LUKS encryption is widely used in various Linux distributions to protect disks and create encrypted containers. Being a platform-independent, open-source specification, LUKS can be viewed as an exemplary implementation of disk encryption. Offering the choice of multiple encryption algorithms, several modes of encryption and several hash functions to choose from, LUKS is one of the tougher disk encryption systems to break. Learn how to deal with LUKS encryption in Windows and how to break in with distributed password attacks.
Disk Encryption Basics
All disk encryption tools rely on symmetric cryptography to encrypt data. More often than not, major disk encryption tools rely on the hardware-accelerated AES encryption with a 256-bit key, although Microsoft BitLocker defaults to using 128-bit AES keys. Some disk encryption tools offer the choice of encryption algorithms, the champion being VeraCrypt with some 15 options for symmetric encryption.
The symmetric encryption keys are derived from the user’s password (or other data) by using a Key Derivation Function (KDF). The KDF employs one-way transformations (hash functions) of the user’s input to produce the binary encryption key (or an to unwrap an intermediary key that decrypts the actual symmetric encryption key). Different hash functions and with numerous hash iterations are used to slow down the speed of potential brute force attacks.
When attacking an encrypted container, you must either know the exact combination of the encryption algorithm, the hash function, and the number of hash iterations. Making the wrong choice effectively voids your chance of successful recovery even if you stumble upon the correct password.
LUKS Disk Encryption
LUKS is a platform-independent disk encryption specification originally developed for the Linux OS. LUKS is a de-facto standard for disk encryption in Linux, facilitating compatibility among various Linux distributions and providing secure management of multiple user passwords. Today, LUKS is widely used in nearly every Linux distribution on desktop and laptop computers. It is also a popular encryption format in Network Attached Storage (NAS) devices, particularly those manufactured by QNAP.
In addition to full-disk encryption, LUKS can be used to create and run encrypted containers in a manner similar to other crypto containers such as VeraCrypt. Encrypted containers feature the same level of protection as LUKS full-disk encryption.
LUKS offers users the choice of various encryption algorithms, hash functions and encryption modes, thus providing some 45 possible combinations.
LUKS encryption algorithms
LUKS supports multiple combinations of encryption algorithms, encryption modes, and hash functions including:
- AES
- Serpent
- Twofish
- CAST-128
- CAST-256.
Being the only hardware-accelerated encryption algorithm, AES is by far the most common of the three, especially when used in enterprise environments and network attached storage (NAS) devices. AES encryption offers that highest stream cipher performance when used on chip sets featuring AES encryption acceleration (e.g. the AES-NI instruction set in Intel CPUs). Serpent and Twofish can be manually specified by the user at the time of creating the encrypted volume. In our tools, AES, Serpent, and Twofish algorithms are supported.
LUKS encryption modes
LUKS supports the following encryption modes:
- ECB
- CBC-PLAIN64
- CBC-ESSIV:hash
- XTS-PLAIN64
Various Linux distributions may use different default settings when setting up an encrypted volume. For example, Red Hat Linux employs cbc-essiv:sha256 with a 256-bit AES key, which is the default combination for many popular Linux distributions. Our tools support CBC-PLAIN64, CBC-ESSIV:SHA256, and XTS-PLAIN64 encryption modes.
LUKS hash functions
In disk encryption, hash functions are used as part of the Key Derivation Function (KDF). KDF are used to derive the binary encryption key out of the user-provided input (typically, a text-based passphrase). The following hash functions are supported in the LUKS specification:
- SHA-1
- SHA-256
- SHA-512
- RIPEMD160
- WHIRLPOOL *
* The support for WHIRLPOOL is not part of the specification, yet our tools support this hash function along with the four “official” ones. By default, most Linux distros use SHA-256 as a hash function.
LUKS Default encryption settings
While the maintainers of each Linux distro and hardware manufacturers with embedded Linux are free to choose their very own default encryption settings, aes-cbc-essiv:sha256 with 256-bit symmetric encryption keys is the most common default encryption setting. This is what it stands for:
- AES – the encryption algorithm is AES (by default, 256-bit keys are used)
- CBC – Cipher Block Chaining encryption mode
- ESSIV – Encrypted Salt-Sector Initialization Vector. This IV should be used for ciphers in CBC mode.
