In Apple’s land, losing your Apple Account password is not a big deal. If you’d lost your password, there could be a number of options to reinstate access to your account. If your account is not using Two-Factor Authentication, you could answer security questions to quickly reset your password, or use iForgot to reinstate access to your account. If you switched on Two-Factor Authentication to protect your Apple Account, you (or anyone else who knows your device passcode and has physical access to one of your Apple devices) can easily change the password; literally in a matter of seconds.
But what if you do know your password and your passcode but lost access to the only physical iOS device using your Apple ID and your SIM card at the same time? This could easily happen if you travel abroad and your phone is stolen together with the SIM card. There could be an even worse situation if your trusted phone number is no longer available (if, for example, you switched carrier or used a prepaid line and that line has expired).
It’s particularly interesting if you have a child under the age of 13 registered in your Family Sharing, and the child loses their only iOS device (at that age, they are likely to have just one) and their phone number (at that age, they are likely to use prepaid service). So let us explore what happens to your Apple Account if you lose access to your secondary authentication factor, and compare the process of regaining control over your account in Apple and Google ecosystems.
Apple Account: Two-Factor Authentication
If you are not familiar with two-factor authentication, go ahead and read this Apple’s article: Two-factor authentication for Apple ID. It’s good reading and really explains a lot of things (but doesn’t cover some others).
This is not the first time we write about two-factor authentication (Exploring Two-Factor Authentication is the most recent write-up that’s still worth reading). In fact, this is not even the first time we’re writing about the ugly side of two-factor authentication. Year over year, we couldn’t help but observe that Apple are making 2FA a way too powerful tool. Two-factor authentication had slowly mutated from being a roadblock to unauthorized account access into something else. Something that can be used to change one’s account password in a click, remove factory reset protection and disable iCloud lock/Find My iPhone. Today, your second authentication factor has become way more important than your password. Let’s compare what you can and cannot do with your login/password and your trusted device as your second authentication factor.
Log in to Apple Account
- Using login and password: no, you still need your second authentication factor.
- Using your second authentication factor: yes, you can change or reset your password to log in.
Factory resetting the iPhone, turning off iCloud Lock
- Using login and password: yes, you can use your Apple ID password to disable iCloud lock
- Using your second authentication factor: yes, you can change or reset your Apple ID password, then reset the phone and disable iCloud Lock
Restore new device from iCloud backup
- Using login and password: no, you still need your second authentication factor.
- Using your second authentication factor: yes, you can change or reset your password, then set up the new device.
If you lost your password
Losing the password to your Apple ID is no big deal. After all, companies have been dealing with lost passwords for decades. Well-established mechanisms exist allowing you or anyone else who has access to your SIM card or your iPhone (and knowing your passcode to that phone) to easily change or reset your account password.
Option 1: you can change the password if you have at least one trusted device acting as your second authentication factor.
Option 2: you can use iforgot.apple.com to reset your password. If you still have one of your devices that can receive a push notification via the 2FA mechanism, resetting the password takes less than a minute.
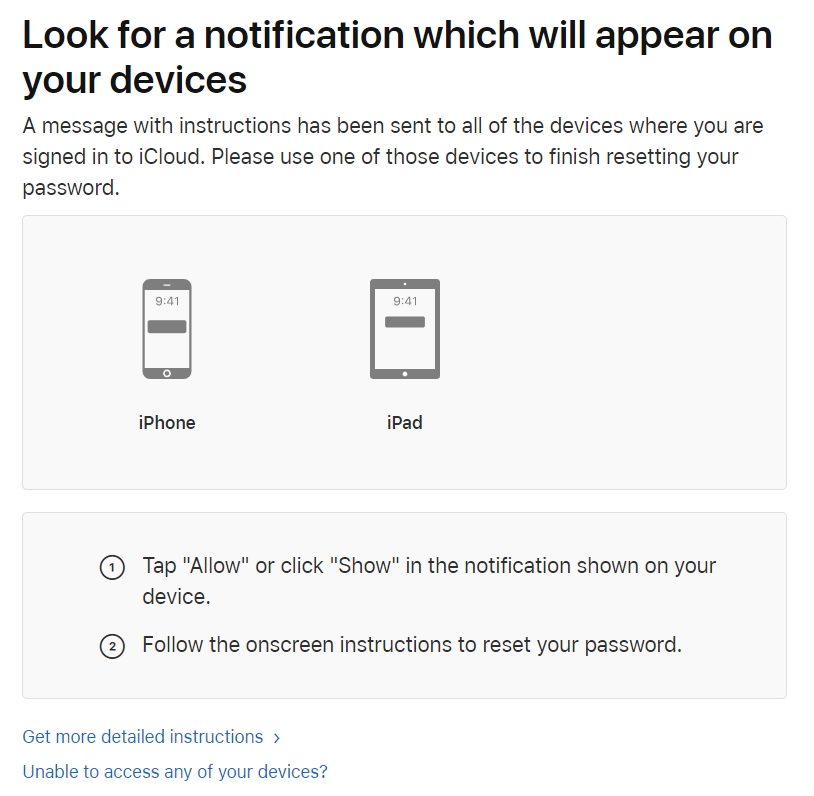
Option 3: there are plenty of other options allowing you to reset your Apple ID password if you still have access to your second authentication factor (be it a trusted device or a SIM card with a trusted phone number).

