Virtual machines use a portable, hardware-independent environment to perform essentially the same role as an actual computer. Activities performed under the virtual umbrella leave trails mostly in the VM image files and not on the host computer. The ability to analyze virtual machines becomes essential when performing digital investigations.
Many types of virtual machines used in the criminal world feature secure encryption. Evidence stored in encrypted VM images can be only accessed if one can produce the original encryption password. We built a tool to enable experts run hardware-accelerated distributed attacks on passwords protecting encrypted VM images created by VMWare, Parallels, and VirtualBox.
Virtual machine encryption
The most common virtual machines that can encrypt the entire image are Parallels, VMWare, and VirtualBox. However, the encryption strength and the resulting password recovery speeds are vastly different between these VMs. Let us have a look at what the developers of the three VMs do to protect their content.

Parallels: the broken implementation
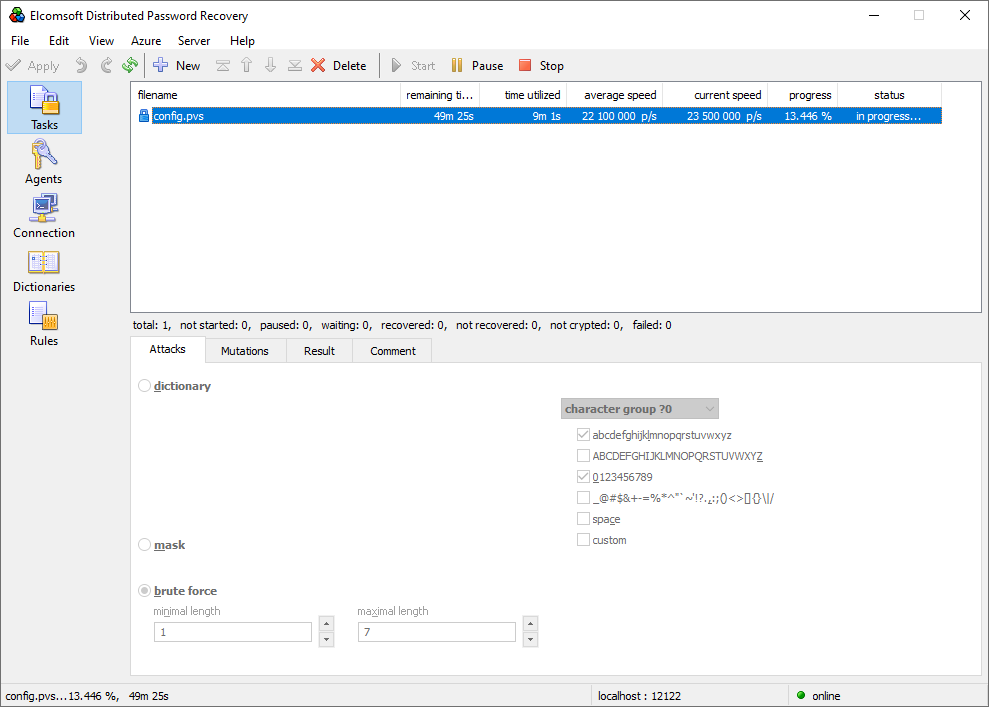
Parallels has the weakest protection of the trio. While Parallels uses the AES-128 CBC algorithm to encrypt the data, the encryption key is derived with a measly two iterations of a dated MD5 hash function. As a result, Parallels is the fastest to attack. We’ve been able to reach the speed of some 19 million passwords per second on a single Intel i7 CPU. With this kind of speed, the recovery of reasonably complex passwords is possible even without GPU acceleration. This speed is fast enough to discover simple passwords using plain old brute force, while the more complex ones will still require the use of dictionaries and mutations.
VMware: just about average
VMvare uses the same AES-128 encryption algorithm. However, its real-world protection is a night and day difference to Parallels. VMware uses 10,000 rounds of stronger PBKDF-SHA1 hash to derive the encryption key from the password. A CPU-only attack results in around 10,000 passwords a second, making the supported GPU-assisted recovery strongly recommended. The use of a single NVIDIA GeForce 2070 RTX board boosts the recovery speed to 1,6 million passwords per second. This allows finding the reasonably complex passwords. Still, using a targeted dictionary with reasonable mutation settings is recommended.
VirtualBox: the toughest protection
Finally, Oracle VirtualBox delivers the strongest protection with the most secure encryption. The encryption algorithm can be either AES-XTS128-PLAIN64 or AES-XTS256-PLAIN64, while the SHA-256 hash function is used to derive the encryption key from the password. The number of hash iterations depends on the length of the AES encryption key, and reaches an astonishing value of up to 1.2 million hash iterations. It’s no wonder that CPU-only attacks are miserably slow, yielding the recovery speed of only 15 passwords per second. GPU-assisted attacks are significantly faster, delivering the speed of up to 2700 passwords a second on a single NVIDIA GeForce 2070 RTX board. In addition to a good GPU, we strongly recommend a targeted dictionary and reasonable mutation settings.
Steps to break VM encryption
We’ll use Elcomsoft Distributed Password Recovery to open the encrypted virtual machine and set up an attack on its password.
Pre requisites: You will need Elcomsoft Distributed Password Recovery 4.30 or newer to attack VM passwords. In order to launch the attack, you won’t need opening the entire container, which may be extremely large. Instead, we’ll be using small files from the VM folder. For Parallels, we’ll need the config.pvs file. For VirtualBox, the corresponding .vbox file. For VMware, the .vmx. These files are very small (several KB), and are all that you need to launch the attack.
- Launch Elcomsoft Distributed Password Recovery 4.30 or newer.
- Open the virtual machine as shown on the screen shots below. Use the corresponding files for each type of the virtual machine.
- For Virtualbox, open the .vbox file:

