Big news is coming – and this time, it’s from the living room. Our team has successfully extracted a complete file system image from an Apple TV 4K running tvOS 26. This marks the first-ever low-level extraction of Apple’s 26th-generation operating systems, including iOS 26, iPadOS 26, and tvOS 26. No one – not even the major forensic players! – has been able to achieve this before.
The full announcement, complete with technical details and tool availability in iOS Forensic Toolkit, is coming soon.
Apple TV specifics
The first-generation Apple TV 4K (model A1842, released in 2017) is based on the A10X SoC – the same chip used in the iPad Pro 2. (Fun fact: while the iPad Pro 2 never received iPadOS 18, the Apple TV 4K can run tvOS 26.)
This is the first Apple TV model without a USB-C port. However, it features a hidden Lightning port under the RJ-45 connector. To access it, you’ll need the Foxlink X892 GoldenEye adapter, available from many stores for about $25.
Entering DFU mode on this model isn’t straightforward – it can no longer be done via the Apple TV remote (as on older models). The “hacker’s way” involves disassembling the device and shorting specific pins, but there’s a much easier and safer method we’ve written about before: use a DCSD cable. We recommend the Colobus cable (in SWD mode) instead, which is more reliable, offers additional features, and provides a USB-C connection to the host. This means the usual USB-A to Lightning cable (normally required for the checkm8 exploit) can be replaced with a regular USB-C cable.
