In this article we’ll discuss the differences between implementations of two-factor authentication in popular mobile platforms. We’ll research how two-factor authentication is implemented in Android, iOS and Windows 10 Mobile, and discuss usability and security implications of each implementation.
What Is Two-Factor Authentication?
Two-factor authentication is an additional security layer protecting access to user accounts in addition to their username and password. In two-factor authentication an extra verification step is required that is separate from the password. Ideally, two-factor authentication schemes would be based on verifying “something you have” in addition to “something you know”. In practical terms this is not always convenient for the end user, so very few straightforward implementations exist (mostly in the banking industry in Europe).
Using the extra verification step based on a piece of information that only the user knows or has access to makes it significantly harder for potential intruders to break in.
Historically, banks were the first to use two-factor authentication. A low-tech solution of pre-printed, single-use Transaction Authentication Numbers (TAN) delivered to the user’s registered home address were used on top of the login and password to authorize bank transfers. Since then the banking technology moved on, utilizing a wide range of authentication options (http://www.wikibanking.net/onlinebanking/verfahren/phototan/). For example, an authentication scheme called photoTAN makes use of complex 3D codes and interactive two-way validation. In a typical photoTAN implementation, the bank generates a unique 3D code. The code must be scanned by an authorized device such as smartphone or token which, again, had to be initialized with an interactive two-way process. The device generates a verification code that must be entered into the confirmation box.

While this authentication scheme provides exemplary security with full control over authorized devices, the authentication process is just too slow and cumbersome for an average smartphone user performing day to day activities. Other authentication schemes employ proprietary devices and chip technologies, making them even less attractive for mass use.
Developers of major mobile operating systems, Apple, Google and Microsoft, each developed their very own implementations of two-factor authentication in an attempt to balance convenience and security. The three companies arrived to very different results. So let’s have a look at what we have today for two-factor authentication on the three popular mobile platforms.
Apple iOS
Apple has had some form of two-factor authentication since 2013. Designed to protect users’ Apple ID from being exploited in terms of direct financial loss (unauthorized purchases, password change etc.), the then-current “Two-Step Verification” scheme offered a very limited protection scope. Apple was working on a more universal solution for the upcoming version of iOS.
In August 2014, news outlets were struck with a story of 500 private pictures of various celebrities leaked via a breach of Apple’s iCloud services (https://en.wikipedia.org/wiki/ICloud_leaks_of_celebrity_photos). The photos were extracted from iCloud storage. The hackers performed targeted attack on user names, passwords and security questions using a combination of social engineering and brute-force attacks.
This was a major scandal, and Apple reacted. Ahead of iOS 9 release, Apple expanded Two-Step Verification to protect iCloud sign-ins, which included iOS backups and photos.
Apple’s First Attempt: Two-Step Verification
Two-step verification is a half-baked solution and a rushed answer to a problem long overdue. This authentication method was slapped on top of Apple’s existing mobile ecosystem and works completely on the server side. Two-step verification uses verification codes pushed to trusted devices. Since Find My Phone is used to deliver verification codes to a selected trusted device, the code would show up on the device even with its screen locked. This was but one weakness of this implementation.
Alternatively, two-step verification codes can be delivered via text messages or phone calls to a one of the registered phone numbers. Users could generate app-specific passwords from Apple ID account page https://appleid.apple.com/. Up to 25 app-specific passwords could be active at any given time.
Account recovery would be performed with a printable 14-character Recovery Key. Should the user lose their Recovery Key, they could as well lose access to their Apple account.
- Verification code pushed (via Find My Phone) to a selected trusted device
– Shows up even on locked devices!
- Text message or phone call to a registered number
- Application-specific passwords generated from Apple ID account page https://appleid.apple.com/
– Up to 25 active app-specific passwords at any given time
– Can be revoked individually
- Account recovery: 14-character printable Recovery Key
Two-step verification was never intended, and could not be, a fully featured multiple-factor authentication solution. Since support for two-factor authentication was not baked into the OS itself, it could only protect users in counted circumstances:
- Sign in to Apple ID account page
- Sign in to iCloud on a new device or at iCloud.com
- Sign in to iMessage, Game Center, or FaceTime
- Make an iTunes, iBooks, or App Store purchase from a new device
- Get Apple ID related support from Apple
Enrolling into two-step verification is possible from an Apple device or through a Web browser by signing in to My Apple ID. Users are required to enroll at least one trusted phone number, which represents yet another potential vulnerability of this scheme.