- SHA-256 – Secure Hash Algorithm computed with 32-bit words. This is the default hash function for ciphers in CBC mode.
Non-default encryption settings
Decryption settings other than the defaults can be specified by the user at the time they encrypt the disk. Unlike TrueCrypt/VeraCrypt, LUKS does store the information about the selected encryption settings in the encryption metadata, making it possible to detect the encryption settings prior to launching the attack. Elcomsoft Distributed Password Recovery automatically detects LUKS encryption settings by analyzing the encryption metadata, which must be extracted with Elcomsoft Forensic Disk Decryptor prior to launching the attack.
Multiple encryption keys
A single LUKS volume may be protected with more than one key. The specification allows multiple user keys to decrypt the master key that is used for encryption. As a result, a LUKS-encrypted device may contain multiple key slots, which are used to store backup keys/passphrases and to allow multiple users unlock LUKS volumes each with their own password.
Each key slot is protected with a unique salt, making the reverse brute force attack (matching the same KDF of a password against the different slots) unfeasible. A KDF must be calculated separately for each key slot during the attack. As a result, recovering password to protecting a LUKS device requires selecting a key slot to attack. This selection is performed with Elcomsoft Distributed Password Recovery when setting up the attack.
Breaking LUKS Encryption Step 1: Extracting Encryption Metadata
To secure access to the data stored in the encrypted device, you must first recover the original, plain-text password. There are several steps involved requiring the use of several different tools.
- Extract the encryption metadata from the encrypted device or disk image using Elcomsoft Forensic Disk Decryptor or Elcomsoft System Recovery.
- Use the extracted metadata (a small file) to launch an attack on the password with Elcomsoft Distributed Password Recovery.
- Once the password is found, mount the disk volume or decrypt the data.
We have two different tools for extracting LUKS encryption metadata. The choice of the right tool depends on whether you are working in the field or in a lab. If you are analyzing the suspect’s computer, Elcomsoft System Recovery can be used to boot the system from a USB flash drive and extract the encryption metadata from the storage devices connected to the computer.
Note: LUKS encryption is supported in Elcomsoft System Recovery 7.06 and newer. If you are using an older version of the tool, please update to the latest version to obtain LUKS support.
- Download Elcomsoft System Recovery, launch the installer and create a bootable USB drive.
- Use the USB drive to boot the target system into the Windows PE environment.
- Elcomsoft System Recovery will be launched automatically.v
- Review the attached disks.
- Select LUKS-encrypted partitions and click “Dump” to extract the encryption metadata.

- Transfer the encryption metadata on your computer and use it with Elcomsoft Distributed Password Recovery to launch an attack on the LUKS encryption password.
If you are working in a lab and processing disks or disk images, you’ll be using Elcomsoft Forensic Disk Decryptor. Extracting encryption metadata with Elcomsoft Forensic Disk Decryptor is simple.
Note: LUKS encryption is supported in Elcomsoft Forensic Disk Decryptor 2.13 and newer versions. If you are using an older version of the tool, please update to the latest version to obtain LUKS support.
- Launch Elcomsoft Forensic Disk Decryptor.
- Select operation mode “Extract/prepare data for further password recovery”.

- Open the physical device or disk image containing LUKS volume(s). In the example below, we’re dealing with a physical device.