Security consequences of losing the password
There are no severe consequences to your personal information when losing your Apple ID password if you haven’t also lost your second authentication factor.
The only Apple service one can use without your second authentication factor is Find My Phone. In worst case scenario, a malicious person may remotely lock all your devices registered on that Apple ID (you can unlock them and change your Apple ID password) or remotely wipe your devices (in this case you lose data, but can change your Apple ID password and restore from a backup).
What counts as a second authentication factor?
The following items count as your second authentication factors:
- Your iPhone, iPad, iPod Touch or Mac computer that is signed in to your Apple ID
- Only if you can unlock it (with Touch ID, Face ID or passcode)
- Offline codes available via Settings > Apple ID > Password & Security
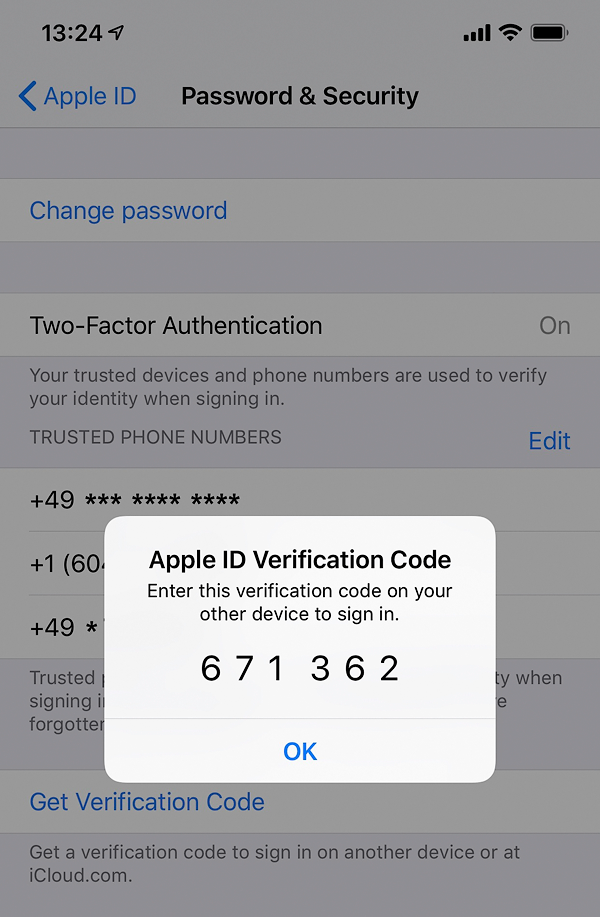
- Online codes pushed to your device (if Internet connection is available)
- In iOS 11.3 or later on your iPhone, users might not need to enter a verification code. In some cases, the trusted phone number can be automatically verified in the background on the iPhone.
- Your trusted phone number
- SIM card to receive SMS or phone call
- At least one trusted phone number must be registered with your Apple ID to use 2FA
- You can register multiple phone numbers as trusted numbers, but…
- Any trusted phone number can be used to change or reset your Apple ID
- Each trusted device initialized with unique seed; different verification codes pushed to different devices
Did you notice a trend here? Only your Apple device OR your trusted phone number can become your second authentication factor. No QR codes you could back up and no Windows/Android devices to serve as backups.
So what happens if you only have one Apple device (e.g. an iPhone or, say, an iPad mini) and one trusted phone number, and suddenly lose access to both?
If you lost your second authentication factor: Apple ID
Interestingly, losing your second authentication factor presents a truly unsolvable challenge. As in, if you lost access to ALL your trusted devices AND your trusted phone number, you are so out of luck – even if you know your account password and the passcode.
One may suggest that losing access to all instances of the second authentication factor would be highly unlikely (in fact, not that unlikely).
Security consequences of losing the second authentication factor
There may be severe consequences if you’ve lost your second authentication factor.
If you lost your iPhone, iPad or other Apple device WITHOUT a SIM card in it: a malicious person must first unlock it to access the second authentication factor. If you are using secure lock screen, the chance of successful unlock is low.