To enter DFU mode automatically, connect the Colobus cable to the Apple TV first, then connect Colobus to the PC, and finally connect the Apple TV to power.

How it works
Once the Apple TV is in DFU mode, start with the boot command as usual:
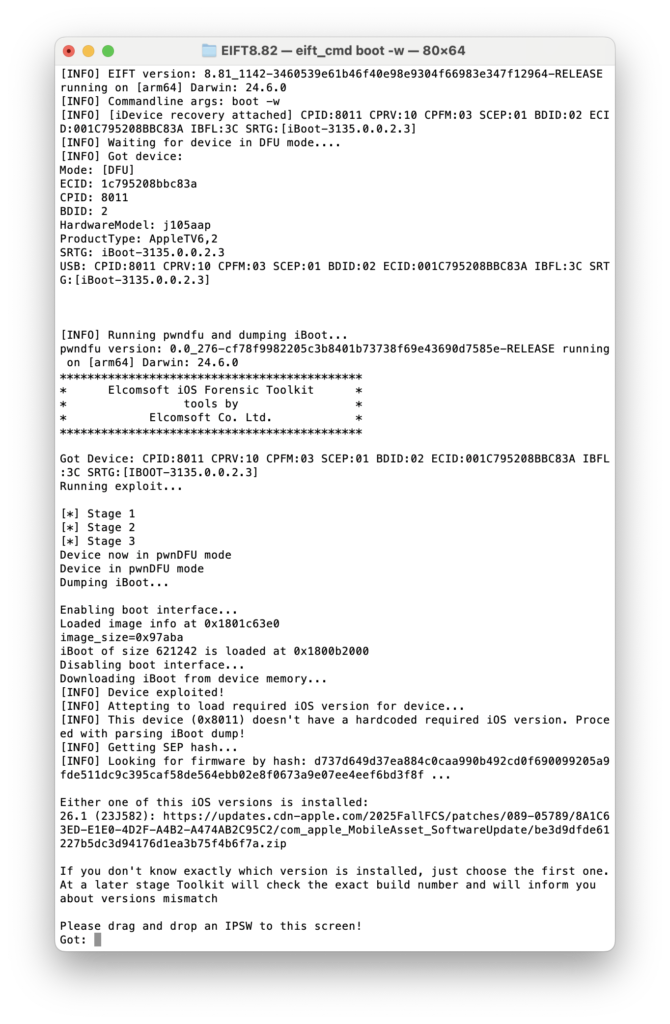
As you can see, the tvOS version is properly recognized (26.1 here), and the correct firmware link is provided. Note that this is not the full IPSW but an OTA update. Then, proceed with unlockdata:
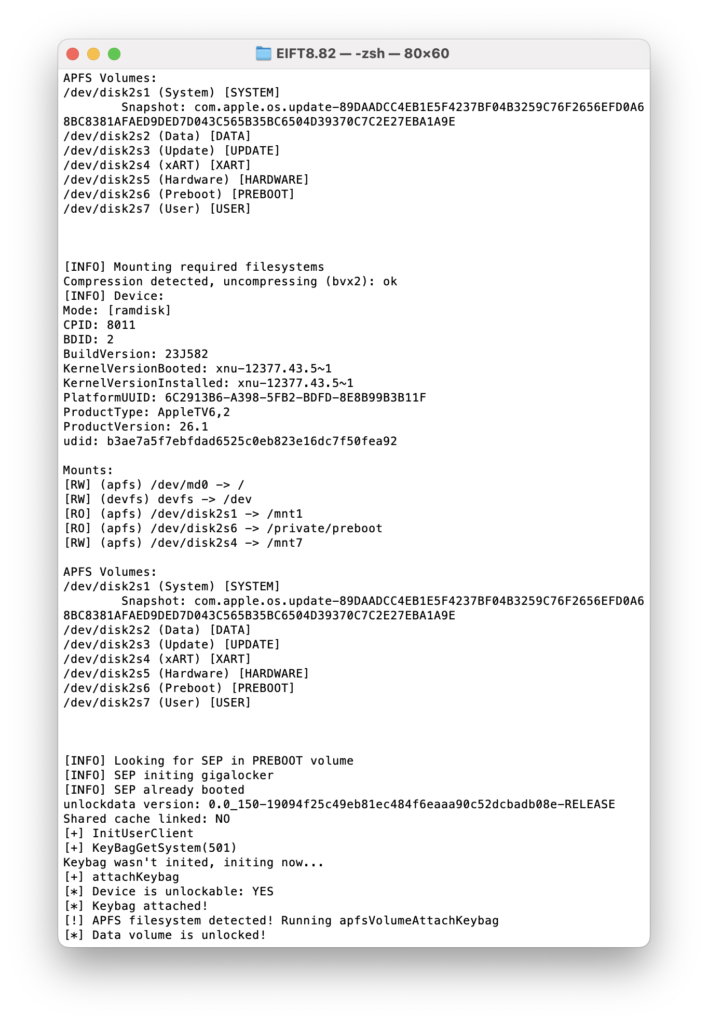
Next, the keychain:
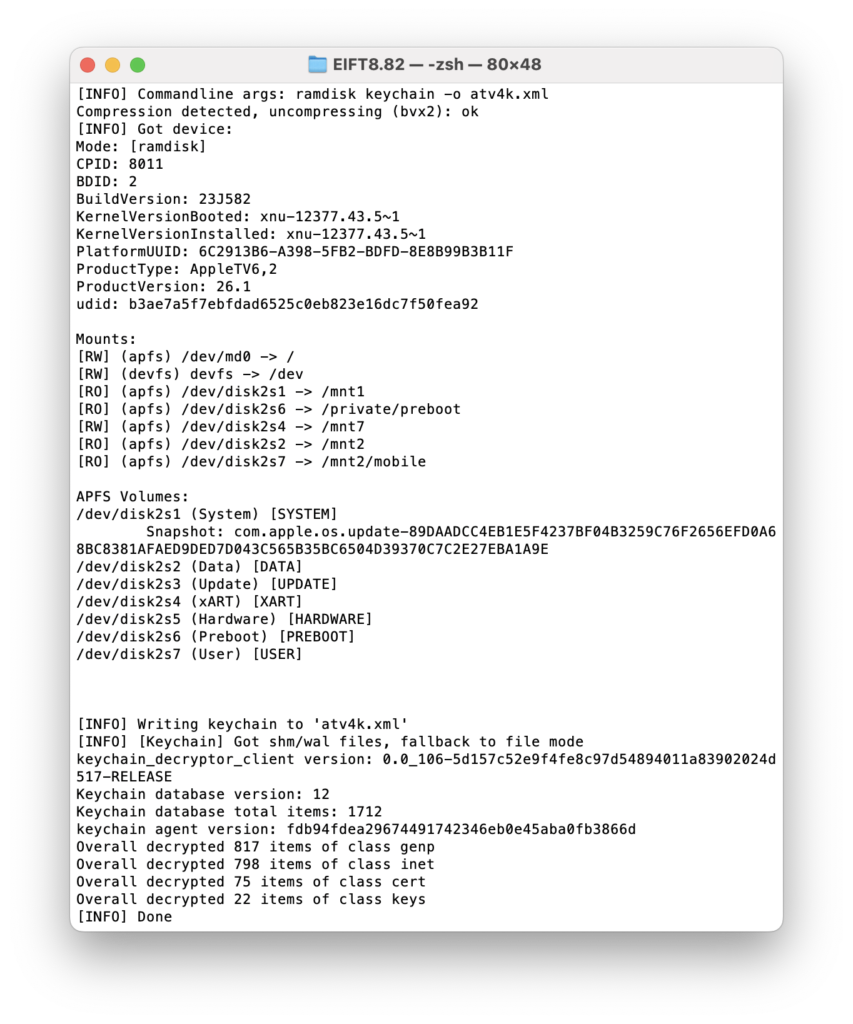
And finally, the full file system; the acquisition speed is over 40 MB/s:
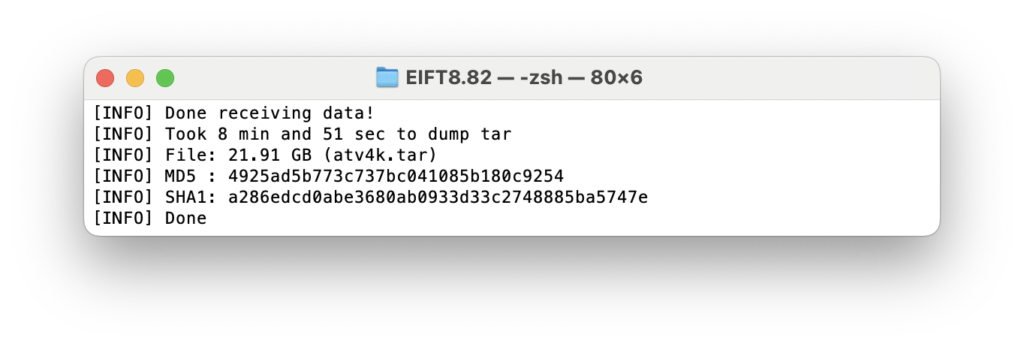
Now you have everything you need for further analysis.
Why this matters
The importance of IoT forensics is hard to overestimate. Apple TV is a part of Apple ecosystem, and once logged into Apple Account, it syncs lots of data with the iCloud; unfortunately, not as much as iPhone and iPad do, but still the photos and videos are usually there (although it depends on device settings). Just note, first, that media files are not being synced automatically (until they browse them at TV); and second, not the originals are stored at Apple TV but smaller size. The good news are that metadata is sync is full, so Apple TV contains info on all the media files stored in the iCloud, including geolocation data, and that allows to build the timeline.
Next, the keychain. We’d be happy to see the complete keychain synced with Apple TV, but only Wi-Fi passwords are present. This is a feature, not a bug, since Apple TV cannot be protected with a passcode. Well, some tokens (and probably passkeys) appear to be there too, but this still requires further exploration. And, while the contact list is not there, there is a list of blocked numbers that is still available on the box. Also, one may find it useful to research the various 3rd party app data.
Anything else? Well, if Apple TV is configured as a home hub (see how), then you’re going to get more – at least information about other devices, as well as a much better timeline.
But that’s not all. tvOS 26 isn’t just a streaming box firmware; it uses the same or similar data structures as iOS. Gaining full file system access provides unprecedented insight into Apple’s evolving forensic landscape. This breakthrough will allow experts and vendors to analyze new data formats, authentication mechanisms, and file system structures, ensuring their tools remain up to date as Apple continues to strengthen its ecosystem.
Analysis (sort of)
We tried processing our test extraction (22 GB) with a couple of popular forensic tools, and honestly, were a bit disappointed – not with the content, but with the depth of analysis these tools provide.
