Beginning with Windows 8.1 and Windows Phone 8.1, Microsoft started unifying its mobile and desktop operating systems. No wonder the two versions of Microsoft’s latest OS, Windows 10, share the same approach to two-factor authentication.
Microsoft employs a somewhat unique approach to two-factor authentication. Even if the user does not want to use two-factor authentication and does not set up any secondary authentication methods, in some circumstances Microsoft would still prompt to confirm account login. Just like Google, the company would verify unusual sign-in activities occurring from a new device in another country. However, it’s not just that. Microsoft would also try to verify Microsoft Account activities once the user attempts to restore a new phone (Windows Phone 8.1 or Windows 10 Mobile) from OneDrive backup. Interestingly, Microsoft would do exactly the same verification if one sets up an account on a new PC (desktop, laptop or tablet) and attempts to restore from OneDrive backup.
If no two-factor authentication is configured but the user has a trusted phone number and the device being set up is a new phone, Microsoft will attempt to send a text message to that phone. Interestingly, the SMS will be automatically processed by the setup tool; no user interaction would be required when setting up that phone.
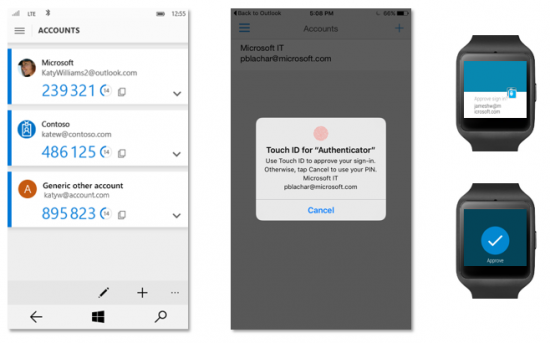
What’s so unique about this setup is the ability for the user to configure all possible two-factor authentication methods (SMS, push, TOTP etc.) without actually ENABLING two-factor authentication. For example, one can set up offline authentication with Authenticator app (made by Google, Microsoft, or one of the many third parties) as well as prompt-based authentication with Microsoft Authenticator (available for Google, iOS and both versions of Windows 10). The second authentication factor will NOT be normally prompted. However, if Microsoft detects unusual sign-in activity, or if the user attempts performing a highly sensitive operation (restoring from a cloud backup, syncing passwords), the system will then request additional verification with any method.
(Image from https://blogs.technet.microsoft.com/enterprisemobility/2016/07/25/microsoft-authenticator-coming-august-15th/ )
If the user decides to enable the full protection provided by two-factor authentication, nothing will really change except that secondary verification will take place at every attempt to sign in to a Microsoft Account.
In a way, this all means that two-factor authentication for Microsoft Accounts is always there. Whether the user has the switch “enabled” or “disabled” only affects the scope of protection: “enabled” two-factor authentication protects all sign-in requests, while if the additional protection is “disabled” it only protects against suspicious sign-in activities and highly sensitive operations such as restoring data from a cloud backup and syncing Internet Explorer/Edge passwords with a new device.
Enrolling to two-factor authentication can only be performed online from the user’s Microsoft Account: https://account.live.com/proofs/Manage
The user does not have to have any Microsoft or Windows device in order to use two-factor authentication. It’s the same with Google, but Apple would only enable two-factor authentication if the user owns at least one iOS or macOS device. On the other hand, Apple’s two-step verification could be also enabled via the browser.
Microsoft Account: Delivery Options
Microsoft offers plenty of delivery options for secondary authentication. This includes:
- A code sent to backup email address (Microsoft or non-Microsoft email addresses supported)
- Text message sent to a trusted phone number
- Identity verification app: interactive prompt (similar to Google Prompt) delivered to Microsoft Authenticator apps on Windows, Android and iOS
- Previously, Microsoft Account app was used on Android for the same purpose
- Microsoft Authenticator app integrates interactive authentication functionality for Microsoft Accounts with TOTP for third-party accounts
- App-specific passwords
- An email is sent every time the user attempts to sign in from an app or device not supporting two-factor authentication, suggests using app-specific password
- If Microsoft knows such apps or devices are used, an app-specific password will be generated and displayed automatically as the user sets up two-factor authentication for the first time
- Alerts are delivered to trusted emails and phone numbers
- Printable recovery code (for reinstating account access)
Microsoft Account: SIM-Based Authentication
We discussed SIM-based authentication already. Notably, Microsoft does not require the user to configure a trusted phone number. If, however, a trusted phone number is configured, Microsoft will attempt to automatically perform the secondary authentication step when setting up a new Windows 10 Mobile device and restoring it from the OneDrive backup. The company will send a text message to that phone, and the Setup wizard will automatically receive that message and verify sign-in.