If you lost your trusted SIM card (with or without the iPhone): a malicious person may be able to reset your Apple Account password, remotely lock/erase your other devices, download your iCloud backups and some synchronized data (such as calendars, iCloud mail, photos and so on).
They will not gain access to any of the following: your passwords stored in iCloud Keychain; your Health data (if you were using iOS 12.0 or newer); your messages (text messages and iMessage history); some app data (e.g. Authenticator secrets, Gmail messages, chat logs in many instant messengers etc.)
Account recovery
A very common scenario for Apple users is losing their only iPhone while traveling. Without two-factor authentication, replacing the device would be as easy as buying a new one and restoring from the cloud backup. However, the lack of a trusted device and the loss of the only trusted SIM card puts travelers in an unfortunate situation where their only option is wait.
With Two-Factor Authentication, Apple introduced an automated way to reinstate account access. In most situation, a lengthy wait is imposed. Providing certain bits of additional information such as the registered phone number(s) can theoretically speed up the recovery.
Users are advised to go to iforgot.apple.com and follow the prompts. Even though the process is automated, recovery may take a very long time. According to Apple, “If you use two-factor authentication and can’t sign in or reset your password, you can regain access after an account recovery waiting period.” “When the wait period is over, Apple sends you a text or automated phone call with instructions to regain access to your account. Follow the instructions to immediately regain access to your Apple ID.”
Securing Children Accounts: Family Sharing, Screen Time and Two-Factor Authentication
Family Sharing is a great way to share one’s purchases with up to six family members. Apple recommends everyone, including minors, to use their very own Apple IDs on their personal devices. Adding children to your Family Sharing account also enables you to take control of how they use their devices by enabling Screen Time. In order for Screen Time to provide you with remote control over the child’s device through iCloud, you’ll be forced to add Two-Factor Authentication to your child’s account.
Adding children who are less than 13 years age to your family group is a one-way venue. For reasons unknown, Apple does not allow removing underage children from Family Sharing (not even by disbanding the family). As a result, if your child loses access to their (only) device and their trusted phone number at the same time, you may be stuck with an inactive Apple ID in your family that occupies one of the six available sharing slots. This is especially true if you didn’t bother registering a non-iCloud email for your child, making “yourchild@icloud.com” not only their Apple ID but their only email address as well.
Apple’s official recommendation is pushing the child’s account to another family group (a telephone conversation with Apple support left me with a clear impression of them suggesting you to make a fake Apple ID to push that stuck child away; don’t ask me why Apple chose to do it this way).
Think Different: How Google Handles Secondary Authentication
When it comes to two-factor authentication, Google is pretty much the direct opposite of Apple. Google does not tie you to any particular ecosystem, allowing you to use any (and I mean, any) device as your second authentication factor. Let’s just list what can act as 2FA in Google’s world:
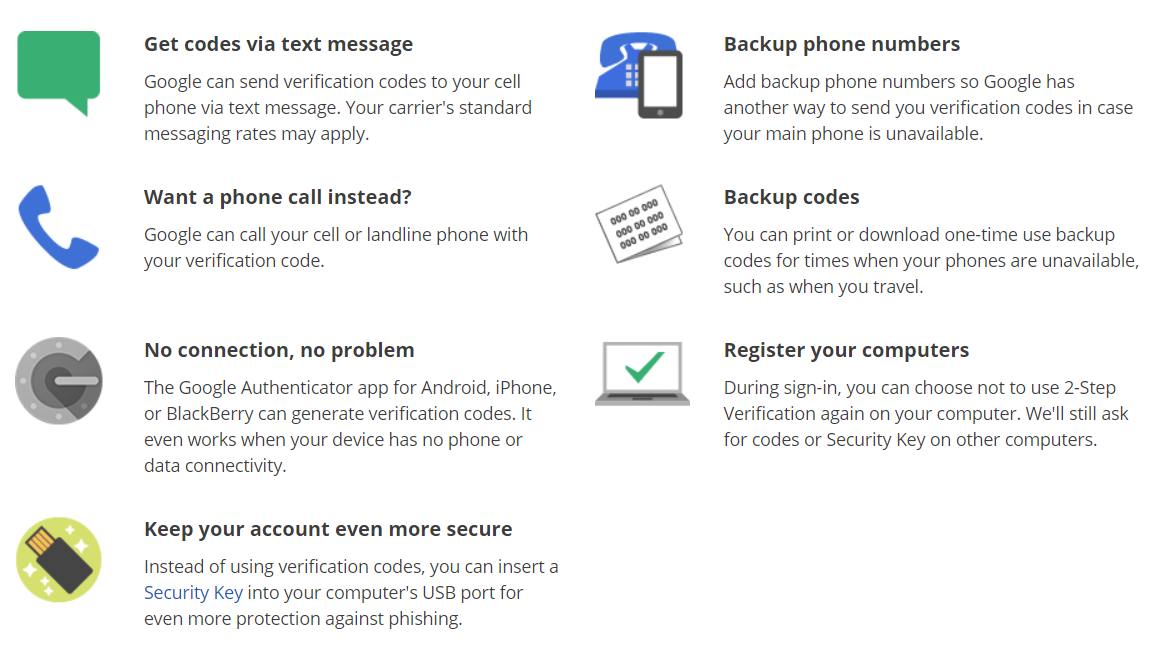
- Your Android phone or tablet that is signed in to your Google Account and configured to accept 2FA push prompts
- Only if you can unlock it (with biometrics, passcode, pattern etc.)
