The checkra1n jailbreak is fantastic. Not only does it work with the latest versions of iOS the other jailbreaks aren’t even available for, but it also allows performing partial data extraction from disabled and locked iPhones even if the passcode is not known. Still, you can encounter some problems if the USB restricted mode has been activated on the device. The latest build of chechra1n is to the rescue.
USB restrictions
If you missed our articles on the USB restricted mode, start reading from Apple’s Using USB accessories with iOS 11.4.1 and later article.
Starting with iOS 11.4.1, if you use USB accessories with your iPhone, iPad, or iPod touch, or if you connect your device to a Mac or PC, you might need to unlock your device for it to recognize and use the accessory. Your accessory then remains connected, even if your device is subsequently locked.
If you don’t first unlock your password-protected iOS device—or you haven’t unlocked and connected it to a USB accessory within the past hour—your iOS device won’t communicate with the accessory or computer, and in some cases, it might not charge. You might also see an alert asking you to unlock your device to use accessories.
There were some notable improvements to this mode since then in both iOS 12 and 13. Currently, the major problem for the forensic expert is this: under certain circumstances (after a period of time, or if the emergency S.O.S. mode has been activated), the Lightning port is disabled on the device, and you cannot connect to the iPhone at all.
checkra1n
Whether the device is locked or not, you can still extract some information from it even without breaking the passcode. We have introduced BFU data extraction with the help of checkra1n back in November last year, see iOS Device Acquisition with checkra1n Jailbreak. What about the USB restrictions? See A word on USB restricted mode and pairing chapter at the link above. checkra1n is installed from the DFU (Device Firmware Update) mode that is always accessible even if the restricted mode has been activated for any reason. Moreover, old versions of checkra1n (that were available at the time), USB restrictions were turned off once jailbreak was installed.
The situation had changed in the later builds of chechra1n, see the DFU and USB Restricted Mode chapter in BFU Extraction: Forensic Analysis of Locked and Disabled iPhones. While you can still use the older build of checkra1n 0.9.5, that older build may not support the latest iOS versions (currently iOS 13.6). The solution, however, has been found: use a third-party tool that turns the USB restrictions off through the diagnostics mode, see Working Around the iPhone USB Restricted Mode. This extra step was never obvious and rather complicated, but at least it was there.
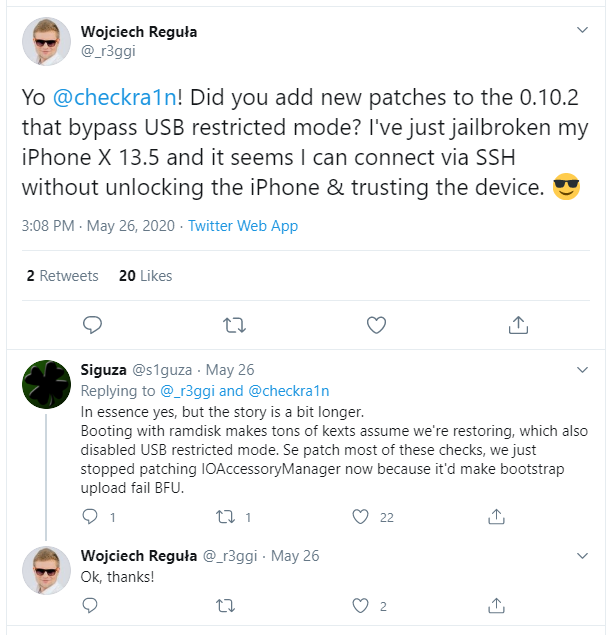
With checkra1n 0.10.2 (currently the latest version), the game has changed again. Whether USB restrictions are activated or not before you turned the device into the DFU mode, the device will be available after the reboot over the USB cable, and you can perform the extraction with Elcomsoft iOS Forensic Toolkit (do not forget the port number is 44 instead of common 22). Due to the nature of BFU extraction, do not expect too much of the keychain though. Speaking of the file system, not that much data is available either, but some notable evidence still can be found. The available bits and pieces include the account information, several system files, logs, message attachments, third-party app data, etc. If the device is locked with an unknown passcode, this is much better than nothing.
If you need a technical explanation why it works this way, here it is:
Installation & usage
There is quite a lot of checkra1n manuals available, and we are not going to do copy-and-paste, but there are still a couple of important things that are rarely mentioned.
First, make sure you have read our recent article about checkra1n Installation Tips & Tricks, it will save you a lot of time.
Second, if you want to use checkra1n in the BFU mode (when the passcode is not known) and USB restrictions have been activated, it is not enough just to fire checkra1n an follow the instructions, as the program simply will not see the device connected. You have to do one of the following manually:
- Put device into Recovery mode and start the GUI version of checkra1n, then follow the instructions in the program, or
- Put device into DFU mode and start the CLI version (it will do everything automatically).
