New in Elcomsoft System Recovery: Microsoft Azure Accounts, LUKS2 and Forensic Tool Filters
August 4th, 2022 by Oleg Afonin
Category: «General»
Elcomsoft System Recovery 8.30 introduced the ability to break Windows Hello PIN codes on TPM-less computers. This, however, was just one of the many new features added to the updated release. Other features include the ability to detect Microsoft Azure accounts and LUKS2 encryption, as well as new filters for bootable forensic tools.
Microsoft Azure accounts
There are several types of user accounts in Windows that include local accounts, Active Directory, and Microsoft Accounts. Local accounts used to be the most common among home users, now being phased out by Microsoft in favor of online Microsoft Account. For corporate users, domain accounts are the most common type.
Elcomsoft System Recovery supports all of these account types. The tool can be used to reset account passwords, assign administrative privileges to a given account, or change the account type from (e.g. converting a Microsoft Account into a local account). The tool supports the newest type of Windows 11 accounts with passwordless sign-in.
However, there is yet another type of account tied to Microsoft Azure. Microsoft Azure accounts belong to Microsoft Works and School Accounts. They are relatively little known. Microsoft Azure accounts are not listed in the Settings app. Elcomsoft System Recovery 8.30 can now detect the presence of Microsoft Azure accounts on the user’s computer.
LUKS2 encryption
The many features of Elcomsoft System Recovery are targeted to Windows computers. However, the tool supports macOS and Linux systems to a limited extent. For these systems, Elcomsoft System Recovery can detect encrypted disks and extract encryption metadata for subsequent recovery in Elcomsoft Distributed Password Recovery. Previous versions of the product supported a long list of disk encryption standards including TrueCrypt, VeraCrypt, BitLocker, FileVault (HFS+/APFS), PGP Disk, and LUKS.
LUKS is the most common disk encryption system in many Linux distributions. The latest Elcomsoft System Recovery update can not detect disks encrypted with its successor, LUKS2. Compared to the original LUKS, LUKS2 is even more secure, supporting more algorithms and more hash iterations.
We are working on an update to Elcomsoft Distributed Password Recovery that will support the recovery of LUKS2 encrypted drives with optimized performance on modern graphics cards. However, you can extract LUKS2 encryption metadata today.
An update to bootable forensic tools
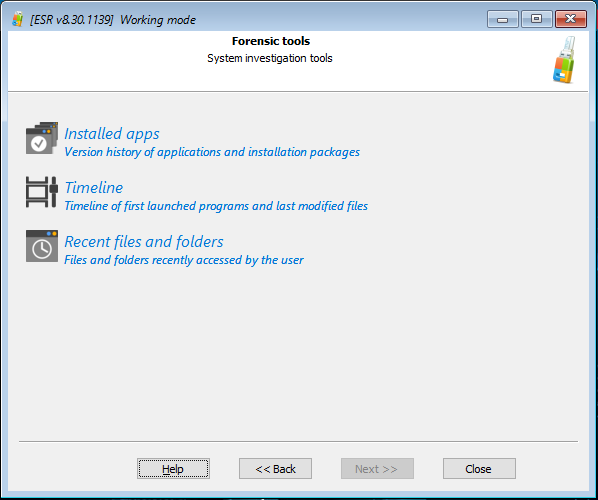
Elcomsoft System Recovery helps forensic experts overcome the challenge of accessing a locked system, delivering a straightforward workflow for investigating computers in the field. A recent update added several bootable forensic tools, which include:
- Timeline: allows reviewing the user’s activities logged by the Windows Timeline. This includes the list of launched apps and past activities laid out in the convenient timeline view.
- Recent files and folders: lists recently accessed files and folders.
- Installed apps: lists applications installed in the system.
Thanks to these features, experts can simply boot a PC from a USB flash drive and quickly review the user’s latest activities. The shortcut saves the time and effort of removing and imaging the hard drive(s), making it possible to make real-time decisions in the field.
