Just before the turn of the year, we’ve made an important update to Elcomsoft iOS Forensic Toolkit, a low-level iOS file system extraction and keychain decryption tool. The update brings checkm8 support to iOS, iPadOS and tvOS 16.2 devices, and enables agent-based low-level extraction of iOS 15.5. We’ve also fixed what’s been long broken: the ability to sideload the extraction agent from Windows PCs, yet the two updates are delivered in different branches. Sounds confusing? We’re here to solve it for you.
checkm8: full file system extraction for iOS, iPadOS and tvOS 16.2
Not long ago we’ve made a big release. iOS Forensic Toolkit 8.0 brought checkm8 support to a plethora of devices. checkm8-based extraction is the cleanest, safest, and most technologically advanced extraction method available for a range of Apple devices with a vulnerable bootloader. Compared to other acquisition methods, our implementation of checkm8 is the only true forensically sound solution that delivers repeatable and verifiable extractions. Compared to logical acquisition, low-level extraction delivers significantly more information. For most system builds, checkm8 extraction can decrypt the entire content of the keychain including encryption keys and authentication tokens. The tool was a complete overhaul, introducing a command-line interface instead of the previously used console menu.
iOS Forensic Toolkit 8.10 is the first major update, now bringing low-level full file system extraction support to Apple devices running iOS, iPadOS and tvOS 16.2. The new build enables forensically sound checkm8 extraction of compatible iPhone, iPad, and Apple TV devices up to and including the iPhone X range, as well as iPad and Apple TV devices built with the corresponding SoC.
A small peculiarity: when loading ramdisk on a device running iOS, iPadOS or tvOS 16.1-16.2, the following prompt will pop up on your computer:
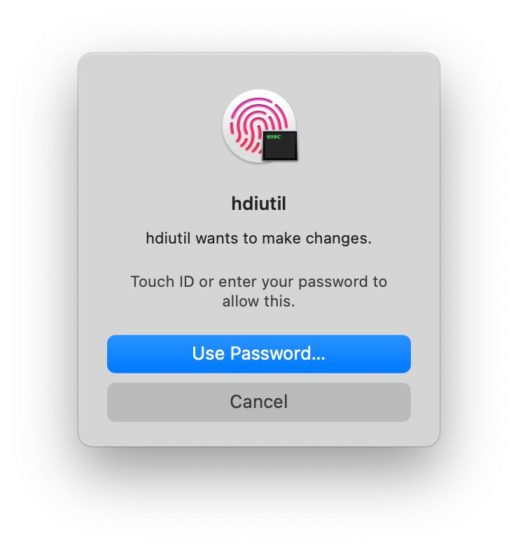
You will need to authenticate with either Touch ID or password to continue.
Note: keychain decryption for iOS, iPadOS and tvOS 16.2 is coming soon.
checkm8 limitations: iOS 16.x on the iPhone 8, 8 Plus, and iPhone X
With the release of iOS 16, Apple made things more difficult for the mobile forensic specialists. We’ve already talked about it in iOS 16: SEP Hardening, New Security Measures and Their Forensic Implications. That final build of iOS 16 introduced a brand-new SEP (Secure Enclave Processor) hardening patch that effectively prevents access to user data if a screen lock passcode was ever used on the device, thus ruling out the possibility to use the bootloader exploit for accessing data on pretty much all A11 iPhones in circulation. Older iPhones did not receive the update, but they didn’t get iOS 16 in the first place.
Let’s reiterate: the extraction will fail if a passcode was ever used on the iPhone 8, 8 Plus or iPhone X after the initial setup. The practical value of our solution for these devices is low as the overwhelming majority of Apple iPhones are (or at least were) protected with a passcode. You can still use it on other devices (e.g. iPads), as well as for R&D purposes.
checkm8 extraction and iPadOS 16: working good (with caveats)
We had to wait for the first official release of iOS 16 for iPads, which was iPadOS 16.1, to figure out if the same hardening patch was applied to iPads. It turned out this was not the case, and you can still use checkm8 extraction on iPad devices running iOS 16.x regardless of the generation of SoC they are built on.
The ability to use checkm8 extraction is limited on the iPhone 8, 8 Plus, and iPhone X devices. On these devices, the extraction only works if no screen lock passcode was ever used on the device since the initial setup. This limitation does not apply to any iPad or Apple TV models, yet you may have to remove the screen lock passcode when acquiring an iPadOS 16 device.