Two-Step Verification Security
How secure is Apple’s two-step verification? With no OS-level support, it can be characterized as “better than nothing”. With Find My Phone used for delivering verification codes, a hacker could easily request and receive a code on a stolen iPhone. Text and phone call delivery open yet another vector of attack, allowing intruders request a duplicate/replacement SIM card from the victim’s mobile operator using a fake power of attorney.
This last method is commonly used in Russia to target victims’ online banking apps. The banks have responded by limiting verification access to SIM card’s ICCID identifier as opposed to relying solely on the phone number. However, this is not the case with Apple, so a cloned/replacement SIM card can be successfully used to receive verification codes.
Two-step verification is still available today alongside with Apple’s second implementation called “Two-Factor Authentication” (albeit only one system can be active for a given Apple ID). As such, we’ll view it in modern rather than legacy context. In today’s day and age, Apple’s Two-Step Verification is an afterthought at best. Its limited protection scope, obvious security shortcomings and difficult recovery procedure should the user lose access to their secondary authentication factor leave much to be desired.
- Initially, 2SV did not protect iOS backups and iCloud data; protection added after Celebgate
- Also, 2SV did not prevent restoring iCloud backups onto new devices (now it does)
- Delivery via test messages of phone calls is insecure
- SMS/phone call delivery can be selected and no prompt will appear on trusted devices
- Find My Phone push is even less secure than SMS
- Verification code appears on the lock screen
- Can be accessed without entering the passcode
- Was considered the weakest implementation of all the major tech firms http://www.theregister.co.uk/2013/05/31/apple_2fa_security_weak/
Apple’s Second Attempt: Two-Factor Authentication
While two-step verification worked (and continues to work) on top of the operating system, Apple continued their work on a proper implementation. The resulting new authentication method dubbed “Two-Factor Authentication” was finally released with iOS 9.
This new authentication method is fully integrated into the mobile OS, and protects all attempts to sign in with the user’s Apple ID on a new device.
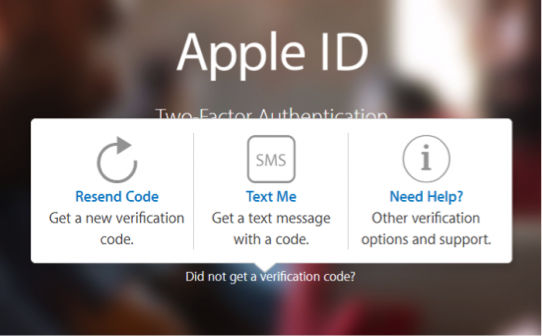
Apple’s Two-Factor Authentication, while designed to serve the same purpose, works in a distinctly different way. Interactive push notifications that must be confirmed before one can access the 6-digit verification code are now delivered by default to all trusted devices. It is no longer possible to select “text message/phone call” to quietly receive an SMS with a verification code; all trusted devices will receive a 2FA push prompt immediately upon sign-in attempt.
The following list summarizes verification code delivery options with Apple two-factor authentication:
- A notification is instantly pushed to all trusted device
- Interactive prompt
- Must unlock device to respond to prompt and access a 6-digit code
- Must enter the received 6-digit code to verify sign-in
- Each trusted device initialized with unique seed; different verification codes pushed to different devices
- Only iOS (or macOS) devices can be trusted
- 6-digit code generated from device settings (can be used offline)
- Each device uses unique seed, generated codes are different across devices (this is not a given on other platforms)
- Text message or phone call to a registered number
- An attempt to deliver push notifications to trusted devices is made beforehand
- Accessible via “Did not get a verification code?” prompt
- App-specific passwords
Interestingly, there are two types of app-specific passwords for those apps that don’t support Two-Factor Authentication. The first type can be generated via the user’s Apple Account and looks like this: veur-crlz-wksx-yege. These passwords can only be used for limited access to certain types of information (e.g. iCloud email), and cannot be used to download iCloud backups.
The second type of app-specific passwords is more interesting. It can be produced by appending a 6-digit verification code (received or generated via the usual means), and can be used to access all types of data. For example, such passwords can be used to download iOS backups from iCloud, or to sign to Apple ID/App Store in on an iPhone running iOS 8 (which does not support Two-Factor Authentication yet).
