Thanks to its presence on Windows and Mac computers, iPhones and Android smartphones (on which it enjoys the default browser status), Google Chrome is the world’s most popular Web browser. In this article you’ll find a comprehensive guide on how to extract Google Chrome passwords from local computers and Google Account. We’ll also cover some common and some little known scenarios helping examiners put extracted passwords to good use – such as decrypting external NAS storage, unlocking BitLocker drives and attacking strong passwords. Let’s find out how to obtain Google Chrome passwords from multiple local and cloud sources such as the user’s Mac or Windows computer and their Google account.
Did you know you might be able to use Chrome passwords to decrypt BitLocker drives, download iCloud backups, break strong encryption or access the user’s comprehensive location history? Scroll down to Case Studies to find out how!
Extracting Chrome Passwords Instantly from a Local Computer (Windows)
For extracting Chrome passwords from a Windows computer, we’ll use Elcomsoft Internet Password Breaker (EINPB). Note that the extraction works on a live system only; you must be logged in under the user account whose passwords you are about to extract.
Why does one need to perform the extraction on a live system, with the user being logged on? The reason lies in Windows protection mechanisms. While it is technically possible to extract passwords from an offline system or disk image, the required encryption keys are difficult to access and extract if the user is not logged in.
Pre-requisites:
- Live system (or VM)
- Logged in as a user whose passwords are being extracted
- Elcomsoft Internet Password Breaker
Steps to extract Chrome passwords using Elcomsoft Internet Password Breaker:
- Launch Elcomsoft Internet Password Breaker
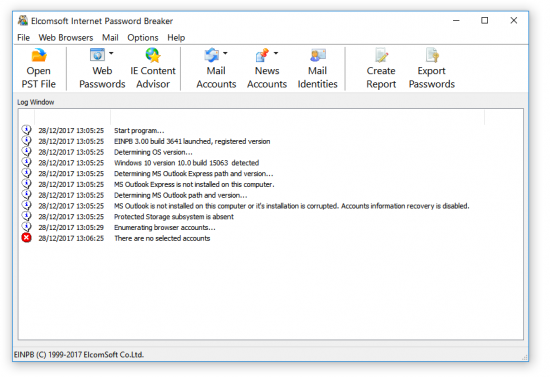
- Click Web Passwords – Google Chrome
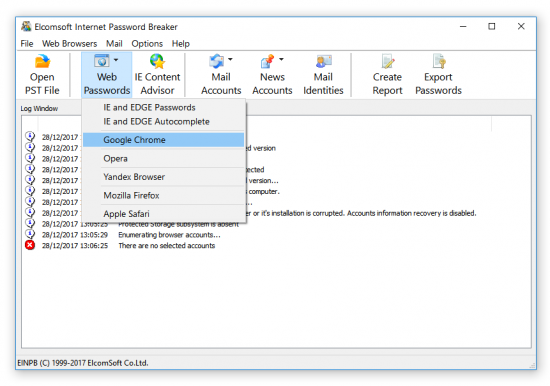
- In a few moments, a window containing the list of accounts and passwords will be opened.
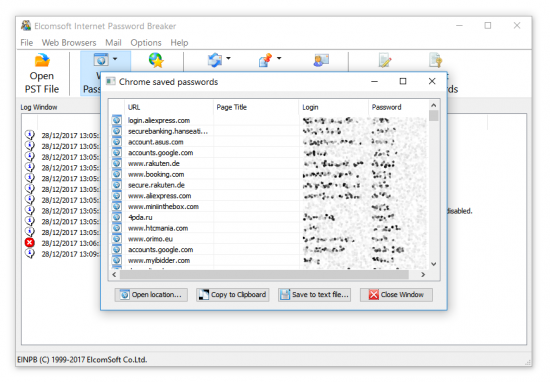
- You may review individual passwords or export the list of accounts and passwords into a text file. However, we recommend using the Export Passwords button to create a filtered dictionary of all passwords discovered on the user’s computers. This dictionary may be used to attack other passwords with Elcomsoft Distributed Password Recovery, Advanced Office Password Recovery or other similar tools.

- You will be prompted for name and location of the text file to contain the passwords.
Extracting Chrome Passwords from Google Account
Google collects, stores and processes huge amounts of information. This includes accounts and passwords used in Google Chrome. Passwords are stored in the user’s Google Account and automatically synchronized across devices and Chrome instances that are signed in to the same account.