- For VMware, open the .vmx file:
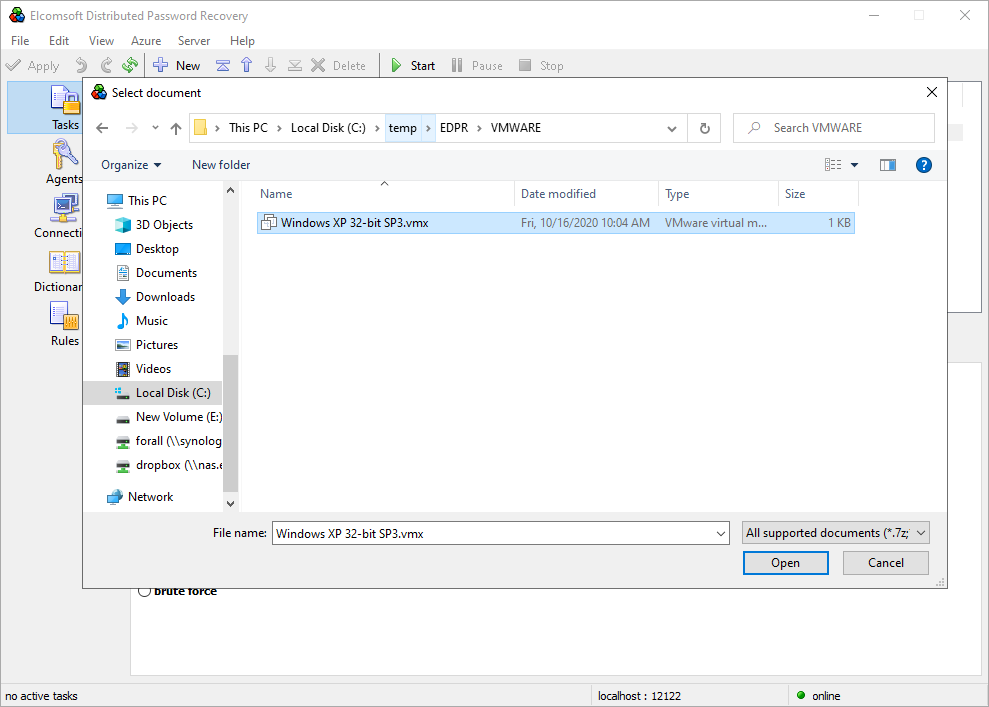
- For Parallels, open the config.pvs file from the folder containing the VM.

- Configure and launch the attack using the dictionaries, mutations and/or the new Rules tab to set up a hybrid attack using the John the Ripper syntax. You can read more about the hybrid attack in this blog article.
Once you launch the attack, you can observe the recovery speed. Parallels would be the quickest to attack even with a single CPU:
Conclusion
The use of virtual machines in the criminal world is on the rise. The ease of use and the level of protection provided by common VMs enable criminals to sneak their traces under a virtual umbrella, reducing the risks of an accidental leak of incriminating evidence. We made our step, building a tool to help law enforcement gain access to evidence stored in encrypted VMs by doing our best in breaking the encryption password in as little time as possible.