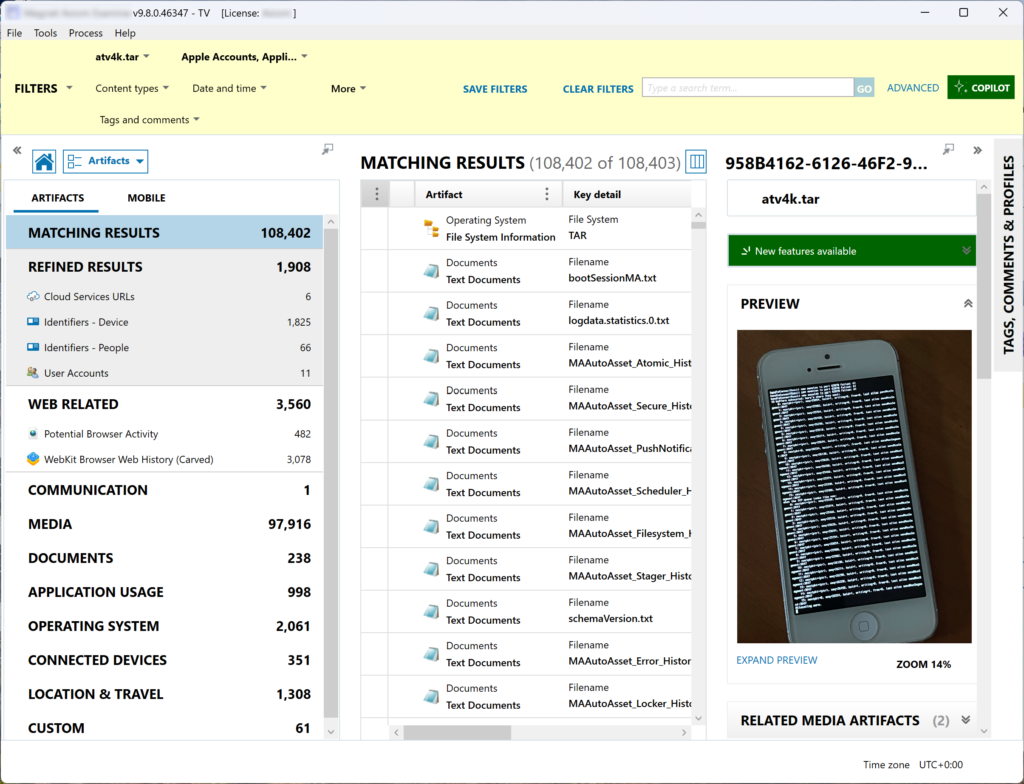
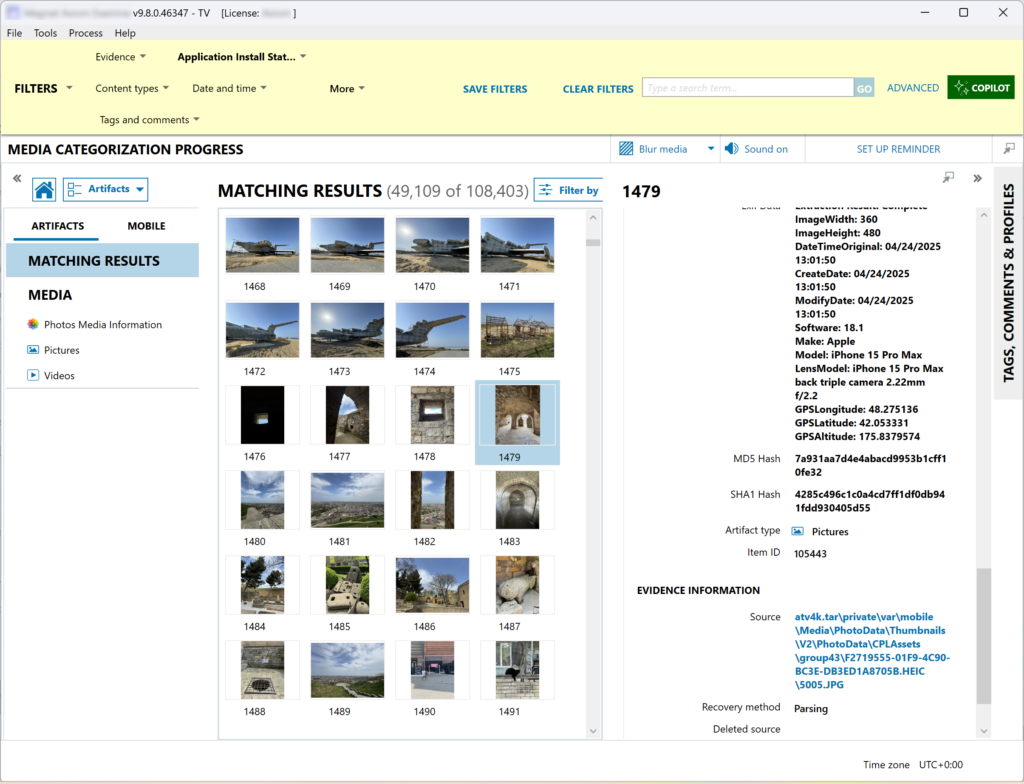
Over a hundred thousand artefacts, full EXIF data – looks good, yet a lot of manual analysis is still required.