Elcomsoft Cloud Explorer 1.30 or newer is required to extract text messages from the Google Account. In order to download text messages, do the following:
- Launch Elcomsoft Cloud Explorer 1.30 (or newer)
- Click File – Add Google Snapshot
- Authenticate into the Google Account by providing the user name and password
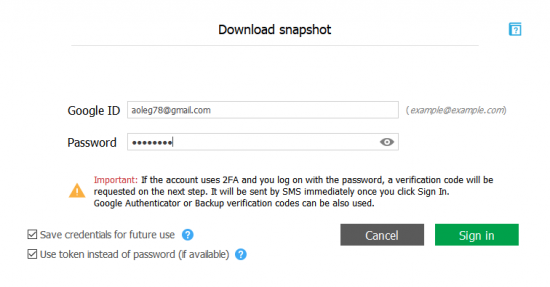
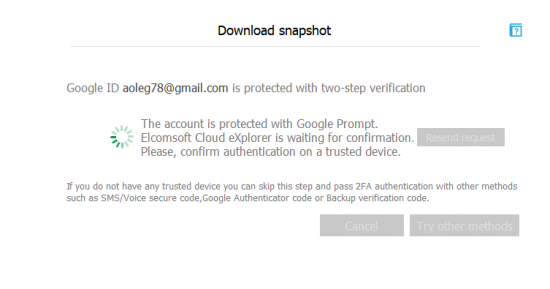
- If Two-Factor Authentication is enabled, you will be prompted for a secondary authentication code. Elcomsoft Cloud Explorer automatically detects the type of two-factor authentication on the user’s account. As an example, if an account is protected with Google Prompt, you will be asked to confirm an interactive prompt on one of the user’s trusted devices. If a trusted device is not available, choose “Try other methods” instead. In this case, you will be able to use an 8-digit backup code or a 6-digit TOTP code generated by the Authenticator app.
- Once the authentication is completed, select Chrome.
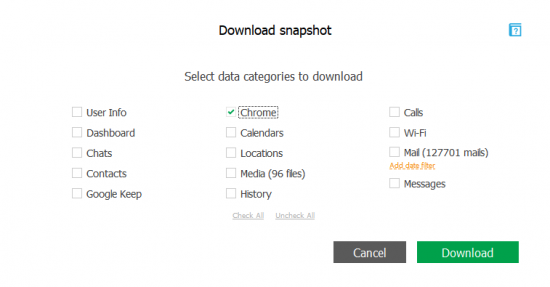
- Elcomsoft Cloud Explorer will download Chrome data from the Google Account. This may take a few minutes depending on the number of data stored in that Google Account.

- Once the download is finished, you’ll be able to access Chrome data.
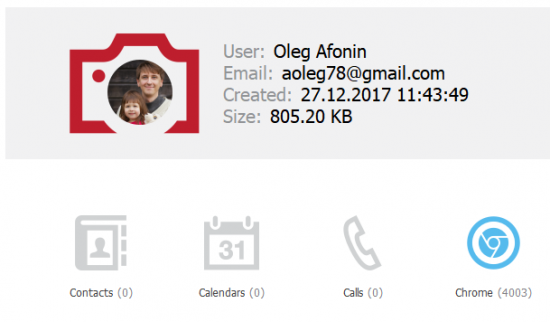
- Click Chrome, and the passwords will be displayed in the window that opens.

- You may use the Export button to export Chrome accounts and passwords into an Excel-compatible spreadsheet. If you need to build a filtered password dictionary for using with Elcomsoft Distributed Password Recovery, you may copy passwords from the Excel spreadsheet, filter out duplicated entries and save them into a text file.
Chrome Password Sync Protection
If it is this easy to extract passwords from the user’s Google Account, does it mean they are not protected? Not exactly. By default, the data (logins and passwords) is protected with the user’s Google credentials. However, the user may specify their own passphrase to additionally protect passwords.
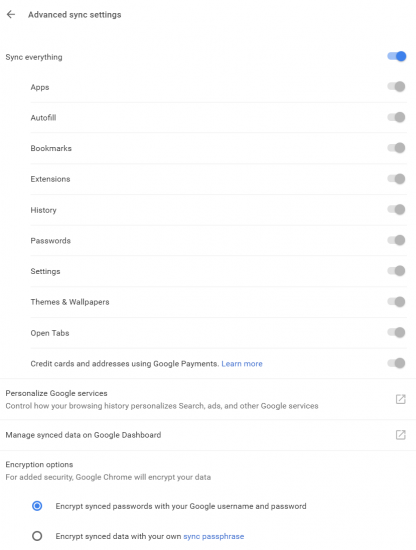
The differences between the two types of protection are described in Google’s documentation.
