The long-awaited update for Elcomsoft Phone Breaker has arrived. The update brought back the ability to download iCloud backups, which was sorely broken since recent server-side changes introduced by Apple. We are also excited to become the first forensic company to offer support for iCloud backups saved by iOS 14 beta devices, all while supporting the full spectrum of two-factor authentication methods. We are proud to provide the most comprehensive forensic support of Apple iCloud with unmatched performance, accelerating forensic investigations and providing access to critical evidence stored in the cloud.
The Synced Data
We’ll be back to iCloud backups shortly. The screen shot below is just to grab your attention:
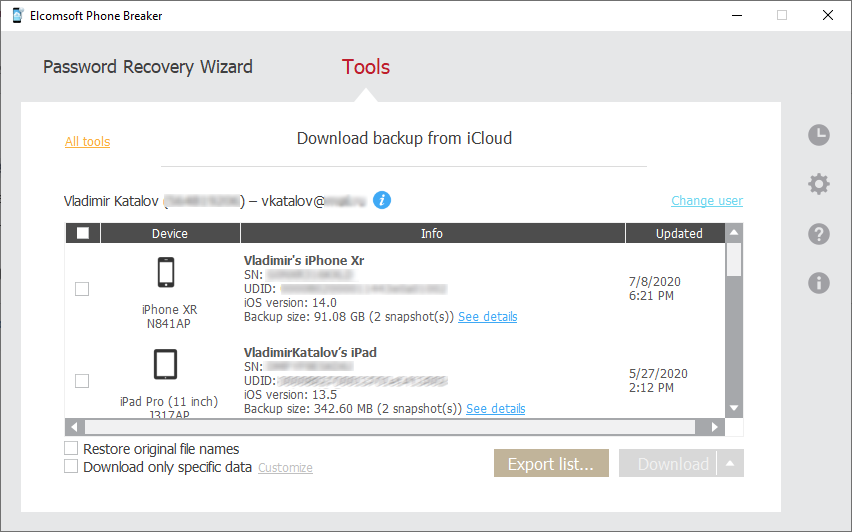
In the previous update released over a month ago, we concentrated on synced data. The previous update was making it easier for you to get them altogether in just a few clicks. The price for this was the lost ability to selectively download albums from iCloud Photos; we hope you don’t mind as it usually does not take long downloading them all.
Downloading synchronized data from Apple iCloud is not as simple as we make it sound, especially when talking about “end to end encrypted” data, which includes the iCloud Keychain, Health, Messages and so on. Not only do you need the account credentials including the second authentication factor, but also the passcode (or password, speaking of a Mac) of one of the trusted devices. Our software pretends to be a trusted device, which is the only way to access what Apple calls end to end encrypted data. Note that we do not need the device itself, just its passcode.
Here is where the trouble starts. We were experimenting with a couple dozen different devices ranging from the Apple TV to the latest iPhones, and including legacy devices running outdated iOS versions. We used those with multiple iCloud accounts ranging from our daily drivers to disposable test accounts. The accounts have been registered in several different countries, as iCloud actually works differently depending on the territory. What we found was surprising: Apple iCloud was just slightly less reliable and transparent than any of its major rivals (bar Microsoft).
We always start our research without even looking at the low-level code or poking the protocols. Instead, we are using devices and accounts the way we normally do. While doing that, we observe how syncing works in the real life, what exactly is synced and how, what is the effect of changing the passcode on one of the trusted devices, for how long deleted data is stored (or remains accessible), and so on. We apply the same methodology when testing our products. Our Q&A team had spent an enormous amount of time trying to understand why certain features of our products do not work as expected (while they definitely should). The answer was simple. They did not work on real Apple devices either. Sometimes logging out and back it forced certain data to resume syncing, and sometimes not. We encountered that with the keychain, Health, Safari history etc.; it’s hard to name a category that always works properly.
We are doing our best, and our software has support of widest range of iCloud data (though something is still left out, such as everything about HomeKit).
The iCloud Backups
If pulling synchronized data from iCloud is just very complex, accessing iCloud backups is a nightmare. It was a nightmare from the very beginning since we first added support for iCloud backups some 7 years ago, remaining the only company doing that for a long time. Apple did not have 2FA at the time, can you believe that?
iCloud backups are stored in a very sophisticated way, and downloading them was always troublesome. Nearly every major iOS update brought surprises. Even worse, Apple are continuously introducing small changes to iCloud protocols, data storage formats, encryption etc.
Are they improvements? We don’t believe so, as many (if not most) of them have a sole purpose of stopping our tools (and the tools of our competitors) from working. Or, for example, locking the user’s iCloud account after the data has been already downloaded. Or force the user to change the password. Or… Well, this is definitely outside the scope of this article.
Locating and fixing these issues and implementing workarounds takes an enormous amount of time. We never give up, but I am curious how the law enforcement agencies are going to work if they cannot download the data from Apple servers. While it is possible to obtain the data directly from Apple, it is a long and complex procedure; while with the right software it may take just minutes. For my thoughts on the matter (as well as iCloud security tips), read the Apple vs Law Enforcement: Cloudy Times article.