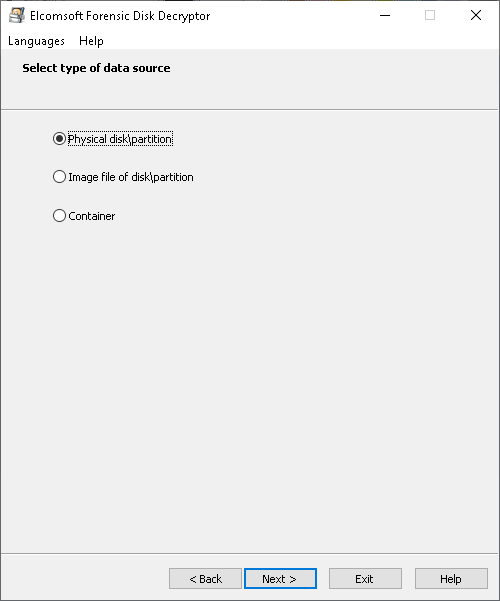
- EFDD will display the list of encrypted volumes. Select the volume you are about to extract encryption metadata from.
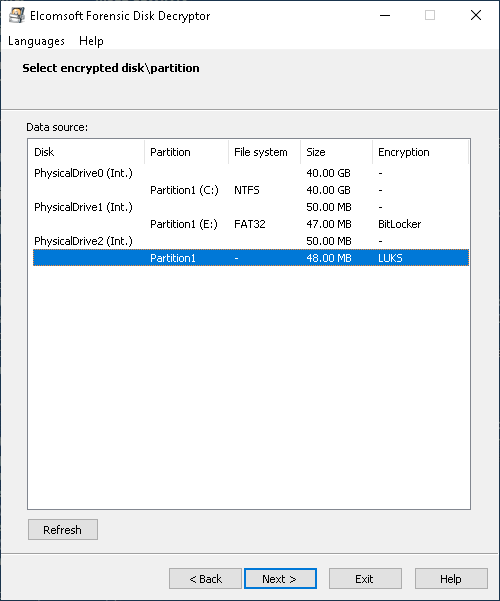
- Click Next to extract the encryption metadata and save it into a file.

Breaking LUKS Encryption Step 2: Attacking the Password
While LUKS offers strong protection against brute force attacks by using thousands of iterations of a hash function during key derivation, we have significant advances in password recovery attacks compared to what we had in the past. Brute-forcing a password today becomes significantly faster due to the use of GPU acceleration, distributed and cloud computing. Up to 10,000 computers and on-demand cloud instances can be used to attack a single password with Elcomsoft Distributed Password Recovery.
In order to set up the attack, do the following.
- Launch Elcomsoft Distributed Password Recovery.
- Open the file containing the encryption metadata that you obtained with Elcomsoft Forensic Disk Decryptor during the previous step.
- The available key slots along with the number of hash iterations will be displayed. Specify the key slot to attack.
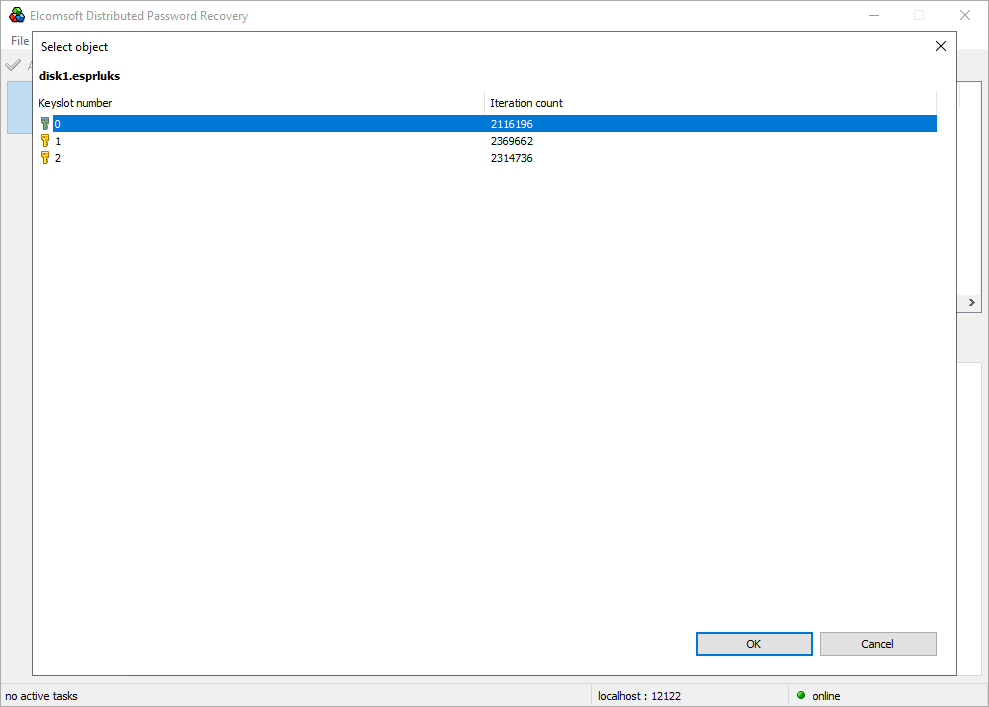
- Configure and launch the attack.