Notably, if the user forgets their passphrase, there is no way to access passwords. Google recommends disabling and re-enabling password sync, which will remove all previously stored passwords from the user’s account.
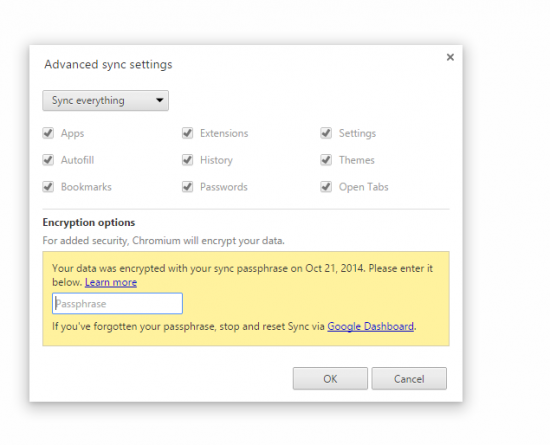
If Elcomsoft Cloud Explorer detects that the passwords are additionally protected with a passphrase, it will prompt for the sync passphrase before downloading the data.
Extracting Chrome Passwords from macOS
Similar to iOS devices, macOS offers a system-wide protected storage for keeping account credentials, passwords and other sensitive information. Among other things, macOS keychain contains passwords used by Google Chrome. By extracting and analysing macOS keychain, experts can gain access to Chrome passwords stored on Mac computers.
Similar to Windows, keychain extraction is only possible for the current user during a live system analysis.
Pre-requisites:
- Live system (or VM)
- Logged in as a user whose passwords are being extracted (password MUST be known or recovered), OR
- If extracting keychain of a different user: administrative password and user’s password are both known (or recovered)
- Elcomsoft Password Digger
Steps to extract Chrome passwords from a Mac:
Step 1: Make local copies of the keychain database files on the Mac:
– Create a new folder (e.g. “KEYCHAINS” on the Desktop)
– Open Terminal and change current folder to the one you just created, e.g:
cd Desktop/KEYCHAINS
– Copy the following files into the current folder:
cp /Users/<username>/Library/Keychains/login.keychain-db .
Optional (see below notes):
cp /Library/Keychains/System.keychain .
sudo cp /private/var/db/SystemKey .
Note: the trailing dot “ . “ is required as it represents the current folder.
The first command copies the main keychain (user keychain). In macOS 11.12 (Sierra) and 11.13 (High Sierra), the file name is “login.keychain-db”.
Note: in older versions of macOS the file name is “login.keychain”.

In order to decrypt the file, the user’s password will be required. In order to access a keychain database of a user other than the currently logged in one, a sudo command must be entered first.
The second command copies the system keychain. This keychain is system-wide, and is the same for all users. This step is optional as the system keychain contains little useful data other than Wi-Fi passwords. In order to decrypt this keychain, a system key is required, which is copied using the next command.
The third command copies the system key (sudo and administrative password both required).
Step 2. Copy the file(s) to a Windows computer with Elcomsoft Password Digger installed.
Step 3. The rest is easy. Launch Elcomsoft Password Digger and specify path to the file(s) you’ve extracted. You will need to specify the user’s password to decrypt the user keychain.
For macOS Sierra and High Sierra:
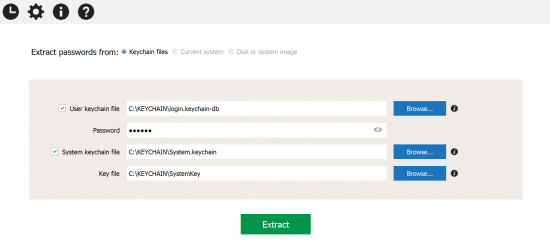
For older versions of macOS:
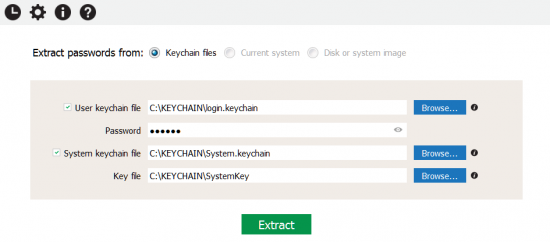
Important: By default, the keychain password is the same as the user’s login password. However, macOS has an option allowing users to manually change keychain password. In addition, the keychain password may differ from the user’s account password if the account password was reset. If this is the case, you will need to provide the correct keychain password (rather than the user’s login password). Additional information:
https://support.apple.com/kb/PH20094
https://support.apple.com/en-us/HT201609
Step 4. In a few moments, the keychain will be decrypted. You will then be able to save the entire content of the keychain into an XML file, or create a filtered text dictionary for using with Elcomsoft Distributed Password Recovery or other password recovery tools.