The other tool has a more convenient UI and provided more information about the extraction and the device itself:
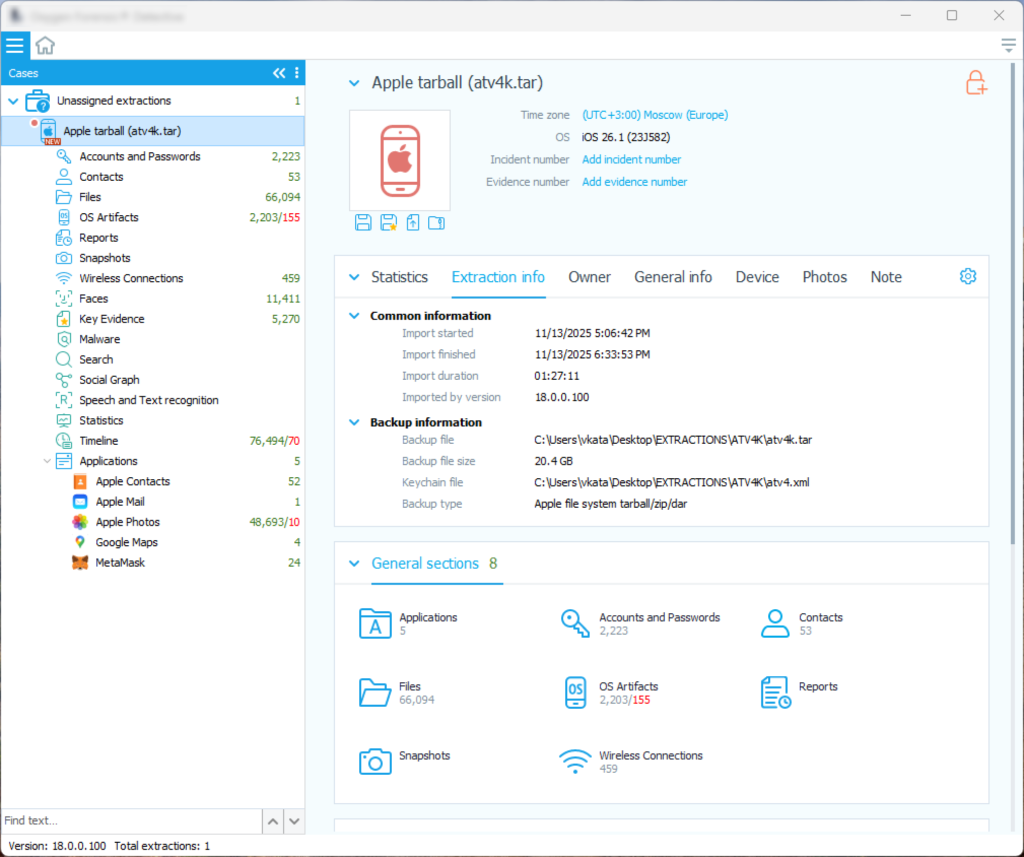
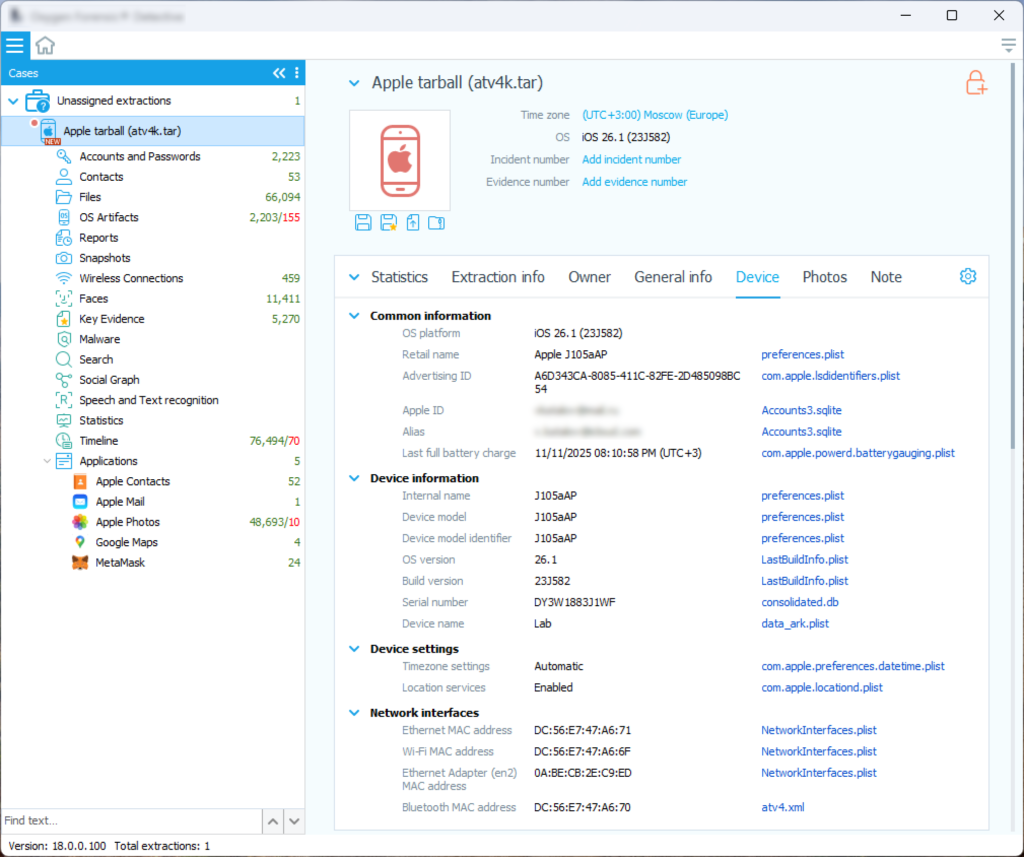
And it generated a nice timeline:
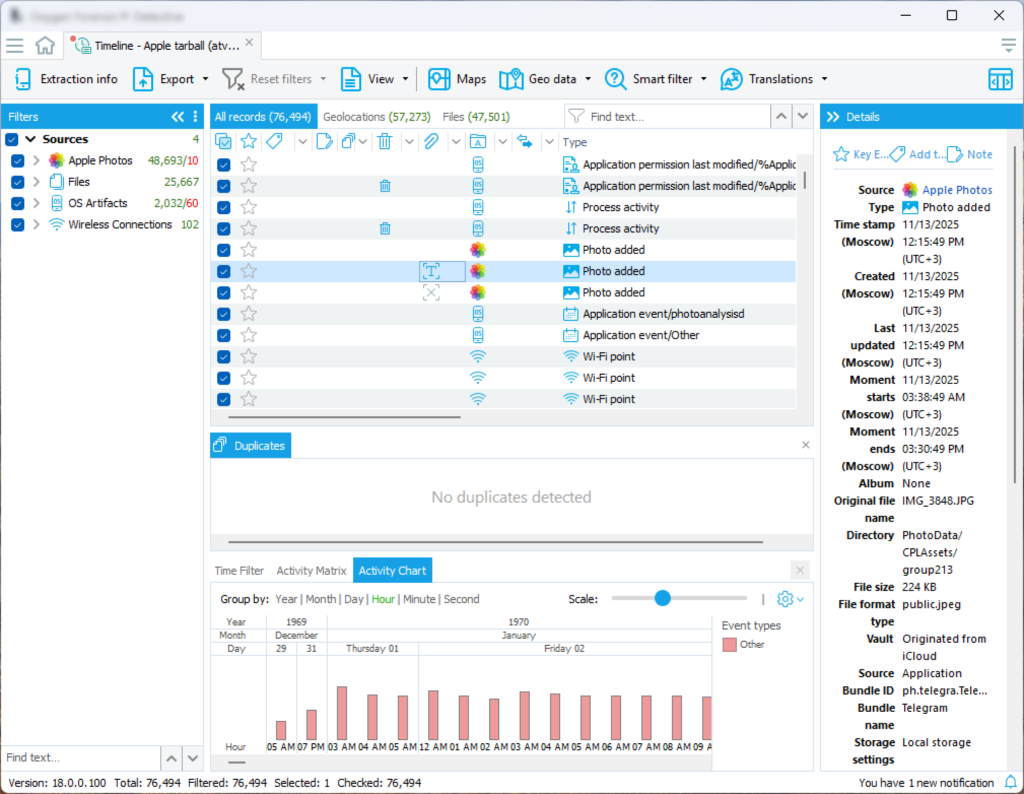
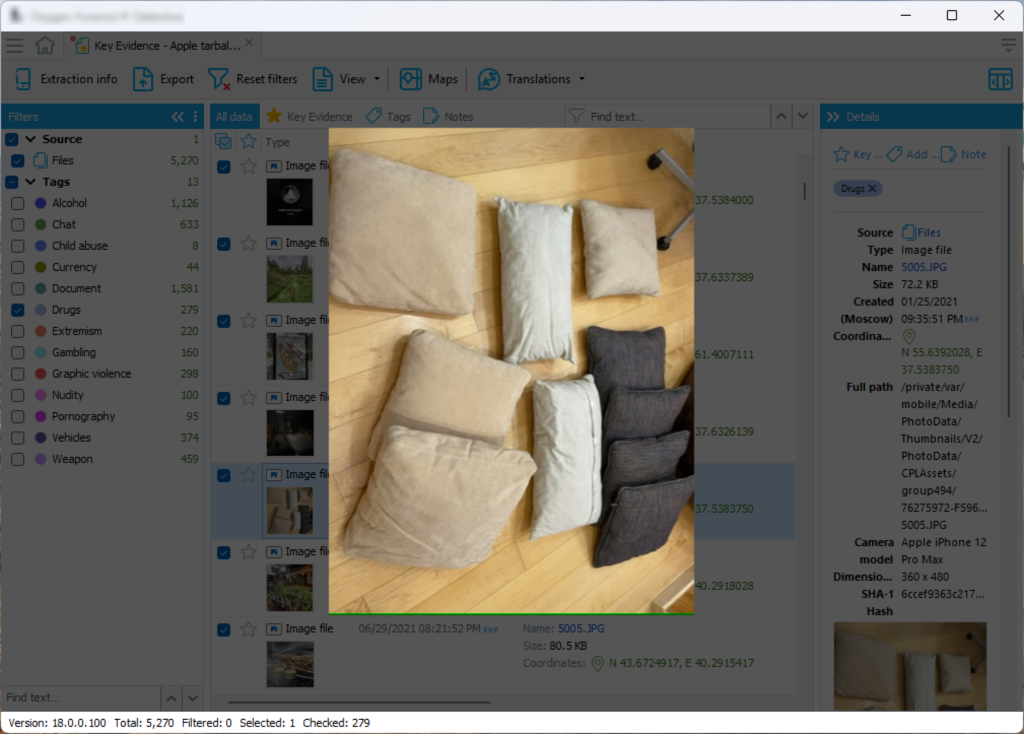