Microsoft Account: TOTP
Microsoft supports the time-based one-time password algorithm to generate 6-digit verification codes. Users can add trusted devices by scanning a QR code. Just like Google, Microsoft allows using the same seed on multiple devices, which also means that TOTP-based authenticator apps are not individually revocable. Revoking an authentication app instantly invalidates codes generated by all other authentication apps initialized with that seed.
While Microsoft makes use of the industry-standard implementation that generates a new 6-digit password every 30 seconds, the company’s proprietary Microsoft Authenticator offers a somewhat different experience. Adding a Microsoft Account by signing in (with email and password) as opposed to scanning a QR code results in a new entry that generates 8-digit passwords every 30 seconds. Interestingly, in this scenario a unique seed is used for every Microsoft Authenticator installation; as such, those are individually revocable.
Microsoft Authenticator is available for Android, iOS and Windows 10 platforms, and provides push-based authentication in addition to 6-digit and 8-digit TOTP codes. Interestingly, one can freely choose between using 6-digit and 8-digit TOTP codes at any time to verify Microsoft Account sign-ins.
Microsoft Identity Verification App: Push and TOTP
Microsoft implements push-based authentication prompt via its proprietary Microsoft Authenticator app. Historically, Microsoft offered this authentication experience exclusively on the Android platform via the Microsoft Account app. Ironically, this very functionality was not available on Microsoft’s own mobile operating system, Windows Phone 8.1 and later Windows 10 Mobile.
It was only recently that Microsoft has released a proper Microsoft Authenticator app with an interactive authentication prompt. In this case, it’s a simple “Yes” or “No” prompt with no additional code displayed or required. Each prompt has its own unique identifier allowing the user to see if the request comes from the login session they are trying to authenticate. This type of authentication is server-based. Confirming the request automatically verifies sign-in session.
Interestingly, Microsoft Authenticator operates differently across platforms. Android and iOS devices must be unlocked in order for the user to access the prompt. Windows 10 Mobile devices will display the authentication prompt and allow the user to confirm the request even if the phone is locked. This is one major security issue with Microsoft’s implementation on Windows 10 Mobile smartphones.
Microsoft: App-Specific Passwords
Microsoft offers app-specific passwords. The implementation is similar to Apple’s and Google’s. App-specific passwords consist of 16 lowercase letters, and are individually revocable.
Microsoft sends an email to the user’s registered email address every time it detects an attempt to use Microsoft Account-related services with an app not supporting two-factor authentication. This, for example, includes BlackBerry 10 Hub (built-in email app) as well Microsoft Outlook from older versions of Microsoft Office that use IMAP to access Microsoft email accounts. If the user attempts to sign in from an app or device not supporting two-factor authentication, the company will deliver an email with instructions on how to generate an app-specific password for that app.
Interestingly, Microsoft seems really serious about app-specific passwords; much more so than Google or Apple. If Microsoft knows that the user has active apps or devices accessing Microsoft services and not supporting two-factor authentication, an app-specific password will be generated and displayed automatically as the user sets up two-factor authentication for the first time.
Conclusion
We reviewed two-factor authentication options available on all three major mobile platforms. Apple prefers keeping things inside their closed ecosystem which, in theory, could offer the best security. This is spoiled with one notable exception: Apple requires users verifying at least one trusted phone number, which opens a way for attackers to spoof two-factor authentication by cloning or replacing the victim’s SIM card. Google offers a wide array of authentication options. The insecure SMS/phone call verification is also there, but at least it’s not obligatory. Microsoft offers some very interesting authentication options; insecure delivery methods include trusted email address (Microsoft or non-Microsoft) and SMS/phone calls. In addition, Microsoft’s implementation of cloud-based push is flawed on the company’s very own mobile platform: Windows 10 Mobile devices allow confirming such prompts even if their display is locked. We have no clear winner as each company offers the choice of authentication options catering to their very own audience.