You can now access Chrome passwords along with all other passwords stored in the user’s macOS keychain.
If you need to break keychain password
If you don’t know the correct user password and/or the keychain password, you may recover it with Elcomsoft Distributed Password Recovery. While you may attack either password, note that macOS uses significantly weaker encryption to protect the keychain as opposed to user accounts. As a result, we recommend to always attack the keychain password (as opposed to attacking user account passwords). The speed of recovery for keychain passwords is nearly 100 times faster compared to breaking macOS account passwords.
If FileVault 2 encryption is enabled
If the Mac is encrypted (FileVault 2), you will need to decrypt the volume before you can copy the keychain database. While you can easily decrypt the volume if you know the user’s login password, you may still need to brute-force that password if it’s unknown. Elcomsoft Distributed Password Recovery supports FileVault 2 passwords.
Case Studies
Now that you have the user’s stored passwords, what do you use them for? While accessing the user’s social networks, chats and online shopping accounts may provide essential evidence, we have a few use cases you may have never thought of.
Decrypt Encrypted Archives, Documents and Disk Volumes
By combining the user’s Chrome passwords into a filtered text file (removing duplicates and sorting passwords by the number of accounts they are used with), you are creating the most targeted custom dictionary for attacking the user’s other passwords. You can use this dictionary to attack data protected with strong encryption that would take years (or eternity) to brute-force. You can use this dictionary with Elcomsoft Distributed Password Recovery or similar tools to attack password-protected Microsoft Office documents, ZIP/RAR archives, encrypted volumes, and much more.
Microsoft Account and BitLocker
Did you know that, in many cases, Microsoft automatically backs up BitLocker recovery keys into the user’s Microsoft Account? This, in particular, applies to most devices encrypted with so-called BitLocker Device Protection. BitLocker Device Protection is activated automatically, without the user even realizing their device is encrypted, if several conditions are met:
- The device runs Windows 8, 8.1, Windows RT or Windows 10
- The device meets all Connected Standby criteria such as solid-state storage and non-removable memory
- The device is equipped with a TPM2.0 module
- The user signs in to their computer with their Microsoft Account credentials as opposed to using a local Windows account
If all of the conditions listed above are met, the device will begin encrypting the disk immediately after the user logs in with their Microsoft Account credentials (with administrative privileges). The BitLocker recovery key will be automatically (and silently) uploaded into the user’s Microsoft Account.
By analysing Chrome passwords, you may be able to obtain the user’s Microsoft Account password. This password may be cached under live.com, hotmail.com, microsoft.com etc.
BitLocker recovery keys to all devices registered under that Microsoft Accounts can be retrieved by using the following link:
https://account.microsoft.com/devices/recoverykey
You can then mount or decrypt the encrypted volume by using Elcomsoft Forensic Disk Decryptor.
More information about BitLocker recovery keys:
https://support.microsoft.com/en-us/help/4026181/windows-find-my-bitlocker-recovery-key
iCloud: iOS Backups
If the user signed in with their Apple ID into any services provided by Apple, you may be able to access their Apple ID password by looking for items such as “icloud.com” or “apple.com” in Chrome passwords. Once you have the user’s Apple ID password, you may be able to use Elcomsoft Phone Breaker to access the user’s iCloud backups, synchronized data such as call logs, calendars and notes, as well as their iCloud Photo Library. If Two-Factor Authentication is enabled, you would still need access to the secondary authentication factor.
Google Account and Location History
With Elcomsoft Cloud Explorer, you can extract comprehensive location history, text messages, and a lot more information directly from the user’s Google Account. You may be able to retrieve the user’s Google Account passwords by looking for “google” in Chrome passwords.
Note: if two-factor authentication is enabled, you will still need access to the secondary authentication factor.



