Brute force attacks became not just faster, but much smarter as well. The user’s existing passwords are an excellent starting point. These passwords can be pulled from the user’s Google Account, macOS, iOS or iCloud keychain, Microsoft Account, or simply extracted from the user’s computer. The user’s existing passwords give a hint at what character groups are likely used:
Elcomsoft Distributed Password Recovery offers a number of options to automatically try the most common variations of your password (such as the Password1, password1967 or pa$$w0rd):
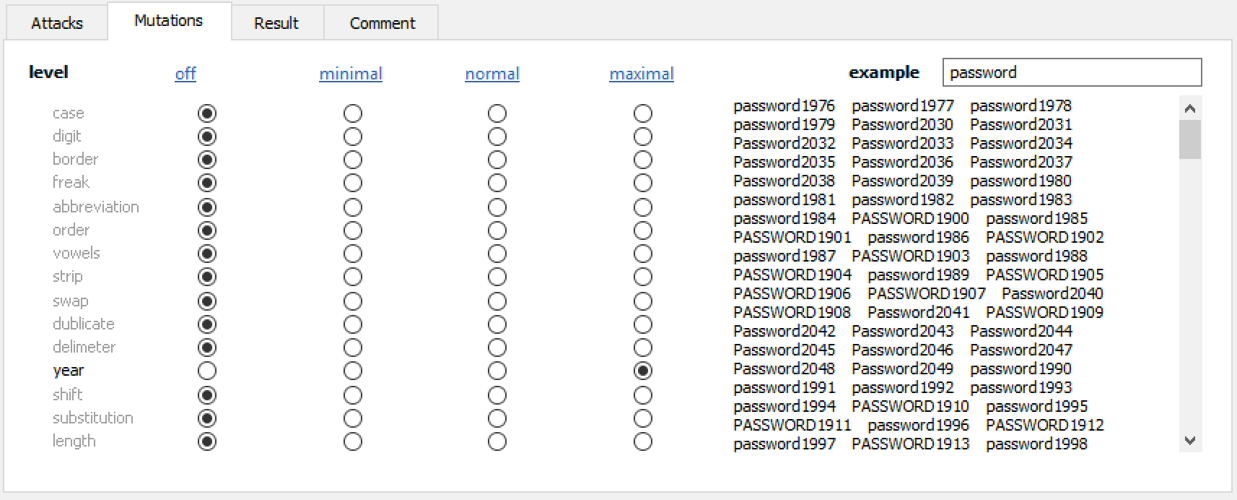
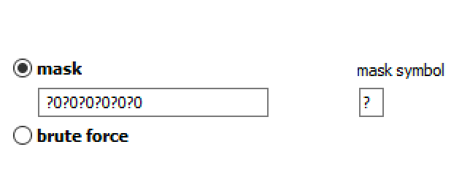
Masks can be used to try passwords matching established common patterns:
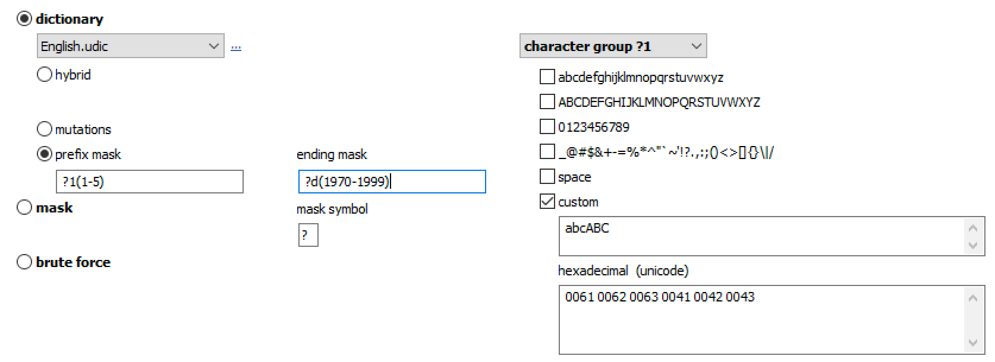
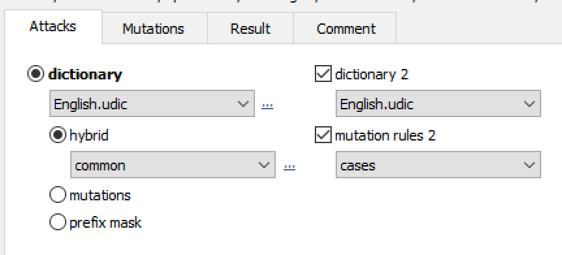
Advanced techniques allow composing passwords with up to two dictionaries and scriptable rules:
How Long Will It Take to Break the Password?
Even if you know exactly how many passwords per second the attack will yield, there are many things affecting the time it will take to recover the LUKS password. The length of the password and its entropy, as well as the things you know about the password or the way the user makes up their passwords, will have drastic effect on the time it will take to break a particular LUKS volume.
What about the recovery speed? The speed is also not a constant, and there are a lot of things affecting the speed of the attack that aren’t immediately obvious. The number of passwords per second you can try depends on several things, the most important being the following:
The hardware. The more/higher end video cards you have, the higher the raw speed you will get. Same goes for the number of computers doing the attack; the more computers are crunching the password, the faster the speed will be.