- By default, there will be no offline codes generated on the device (you may set them up separately)
- Online prompt pushed to your device (if Internet connection is available); a simple tap on “Yes” is enough to pass 2FA
- Authentication is always performed server side
- Your trusted phone number
- SIM card to receive SMS or phone call
- Google does not deem SIM cards and text messages as secure means of two-factor authentication, tries to push users away from using SMS for 2FA
- You can register multiple phone numbers as trusted numbers
- The Authenticator app
- Uses industry-standard TOTP protocol
- Multiple authenticator apps available on all major, minor and God forgotten platforms
- Compatible authenticator apps made by different manufacturers including Google, Microsoft, Xiaomi and independent developers
- All of them rely on a single seed delivered as QR code
- The QR code can be saved and re-used multiple times to initialize new authenticator apps
- The QR code can be stored in the cloud (different account) to allow remote access
- The QR code can be revoked instantly from the Google Account
- Backup codes: printable, to be stored in a safe place
- Security keys (FIDO U2F or built into your phone)
- A Web browser you used to sign in to your Google Account if you asked to no longer prompt for 2FA codes on that computer
If you lost your second authentication factor: Google Account
Google recognizes the issue of 2FA codes not being available after your phone is lost or stolen, and has a comprehensive write-up on the issue: Common issues with 2-Step Verification. Google makes its point by suggesting you use your backup options to sign in to your Google Account. Since Google is offering a much wider choice of secondary authentication factors, this suggestion does not look like a mockery, which we feel is the case with Apple.
If none of the backup options are available but you can still use your computer, you may be able to use that computer’s Web browser as a secondary authentication factor. If you are signed in to your Google Account in your computer (e.g. in the Chrome browser) and you asked Google to no longer prompt for 2FA codes on that device, you can simply open the Google Two-Step Verification page, type in your Google Account password and reset your two-factor authentication options. As an example, you can generate a new set of backup codes to allow you sign in to your Google Account instantly on a new Android phone, which will then become your secondary authentication factor.
If you have exhausted all of your backup options and don’t have access to a computer with trusted Web browser, you’ll have to go through the automated Account Recovery procedure. We tried following this procedure after deliberately losing the second authentication factor (but still specifying the correct password). Unfortunately, this can be hit or miss. In our test, not only was our recovery attempt unsuccessful, but Google has temporarily blocked access to the test account we were attempting to recover, requiring us to change the password.
Regaining access to Google child accounts via Family Link
Just like Apple, Google also allows users creating a family to share their purchases across several Google accounts. On Android devices, Google Family Link offers similar functionality to Apple Screen Time, allowing you to control how your children use their Android devices.
Google implements a very different approach to securing children accounts. While children under the age of 13 cannot set up their accounts to use two-factor authentication, it does not mean that anyone who knows the password can sign in. In order to log in to the child’s account, the sign-in must be approved by one of the authorized adult supervisors. An adult must enter a password to their Google Account (and pass 2FA) in order to authorize the child’s sign in.
If the child loses their only Apple device and their only trusted phone number, in Apple’s world they’ll be denied access to their Apple Account. Their parents can do very little (or nothing at all) to regain control over such accounts.
Google does not believe that this is an acceptable trade-off between security and convenience, and offers parents or legal guardians an easy way to regain control over the child’s account: one can simply reset the child’s password right away through the Family Link app (which, coincidentally, can be run on Android and iOS devices).
Conclusion
Both Apple and Google have their own implementations of two-factor authentication. In this article, we reviewed the differences between the two implementations in situation when the user, while still knowing their password, loses access to the secondary authentication factor. In addition, we reviewed the differences in accessing dependent (child) accounts in Apple and Google ecosystems.