We recommend the latter although it is a little bit more tricky; by our experience, this method has better success rate (while that may sound strange, as the program is course the same). I bet you will spend may be half an hour at the first time (if you did not do that before, and especially if you are not very familiar with macOS, command-line tools and DFU mode), but then will do that at the blink of an eye.
iOS 13.6 and iOS 12.4.8
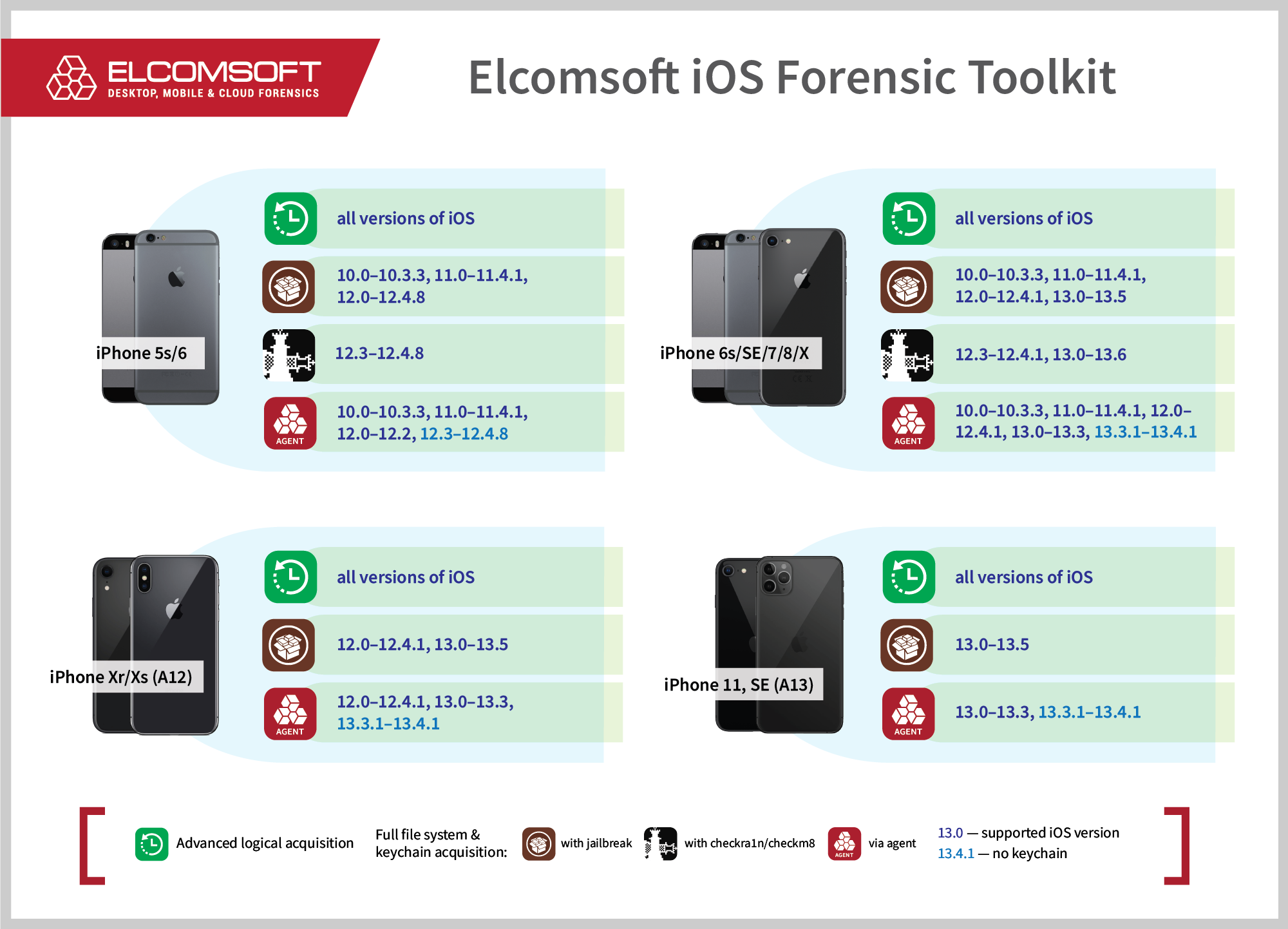
checkra1n works just fine with the latest versions of iOS, including iOS 12.4.8 for the iPhone 5s and iPhone 6, and iOS 13.6 on the iPhone 6s and later, both released just a couple of days ago. We have verified that on several test devices we have in our lab. Just remember that the last model supported by checkra1n is the iPhone X. For iPhone Xr, iPhone Xs and iPhone 11 devices, BFU acquisition is not possible at all.
Do you know the passcode (or the device is not locked at all) and want to perform the keychain and file system extraction? We got you covered in more than one way. Below is the updated compatibility chart. Interestingly, iOS 12.4.8 does not fix several known vulnerabilities, and apart from checkra1n, you have other options available. You can use our agent-based extraction method (recommended, as it is a forensically sound and safe to the device). Alternatively, you can install the latest version of RootlessJB4. RootlessJB4 is not completely stable as of yet, but still worth trying if you also need to extract the keychain without installing checkra1n, as our agent cannot access the keychain for iOS 12.3 through 12.4.8 (only file system extraction is available for these iOS versions).