The hash function. Some hash functions are slower than others. In the case of LUKS, the user has the choice of five hash functions including RIPEMD160, SHA-1, SHA-256, SHA-512, and WHIRLPOOL, RIPEMD160 being the fastest and WHIRLPOOL the slowest of the pool. Depending on the choice of the hash function made at the time of setting up the encryption, your attacks may go faster or slower.
The encryption algorithm and encryption mode. Once again, these settings are selected at the time the user sets up the encryption. The choice affects the speed of the attack, but to a significantly minor degree compared to the choice of a hash function.
The number of hash iterations and, indirectly, the speed of the user’s computer. Unlike other disk encryption tools such as BitLocker or VeraCrypt, LUKS varies the number of hash iterations used to protect the master encryption key. When creating an encrypted disk with a given combination of encryption settings, LUKS benchmarks the user’s system. The data is used to select the number of hash iterations protecting the master encryption key. Effectively, LUKS-encrypted disks or containers created on a lower-end computer will feature weaker protection compared to similar disks or containers created on higher-end hardware. The number of hash iterations does not change if the disk or container is moved to a new, more powerful computer.
What’s even more interesting is that the number of hash iterations varies depending on the choice of other encryption settings. A larger number of hash iterations is selected if a weaker (faster) hash function is used, and vice versa. Theoretically, the variable number of hash iterations would make the speed of attacking LUKS volumes or containers created on similar hardware the same regardless of the chosen hash function and encryption settings. This is not the case; there are still differences in attack speeds between the different algorithms and hash functions as shown in the following benchmark.