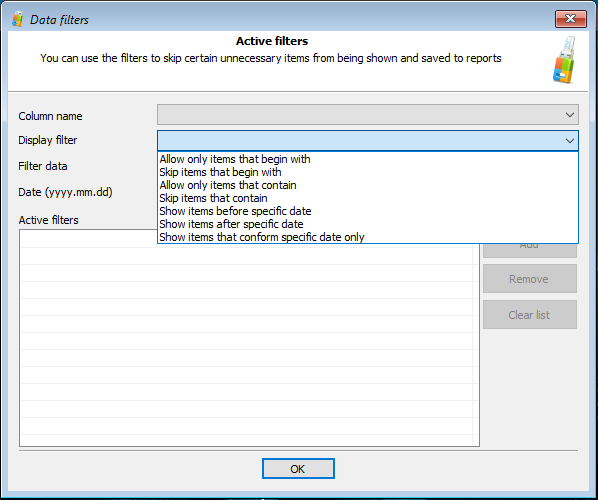
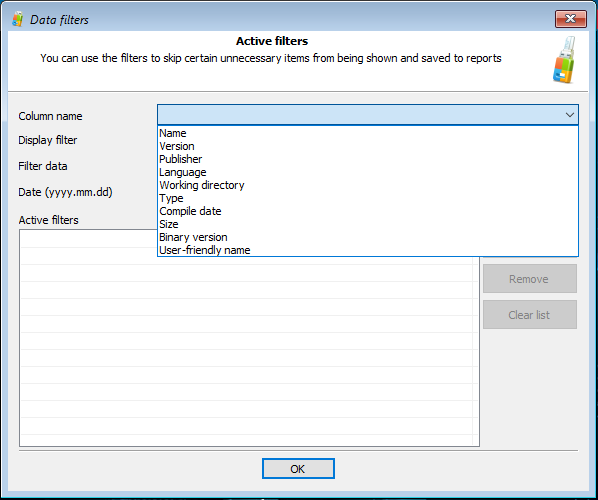
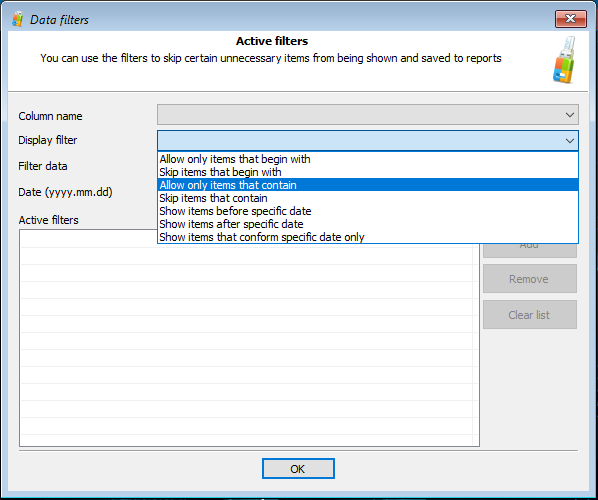
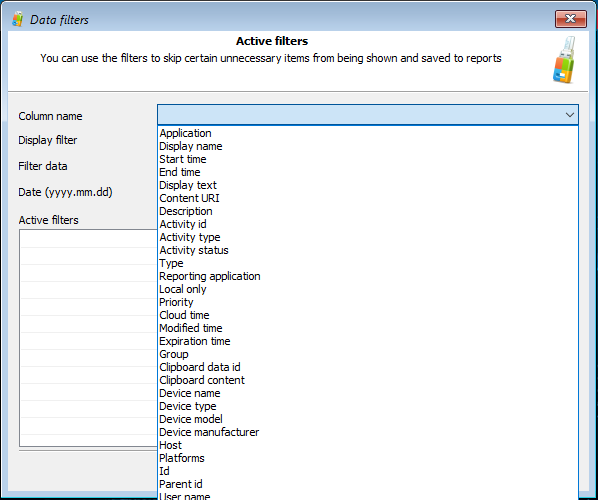
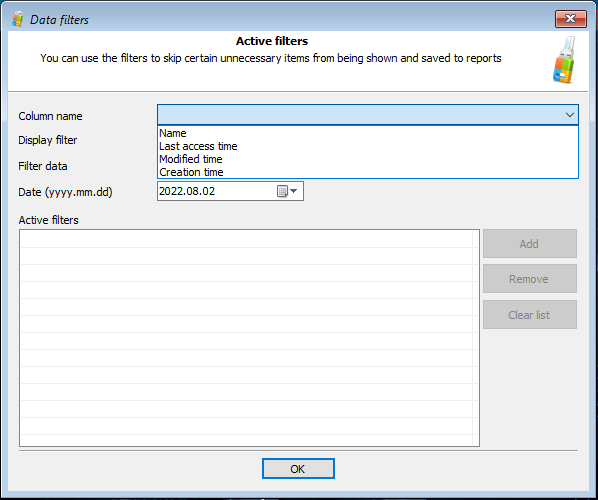
In real life, the amount of data returned by these tools quickly becomes overwhelming. Moreover, a significant chunk of that data might be irrelevant to the investigation. To streamline the analysis, we introduced a powerful filtering system. By using filters, one can quickly configure the tool to only display data that belongs to a certain date and time range, or only include files located in specific directories, or exclude files located in a specific folder (such as C:\Windows\ for system files).
To access the new Forensic Tools section, boot the computer being investigated from a dedicated USB media with Elcomsoft System Recovery 8.30 or newer. If you have not done it already, here’s how to make the bootable USB drive with Elcomsoft System Recovery: A Bootable Flash Drive to Extract Encrypted Volume Keys, Break Full-Disk Encryption.
