Google has started its journey on convincing people to move away from SMS-based verification, and start receiving push messages via the Google Prompt instead of using six-digit codes. Why does Google want us away from SMS, and why using Google Prompt instead? Let’s try to find out.
SMS Are Insecure, Aren’t They?
In late July 2016, the US National Institute of Standards and Technology’s (NIST) released an updated set of guidelines that deprecated SMS as a way to deliver two factor authentication because of their many insecurities. A year later, NIST took it back, no longer recommending to “deprecate” SMS usage. Are we, or are we not at risk if we choose to have our two-factor authentication delivered over the (arguably) insecure SMS channel?
While we are not going to have a detailed discussion on whether or not SMS are secure enough to be used for consumer-based two-factor authentication, Google seems to be convinced they aren’t. For this reason, Google is making the move of pushing its users towards the newer, more secure authentication method. In addition to being more secure new prompts are more secure than SMS, the new authentication method makes the process of signing into the Google account faster and easier than SMS. Meet Google Prompt, the (relatively) new two-factor authentication mechanism aimed at replacing the insecure SMS authentication and the aging Authenticator app.
The Google Prompt
Google Prompt was designed to both mitigate the security risks associated with the delivery of secondary verification codes via SMS, and make the sign process easier and more streamlined. It seems that Google was able to strike both.
Text messages may not be great for delivering two-factor authentication, but they’ve been there for ages. On the other hand, Google Prompt has made its first appearance about a year ago. This relatively new technique is now pushed by Google to replace the aging and insecure SMS verification.
What is Google Prompt about? Instead of generating codes in the Authenticator app or sending a one-time code in a text message, Google Prompt simply asks users if they are trying to sign in by pushing an interactive prompt to the user’s enrolled (trusted) devices. If the user confirms the prompt (by unlocking their device and tapping “Yes”), they are allowed to sign in. There are no codes to enter, and no additional steps are required on the device (or browser) that is attempting to sign in. The entire process is straightforward and as much automated as possible.
Here are the differences between Google Prompt and traditional (SMS or Authenticator based) two-factor authentication techniques.
Authenticator
- User enters their Google ID and password
- User is prompted for a code
- User opens the Authenticator app on the same or another device, obtains a 6-digit code, switches back to the original device or app, and enters that code into the prompt on the original device or browser
- Sign in complete
SMS verification
- User enters their Google ID and password
- User is prompted for a code
- User receives a text message (SMS) with the code, goes back to the original device or app, and enters that code into the prompt on the original device or browser
- Sign in complete
Google Prompt
- User enters their Google ID and password
- User is prompted to confirm the sign in attempt on a trusted device
- User receives a prompt on the same or different device and taps “Yes”
- Sign in complete
Of the three authentication methods, Google Prompt offers the easiest and most streamlined sign-in experience. All communications are performed over a secured (encrypted) communication channel, and are impossible to intercept or tamper with (unlike a SIM card that could be inserted into a different – unlocked – phone or replaced at a mobile service provider).
Is Google Prompt invincible? It’s not. We had experience where cloning the content of the device by making and restoring a nandroid backup onto a different phone resulted in Google Prompt notifications being pushed onto the new device. However, making a nandroid backup requires the donor device to have an already unlocked or exploitable bootloader, which is not a given.
Google Prompt vs. Apple Two-Factor Authentication
How does Google Prompt fare against its closest rival, Apple’s Two-Factor Authentication? The two authentication systems have similarities, but they also have differences. Let’s have a closer look on how two-factor authentication prompts are delivered, how the user can access them, and how the user has to interact with them in order to pass the secondary authentication step.
Delivery
Both Google Prompt and Apple Two-Factor Authentication (2FA) messages are delivered instantly and simultaneously to *all* trusted devices enrolled into the corresponding two-factor authentication scheme. The prompts are delivered using each company’s proprietary push mechanisms.
Compatibility
Google Prompt is supported on Google Android devices (Android smartphones and tablets running a Google-certified version of Android with Google Cloud Messaging services installed). In addition, Google Prompt is supported on iOS devices through Google app.
Apple’s 2FA is exclusively supported on Apple devices running iOS 9 (and newer) and macOS Sierra (and newer).
Interaction
In order to pass two-factor authentication challenge for Google Accounts, users have to unlock their device (secure lock screen not required) and tap “Yes” on the full-screen Google Prompt (Android). In iOS, the user would have to tap a lock screen notification to open the Google app, and tap “Yes” to confirm the request. At this point, whichever app or service was trying to sign in to the Google Account would be automatically authenticated.
Apple’s 2FA is a two-step process. First, the user unlocks the trusted device and confirms the pop-up prompt by tapping “Yes”. This would be all if that would be Google Prompt; however, Apple will then additionally push a 6-digit code. The user must enter the six digits into the sign in prompt in the app or service they were using to access the Apple ID account. Only then the sign in process will be completed.
Extracting Data from Google Accounts Protected with Google Prompt
You can extract information from users’ Google Accounts even if they are protected with Google Prompt. In order to do this, you will have to have access to all of the following:
- The user’s login (Google ID) and password.
- A trusted device signed in to the target Google Account and enrolled into Google Prompt. This can be a smartphone or tablet running Android or iOS.