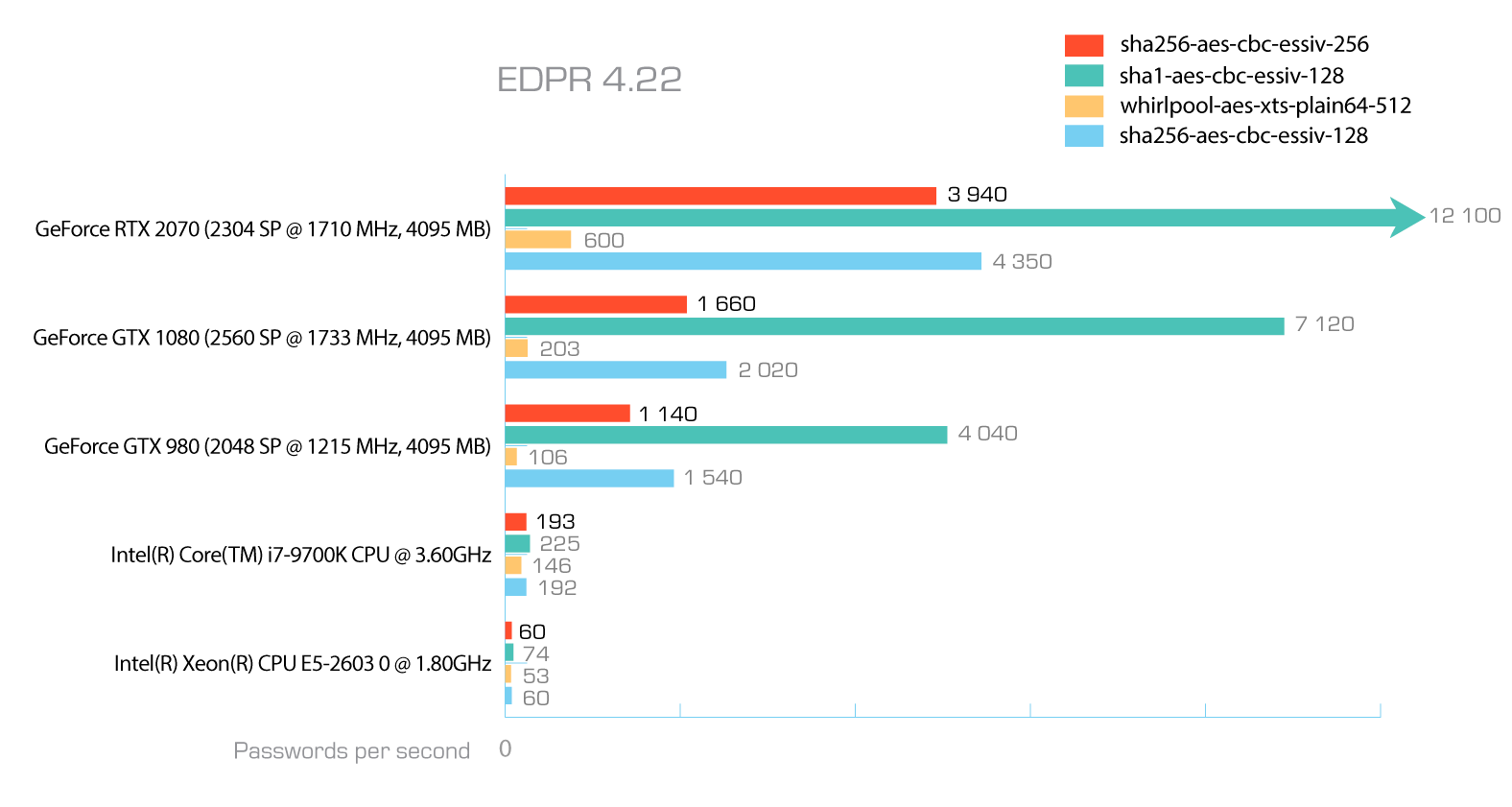
Notably, the number of hash iterations is stored with other encryption metadata (which is not the case for TrueCrypt/VeraCrypt containers making the number of hash iterations yet another user-provided secret).
Conclusion
LUKS is not only a popular and widespread encryption specification, it’s also a very interesting one to work with. The support of multiple key slots, the choice of hash functions, encryption algorithms and encryption modes, and the benchmark-based algorithm for automatically selecting the number of hash iterations when setting up encryption based on the performance of the user’s computer make LUKS an exemplary implementation of disk encryption.