Once you boot the computer into Elcomsoft System Recovery and accept the license agreement, you will see the program’s main window. Click the “Forensic Tools” shortcut at the bottom of the window. You will see the list of available forensic tools:
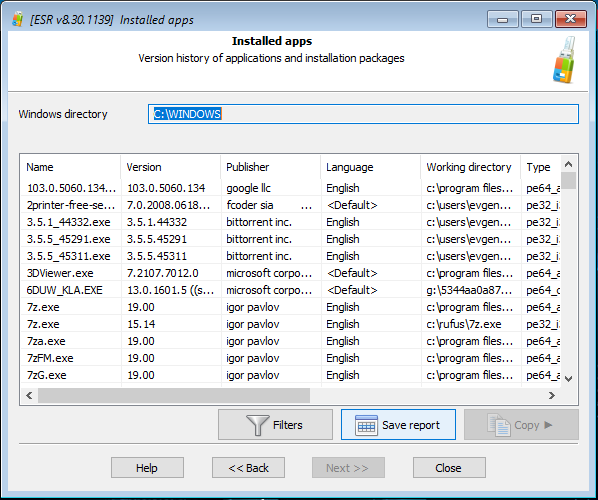
The Installed apps tool displays the list of applications installed in the system being investigated. By default, the tool lists all apps installed on the computer:
You can easily configure the tool to only include certain apps (or exclude certain apps) with newly added filters:
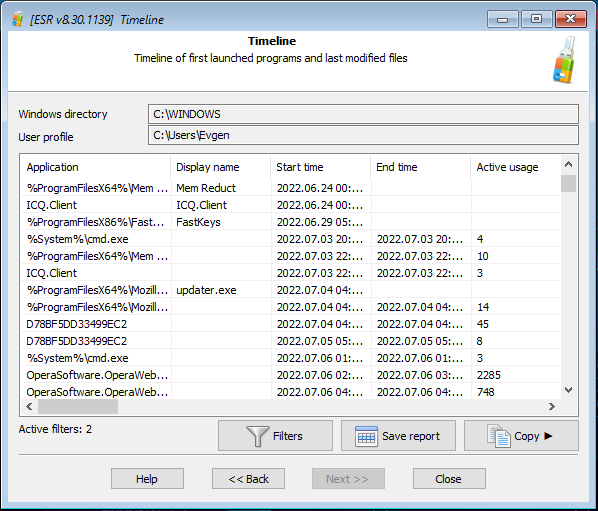
Windows Timeline is a feature that first appeared in the Windows 10 April 2018 Update. The feature enhances Task View, enabling a glance into the past by displaying the user’s historical activities. The Timeline contains timestamped information about the user’s launched applications, searches, documents, and Web browsing history. Along with Windows jumplists, the feature is little known and rarely disabled, giving a valuable insight into the history of system’s usage. By analyzing the Timeline data, experts can access to timestamped information about the app usage and Web page visits.
Timeline data is collected individually per user. When analyzing the timeline, you will have to specify the Windows installation path as well as the path to the user profile. The user’s password is not required. The sheer amount of Timeline data can quickly overwhelm even the most experienced expert:

The newly added filters help restrict the amount of data displayed, allowing experts to concentrate on what’s really important:
The filtered result is much easier to read:
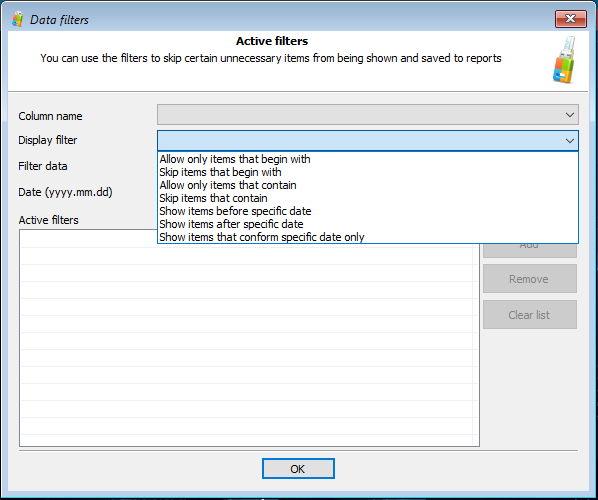
Just like the Timeline, Recent files and folders is a user-specific feature, requiring the path to the user profile. Just like the Timeline, Recent files and folders may contain an overwhelming number of records. The newly added filters help concentrate on files stored under specific paths or exclude irrelevant information:
Conclusion
Originally released as a simple tool for resetting Windows users’ passwords, Elcomsoft System Recovery is quickly evolving into a fully featured bootable forensic toolkit. The new release makes field analysis faster and more straightforward while still producing court admissible evidence with write-blocking disk imaging. Conveniently, using many of the newly added features do not require the user’s or administrator’s password.