How do backups and synced data compare? They don’t, as they mostly cover different and exclusive types of data. Try to get get both if you can. Some data is being synced only, while the other data is available only in backups. Examples? The most notable ones are media files, messages and health data. Depending on your iCloud settings, media files and messages are either synced or stored in iCloud backups, but not both. Health data is always synced only (also available in local iTunes backups, but only if you have a password set). Some data like call log is not available anymore in either cloud backups or synced data.
Troubleshooting
Please note that once you attempt downloading an iCloud backup with any version of Elcomsoft Phone Breaker older than the 9.61, the following two things will happen:
- Authentication fails with an error.
- The user’s iCloud account is temporarily locked for up to 48 hours. During that period, even attempts to restore the physical iOS device from the iCloud backup will fail. Downloading synced data will continue working.
Note that once the account is locked, even the latest version of Elcomsoft Phone Breaker will fail accessing iCloud backups until the lockout timer runs out. If you still experience a problem with the latest version (at this time, EPB 9.61) and you had not used an older version during the past 48 hours, here is what to do:
- Close the program.
- Delete or move to a different folder the following files from the program’s AppData (Windows) or Library (macOS) folder:
- Credentials
- EscrowCache2.0
- Settings.xml
- Start the program and try again.
You will have to enter the Apple ID credentials again instead of using saved ones, and you will need to pass two-factor authentication once again. If you are accessing end-to-end encrypted data, you’ll have to re-enter the device passcode or system password of a trusted device; the latter does not apply to backups. You’ll have to specify the correct settings such as the output folder, log level etc. The tool does its best to “recover” from failed logins, and one of the reasons for authentication errors could be using outdated cached data. It does not always work, but removing the files mentioned above usually helps. If not, generate a maximum-level log file and send it over to our support team.
TL;DR
We can download iCloud backups again, and iOS 13 is now fully supported, as well as the older versions of iOS versions. There is no access to iCloud backup with authentication tokens; this is no longer possible, and haven’t been for a long time. We don’t expect token-based authentication to work anytime soon for the purpose of accessing iCloud backups. The good news? We have all available 2FA methods covered, including SMS codes, push messages, or offline codes generated on the device.
iOS 14 (beta) is supported, too, although treat it as preliminary due to the pre-release nature of the new OS. We compared cloud backups saved by iOS 13 and iOS 14 devices, and discovered only a few notable differences.
To tell the truth, I would call cloud backups for iOS 13 and below can “experimental”, too. At any time, Apple can roll out a server-side update with improvements, restrictions or protections. For the time being, downloading iOS 13 and 14 backups with our tool works perfectly.
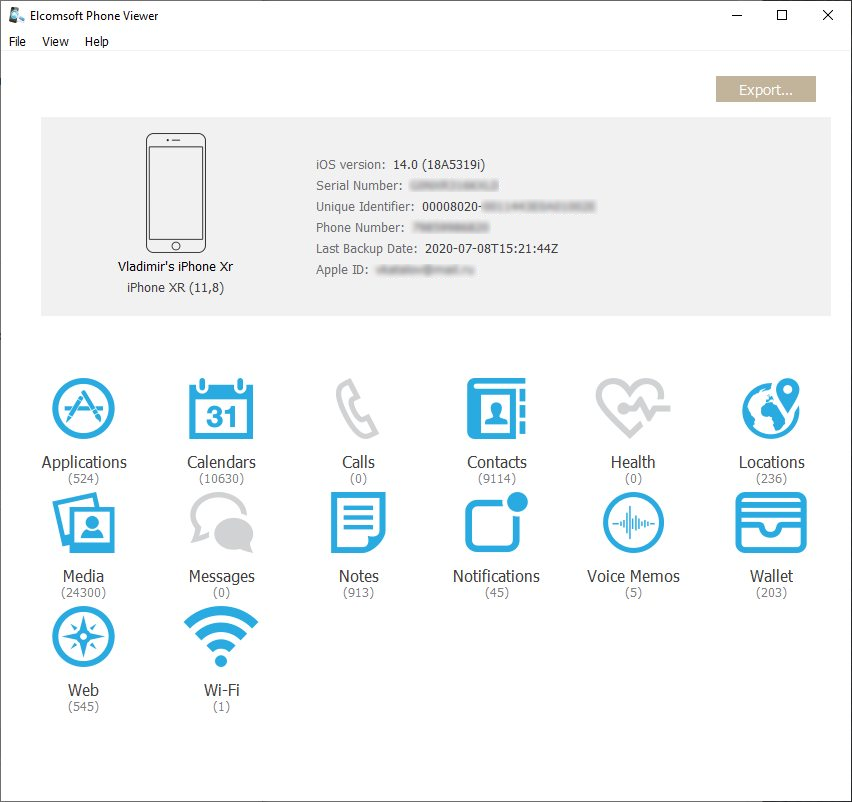
To view backups downloaded from iCloud, use Elcomsoft Phone Viewer or a different tool of your choice. Please note that the current version of the tool does not support iOS 14 backups yet. This is not about iCloud but about iOS 14 itself (local iTunes backups are not supported by EPV either). We will keep you updated. We have an update for Elcomsoft Phone Viewer in the works, and it is currently being tested internally. We just need to take care of a few changes in a few system and user databases.