- A way to unlock the trusted device (PIN, pattern, fingerprint, Smart Unlock, exploit, leaked engineering bootloader)
- Elcomsoft Cloud Explorer 2.0 or newer (Windows or Mac edition)
In order to access someone’s data with Elcomsoft Cloud Explorer 2.0, perform the following steps.
- Open Elcomsoft Cloud Explorer.
- Enter Google ID and password.
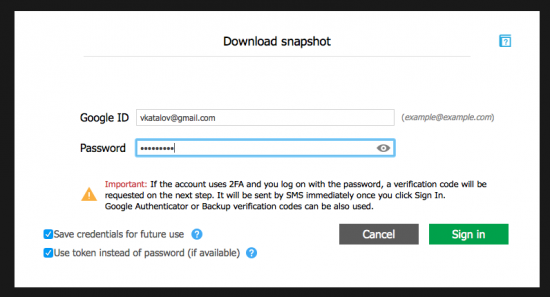
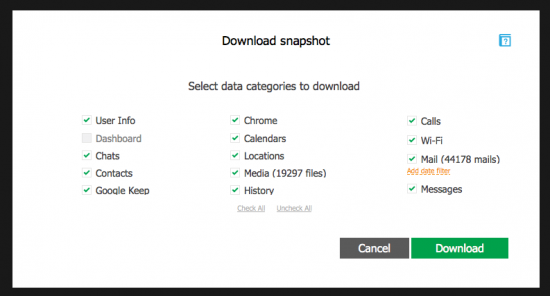
- If two-factor authentication is enabled on that Google Account, you will see the following window.
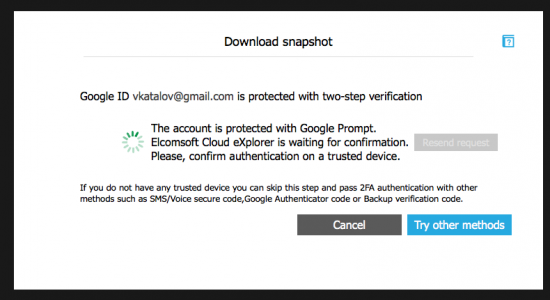
- If Google Prompt is active, you will receive a push message on the trusted device.
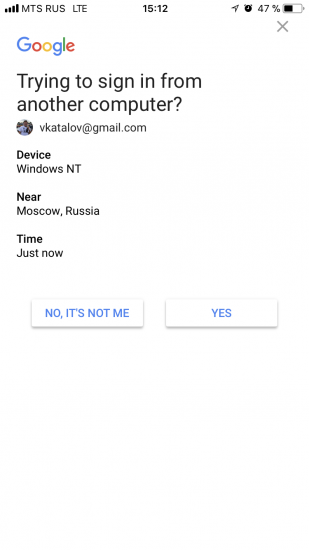
- Confirm Google Prompt by tapping “Yes”.
- In Elcomsoft Cloud Explorer, click “Next”.
- You have now successfully signed in.
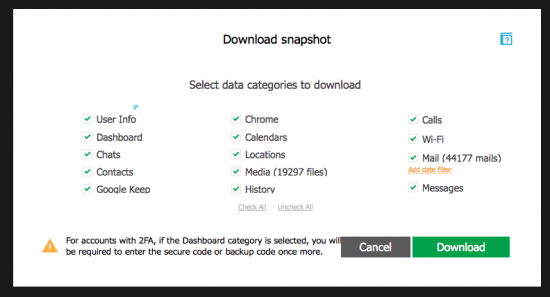
Note: if you have previously logged in at least once, with or without 2FA, and the “Save Credentials” option was selected, you will be able to use previously saved credentials by choosing the “use token instead of password” option. In this case, you will not require a secondary authentication factors. However, if you do, the Dashboard category will not be available as it always requires authentication. This is intended behavior.
Extracting Data from Google Accounts Protected with a FIDO Key
You can extract information from users’ Google Accounts protected with a hardware-based two-factor authentication solution compatible with the FIDO Key standard. Since FIDO Key and Google Prompt are mutually exclusive (one can choose one or the other in a single account), you will not have a choice of which authentication method to prefer. However, SMS-based authentication codes are still available during both processes. In order to acquire a FIDO Key protected account, you will have to have access to all of the following:
- The user’s login (Google ID) and password.
- A trusted FIDO Key.
- Your computer (Windows or Mac) must be capable to read the key (USB port, hub or adapter required).
- Elcomsoft Cloud Explorer 2.0 or newer (Windows or Mac edition).
In order to access someone’s data with Elcomsoft Cloud Explorer 2.0, perform the following steps.
- Open Elcomsoft Cloud Explorer.
- Enter Google ID and password.
- If two-factor authentication is enabled on that Google Account, you will see the following window.
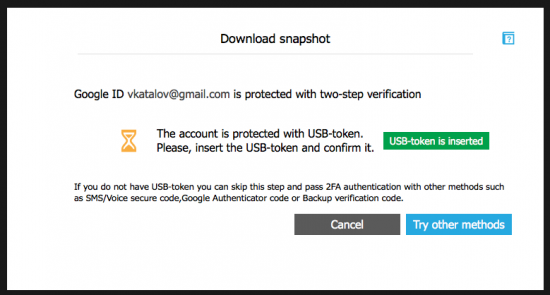
- Insert the USB token (FIDO Key) into a USB port on your computer.
- In Elcomsoft Cloud Explorer, click “USB token is inserted”.
- You have now successfully signed in.