What about the caveats? It’s also about the passcode. If there is no passcode on the iPad being extracted (or if the passcode has been removed prior to the extraction), the extraction is guaranteed to work. If the passcode is enabled (and you know it), you may need an additional SEP unlock step (the loadnfcd command), but even then the extraction may fail. If this happens after you tried a few times, there’s no other choice but booting the device and removing the passcode in iPadOS Settings. Deleting the passcode has serious forensic implications, so don’t do it lightly; however, this can be the only way to do checkm8 extraction on iPads running iOS 16.x.
checkm8 on Apple TVs: generally fine
We tested checkm8 on the AppleTV 4K, and the extraction is stable. We’re still working on the newer AppleTV HDR running tvOS 16.x for which the extraction is not currently stable.
Extraction agent: experimental support of iOS 15.5
The new build of iOS Forensic Toolkit adds experimental agent-based low-level extraction support for iOS/iPadOS 15.5, but only for A12 and newer devices. For A11 and older platforms (the iPhone 8/8Plus and iPhone X), the agent still only supports iOS builds up to 15.3.1, but that does not really matter as a much cleaner checkm8 extraction process is available for these older platforms. Note that iOS/iPadOS 15.5 support is still experimental as we have only tested the exploit on a handful of devices.
We discovered that the exploit works most reliably after approximately one minute (or longer) after the device is rebooted. The device must be switched into airplane mode for the exploit to work. If the device was kept powered on for a long period of time, we recommend rebooting and unlocking the device, and waiting for at least one minute before applying the exploit. Mind the airplane mode!
If you encounter the “All exploits failed. Please reboot the device and try again” error, reboot the device and make sure it’s paired to the computer. Reconfirm the airplane mode, wait for at least one minute and repeat the attempt. Another error you may encounter is a spontaneous reboot.
The full list of supported devices includes the following models:
- iPhone Xr, Xs
- iPhone 11, iPhone SE (2nd gen)
- iPhone 12
- iPhone 13, iPhone SE (3rd gen)
- iPad 8, 9, 10
- iPad Mini 5, 6
- iPad Air 3, 4, 5
- iPad Pro 3, 4, 5
Note: you may need 4 to 5 attempts to apply the exploit on M1-based iPads.
Some of our competitors have also introduced their versions of iOS extraction agents. We discovered that those competing solutions rely exclusively on public exploits, which is sub-optimal to say the least. Our solution uses all known vulnerabilities; we deeply rework and improve the exploits, and test them on a large fleet of devices to ensure maximum stability. The extra work is essential as the kernel exploit covers about a fifth of what needs to be done to reliably run the extraction agent. The file system extraction requires several stages including privilege escalation, sandbox escape, Pointer Authentication bypass, and so on, while kernel exploits only cover the very first step.
What’s up with the Windows edition?
iOS Forensic Toolkit 8 is only available for Mac computers for the time being as we need more time to finalize the checkm8 support on Windows and Linux platforms. Our Windows customers are served with the EIFT 7.x branch, which is all but abandoned and is still in active development. To use low-level extraction in iOS Forensic Toolkit 7, you’ll need to use the extraction agent, which in turn is an app that must be sideloaded onto the iOS/iPadOS device running a compatible (vulnerable) version of iOS.
Agent-based extraction is second best to checkm8. By using the extraction agent, one can image the complete file system of the device. For most devices, the tool can also decrypt the keychain, accessing all keychain records regardless of their protection class. Unlike checkm8, agent-based extraction cannot be classified as completely forensically sound, yet it comes close by leaving almost no traces on the device once the extraction is finished.
The extraction agent is back
To install the extraction agent onto an iOS/iPadOS device, you’ll need to sideload it first. The term describes the process of pushing an app to a mobile device directly from the computer, bypassing the App Store and standard installation mechanisms. Apple is not keen of sideloading, and tries to limit the users’ ability to sideload apps onto their devices. A few years back anyone could install an app onto their iPhone using Cydia Impactor, a free sideloading tool that no longer works. In the meanwhile, we developed an alternative sideloading process that was used in iOS Forensic Toolkit to install the extraction agent. Some time ago Apple further restricted sideloading, which continued to work if you used a Mac but failed if you tried to install the extraction agent from a Windows PC.
We’ve been working hard to bypass this limitation. Finally, iOS Forensic Toolkit 7.70 brings back the extraction agent to Windows PCs: you can now sideload the agent to an iOS/iPadOS device by using a a Windows PC. The new signing mechanism now employs regular Apple ID passwords instead of the previously used one-time passwords, but you still need an Apple ID enrolled in the Apple’s Developer Program to sideload and sign the extraction agent.
Please refer to the following chart for details on the types of extraction supported on the different platforms:

Viewing the data
Viewing the extracted file system image is possible with Elcomsoft Phone Viewer, which was recently updated to support iOS 16.x file system images. The updated iOS release introduced multiple changes in the data formats, which required updating the viewing tool to conform to these changes. Alternatively, you may use a third-party forensic tool compatible with iOS 16 file system images.