Apple Two-Factor Authentication and Time-based One-time Password Algorithm
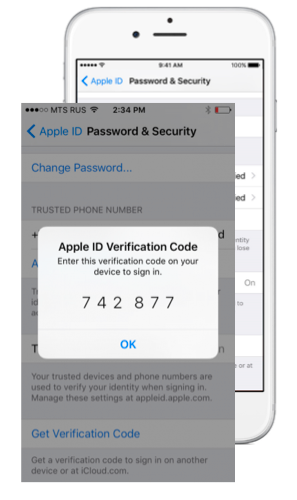 Starting with iOS 9, Apple added the ability to generate verification codes offline. The actual iOS device (iPhone, iPad or iPod Touch) is used as a trusted device in terms of the Time-based One-time Password Algorithm (TOTP) algorithm.
Starting with iOS 9, Apple added the ability to generate verification codes offline. The actual iOS device (iPhone, iPad or iPod Touch) is used as a trusted device in terms of the Time-based One-time Password Algorithm (TOTP) algorithm.
Unlike other platforms, Apple does not allow for manual initialization of trusted devices by scanning QR codes or entering a secret. Instead, each device receives a unique seed directly from Apple. This achieves two goals. First, each device receives a unique seed that can be revoked at any time without affecting other devices’ trust status (this is not the case with other platforms). Second, by making the seed inaccessible to the end user, Apple effectively keeps everything authentication-related within their closed ecosystem. Under these terms, you can only initialize an Apple device as a trusted device. You cannot have an Authenticator app on an Android smartphone or Windows 10 Mobile device.
TOTP summary:
- TOTP: offline, time-dependent code generated from the Settings of a trusted device
- Each trusted device initialized with unique seed
- Trusted devices can be individually revoked
- All devices generate different TOTP codes
SIM-based Authentication
In order to enable two-factor authentication, Apple requires the user to verify at least one phone number. This opens up a potential vector of attack.
- Intruder has the ability to use SMS or phone call to receive codes
- One can pull a SIM card and use in dumb phone to receive verification code
- Criminals can clone or order a new SIM card and use it to receive codes
- This is a massive problem in Russia
- Thieves use fake IDs, fake power of attorney
- Thieves gaining access to victim’s online banking
There is some improvement in this department compared to Apple’s old Two-Step Verification. When Two-Factor Authentication is active, any attempt to access the user’s Apple ID immediately pushes a 2FA prompt to all trusted devices before the intruder can request a code delivered by SMS or phone call.
Apple Two-Factor Authentication Security
This new authentication scheme is immensely better compared to the old Two-Step Verification. It’s both more secure and more convenient, allowing to generate offline authentication codes on trusted devices and prompting users on all of their devices if someone attempts to sign in to their account.
Attackers can still bypass some of these security measures. For example, if they sign in to victim’s account during the night (using a cloned/replaced SIM card, for example), the chance that the victim will be able to react to sign-in prompts is minimal.
Account Recovery
A very common scenario for Apple users is losing their only iPhone while traveling. In such situations, a SIM card with a trusted phone number is also missing and not always easily obtainable. With Apple’s excellent backup system, recovering from such an uncomfortable situation could be as easy as visiting a nearby Apple Store for a new iPhone, entering iCloud credentials and waiting for the phone to restore from the last backup.
Two-factor authentication becomes a real roadblock. If Two-Step Verification was enabled, users were given an option to print a long Recovery Code. With this Recovery Code, they could bypass the secondary verification step. If no Recovery Code is available, there is no straightforward way to regain control over Apple ID. (Calling Apple and having a saved credit card may or may not help).
With Two-Factor Authentication, Apple introduced a formal way to reinstate account access (https://support.apple.com/en-ie/HT204921). Users are advised to go to iforgot.apple.com and follow the prompts. Apple may verify additional information such as saved credit card numbers. Even though the process is automated, recovery may take a very long time.
Apple: References
More information about two-step verification and two-factor authentication is available from the following sources:
In addition, you may find the following reading both useful and interesting:
https://www.grahamcluley.com/factor-authentication-2fa-versus-step-verification-2sv/
http://lifehacker.com/the-difference-between-two-factor-and-two-step-authenti-1787159870
https://paul.reviews/the-difference-between-two-factor-and-two-step-authentication/
https://sixcolors.com/post/2016/07/doing-the-two-step-switching-to-apples-two-factor-authentication/