But when it comes to analysis, the results are… unexpected, to say the least. For example, here is “drugs” (tip: these are pillows):
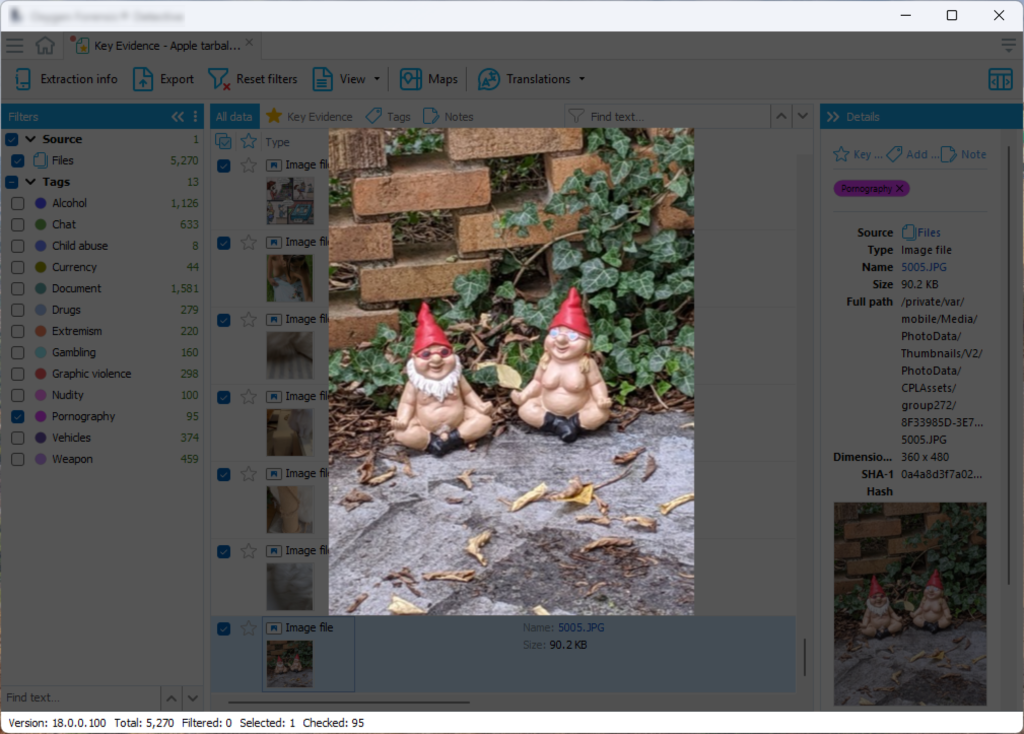
Some “pornography” (garden gnomes, in fact):
And finally, “child abuse” (spot the cat):
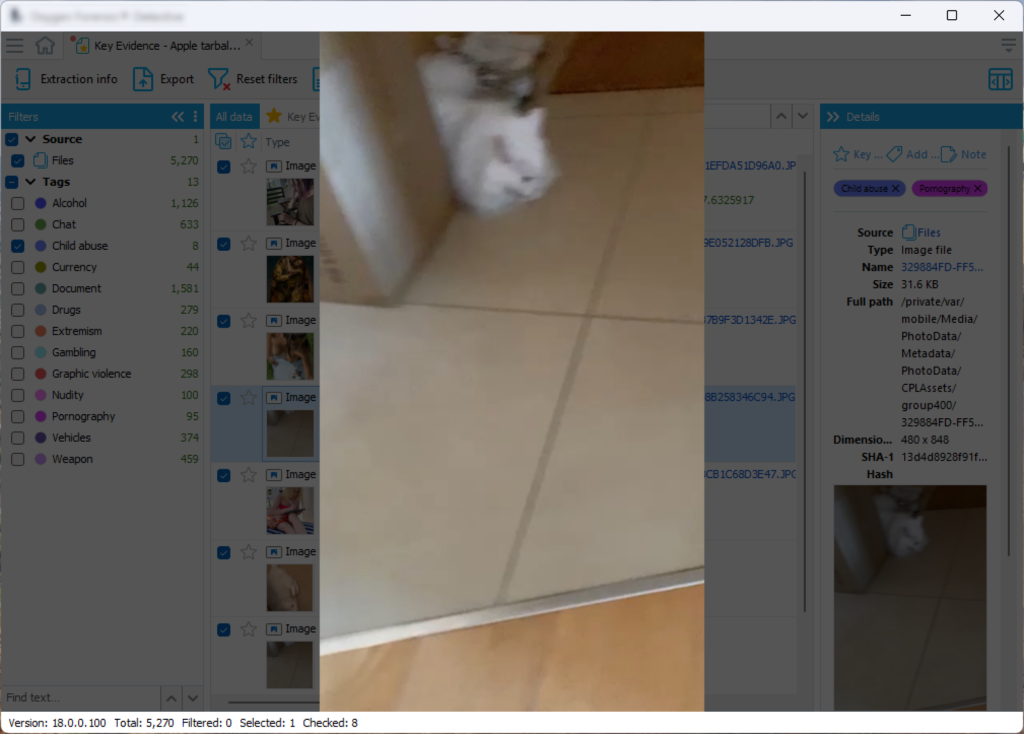
I honestly have absolutely no idea how this kind of “image classification” can be useful in an investigation.
Conclusion
We’ve done our part: we extracted everything that could possibly be retrieved from the device. But the real work begins with the expert. To uncover meaningful evidence, a forensic analyst must have the skill and experience to interpret the data correctly. Good software is usually enough for the extraction itself, but when it comes to analysis, no tool can replace expertise. Relying solely on automated classifications or predefined reports is a shortcut to incomplete or misleading results. In the end, it’s the specialist, not the software, who turns raw data into actionable insight.















