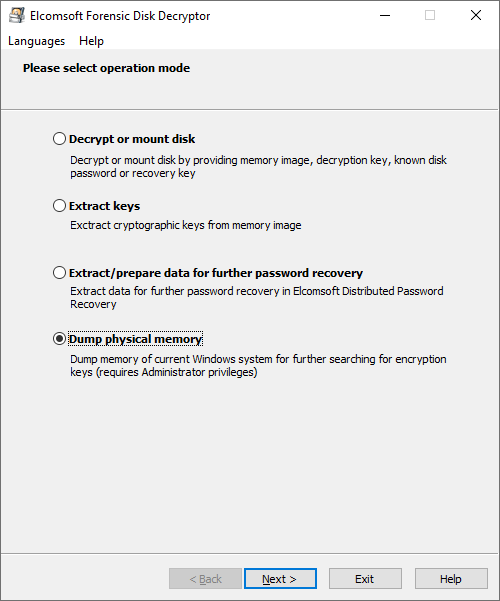
The memory dump will be saved. Make sure to specify the correct path on the flash drive.
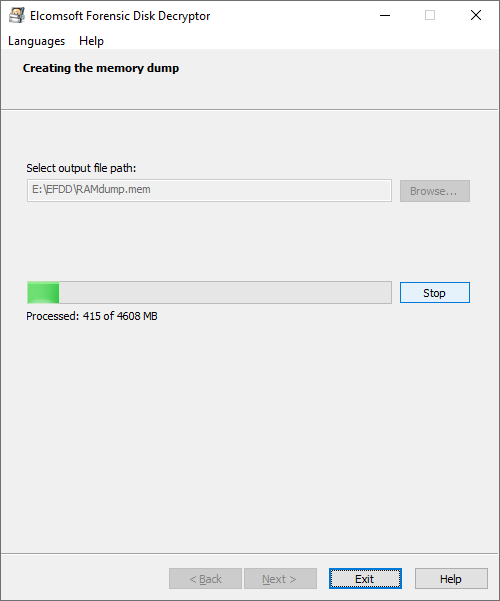
You can now transfer the memory dump onto your computer, and run Elcomsoft Forensic Disk Decryptor to search for OTFE keys.
Conclusion
Elcomsoft System Recovery does not allow you to magically break into encrypted disk volumes. Instead, the tool offers a faster alternative workflow to allow you quickly extracting information that may allow you extracting on-the-fly encryption keys or launching a password attack sooner than you would by employing the traditional approach.

















